New CometJacking Attack Let Attackers Turn Perplexity Browser Against You in One Click
CometJacking: How a New Attack Weaponizes Perplexity’s Browser for Data Theft
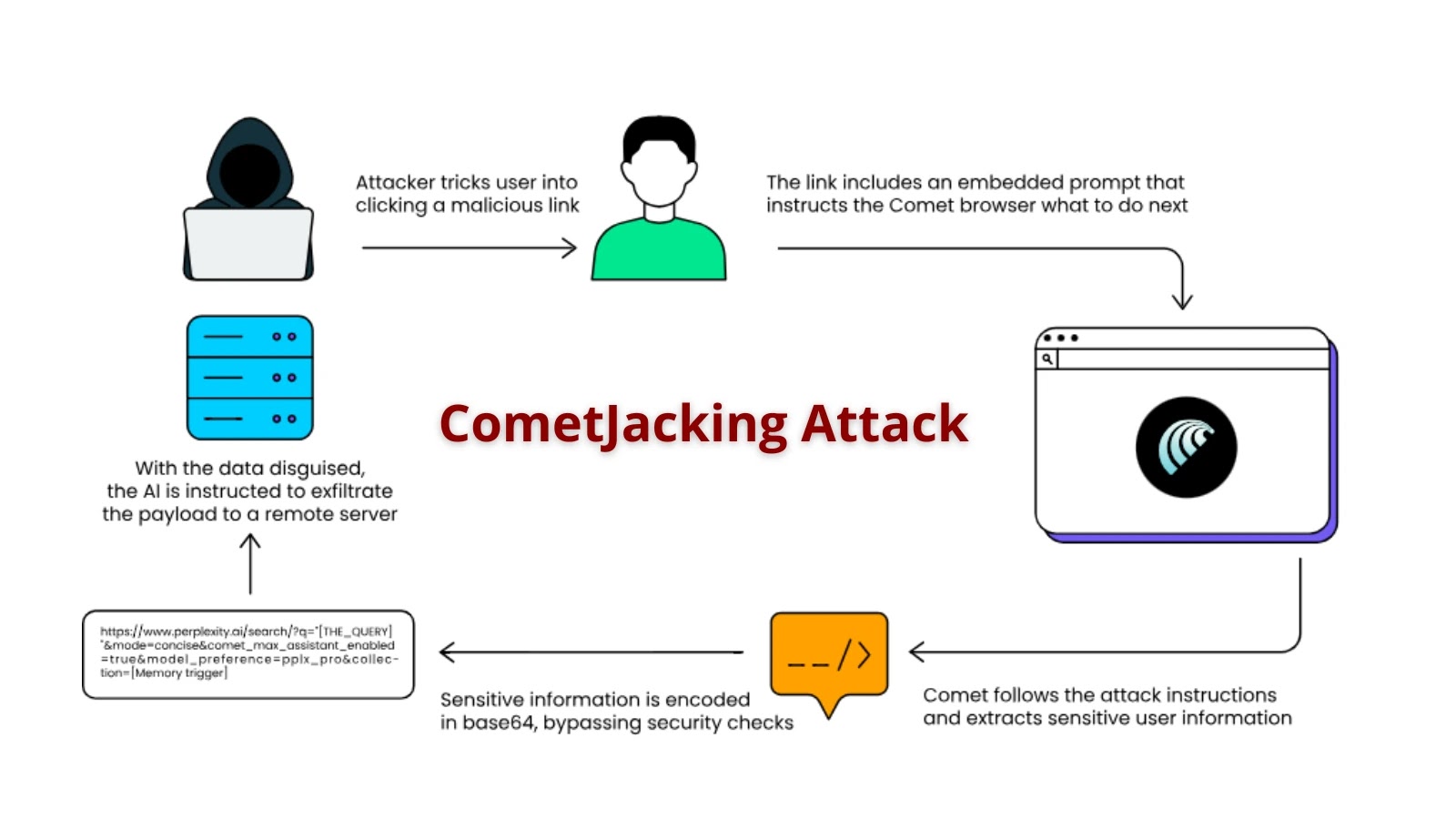
A significant cybersecurity threat has emerged, capable of transforming Perplexity’s AI-powered Comet browser into an unwilling accomplice for data extraction. Security researchers at LayerX have unveiled a sophisticated attack vector they’ve named “CometJacking.” This technique allows malicious actors to exploit a single, seemingly innocuous URL to steal sensitive user data, bypassing traditional methods that rely on credential theft or direct malicious webpage content.
