New PoC Exploit Released for Sudo Chroot Privilege Escalation Vulnerability
Sudo Chroot Privilege Escalation: A Critical Warning for Linux Administrators
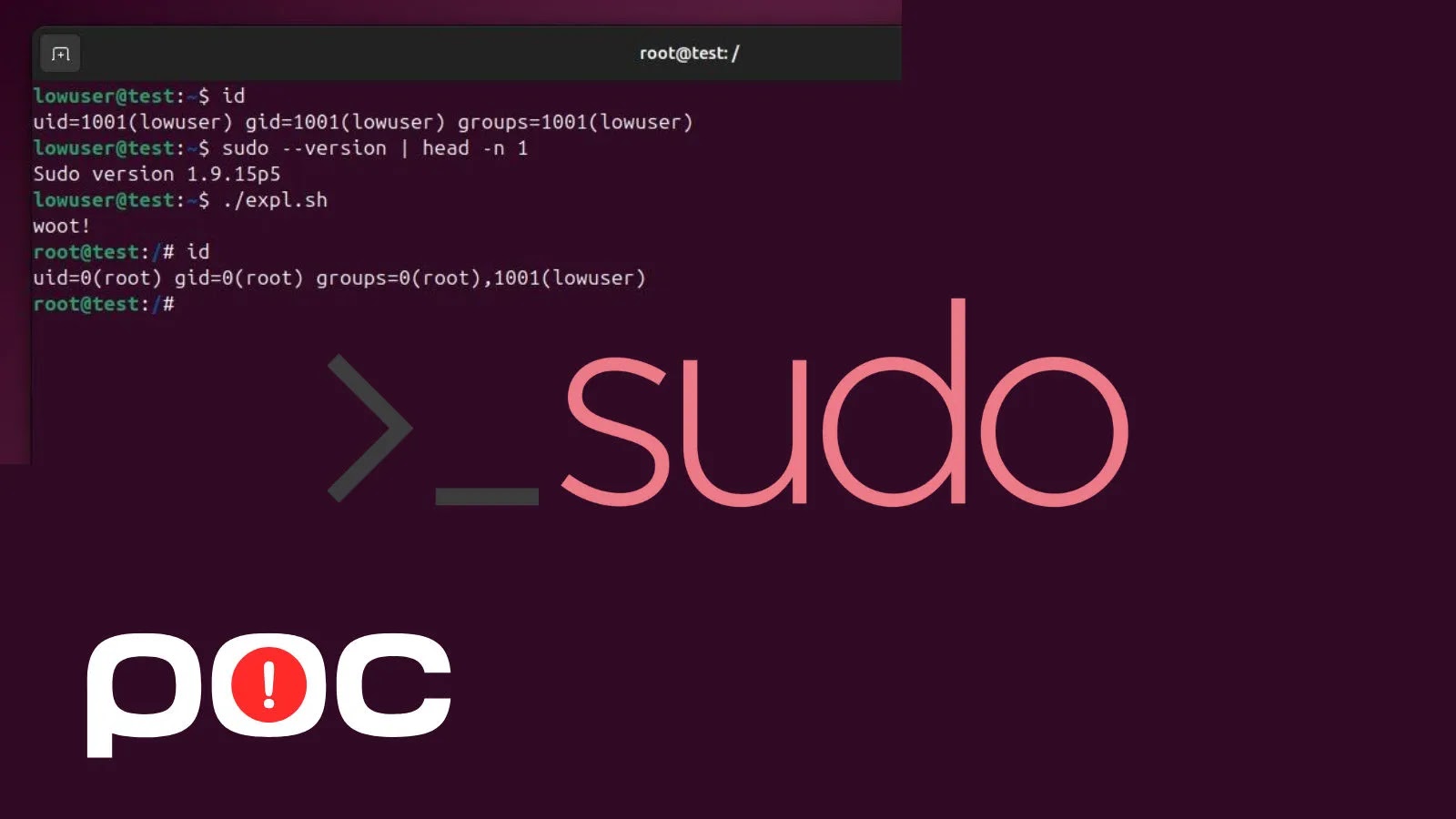
A significant cybersecurity alert is sounding across the Linux ecosystem. A critical vulnerability within the widely used Sudo utility, specifically targeting its chroot feature, has been exposed with the public release of a proof-of-concept (PoC) exploit. This development immediately escalates the threat level, demanding urgent attention from system administrators globally. The vulnerability, tracked as CVE-2025-32463, carries the potential for local attackers to effortlessly achieve root-level privileges on affected systems.
