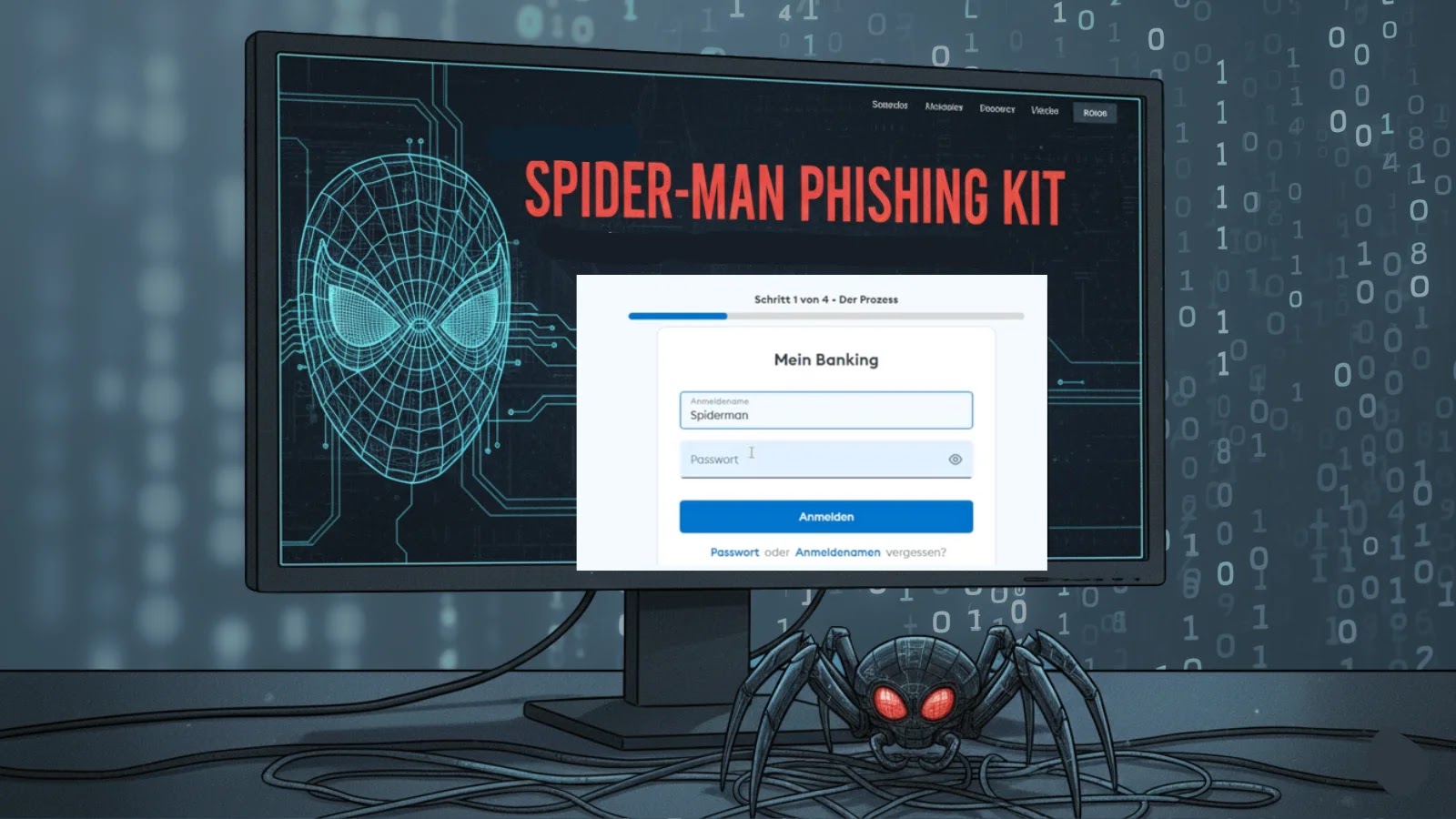
New Spiderman Phishing Kit Lets Attackers Create Malicious Bank Login Pages in Few Clicks
In the relentless cat-and-mouse game of cybersecurity, new threats constantly emerge, lowering the bar for malicious actors and expanding their reach. A sophisticated new phishing framework, aptly named “Spiderman,” has recently surfaced in the cybercrime underground, significantly simplifying the process of launching financial fraud campaigns. This innovative toolkit empowers threat actors, even those with minimal technical expertise, to rapidly deploy pixel-perfect replicas of legitimate banking portals. This development marks a concerning escalation in the ease with which attackers can target unsuspecting individuals and organizations.
The Rise of the Spiderman Phishing Kit
First observed and reported by cybersecurity firm Varonis, the Spiderman phishing kit represents a significant advancement in the tools available to cybercriminals. Unlike older, more technically demanding phishing methods, Spiderman is designed for ease of use, enabling even novice attackers to launch highly convincing phishing attacks. This kit specializes in creating high-fidelity duplicates of banking login pages, making it exceedingly difficult for victims to discern legitimate sites from malicious ones.
The core innovation of the Spiderman kit lies in its ability to streamline the creation and deployment of these deceptive pages. Threat actors can, with just a few clicks, configure and activate a phishing campaign that mirrors the branding and user experience of prominent financial institutions. This automation drastically reduces the time and technical skill required to initiate such attacks, broadening the pool of potential attackers and increasing the overall volume of phishing attempts.
