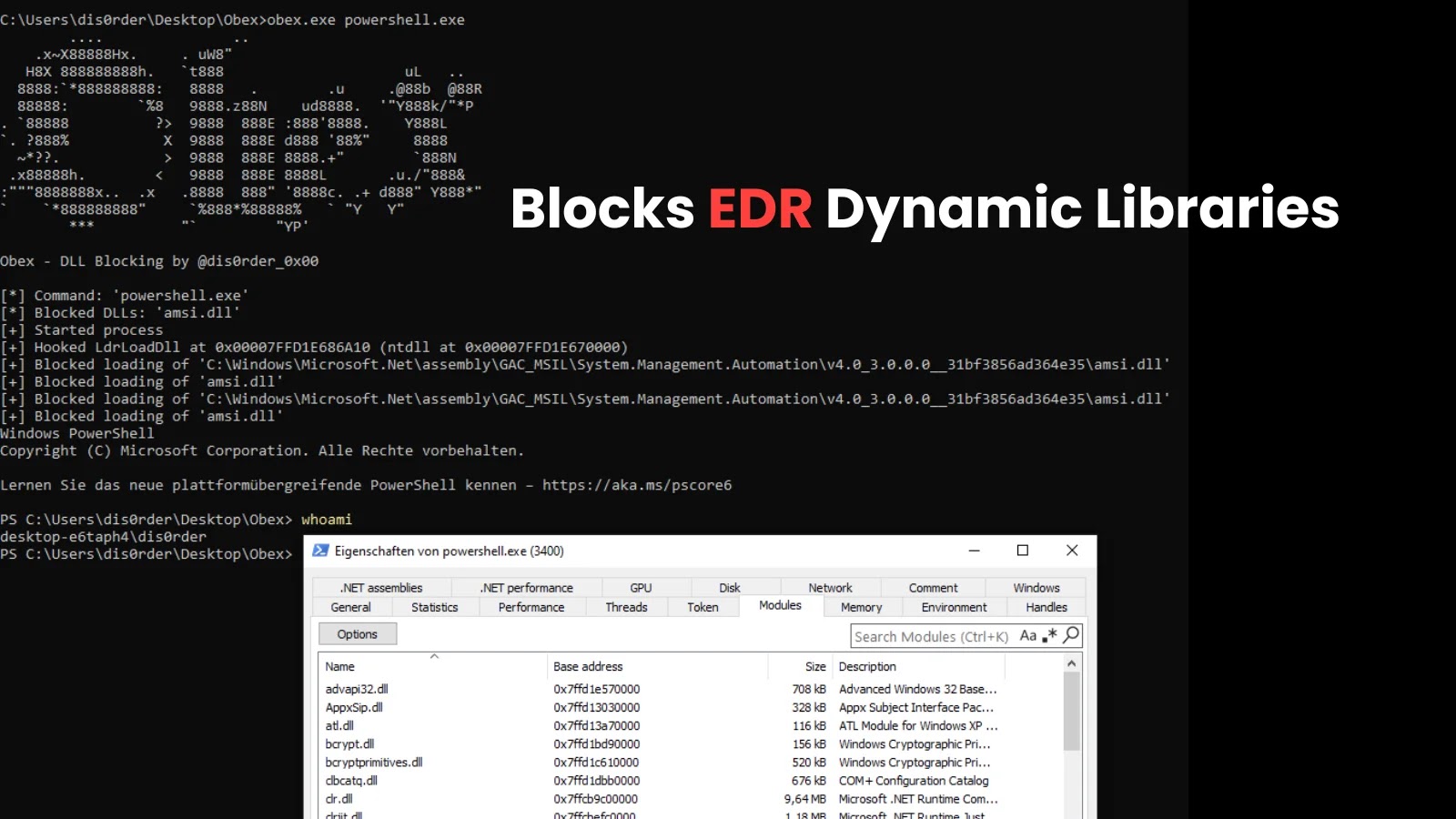
New Obex Tool Blocks EDR Dynamic Libraries From Loading at Runtime
Endpoint Detection and Response (EDR) solutions are a cornerstone of modern cybersecurity, designed to monitor endpoints for malicious activity and provide threat visibility. However, a newly unveiled proof-of-concept (PoC) tool named Obex is challenging the effectiveness of these defense mechanisms. Developed by researcher “dis0rder0x00,” Obex introduces a method to prevent EDR and other monitoring solutions’ dynamic-link libraries (DLLs) from loading into processes at runtime. This development has significant implications for enterprise security teams and demands a closer look.
