New Clickfix Attack Promises “Free WiFi” But Delivers Powershell-Based Malware
The Deceptive Lure of “Free WiFi”: Unpacking the Clickfix Attack
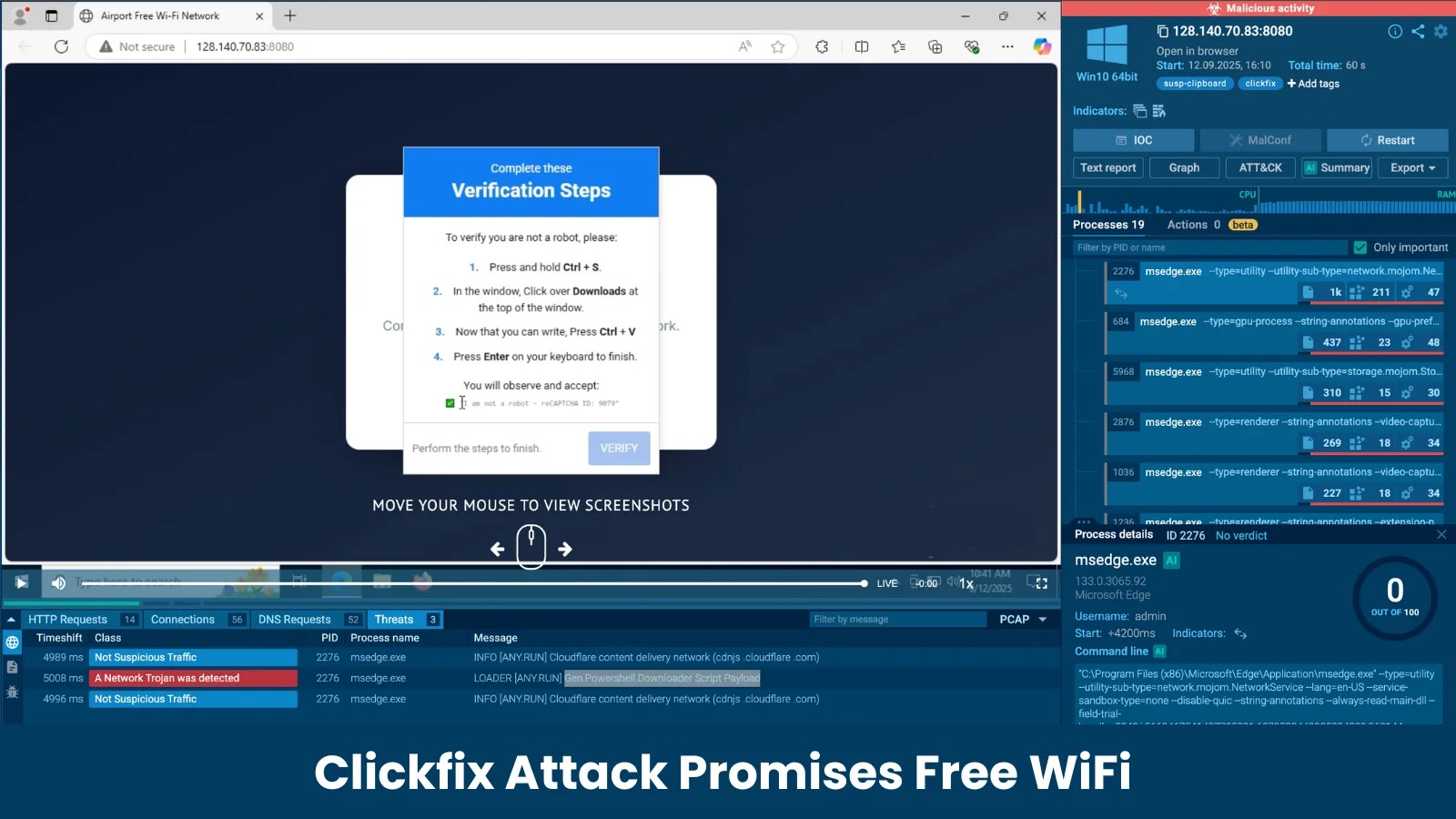
In an increasingly connected world, the promise of free internet access often proves irresistible. Cybercriminals are keenly aware of this universal desire, and a recent campaign dubbed the “Clickfix” attack masterfully exploits it. This sophisticated social engineering tactic, uncovered by the dedicated research team at Cybersecuritynews, leverages deceptive Wi-Fi portals to trick unsuspecting users into compromising their own systems. Far from offering convenience, the Clickfix attack delivers potent PowerShell-based malware, turning a simple browser action into a complete system compromise.
Understanding the intricacies of this threat is paramount for IT professionals, security analysts, and developers tasked with safeguarding digital environments. This post delves into the mechanics of the Clickfix attack, outlines its impact, and provides actionable remediation strategies to protect against similar social engineering exploits.
How the Clickfix Attack Operates
The Clickfix attack distinguishes itself through its insidious simplicity and effective use of social engineering. At its core, the attack preys on the immediate gratification associated with obtaining free Wi-Fi.
