New Inboxfuscation Tool That Bypasses Microsoft Exchange Inbox Rules and Evade Detection
Unmasking Inboxfuscation: A Stealthy Threat to Microsoft Exchange Security
In the intricate landscape of enterprise security, the email inbox remains a prime target for adversaries. Microsoft Exchange, a cornerstone of corporate communication, has become a battleground where persistence and data exfiltration tactics constantly evolve. A recent development throws a new spotlight on this challenge: a sophisticated tool called Inboxfuscation. This innovative framework weaponizes a seemingly innocuous feature – Exchange inbox rules – to establish stealthy persistence and evade detection.
Developed by Permiso, Inboxfuscation demonstrates a powerful new technique for bypassing conventional security controls. This post will delve into how this tool operates, the threat it poses, and crucial steps organizations can take to defend against it.
The Evolution of Persistence: Why Inbox Rules Matter
Attackers are always seeking low-detection methods to maintain a foothold within compromised networks. Microsoft Exchange inbox rules, designed to automate email management, have become an increasingly popular vector. These rules allow users to automatically forward, move, or delete emails based on predefined criteria. For an attacker, an illicit inbox rule can:
- Maintain Persistence: Ensure continued access to a compromised mailbox, even if account credentials are changed or reset.
- Exfiltrate Data: Automatically forward sensitive emails containing confidential information to an external attacker-controlled address.
- Phishing Augmentation: Automatically delete or move legitimate security alerts, preventing users from seeing warnings.
The challenge has been creating these rules in a way that avoids immediate detection by security tools designed to flag suspicious rule configurations. This is precisely where Inboxfuscation introduces a significant escalation in attacker capabilities.
Inboxfuscation: Leveraging Unicode Obfuscation for Evasion
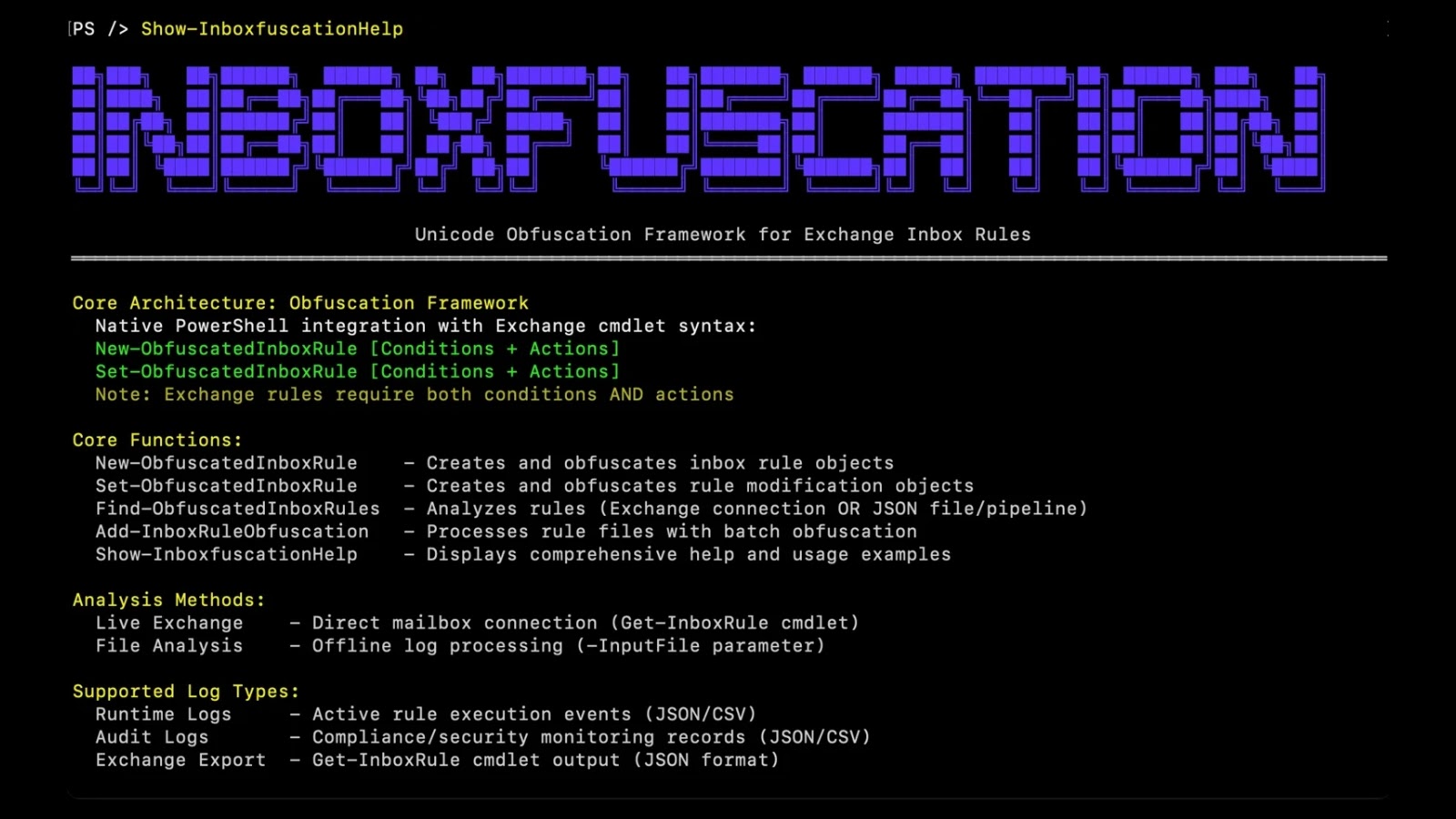
The core innovation behind Inboxfuscation lies in its use of Unicode-based obfuscation. Traditional security tools often rely on pattern matching and signature-based detection to identify malicious inbox rules. By crafting rule parameters using various Unicode characters that appear benign or even identical to legitimate ASCII characters, Inboxfuscation makes these rules incredibly difficult for automated systems to parse and flag as suspicious.
