New eSIM Hack Lets Attackers Clone Profiles and Hijack Phone Identities
The ubiquity of mobile devices in our daily lives means the security of our cellular connections is paramount. With the advent of eSIM technology, promising greater flexibility and convenience, the underlying security mechanisms are under intense scrutiny. A recent discovery, however, has sent ripples through the cybersecurity community: a critical vulnerability in eSIM technology enables attackers to clone mobile subscriber profiles and potentially hijack phone identities. This revelation underscores the persistent challenge of securing evolving mobile communication standards.
The eSIM Vulnerability: A Deep Dive
AG Security Research recently announced a groundbreaking and concerning achievement: they successfully broke the security of Kigen eUICC cards equipped with GSMA consumer certificates. This marks what they claim is the first public and successful hack against consumer GSMA eUICC and EAL-certified GSMA security chips. This vulnerability represents a significant threat because it allows malicious actors to duplicate a victim’s eSIM profile, effectively granting them control over the victim’s phone identity.
The core of the issue lies in the ability to manipulate the eUICC (embedded Universal Integrated Circuit Card), which is the secure element within an eSIM-enabled device that stores subscriber credentials. By compromising this component, an attacker can extract or replicate the profile, leading to unauthorized access to cellular services tied to the victim’s identity.
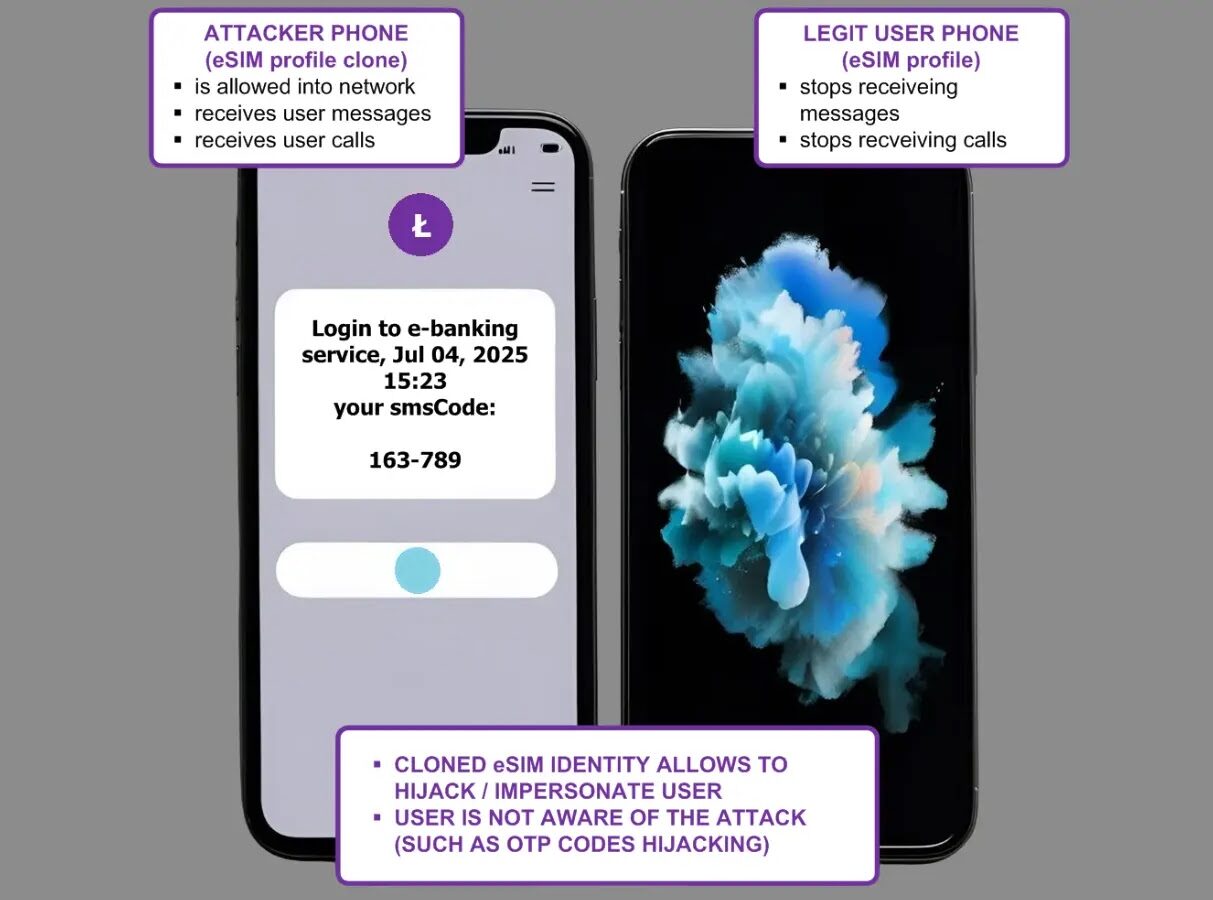
Understanding the Impact: Profile Cloning and Identity Hijacking
The consequences of this eSIM vulnerability are severe and far-reaching. Here’s a breakdown of the primary threats:
- Profile Cloning: Attackers can create an exact duplicate of a user’s eSIM profile. This cloned profile functions identically to the legitimate one, allowing the attacker to receive calls, SMS messages, and access mobile data as if they were the legitimate user.