- Deceptive Wi-Fi Portals: Users are initially lured by what appears to be a legitimate free Wi-Fi hotspot. These rogue access points are designed to mimic common public Wi-Fi networks found in cafes, airports, or public spaces.
- Browser-Based Trickery: Once connected to the fraudulent network, the user’s browser is redirected to a captive portal page. This page, crafted to appear trustworthy, includes prompts or buttons that seem necessary to gain internet access.
- Exploiting Trust and Urgency: The critical step involves the user’s interaction. Instead of simply authenticating, clicking a seemingly innocuous “connect” or “agree” button triggers a malicious download or script execution. The clever aspect of Clickfix is that it leverages the user’s own browser actions—something typically perceived as safe—against them.
- PowerShell-Based Malware Delivery: The downloaded payload or executed script is PowerShell-based. PowerShell, a powerful command-line shell and scripting language, is a legitimate and often essential tool for system administration but is frequently abused by attackers due to its inherent capabilities and common presence on Windows systems. The use of PowerShell allows the attackers to execute arbitrary commands, download additional malware, establish persistence, and exfiltrate data, often bypassing traditional endpoint security measures if not properly configured.
The Peril of PowerShell and Social Engineering
The combination of social engineering and PowerShell exploitation presents a significant challenge. Social engineering bypasses technical controls by manipulating human behavior, acting as the initial entry vector. Once a user is tricked, PowerShell provides a flexible and powerful mechanism for the adversary to achieve their objectives on the compromised machine.
Unlike traditional executable files that might raise immediate red flags, PowerShell scripts can sometimes be less conspicuous, especially if they are disguised or executed as part of legitimate system processes. This low-profile execution can allow the malware to establish a foothold and operate undetected for extended periods, leading to data breaches, ransomware infections, or further network infiltration.
Remediation Actions and Prevention Strategies
Mitigating the risk posed by attacks like Clickfix requires a multi-layered approach that combines technical controls with user education. Proactive measures are always more effective than reactive responses.
- Exercise Extreme Caution with Public Wi-Fi: Users should be highly skeptical of “free” or unsecured public Wi-Fi networks. It’s advisable to use a VPN (Virtual Private Network) when connecting to any public Wi-Fi to encrypt all traffic, or, ideally, use a mobile hotspot for sensitive tasks.
- Validate Wi-Fi Networks: Before connecting, confirm the legitimacy of the network with the establishment staff. Be wary of networks with generic names or unusually strong signals that appear out of place.
- Disable Auto-Connect: Configure devices not to automatically connect to unknown Wi-Fi networks. Manually selecting and verifying networks adds a crucial layer of security.
- Employ Endpoint Detection and Response (EDR): Advanced EDR solutions can monitor PowerShell activity for suspicious behavior, detecting and blocking malicious scripts even if they are executed through social engineering. Look for solutions that focus on behavioral analysis rather than just signature-based detection.
- Implement Least Privilege: Ensure users operate with the minimum necessary permissions. This can limit the impact of a successful PowerShell attack, as the malware will be restricted in what it can do on the system.
- Regular Security Awareness Training: Educate employees about the dangers of social engineering, phishing, and deceptive Wi-Fi hotspots. Emphasize the importance of verifying sources before clicking links or executing files.
- Keep Systems Updated: Apply security patches and updates promptly. While Clickfix exploits social engineering, underlying system vulnerabilities could be exploited by the PowerShell malware once it gains access. Regularly patching operating systems and applications reduces the attack surface.
- Antivirus/Anti-Malware Solutions: Maintain robust, up-to-date antivirus and anti-malware software on all endpoints. While they may not initially block the social engineering aspect, they can detect and quarantine the PowerShell payloads.
Relevant Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| PowerShell Logging | Enables comprehensive logging of PowerShell activity for forensic analysis and threat detection. | Not a specific tool, but an OS feature. Refer to Microsoft documentation. |
| Microsoft Defender for Endpoint | Comprehensive EDR solution with behavioral monitoring for PowerShell and other threats. | https://www.microsoft.com/en-us/security/business/microsoft-365-defender/endpoint-detection-response-edr |
| Splunk (or other SIEM) | Centralized log management and security information and event management; useful for correlating PowerShell logs with other security events. | https://www.splunk.com/ |
| Wireshark | Network protocol analyzer for detecting suspicious network activity potentially initiated by malware. | https://www.wireshark.org/ |
| Metasploit Framework | Penetration testing tool, useful for understanding how such attacks are constructed and for testing defenses against them. | https://www.metasploit.com/ |
Conclusion
The Clickfix attack serves as a stark reminder that cyber threats are constantly evolving, leveraging human tendencies as much as technical vulnerabilities. The deceptive promise of “free WiFi” can lead directly to potent PowerShell-based malware, turning convenience into compromise. By understanding the mechanisms of such social engineering campaigns and implementing robust technical controls coupled with continuous user education, organizations and individuals can significantly reduce their exposure to these insidious threats.
Vigilance against seemingly innocuous offers and a deep understanding of how adversaries exploit trust remain critical components of effective cybersecurity. Staying informed about new attack vectors, such as the Clickfix method, is not merely advisable but essential for maintaining a strong security posture in an interconnected world.





