New Salty 2FA PhaaS platform Attacking Microsoft 365 Users to Steal Login Credentials
The Rise of Salty 2FA: A New PhaaS Threat Targeting Microsoft 365 Users
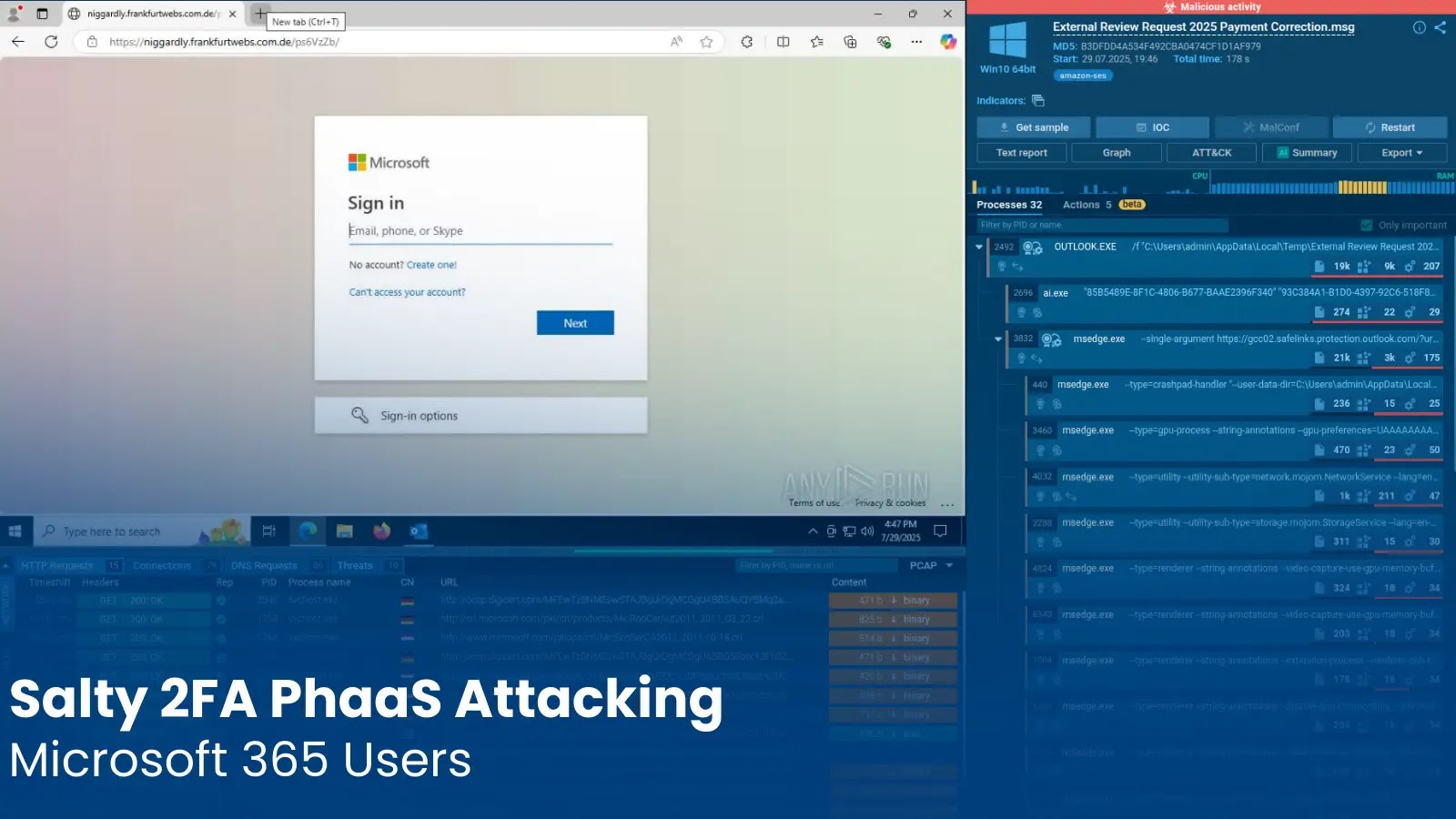
In the evolving landscape of cyber threats, a sophisticated new player has emerged, specifically targeting Microsoft 365 users across vital industries in the US and Europe. Dubbed “Salty 2FA,” this previously undocumented Phishing-as-a-Service (PhaaS) platform represents a significant leap in credential theft tactics, designed to expertly bypass two-factor authentication (2FA) mechanisms. As a cybersecurity analyst, recognizing and understanding the intricacies of such frameworks is paramount to defending organizational assets.
Understanding the Salty 2FA PhaaS Platform
Salty 2FA is not just another phishing kit; it’s a meticulously crafted PhaaS solution. This means it provides a comprehensive, ready-to-deploy infrastructure for malicious actors, lowering the barrier to entry for sophisticated phishing campaigns. Its primary target: stealing corporate login credentials from Microsoft 365 environments. The platform’s efficacy lies in its ability to circumvent 2FA, a security measure often considered the last line of defense against account takeover.
