New Scanner Released to Detect SharePoint Servers Vulnerable to 0-Day Attack
Urgent Action Required: New Scanner Detects SharePoint Servers Vulnerable to Critical 0-Day Exploit
The cybersecurity landscape has been rocked by the discovery of an actively exploited zero-day vulnerability in Microsoft SharePoint, designated as CVE-2025-53770. This unauthenticated Remote Code Execution (RCE) flaw poses a severe risk to organizations leveraging SharePoint for their operations. In a rapid response to this critical threat, an open-source scanning tool has been released, empowering IT and security teams to quickly identify vulnerable SharePoint servers within their infrastructure. Proactive detection is paramount in mitigating the immediate danger posed by this in-the-wild exploitation.
Understanding CVE-2025-53770: A Critical SharePoint Zero-Day
The newly identified vulnerability, CVE-2025-53770, is an unauthenticated Remote Code Execution flaw. This means that an attacker can execute arbitrary code on a vulnerable SharePoint server without needing any authentication credentials. The “zero-day” designation indicates that the vendor (Microsoft, in this case) was unaware of the vulnerability, or a patch was not yet available, when the exploit was first discovered and used in attacks. The fact that this vulnerability is being “actively exploited in the wild” underscores the immediate and severe risk it presents to organizations globally. An RCE vulnerability allows attackers to gain full control over the compromised system, potentially leading to data exfiltration, service disruption, or further network penetration.
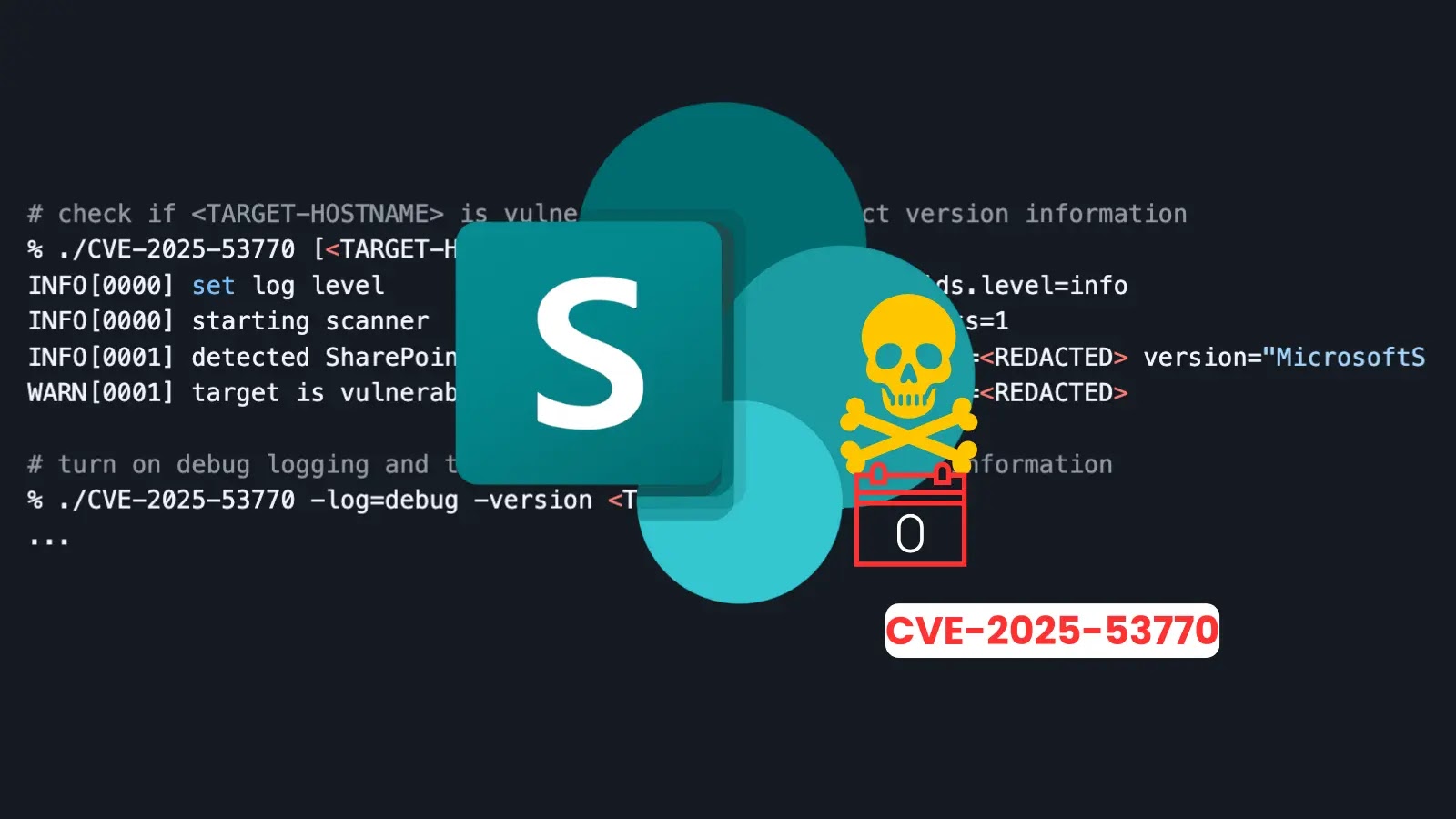
Introducing the Open-Source SharePoint Vulnerability Scanner
In response to the urgent threat posed by CVE-2025-53770, an open-source scanning tool has been made available on GitHub. This tool is designed to allow organizations to rapidly assess their SharePoint environments for susceptibility to this specific zero-day RCE. The release of such a scanner is a crucial development, as it democratizes the ability to detect and respond to novel threats, especially when official patches might still be in development or rollout phases. Security teams can now download and deploy this tool to pinpoint vulnerable instances, enabling targeted remediation efforts.
Why Proactive Scanning is Essential
The active exploitation of CVE-2025-53770 necessitates immediate action. Relying solely on signature-based Intrusion Detection Systems (IDS) or traditional antivirus software may not be sufficient against zero-day exploits. Proactive scanning with purpose-built tools provides a direct method to identify exposed assets before they are compromised. This is particularly vital for SharePoint servers, which often store sensitive organizational data, act as central collaboration hubs, and can represent a critical entry point into an enterprise network.
