New PHP-Based Interlock RAT Variant Uses FileFix Delivery Mechanism to Target Multiple Industries
Unveiling Interlock RAT’s New PHP Variant: A Deep Dive into FileFix Delivery and KongTuke Connections
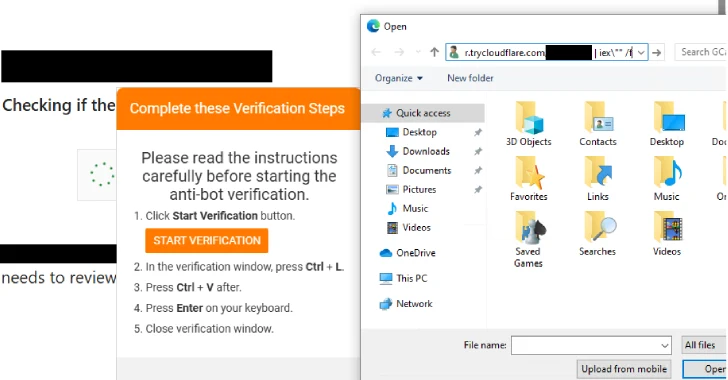
In the evolving threat landscape, understanding the latest tactics, techniques, and procedures (TTPs) of sophisticated threat actors is paramount for effective defense. A recent development highlights a significant shift in the operations of the Interlock ransomware nexus. Threat actors associated with Interlock have unleashed a formidable new PHP-based variant of their bespoke remote access trojan (RAT), delivered through a cunning mechanism dubbed FileFix.
This widespread campaign, leveraging a variant of the previously known ClickFix, signals a heightened threat to multiple industries. Security professionals and IT teams must grasp the intricacies of this new variant, its delivery mechanism, and its connections to existing threat clusters to bolster their defenses.
The New PHP-Based Interlock RAT Variant
The core of this emerging threat is a novel PHP variant of the Interlock RAT. While Interlock has a history of deploying potent ransomware, this new iteration focuses on remote access capabilities. The choice of PHP for the RAT’s development is noteworthy, as it offers several advantages to threat actors:
- Platform Agnosticism: PHP’s cross-platform compatibility allows the RAT to potentially operate across various operating systems where PHP interpreters are present, widening the attack surface.
- Evasion Potential: PHP-based malware can sometimes bypass traditional security tools that are less attuned to detecting compiled executables, making it harder to detect and analyze.
- Web-Centric Operations: Given PHP’s prevalence in web development, this variant likely facilitates web-based command and control (C2) communication, blending in more easily with legitimate web traffic.
This new variant’s capabilities likely extend to data exfiltration, system manipulation, and persistent access, consistent with the functionalities expected of a sophisticated RAT.
FileFix: The Evolved Delivery Mechanism
The delivery of this new Interlock RAT variant relies on a mechanism called FileFix. This is described as a variant of ClickFix, a known method for distributing malicious payloads. The evolution from ClickFix to FileFix suggests a refinement in the initial access phase of the attack chain. While precise technical details of FileFix are still emerging, its role is to ensure the successful download and execution of the PHP-based Interlock RAT onto compromised systems.
FileFix likely employs a combination of social engineering tactics, exploit kits, or malvertising to achieve initial compromise. Understanding the entry vectors associated with FileFix is crucial for implementing robust perimeter defenses and user awareness training.
Connections to LandUpdate808 (KongTuke) Web-Inject Threat Clusters
A critical piece of intelligence regarding this new campaign is its observed connection to the LandUpdate808 (aka KongTuke) web-inject threat clusters. The DFIR Report, a reputable source in cybersecurity incident response, highlighted that “Since May 2025, activity related to the Interlock RAT has been observed in connection with the LandUpdate808 (aka KongTuke) web-inject threat clusters.”
This linkage is significant for several reasons:
- Established Infrastructure: KongTuke is a known entity, implying that the Interlock threat actors are leveraging or collaborating with groups that possess established infrastructure for web-inject campaigns.
- Supply Chain Implications: Web-injects often target online banking portals or e-commerce sites, suggesting that businesses dealing with financial transactions or user data could be primary targets.