How the Spiderman Kit Works
The operational efficiency of the Spiderman phishing kit is a key factor in its danger. Here’s a breakdown of its typical workflow:
- Template Generation: The kit provides pre-built templates or robust customization options to generate fraudulent login pages that precisely mimic targeted banking websites. These templates often include legitimate-looking URLs and even dynamic content to enhance their credibility.
- Credential Harvesting: Once a victim enters their login credentials (username, password, multi-factor authentication codes) into the fake portal, the Spiderman kit captures this information.
- Redirection: After harvesting the data, the kit often redirects the victim to the actual legitimate banking website, creating a seamless experience that minimizes suspicion. This makes it harder for victims to immediately realize they’ve been compromised.
- Data Exfiltration: The stolen credentials are then securely transmitted to the attacker, often via encrypted channels, for later use in account takeovers or other fraudulent activities.
The toolkit’s modular design and user-friendly interface are crucial elements. It effectively abstracts away the complexities of web development and server management, allowing attackers to focus solely on campaign deployment and credential harvesting.
Impact on Financial Institutions and Customers
The proliferation of sophisticated phishing kits like Spiderman poses a considerable threat to both financial institutions and their customers. For banks, such attacks can lead to:
- Reputational Damage: Successful phishing campaigns erode customer trust and can significant harm a bank’s reputation.
- Financial Losses: Banks may incur direct financial losses through fraud, customer reimbursement, and increased cybersecurity incident response costs.
- Increased Security Burden: Financial institutions must continuously invest in advanced detection and prevention mechanisms to stay ahead of evolving phishing techniques.
For customers, the consequences are even more immediate and severe:
- Financial Theft: Compromised banking credentials can lead to unauthorized transactions, draining accounts and causing significant financial distress.
- Identity Theft: Stolen banking information can be used to facilitate broader identity theft, opening new accounts, or securing loans in the victim’s name.
- Emotional Distress: The experience of falling victim to financial fraud can be highly stressful and time-consuming to resolve.
Remediation Actions and Prevention Strategies
Combating sophisticated phishing kits like Spiderman requires a multi-layered approach involving both technical safeguards and user education. No specific CVE number is associated with the Spiderman phishing kit itself, as it is a toolkit rather than a specific vulnerability in a product or service. However, the kit exploits general human vulnerabilities and the trust users place in legitimate websites.
For Financial Institutions:
- Advanced Threat Detection: Implement robust email security gateways, anti-phishing solutions, and anomaly detection systems that can identify and block malicious URLs and suspicious email activity.
- Continuous Monitoring: Proactively monitor DMARC, SPF, and DKIM records to prevent email spoofing of your domains. Utilize threat intelligence feeds to stay informed about new phishing kits and tactics.
- Enhanced Authentication: Advocate for and implement strong multi-factor authentication (MFA) for all online banking services. Consider FIDO2/WebAuthn for phishing-resistant MFA.
- User Education Campaigns: Regularly educate customers on identifying phishing attempts, emphasizing the importance of verifying URLs, looking for padlocks, and never clicking suspicious links.
- Rapid Incident Response: Develop and regularly test a comprehensive incident response plan for phishing attacks, including procedures for identifying compromised accounts, freezing funds, and notifying affected customers.
For Individual Users:
- Verify URLs Carefully: Always check the URL in your browser’s address bar. Look for “https://” and the padlock icon. Be wary of subtle misspellings or unusual domain extensions.
- Never Click Suspicious Links: Avoid clicking links in emails or text messages, especially those requesting sensitive information. Instead, type the bank’s legitimate URL directly into your browser.
- Use Strong, Unique Passwords and MFA: Employ strong, unique passwords for all online accounts, especially banking. Enable multi-factor authentication (MFA) whenever possible for an added layer of security.
- Monitor Bank Statements: Regularly review your bank statements and transaction history for any unfamiliar activity. Report suspicious transactions immediately to your bank.
- Educate Yourself: Stay informed about common phishing tactics. Recognize that legitimate financial institutions will rarely ask for sensitive information via email or text.
Detection and Prevention Tools
While the Spiderman kit is a broad threat, several categories of tools can assist in detection and prevention against its various attack vectors.
| Tool Category | Purpose | Examples/Approach |
|---|---|---|
| Email Security Gateways | Filters out phishing emails before they reach inboxes. | Mimecast, Proofpoint, Microsoft Defender for Office 365. |
| Web Application Firewalls (WAFs) | Protects web applications from various attacks, including some forms of content injection used in phishing. | Cloudflare WAF, Akamai Kona Site Defender, AWS WAF. |
| Endpoint Detection & Response (EDR) | Detects and responds to malicious activity on user endpoints, even if a user falls victim. | CrowdStrike Falcon, SentinelOne, Microsoft Defender for Endpoint. |
| Anti-Phishing Training Platforms | Educates users to recognize and report phishing attempts. | KnowBe4, Cofense, PhishER. |
| Browser Extensions/Security Features | Provides real-time warnings about suspicious websites. | Google Safe Browsing, Netcraft Anti-Phishing Extension. |
Conclusion
The emergence of the Spiderman phishing kit underscores a critical shift in the landscape of cybercrime – the democratization of sophisticated attack tools. Its ability to enable attackers of all skill levels to launch highly convincing financial phishing campaigns presents a significant challenge to both financial institutions and individuals worldwide. Remaining vigilant, fostering a culture of cybersecurity awareness, and deploying robust technical safeguards are no longer optional but essential. By understanding the mechanisms of such kits and proactively implementing protective measures, we can collectively build stronger defenses against this evolving threat.