Remediation Actions for CVE-2025-53770
Upon identifying vulnerable SharePoint servers using the new scanner, immediate remediation is critical. While a definitive patch from Microsoft may be pending, the following actions are recommended:
- Isolate Vulnerable Servers: Where possible, temporarily remove or restrict network access to identified vulnerable SharePoint servers until a patch is applied or other mitigations are in place.
- Apply Vendor Patches: Monitor official Microsoft security advisories and promptly apply any released patches for CVE-2025-53770 as soon as they become available. Prioritize critical production systems.
- Implement Network Segmentation: Ensure SharePoint servers are properly segmented from the rest of the network to limit lateral movement in case of compromise.
- Strengthen Access Controls: Review and tighten access controls for SharePoint environments. Implement the principle of least privilege.
- Deploy Web Application Firewalls (WAFs): Configure WAFs to detect and block suspicious requests targeting SharePoint. While not a guaranteed solution for zero-days, WAFs can add a layer of protection.
- Monitor Logs for Anomalies: Increase vigilance on SharePoint and system logs for any unusual activity,
such as suspicious file modifications, unauthorized access attempts, or unusual process executions. - Backup Critical Data: Ensure comprehensive and recent backups of SharePoint data are maintained and can be rapidly restored.
Essential Tools for SharePoint Security and Vulnerability Management
| Tool Name | Purpose | Link |
|---|---|---|
| SharePoint CVE-2025-53770 Scanner | Detects specific vulnerability CVE-2025-53770 | [Refer to official source for GitHub link] |
| Nessus / OpenVAS | General vulnerability scanning of network devices and applications. | Tenable Nessus / OpenVAS |
| Microsoft Defender for Endpoint | Endpoint detection and response (EDR) for threat detection and response. | Microsoft Defender for Endpoint |
| OWASP ZAP | Web application security scanner for identifying vulnerabilities. | OWASP ZAP |
Key Takeaways for Securing SharePoint
The release of a dedicated scanner for CVE-2025-53770 highlights the immediate need for vigilance regarding SharePoint security. Organizations must:
- Utilize the new open-source scanner to identify vulnerable SharePoint servers without delay.
- Prioritize the application of any official patches from Microsoft for CVE-2025-53770 as soon as they are released.
- Implement layered security controls, including network segmentation, robust access management, and WAFs.
- Maintain continuous monitoring of SharePoint environments for suspicious activity.
- Stay informed about emerging threats and zero-day vulnerabilities affecting critical business applications.





