New Win-DDoS Flaws Let Attackers Turn Public Domain Controllers into DDoS Botnet via RPC, LDAP
A disturbing new attack technique, dubbed Win-DDoS, has been unveiled, posing a significant threat to global network infrastructure. This novel approach enables attackers to weaponize thousands of seemingly innocuous public Windows Domain Controllers (DCs), transforming them into a formidable Distributed Denial-of-Service (DDoS) botnet. The implications are severe, as these compromised DCs can then be leveraged to launch devastating DDoS attacks, crippling online services and critical infrastructure worldwide.
Discovered and presented by SafeBreach researchers Or Yair and Shahak Morag at the DEF CON 33 security conference, Win-DDoS exploits inherent flaws in how Directory Services Remote Protocol (RPC) and Lightweight Directory Access Protocol (LDAP) are utilized by public-facing domain controllers. This blog post delves into the mechanics of this sophisticated attack, its potential impact, and crucial remediation strategies for IT professionals and cybersecurity analysts.
Understanding the Win-DDoS Attack Vector
The Win-DDoS attack capitalizes on the widespread exposure of Windows Domain Controllers to the internet, often a misconfiguration or an oversight in network architecture. These DCs, vital for managing user authentication and network resources within an organization, can become unwitting participants in a malicious botnet if left vulnerable. The core of the attack lies in manipulating RPC and LDAP requests to amplify traffic, turning the DCs into unwitting reflectors for DDoS attacks.
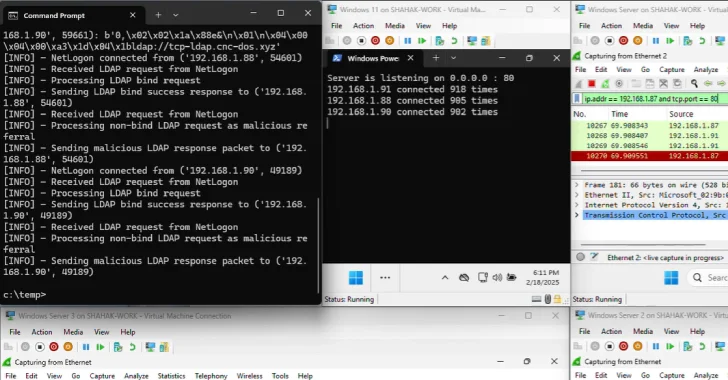
Specifically, the researchers demonstrated how tailored RPC and LDAP queries, directed at public DCs, can elicit significantly larger responses. This amplification factor is the key to the attack’s potency. When multiple compromised DCs simultaneously direct these amplified responses towards a target, the sheer volume of traffic can overwhelm even robust denial-of-service prevention mechanisms.
The Role of RPC and LDAP in DDoS Amplification
Directory Services Remote Protocol (RPC) and Lightweight Directory Access Protocol (LDAP) are fundamental communication protocols within Active Directory environments. RPC facilitates inter-process communication, while LDAP is used for querying and modifying directory services. While essential for legitimate network operations, their susceptibility to amplification attacks when exposed publicly presents a critical security loophole.
Attackers craft specific requests that trigger DCs to respond with large data packets. This magnified response, when directed at a victim, constitutes the amplification. The use of legitimate protocols makes detection more challenging, as the traffic initially appears to be legitimate Active Directory communication. This stealthy nature allows the botnet to grow and operate undetected for longer periods, maximizing its destructive potential.
Potential Impact of Win-DDoS Botnets
The rise of Win-DDoS botnets poses a significant threat to the global digital landscape. The ability to harness thousands of public DCs worldwide to launch DDoS attacks translates to:
- Unprecedented Attack Volume: The sheer number of potential reflectors could generate attack traffic far exceeding typical volumetric DDoS attacks.
- Targeting Critical Infrastructure: Essential services, emergency response systems, and financial institutions are potential targets, leading to widespread disruptions.
- Increased Complexity of Mitigation: Distinguishing legitimate traffic from malicious amplified traffic from compromised DCs becomes a formidable challenge for network defenders.
- Reputational Damage: Organizations whose DCs are unknowingly used in these attacks face reputational harm and potential compliance issues.
Remediation Actions and Best Practices
Protecting against Win-DDoS and similar amplification attacks requires a multi-layered approach focusing on rigorous network hygiene and proactive security measures. While specific CVEs for this newly disclosed technique are pending, immediate actions can significantly reduce exposure:
- Restrict Public Exposure of DCs: The most crucial step is to ensure that Domain Controllers are never directly exposed to the public internet. DCs should reside within an internal network segment, accessible only via secure VPNs or jump boxes. Implement strict firewall rules to block all inbound traffic to DC ports from external networks.
- Implement Network Segmentation: Isolate Domain Controllers into dedicated, highly secured network segments. This limits the blast radius if other parts of the network are compromised.
- Review and Harden RPC/LDAP Configurations: Implement stringent security configurations for RPC and LDAP services. Disable unnecessary services and protocols on DCs, and ensure only authenticated and authorized users/systems can interact with them.
- Apply Principle of Least Privilege: Limit administrative access to Domain Controllers to only those who absolutely require it. Use strong, unique passwords and multi-factor authentication (MFA) for all administrative accounts.
- Regularly Patch and Update: Keep all Windows operating systems and Active Directory components fully patched and updated. While Win-DDoS may not have a specific patch yet, general security updates often contain fixes that indirectly mitigate such vulnerabilities.
- Monitor DC Activity: Implement robust logging and monitoring for all activity on Domain Controllers. Look for unusual spikes in RPC/LDAP traffic, anomalous authentication attempts, or connections from unexpected IP addresses. Utilize Security Information and Event Management (SIEM) systems for centralized logging and anomaly detection.
- Employ DDoS Protection Services: Organizations should leverage cloud-based DDoS protection services at the network edge to filter and mitigate large-scale volumetric attacks.
- Conduct Regular Security Audits and Penetration Testing: Proactively identify misconfigurations and vulnerabilities through regular security audits and penetration tests, focusing specifically on external exposure of internal services.
Relevant Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Wireshark | Network protocol analyzer for deep packet inspection and anomaly detection. | https://www.wireshark.org/ |
| Nmap | Network scanner for identifying open ports and services on DCs. | https://nmap.org/ |
| Microsoft Baseline Security Analyzer (MBSA) (Deprecated, but principles valid) | Identifies common security misconfigurations on Windows systems. (Consider modern alternatives like Microsoft Defender for Cloud) | |
| Active Directory Health Check Tools/Scripts | Various scripts and tools for auditing AD health and security configurations. | (Search for “Active Directory security audit scripts” on GitHub) |
| Cloudflare/Akamai/ otras. | DDoS mitigation services. | https://www.cloudflare.com/ddos/ |
Conclusion
The emergence of Win-DDoS highlights a critical, often overlooked, vulnerability: the unintended exposure of internal infrastructure to the internet. As attackers continually innovate, exploiting seemingly benign protocols for malicious ends, network defenders must remain vigilant. Prioritizing strict network segmentation, robust access controls, and continuous monitoring of Domain Controllers are paramount to defending against current and future amplification attacks. The insights from SafeBreach serve as a powerful reminder that fundamental cybersecurity hygiene remains our strongest defense.