Understanding the Sudo Chroot Vulnerability (CVE-2025-32463)
The core of this vulnerability lies within Sudo versions 1.9.14 through 1.9.17. Sudo, an indispensable tool for allowing authorized users to execute commands as another user (typically the superuser root), employs the chroot command to isolate processes within a restricted directory environment. This isolation is crucial for security, preventing a compromised application from affecting the entire system. However, the identified flaw in these specific Sudo versions allows a local attacker, who already possesses some level of access on the system, to bypass the intended isolation of the chroot environment. By exploiting this weakness, the attacker can break out of the confined directory and execute arbitrary code with root privileges.
The severity of this issue is amplified by the availability of a public PoC exploit. This means that the technical knowledge required to leverage this vulnerability is readily accessible, significantly lowering the barrier for potential attackers. The vulnerability was initially identified and disclosed by a security researcher, whose findings have now materialized into an actionable exploit.
Impact of Privilege Escalation
A successful privilege escalation to root is one of the most critical outcomes for a cyberattack. With root privileges, an attacker gains complete control over a Linux system. This includes, but is not limited to:
- Data Exfiltration: Accessing, copying, or deleting any data on the system.
- System Compromise: Installing malicious software, creating new user accounts, modifying system configurations, or establishing persistent backdoors.
- Network Pivoting: Using the compromised system as a launchpad for further attacks within the network.
- Denial of Service: Shutting down critical services or the entire system.
Given the widespread use of Sudo across virtually all Linux distributions in server environments, workstations, and even embedded systems, the potential impact of CVE-2025-32463 is substantial. Any system running the affected Sudo versions is at severe risk if a local attacker is present.
Remediation Actions
Immediate action is crucial to mitigate the risk posed by CVE-2025-32463. System administrators must prioritize these steps:
- Upgrade Sudo: The most effective remediation is to update Sudo to a patched version that addresses this vulnerability. Administrators should consult their distribution’s repositories for the latest available Sudo packages. Vendors typically release security updates promptly for such critical flaws.
- Apply Security Patches: Regularly apply all security updates to your operating system and installed software.
- Least Privilege Principle: Enforce the principle of least privilege rigorously. Ensure users and services only have the minimum necessary permissions to perform their functions.
- Monitor System Logs: Implement robust logging and monitoring for Sudo activities and unexpected system behavior. Look for unusual privilege escalation attempts or unauthorized access.
- Security Audits: Conduct regular security audits and penetration tests to identify and address potential weaknesses before they can be exploited.
Detection and Mitigation Tools
While direct detection tools for this specific exploit might not be widely available immediately, a range of general cybersecurity tools can aid in overall system hardening and incident response:
| Tool Name | Purpose | Link |
|---|---|---|
| OSSEC | Host-based Intrusion Detection System (HIDS) for log analysis, file integrity monitoring, and rootkit detection. | https://www.ossec.net/ |
| Lynis | Security auditing tool for Linux, Unix, and macOS. Scans for security configuration weaknesses. | https://cisofy.com/lynis/ |
| Tripwire | File integrity monitoring (FIM) tool to detect unauthorized changes to critical system files. | https://www.tripwire.com/ |
| Security Information and Event Management (SIEM) Solutions | Centralized logging and analysis platforms (e.g., Splunk, ELK Stack, QRadar) for anomaly detection. | (Varies by vendor) |
Conclusion
The release of a PoC exploit for CVE-2025-32463 represents a significant threat to Linux systems utilizing vulnerable Sudo versions. This critical privilege escalation flaw highlights the ongoing importance of diligent patching, adherence to security best practices, and continuous monitoring. Organizations must act swiftly to update their systems and safeguard against potential exploitation, ensuring the integrity and security of their Linux environments.