- Sophisticated Attack Chain: The combination of web-inject attacks with RAT deployment indicates a multi-stage, sophisticated attack chain designed for broad compromise and sustained access.
Organizations should review their web application security, especially in light of potential web-inject attacks, and ensure strong defenses against client-side tampering.
Targeted Industries and Impact
While the source information indicates the campaign targets “multiple industries,” the connection to web-injects (specifically LandUpdate808/KongTuke) strongly suggests a focus on sectors where online financial transactions or sensitive data handling are prevalent. This includes:
- Financial Institutions (banks, credit unions)
- E-commerce and Retail
- Healthcare (patient portals, billing systems)
- Any organization handling sensitive user credentials or payment information
The impact of a successful Interlock RAT compromise can be severe, ranging from data breaches and financial fraud to complete network compromise and the eventual deployment of ransomware.
Remediation Actions and Proactive Security Measures
Defending against advanced threats like the new PHP-based Interlock RAT requires a multi-layered security strategy. Organizations should prioritize the following actions:
- Endpoint Detection and Response (EDR): Implement robust EDR solutions that can detect anomalous process behavior, fileless attacks, and suspicious network connections indicative of RAT activity.
- Network Segmentation: Limit lateral movement by segmenting networks, isolating critical assets, and enforcing strict access controls.
- Principle of Least Privilege: Ensure users and applications operate with the minimum necessary permissions to perform their functions.
- Web Application Firewall (WAF): Deploy and configure WAFs to detect and block web-based attacks, including potential web-inject attempts associated with KongTuke.
- Regular Patch Management: Keep all operating systems, applications, and web servers updated to patch known vulnerabilities. This is crucial for preventing exploitation via FileFix delivery mechanisms.
- Email and Web Gateway Security: Enhance security at the perimeter to filter out malicious emails and block access to known malicious websites that might host FileFix payloads.
- User Awareness Training: Educate employees about phishing, social engineering, and the dangers of clicking on suspicious links or downloading untrusted files.
- Threat Intelligence Integration: Subscribe to and integrate threat intelligence feeds, especially those related to Interlock, FileFix, and KongTuke activities, to enhance detection capabilities.
- Regular Backups: Maintain immutable, off-site backups of critical data to ensure recovery in the event of a successful ransomware or data destruction attack.
While no specific CVEs have been publicly assigned directly to this new Interlock RAT variant as of this analysis, organizations should proactively address vulnerabilities that enable initial access. Common weaknesses often exploited include unpatched software (e.g., CVE-2023-38831, a commonly exploited WinRAR vulnerability, or CVE-2023-28252, a critical vulnerability in Microsoft Exchange) and misconfigurations. Staying abreast of the latest CVE advisories is essential.
| Tool Name | Purpose | Link |
|---|---|---|
| Snort/Suricata | Network Intrusion Detection System (NIDS) for detecting malicious traffic patterns. | https://www.snort.org/ or https://suricata.io/ |
| YARA Rules | Pattern matching signatures for identifying malware families across various files. | https://virustotal.github.io/yara/ |
| OWASP ModSecurity Core Rule Set (CRS) | Generic attack detection for Web Application Firewalls (WAFs). | https://coreruleset.org/ |
| Velociraptor | Open-source endpoint visibility and analysis platform for incident response. | https://docs.velociraptor.app/ |
| MISP (Malware Information Sharing Platform) | Threat intelligence platform for sharing, storing, and correlating indicators of compromise (IoCs). | https://www.misp-project.org/ |
Conclusion
The emergence of a new PHP-based Interlock RAT variant, delivered via FileFix and linked to KongTuke web-inject clusters, underscores the dynamic nature of cyber threats. This development highlights the Interlock group’s continued evolution and their sophisticated approach to targeting and compromising organizations. Staying vigilant, implementing robust security controls, and fostering a strong security posture are not merely best practices but critical necessities in this ever-challenging digital landscape. Proactive threat hunting, continuous monitoring, and a rapid incident response capability will be key to defending against this advanced threat.





