New Udados Botnet Launches Massive HTTP Flood DDoS Attacks Targeting Tech Sector
Unmasking Udados: A New Botnet’s Assault on the Tech Sector
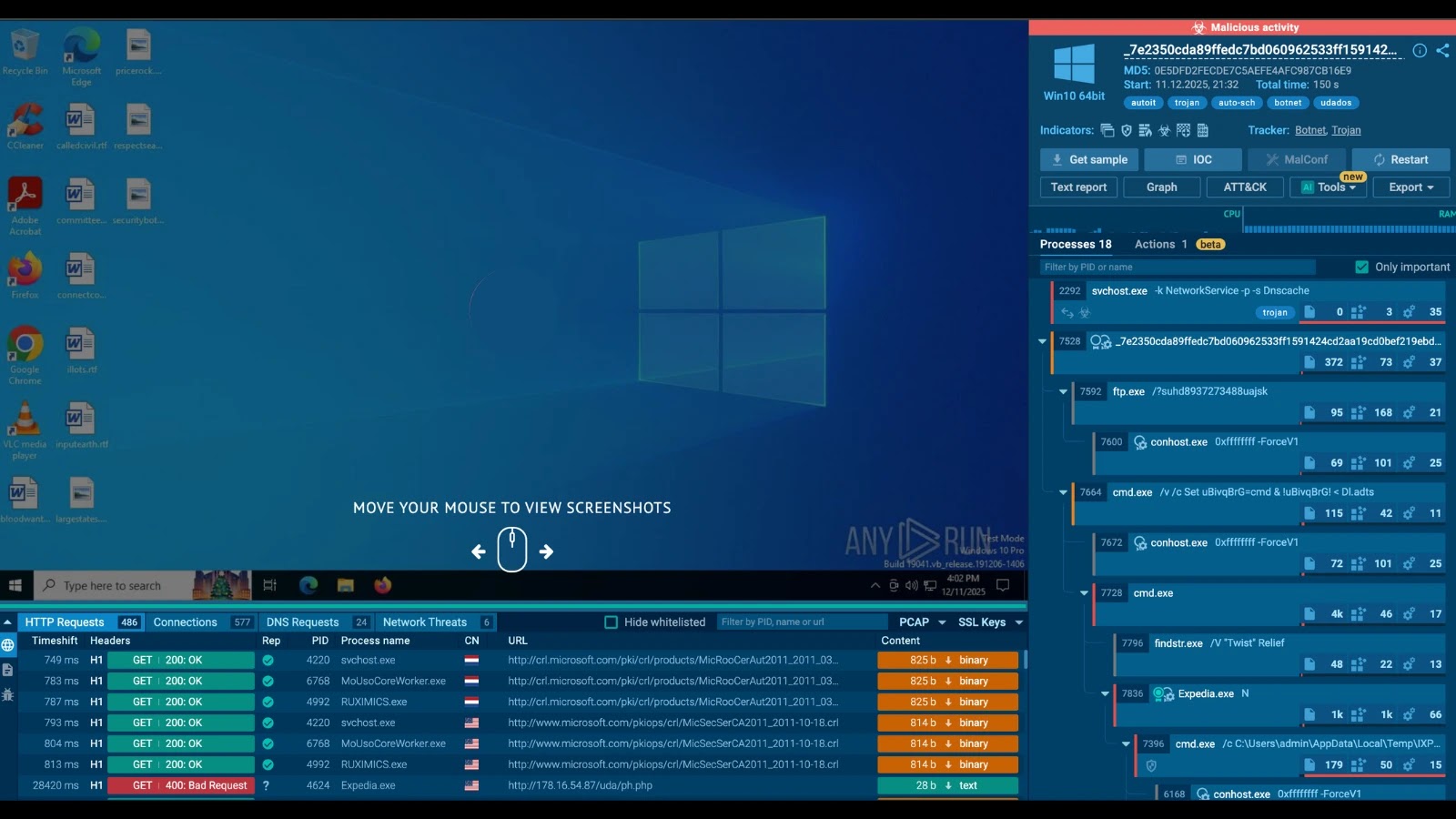
The digital landscape just got a new, formidable adversary. A newly identified botnet malware family, now dubbed Udados, has emerged as a significant threat, specifically targeting the Technology and Telecommunications sectors. This isn’t a mere nuisance; Udados is orchestrating high-volume HTTP flood Distributed Denial-of-Service (DDoS) attacks, designed with one clear objective: to cripple business continuity by overwhelming target servers with a deluge of sophisticated, legitimate-looking traffic.