Consider a simple rule to forward emails to an external address. A standard malicious rule might contain the exact external email address in plain text. Inboxfuscation masks this by weaving in Unicode variations, making the rule’s true purpose opaque to security solutions looking for explicit strings. This technique allows attackers to:
- Create rules with seemingly legitimate-looking names that actually contain hidden malicious logic.
- Obfuscate target email addresses or folder names used for exfiltration.
- Bypass typical string-matching EDR and email security checks.
This method doesn’t exploit a specific software vulnerability in Exchange itself (like CVE-2021-26855 for ProxyLogon, for example). Instead, it weaponizes a legitimate feature through clever obfuscation, highlighting a broader trend in cybersecurity where attackers increasingly leverage features instead of pure vulnerabilities.
The Operational Impact: A Stealthy Backdoor
The implications of a tool like Inboxfuscation are significant. Imagine an attacker gains initial access through a phishing campaign. Instead of immediately moving laterally, they can deploy a stealthy Inboxfuscation-created rule. This rule could forward all emails from key executives to an external account, allowing passive intelligence gathering for months without detection. Alternatively, it could ensure that all incoming emails from a specific vendor are redirected, facilitating supply chain attacks.
The key danger is the longevity and stealth of these rules. They operate silently in the background, making them a persistent threat that is challenging to uncover without specific, targeted investigation.
For more technical details on the tool and its implementation, refer to the original source: New Inboxfuscation Tool That Bypasses Microsoft Exchange Inbox Rules and Evade Detection.
Remediation Actions and Detection Strategies
Defending against advanced rule-based attacks like those facilitated by Inboxfuscation requires a multi-layered approach. Organizations must move beyond simple signature-based detection and embrace deeper analysis of user behavior and rule configurations.
- Regular Audit of Mailbox Rules: Implement a robust and regular audit process for all user and administrator mailbox rules. Look for newly created rules, rules with unusual actions (e.g., forwarding to external domains), or rules created by non-administrative accounts.
- Baseline Normal Activity: Establish a baseline of normal inbox rule activity within your organization. Deviations from this baseline should trigger alerts. Tools that monitor Exchange mailbox configuration changes are crucial here.
- Enhanced Logging and Alerting: Ensure comprehensive logging for Exchange mailbox rule creation, modification, and deletion. Integrate these logs into your Security Information and Event Management (SIEM) system with correlation rules designed to flag suspicious activity.
- Implement Conditional Access Policies: Leverage Conditional Access policies in Microsoft 365 to restrict access to Exchange Online (and other services) based on device compliance, location, and other factors. This reduces the initial attack surface.
- Multi-Factor Authentication (MFA): Enforce MFA rigorously across all user accounts, especially those with elevated privileges. While MFA won’t prevent rule creation post-compromise, it significantly raises the bar for initial access.
- User Training: Educate users about the dangers of phishing and suspicious emails. A strong security culture is the first line of defense.
- Leverage Advanced Email Security Gateways: Employ email security solutions that can analyze email headers, content, and sender reputation for anomalies, potentially flagging suspicious rule-generated forwards.
Relevant Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft Defender for Office 365 | Advanced threat protection, including rule-based anomaly detection. | Official Page |
| PowerShell cmdlets (e.g., Get-InboxRule) | Scripting for auditing and managing Exchange mailbox rules. | Microsoft Learn |
| Mimecast/Proofpoint/Forcepoint | Email security gateways with advanced threat detection, including outbound email anomaly detection. | Mimecast / Proofpoint / Forcepoint |
| SIEM Solutions (e.g., Splunk, Microsoft Sentinel) | Centralized log management, correlation, and alerting for Exchange events. | Splunk / Microsoft Sentinel |
Key Takeaways for Enterprise Security
The emergence of Inboxfuscation underscores a critical shift in attacker methodologies. Threat actors are increasingly leveraging legitimate system functionalities and obfuscation techniques to achieve their objectives while sidestepping traditional security measures. For organizations relying on Microsoft Exchange, this development demands heightened vigilance.
Proactive auditing of mailbox rules, enhanced logging, continuous monitoring, and a strong emphasis on user education are no longer optional. They are essential components of a robust cybersecurity posture designed to detect and neutralize stealthy threats like Inboxfuscation before they lead to significant data breaches or sustained compromise.