New IAmAntimalware Tool Injects Malicious Code Into Processes Of Popular Antiviruses
Recent developments in the cybersecurity landscape have unveiled a concerning new threat: the IAmAntimalware tool. This sophisticated utility, designed to subvert the very software intended to protect systems, injects malicious code directly into the processes of popular antivirus solutions. This novel approach turns trusted security mechanisms into potential vectors for attack, raising serious questions about the integrity of endpoint protection.
IAmAntimalware: A Deep Dive into Its Modus Operandi
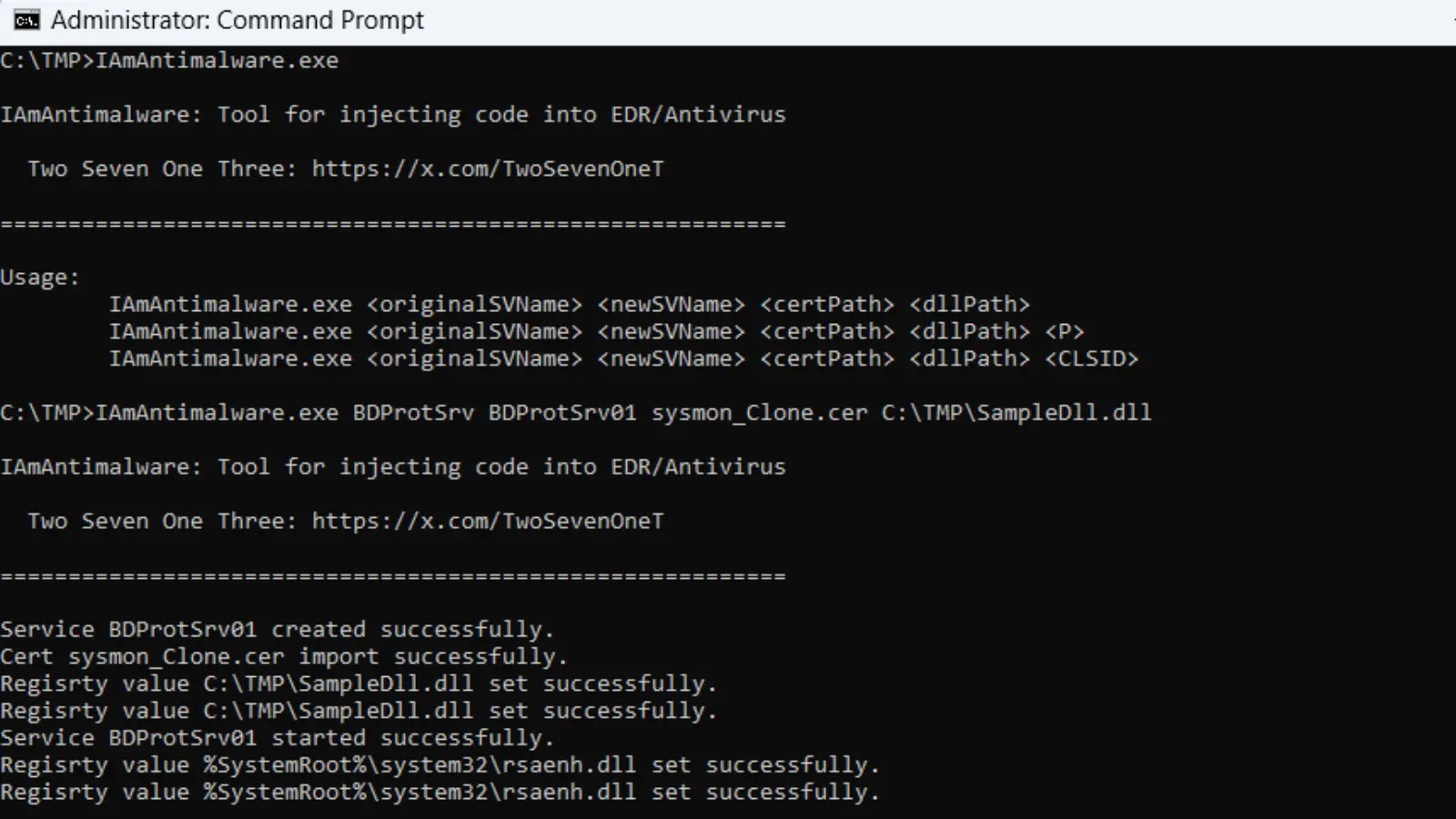
Developed by Two Seven One Three and released on GitHub on October 11, 2025, IAmAntimalware represents a significant evolution in evasion techniques. Its core functionality revolves around injecting arbitrary malicious code into running antivirus processes. This isn’t merely about disabling an antivirus; it’s about weaponizing it against the very system it’s meant to defend.