Advanced Evasion Techniques Employed by Salty 2FA
What sets Salty 2FA apart are its advanced obfuscation techniques and multi-stage execution chains. These methods are designed to:
- Evade Detection: By obscuring its malicious intent, Salty 2FA makes it significantly harder for traditional security solutions, such as email filters and endpoint detection systems, to identify and block the attack.
- Bypass 2FA: The platform is specifically engineered to intercept and relay 2FA codes or session tokens, granting attackers unauthorized access even when users have 2FA enabled. This often involves real-time proxying of user sessions.
- Steal Credential: Once the 2FA is bypassed, the platform harvests corporate credentials, giving attackers a foothold into the victim’s Microsoft 365 ecosystem.
These combined capabilities make Salty 2FA a formidable threat, capable of compromising accounts that would typically be considered secure.
Targeted Industries and Potential Impact
The attackers behind Salty 2FA are not indiscriminate. Initial intelligence indicates a focused targeting of organizations within critical sectors, including:
- Finance: Access to financial systems and sensitive customer data.
- Telecommunications: Potential for network disruption or access to communication data.
- Energy: High-impact targets with potential for operational technology (OT) disruption.
A successful breach in any of these sectors could lead to significant financial losses, data breaches, reputational damage, and even broader systemic risks. The ability to compromise Microsoft 365 accounts means attackers could gain access to sensitive emails, cloud storage, collaborative tools, and internal applications, leading to further lateral movement within an organization’s network.
Remediation Actions and Protective Measures
Defending against advanced PhaaS platforms like Salty 2FA requires a multi-layered and proactive cybersecurity strategy. Organizations leveraging Microsoft 365 should immediately review and strengthen their security posture. While there isn’t a specific CVE for Salty 2FA itself (as it’s a platform, not a single vulnerability), its effectiveness often relies on exploiting human error or misconfigurations that security teams can address.
Recommended Mitigation Strategies:
- Strengthen Authentication Protocols:
- Implement FIDO2/hardware-based security keys (e.g., YubiKey) as the primary 2FA method. These methods are highly resistant to phishing as they rely on cryptographic challenge-response mechanisms tied to the physical device.
- Avoid SMS-based 2FA where possible, as it is susceptible to SIM swapping and other interception techniques.
- Utilize app-based authenticators with number matching features for enhanced security.
- Employee Education and Awareness Training:
- Conduct regular, realistic phishing simulations to train employees to recognize and report suspicious emails.
- Educate users on the dangers of clicking unknown links, verifying sender legitimacy, and the importance of reporting any unusual login prompts.
- Highlight the specific tactics used by sophisticated phishing campaigns, such as those impersonating legitimate services.
- Enhanced Email Security:
- Deploy advanced email security gateways (ESG) capable of detecting and blocking sophisticated phishing attempts, including those utilizing URL manipulation, brand impersonation, and obfuscated content.
- Utilize DMARC, DKIM, and SPF records to prevent email spoofing and ensure the authenticity of incoming emails.
- Endpoint Detection and Response (EDR)/Extended Detection and Response (XDR):
- Implement EDR/XDR solutions across all endpoints to detect anomalous behavior, suspicious process execution, and credential theft attempts in real-time.
- Configure EDR rules to flag activities commonly associated with phishing attacks and post-exploitation.
- Conditional Access Policies in Microsoft 365:
- Implement robust Conditional Access policies to restrict access based on user location, device compliance, and sign-in risk levels.
- Enforce multi-factor authentication for all sensitive applications and for users accessing resources from untrusted networks.
- Regular Security Audits and Monitoring:
- Conduct regular audits of Microsoft 365 configurations and user activity logs to identify suspicious login attempts, unauthorized access, or policy violations.
- Monitor for unusual patterns of data access or changes in user behavior.
Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft 365 Defender | Comprehensive threat protection, EDR, email security, identity protection for Microsoft 365. | Link |
| Proofpoint / Mimecast / Cofense (ESG) | Advanced Email Security Gateway solutions for phishing detection and email threat protection. | Proofpoint / Mimecast / Cofense |
| YubiKey (FIDO2) | Hardware security keys for phishing-resistant multi-factor authentication. | Link |
| KnowBe4 / SANS Security Awareness | Security awareness training platforms for developing human firewalls. | KnowBe4 / SANS |
| Microsoft Entra ID Protection (formerly Azure AD Identity Protection) | Automated detection and remediation of identity-based risks. | Link |
Conclusion: Staying Ahead of Phishing Evolution
The emergence of Salty 2FA underscores a critical trend in cybercrime: the continuous evolution of phishing tactics to bypass traditional security controls, particularly 2FA. For organizations leveraging Microsoft 365, a proactive and adaptive security posture is non-negotiable. This includes investing in phishing-resistant authentication methods, rigorous employee training, advanced email and endpoint security solutions, and vigilant monitoring. By understanding the sophisticated nature of threats like Salty 2FA and implementing robust defenses, security teams can significantly reduce their attack surface and protect valuable corporate assets from credential theft.