Understanding the operational mechanics and potential impact of Udados is critical for any organization within its crosshairs. Cyber intelligence, such as that provided by ANY.RUN sandbox analysis, confirms that this botnet leverages a network of compromised hosts to execute sustained denial-of-service campaigns. For IT professionals, security analysts, and developers, recognizing this threat and implementing robust defense strategies is paramount.
The Mechanics of an HTTP Flood DDoS Attack
HTTP flood DDoS attacks are insidious because they don’t rely on exploiting software vulnerabilities in the traditional sense. Instead, they weaponize standard web requests. Imagine thousands, or even millions, of compromised machines simultaneously requesting pages, images, or data from a target server. This isn’t just random noise; Udados generates traffic that appears to be from legitimate users – browsing, submitting forms, or interacting with a web application.
The sheer volume of these requests quickly exhausts the server’s resources: CPU, memory, and bandwidth. The target server becomes so busy responding to the fake requests that it can no longer process genuine user traffic, leading to service degradation or complete unavailability. This disruption translates directly into lost revenue, reputational damage, and a significant blow to operational efficiency for affected businesses.
Udados’ Modus Operandi: Targeting Tech and Telecom
The strategic focus of Udados on the Technology and Telecommunications sectors is no accident. These industries are highly reliant on uninterrupted online services and often serve as critical infrastructure providers. A successful DDoS attack against a telco provider or a major tech company can have cascading effects, impacting numerous downstream businesses and millions of end-users.
The botnet’s ability to generate “legitimate-looking traffic” further complicates detection and mitigation. Traditional rate-limiting or basic IP blocking might not be sufficient, as the attack traffic blends seamlessly with normal user activity. This necessitates more advanced behavioral analysis and threat intelligence to differentiate between benign and malicious requests effectively.
Remediation Actions: Fortifying Your Defenses
Defending against advanced botnets like Udados requires a multi-layered approach. Proactive measures and robust incident response plans are essential for mitigating the impact of an HTTP flood DDoS attack.
- DDoS Mitigation Services: Partner with a specialized DDoS mitigation service provider. These services can absorb large volumes of malicious traffic, filter it, and forward only legitimate requests to your infrastructure.
- Web Application Firewalls (WAFs): Implement a WAF to inspect HTTP traffic for suspicious patterns and block malicious requests before they reach your web servers. Modern WAFs can detect behavioral anomalies indicative of botnet activity.
- Rate Limiting and Throttling: Configure your web servers and load balancers to implement intelligent rate limiting. This involves setting thresholds on the number of requests a single IP address or session can make within a given timeframe.
- Geographical Filtering: If your user base is regionally focused, consider blocking traffic from geographic regions where your legitimate users are not expected to originate.
- Bot Management Solutions: Deploy advanced bot management tools that use AI and machine learning to distinguish between human users and sophisticated bots.
- Scalable Infrastructure: Ensure your infrastructure is designed to scale horizontally to handle unexpected traffic spikes. Cloud-based solutions often offer inherent scalability advantages.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify and address potential weaknesses in your network and application architecture.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan specifically for DDoS attacks. This plan should outline communication protocols, mitigation steps, and team responsibilities.
Key Takeaways for Cybersecurity Professionals
The emergence of the Udados botnet underscores a critical shift in the threat landscape. Organizations, especially those in the Technology and Telecommunications sectors, must recognize the growing sophistication of HTTP flood DDoS attacks. These attacks are not merely about volume; they are about mimicking legitimate user behavior, making detection and mitigation more complex than ever before.
Proactive investment in advanced DDoS protection, robust WAF solutions, and intelligent bot management systems is no longer optional—it is a baseline requirement for maintaining operational resilience. Staying informed about new threat actors like Udados and continuously adapting defense strategies are crucial steps in safeguarding critical digital assets against these persistent and evolving threats.





