Noodlophile Malware Campaign Expands Global Reach with Copyright Phishing Lures
Noodlophile Malware: Unmasking the Global Copyright Phishing Threat
The digital landscape is a constant battleground, and sophisticated threats emerge daily. Today, we delve into a particularly insidious campaign: Noodlophile, an information stealer that has significantly expanded its global footprint. Initially observed over a year ago, this malware is now leveraging highly convincing copyright infringement phishing lures and updated delivery mechanisms to infiltrate enterprises across the U.S., Europe, the Baltic states, and the Asia-Pacific (APAC) region. Understanding its updated tactics and bolstering our defenses is paramount for every organization.
Evolving Tactics: Spear-Phishing and Delivery Innovations
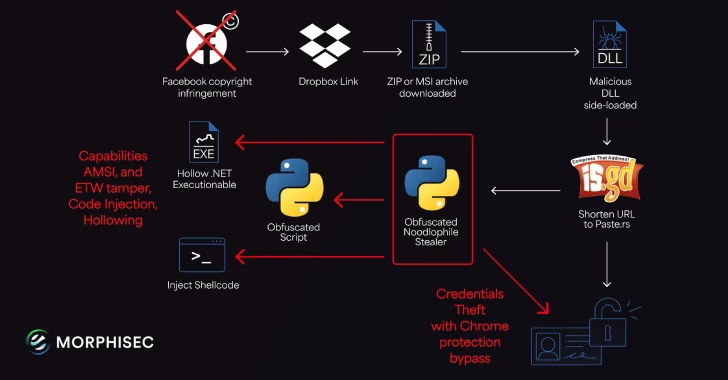
Noodlophile’s longevity stems from its operators’ adaptability. The campaign’s current modus operandi centers on highly targeted spear-phishing emails. These aren’t generic spam; they are crafted to appear as legitimate copyright infringement notices, aiming to evoke a sense of urgency and concern within the recipient. The psychological manipulation inherent in these lures significantly increases the likelihood of a successful compromise.
Beyond the refined social engineering, Noodlophile has also diversified its delivery mechanisms. While the specific new methods are not detailed, the implication is a move away from easily detectable vectors towards more elusive techniques. This could include complex attachment types, embedded malicious links camouflaged as reputable services, or even steganography to conceal payloads within seemingly innocuous files. The shift underscores the need for multi-layered security solutions that can analyze diverse file types and network traffic patterns.
Noodlophile’s Global Ambitions: Targeting Enterprises Worldwide
What differentiates Noodlophile from many other malware campaigns is its broad geographical targeting and specific focus on enterprise environments. The U.S., Europe, Baltic countries, and the APAC region represent significant economic hubs, making them lucrative targets for information theft. This wide net suggests a well-resourced and organized threat actor group aiming for high-value data.
For organizations in these regions, the threat is immediate and significant. Information stealers like Noodlophile are designed to exfiltrate sensitive data, including credentials, financial information, intellectual property, and proprietary business data. A successful breach can lead to severe financial losses, reputational damage, regulatory penalties, and a significant disruption to business operations.
Remediation Actions: Fortifying Your Defenses
Mitigating the Noodlophile threat requires a proactive and comprehensive approach. Organizations must implement a combination of technical controls, user education, and incident response planning.
- Email Security Gateways: Implement advanced email security solutions that can detect and block sophisticated spear-phishing attempts, analyze email content for suspicious links and attachments, and identify anomalies in sender reputation.
- Endpoint Detection and Response (EDR): Deploy EDR solutions on all endpoints to continuously monitor for malicious activity, detect unusual process behavior, and respond to threats in real-time.
- Security Awareness Training: Conduct regular, engaging security awareness training sessions for all employees. Emphasize the dangers of phishing, particularly those involving urgent or emotionally charged topics like copyright infringement. Train users to scrutinize sender details, look for anomalies in email addresses, and verify suspicious requests through alternative communication channels.
- Multi-Factor Authentication (MFA): Enforce MFA for all accounts, especially for access to critical systems and sensitive data. This adds a crucial layer of security, even if credentials are compromised.
- Network Segmentation: Implement network segmentation to limit lateral movement within the network if a compromise occurs. This can contain the damage and prevent the spread of malware.
- Least Privilege Principle: Adhere to the principle of least privilege, ensuring users and applications only have access to the resources absolutely necessary for their functions.
- Regular Backups: Maintain regular, offsite, and air-gapped backups of all critical data. This ensures business continuity even in the event of a successful data breach or ransomware attack facilitated by information stealers.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan. This plan should clearly outline steps for detection, containment, eradication, recovery, and post-incident analysis in the event of a successful Noodlophile infection.
The Ongoing Battle Against Information Stealers
The Noodlophile campaign is a stark reminder that cyber threats are constantly evolving. Their use of compelling social engineering tactics combined with updated delivery mechanisms highlights the need for continuous vigilance and adaptation in our cybersecurity strategies. By understanding these threats, implementing robust technical controls, and empowering employees with effective security awareness, organizations can significantly reduce their risk of falling victim to sophisticated information stealers.
Stay informed, stay secure, and remember that human vigilance remains one of the most powerful defenses against these ever-growing threats.