Understanding Obex: Blocking EDR DLLs at Runtime
Obex functions by intercepting and blocking the loading of specified DLLs. Its primary target is the very mechanism EDR solutions use to inject their monitoring agents into running processes. By preventing these critical DLLs from initializing, Obex essentially blinds the EDR, rendering it incapable of detecting malicious activity within a compromised system. This technique is particularly concerning because it operates at a fundamental level, impacting the initial startup of a process as well as its ongoing execution.
The tool’s release signifies a potential shift in attacker tactics. Rather than attempting to bypass EDR detection rules, attackers could now aim to disable the EDR agent itself. This would allow them to operate with significantly less oversight, increasing the likelihood of successful exploits and data exfiltration.
How EDR Solutions Rely on Dynamic Link Libraries
To perform their extensive monitoring, EDR solutions typically inject custom DLLs into various processes running on an endpoint. These injected DLLs act as hooks, allowing the EDR agent to:
- Monitor API calls
- Track file system operations
- Observe network connections
- Detect suspicious process behavior
By preventing these critical DLLs from loading, Obex effectively severs the EDR’s connection to the processes it’s designed to protect. This creates a significant blind spot, making it challenging for security teams to identify and respond to threats.
The Impact on Enterprise Security and Threat Detection
The existence of tools like Obex presents a substantial challenge for cybersecurity professionals. If an attacker successfully deploys Obex, they can effectively operate under the radar, bypassing even the most sophisticated EDR systems. This could lead to:
- Undetected malware infections
- Prolonged dwell times for attackers
- Increased risk of data breaches and intellectual property theft
- Compromised system integrity
Organizations relying heavily on EDR as their primary line of defense might find themselves vulnerable to this new class of bypass techniques. It underscores the need for a multi-layered security approach that doesn’t solely depend on a single solution.
Remediation Actions and Mitigating the Threat
While Obex itself is a PoC tool, its underlying technique is a valid threat. Organizations must consider how to defend against such methods. Effective mitigation strategies include:
- Application Whitelisting: Implement strict application whitelisting policies to prevent unauthorized executables and DLLs from running. This can restrict what a malicious actor can execute, thereby limiting their ability to deploy tools like Obex.
- Principle of Least Privilege: Enforce the principle of least privilege across all user accounts and system processes. This minimizes the potential damage an attacker can inflict even if they manage to bypass EDR.
- Memory Integrity Protection: Modern operating systems offer memory integrity features (e.g., Windows HVCI) that can make it harder for unauthorized code to inject into processes or modify system behavior. Ensure these are enabled where possible.
- Behavioral Analytics Beyond EDR: Supplement EDR with other security tools that focus on network traffic analysis, log aggregation, and user behavior analytics (UBA). These tools might detect anomalies that an EDR blind spot would miss.
- Regular Security Audits: Conduct frequent security audits and penetration testing to identify weaknesses in your current security posture, including potential EDR bypasses.
- Endpoint Hardening: Implement robust endpoint hardening measures, including disabling unnecessary services, patching vulnerabilities, and configuring strong security settings.
- Supply Chain Security: Be vigilant about your software supply chain. Malicious DLLs could be introduced through compromised legitimate software, making it critical to trust sources and verify software integrity.
The Evolving Landscape of EDR Bypass Techniques
The release of Obex highlights an ongoing arms race between security vendors and malicious actors. As EDR solutions become more sophisticated, so too do the techniques used to circumvent them. This particular method of blocking DLL injection directly challenges the core functionality of many EDR systems. It’s crucial for security professionals to stay informed about these evolving threats and proactively adapt their defenses.
While there isn’t a specific CVE associated with Obex itself, as it’s a PoC tool demonstrating a technique, the underlying methods exploited by such tools often leverage system behaviors that could be considered vulnerabilities in specific contexts. For example, issues related to process injection or memory manipulation could be related to various system-level CVEs if they expose specific weaknesses.
Conclusion: Strengthening Defenses Against EDR Evasion
The Obex tool serves as a stark reminder that no single security solution is foolproof. Its ability to prevent EDR DLLs from loading at runtime poses a significant threat to endpoint visibility and detection capabilities. Organizations must move beyond solely relying on EDR and adopt a comprehensive, multi-layered security strategy. By combining robust endpoint hardening, application whitelisting, memory integrity protection, and advanced behavioral analytics, security teams can build a more resilient defense against sophisticated evasion techniques and ensure continuous protection against evolving cyber threats.