The tool leverages a combination of advanced techniques to achieve its objectives:
- Windows Service Cloning: IAmAntimalware utilizes Windows service cloning to create a replica of a legitimate antivirus service. This allows it to mimic the behavior and permissions of the original service, making its malicious activities harder to detect.
- Digital Signature Manipulation: Bypassing antivirus self-protection mechanisms often requires sophisticated methods. IAmAntimalware achieves this through digital signature manipulation, tricking the system into believing its injected code is legitimate and originating from the trusted antivirus vendor. This circumvents signature-based detection and self-defense integrity checks.
The implications of such a tool are profound. An attacker successfully deploying IAmAntimalware could gain deep access and control over a compromised system, rendering traditional endpoint security ineffective. The compromised antivirus itself could then be used for data exfiltration, lateral movement, or further malware deployment, all masquerading under the guise of a trusted security application.
The Threat Landscape: Why This Matters
This development underscores a critical vulnerability in how some security products operate. By targeting the antivirus process directly, IAmAntimalware challenges the fundamental assumptions of endpoint security. If an attacker can control the security software, they effectively control the entire system, potentially bypassing even the most robust defenses.
This type of attack is particularly insidious because it preys on trust. Users and administrators alike rely on antivirus software to be the last line of defense. When that trust is breached at such a fundamental level, the integrity of an organization’s entire security posture is called into question. It highlights the need for a multi-layered security approach that doesn’t solely rely on a single endpoint protection solution.
Remediation Actions and Proactive Defense
While the specifics of IAmAntimalware exploit novel techniques, organizations can implement several proactive measures to mitigate the risk and enhance their overall security posture:
- Implement Least Privilege: Ensure that all services, including antivirus processes, operate with the absolute minimum privileges required for their function. This limits the potential damage if an attacker manages to compromise a service.
- Advanced Endpoint Detection and Response (EDR): EDR solutions provide deeper visibility into endpoint activities than traditional antivirus. They can detect anomalous behavior, process injection attempts, and suspicious interactions with legitimate processes that IAmAntimalware might generate.
- Operating System Hardening: Regularly apply security updates and patches to operating systems. Implement recommended security configurations, disable unnecessary services, and restrict access to critical system resources.
- Application Whitelisting: Restrict the execution of unauthorized applications to only those explicitly allowed. This can prevent unknown or malicious binaries from running, even if they manage to bypass initial security checks.
- Regular Security Audits: Conduct frequent security audits and penetration testing to identify weaknesses in your current security infrastructure and validate the effectiveness of your defense mechanisms.
- User Training and Awareness: Educate users about social engineering techniques and the importance of vigilance against phishing attempts, as initial compromise often relies on human factors.
- Network Segmentation: Segment your network to limit lateral movement if a system is compromised. This can contain an attack and prevent it from spreading throughout the organization.
Tools for Enhanced Detection and Mitigation
While IAmAntimalware is a new threat, several existing security tools can aid in detecting and mitigating similar types of advanced attacks:
| Tool Name | Purpose | Link |
|---|---|---|
| Sysinternals Process Explorer | Advanced process management, identifying suspicious process injection. | Process Explorer |
| Osquery | Operating system instrumentation, enabling SQL-powered queries into OS data for threat hunting. | Osquery |
| YARA | Pattern matching for malware identification and classification. | YARA |
| Mandiant RedLine | Host investigative tool for compromise assessment. | RedLine |
| Microsoft Defender for Endpoint | Comprehensive EDR capabilities for detecting advanced threats and behaviors. | Microsoft Defender for Endpoint |
Conclusion
The emergence of tools like IAmAntimalware serves as a stark reminder that the battle for cybersecurity is constantly evolving. Attackers are increasingly resourceful, targeting not just the vulnerabilities in applications, but the fundamental trust placed in security software itself. Maintaining a robust security posture demands continuous vigilance, a multi-layered defense strategy, and a commitment to adapting to new and sophisticated threats. For further details on this development, the original report can be found at Cyber Security News.