- Identity Hijacking: With a cloned profile, an attacker can effectively hijack the victim’s phone identity. This opens the door to a multitude of malicious activities, including:
- Bypassing Multi-Factor Authentication (MFA): Many online services use SMS-based MFA. A hijacked phone identity allows attackers to intercept crucial verification codes, thereby gaining unauthorized access to banking, email, social media, and other sensitive accounts.
- Financial Fraud: Armed with access to a victim’s phone identity, attackers can initiate password resets, authorize transactions, or gain access to financial applications.
- Impersonation and Social Engineering: Attackers can impersonate the victim, sending messages or making calls to contacts, potentially perpetrating further scams or spreading malware.
- Data Exfiltration: If the attacker can access other services linked to the phone number, they might exfiltrate personal data.
Technical Nuances: Kigen eUICC and GSMA Certificates
The specific mention of “Kigen eUICC cards with GSMA consumer certificates” highlights the targeted nature of this exploit. Kigen, a subsidiary of Arm, is a significant player in the secure IoT and embedded SIM space. The fact that the vulnerability targets GSMA consumer certificates, which are industry-standard for secure mobile connectivity, suggests a fundamental flaw in the implementation or security protocols surrounding these widely adopted technologies.
While a specific CVE number has not yet been publicly assigned for this vulnerability, its successful exploitation against EAL-certified GSMA security chips indicates a critical weakness in hardware-level security or the process of loading and managing secure profiles.
Remediation Actions for Users and Organizations
Given the severity of this eSIM vulnerability, immediate action is crucial for both individual users and telecommunication providers.
For Individual Users:
- Consult Your Carrier: Immediately contact your mobile network operator to inquire about their response to this vulnerability and any recommended security measures or updates.
- Monitor Financial and Online Accounts: Regularly review financial statements and activity logs for any suspicious transactions or unauthorized access.
- Strengthen MFA: Where possible, migrate from SMS-based MFA to stronger alternatives like authenticator apps (e.g., Google Authenticator, Authy) or hardware security keys (e.g., YubiKey).
- Be Vigilant Against Phishing: Exercise extreme caution with unsolicited messages or calls asking for personal information or account details.
- Report Suspicious Activity: If you suspect your eSIM profile has been compromised, report it to your carrier and relevant authorities immediately.
For Telecommunication Providers and Device Manufacturers:
- Investigate and Patch: Urgently investigate the findings from AG Security Research. Collaborate with Kigen and GSMA to identify the root cause of the vulnerability and develop immediate patches or firmware updates for affected eUICC cards.
- Enhance Secure Provisioning: Review and strengthen the secure provisioning processes for eSIM profiles to prevent unauthorized cloning or manipulation during activation or updates.
- Implement Anomaly Detection: Deploy advanced analytics and AI-powered systems to detect unusual activity patterns associated with eSIM profiles, such as multiple activations or rapid changes in location from a single profile.
- Improve User Notification Systems: Develop robust systems to proactively notify users of any suspicious activity detected on their eSIM profiles.
- Collaborate on Standards: Work closely with industry bodies like GSMA to reinforce existing security standards and introduce new protocols that address the identified vulnerabilities in eUICC and associated certificate management.
Currently, there isn’t a widely available, direct “tool” for users to detect this specific eSIM profile cloning vulnerability. Detection would primarily rely on your mobile carrier’s backend systems. However, users can employ general security hygiene tools and practices that help mitigate the impact of identity theft that might result from such a compromise.
| Tool Category | Purpose | Recommendation |
|---|---|---|
| Password Manager | Generate and store strong, unique passwords for all online accounts. Prevents credential stuffing even if one account is compromised. | Bitwarden, 1Password, Dashlane |
| Authenticator Apps | Provide Time-Based One-Time Passwords (TOTP) for stronger Multi-Factor Authentication (MFA) than SMS. | Google Authenticator, Authy |
| Credit Monitoring Services | Alert you to unusual activity on your credit reports, indicating potential financial fraud. | Credit Karma (free), LifeLock (paid), Experian IdentityWorks (paid) |
| Advanced Endpoint Protection | While not directly related to eSIM, essential for protecting devices from malware that could serve as a vector for initial compromise. | Malwarebytes, Kaspersky |
Conclusion
The discovery of a hack targeting eSIM profiles and their underlying secure elements represents a serious challenge to mobile security. As our lives increasingly move online and depend on the integrity of our phone identities, vulnerabilities like this underscore the constant need for vigilance and innovation in cybersecurity. Telecommunication providers and device manufacturers must act swiftly to patch these critical flaws, while users must adopt stronger security practices to protect themselves from potential identity theft and fraud.