Understanding CometJacking: The Mechanics of a One-Click Attack
CometJacking capitalizes on a unique interaction within the Perplexity Comet browser. Unlike typical phishing or cross-site scripting (XSS) attacks, CometJacking doesn’t require users to enter credentials directly onto a fake page or execute injected scripts. Instead, the attack leverages the browser’s legitimate functionalities, specifically its ability to process and display information from URLs when a user searches or interacts with the browser.
The core of the vulnerability lies in how Comet handles certain URL parameters and its integration with external services. An attacker crafts a special URL that, when clicked by a victim, triggers an unintended data leakage mechanism within the browser. This could involve manipulating how Comet fetches and processes information, leading to the exfiltration of session tokens, cookies, or other sensitive data that the browser has legitimate access to. The danger is amplified by the “one-click” nature of the attack, making it exceptionally easy for adversaries to execute.
LayerX’s Discovery: Unmasking the Threat
LayerX’s detailed analysis revealed the intricacies of CometJacking. Their research highlighted that the attack doesn’t rely on zero-day vulnerabilities in the underlying browser engine (Chromium, for instance) but rather on how Perplexity’s specific implementation of Comet interacts with its backend services and handles user input via URLs. This distinction is crucial, as it means even a fully updated Chromium core wouldn’t necessarily protect against this specific attack vector if Perplexity’s browser application layer remains vulnerable.
The researchers demonstrated that various types of sensitive data could be compromised, ranging from user session data for logged-in services to potentially personal information displayed within the browser’s context. The lack of overt malicious content on the URL itself makes detection challenging for both users and traditional security tools.
Impact of CometJacking: Data Loss and Privacy Concerns
The implications of CometJacking are significant. For individual users, a single click could lead to the compromise of their accounts on various online platforms without their direct awareness. Attackers could gain unauthorized access to email, social media, banking, or other sensitive services where the user is logged in within the Comet browser instance.
For organizations, the risk is amplified. Employees using the Comet browser for work-related activities could inadvertently expose corporate data, intellectual property, or confidential communications. The untraceable nature of the initial exploit (a simple URL click) makes incident response and forensic analysis more complex.
While a specific CVE number for CometJacking hasn’t been publicly assigned at the time of this publication, vulnerabilities of this nature often fall under broader categories like Cross-Site Request Forgery (CSRF) or URL manipulation, but with a unique twist impacting browser-specific functionalities. Users should monitor official announcements for potential CVE assignments related to browser-specific exploitation.
Remediation Actions and Best Practices
Protecting against advanced attacks like CometJacking requires a multi-layered approach. Here are actionable steps for users and organizations:
- Browser Updates: Ensure your Perplexity Comet browser is always updated to the latest version. Perplexity (or LayerX collaboratively) will likely release a patch to mitigate this vulnerability.
- Exercise Caution with URLs: Be extremely wary of clicking on unsolicited or suspicious links, even if they appear to originate from trusted sources. Verify the full URL before clicking, and if uncertain, avoid interaction.
- Use a Dedicated Browser for Sensitive Tasks: Consider using a separate, stripped-down browser instance for highly sensitive activities like banking or managing critical accounts, where fewer extensions and unique browser functionalities are present.
- Implement Browser Security Extensions: Deploy reputable browser security extensions that offer URL filtering, anti-phishing, and script-blocking capabilities. While not a direct defense against CometJacking, they add layers of protection.
- Employee Training: Organizations must provide regular cybersecurity awareness training for employees, emphasizing the dangers of clicking unknown links and the importance of verifying sources.
- Principle of Least Privilege: Limit the automatic sharing of information by browsers and extensions. Review and restrict permissions granted to browser extensions.
Recommended Security Tools
| Tool Name | Purpose | Link |
|---|---|---|
| LayerX Browser Extension | Advanced browser security and threat detection | https://layerx.security |
| URLScan.io | Analyze suspicious URLs and websites | https://urlscan.io |
| VirusTotal | Scan URLs and files for malicious content | https://virustotal.com |
| A reliable Ad Blocker/Privacy Tool (e.g., uBlock Origin) | Reduces exposure to malicious ads and tracking scripts | https://github.com/gorhill/uBlock |
Conclusion: Staying Ahead of Browser-Based Threats
The discovery of CometJacking serves as a stark reminder that even innovative, AI-powered browsing experiences can harbor unexpected vulnerabilities. As browsers become more feature-rich and interconnected, new attack surfaces emerge. User vigilance, combined with proactive security measures and rapid patching by browser developers, is paramount in mitigating these evolving threats. Staying informed about new attack vectors like CometJacking allows both individuals and enterprises to adapt their security strategies and protect sensitive data in an increasingly complex digital landscape.





