OWASP Top 10 2025 – Revised Version Released With Two New Categories
A tectonic shift in web application security is upon us. The Open Web Application Security Project (OWASP) has once again redefined the landscape with the release of the OWASP Top 10 2025. This eighth iteration, unveiled on November 6, 2025, isn’t just an update; it’s a critical recalibration, introducing two new risk categories and consolidating others to reflect the contemporary threat environment. For every cybersecurity analyst, developer, and IT professional, understanding these changes isn’t optional – it’s fundamental to building resilient applications.
Understanding the OWASP Top 10 2025 Evolution
The OWASP Top 10 serves as a crucial awareness document for application security, highlighting the most critical web application security risks. Its regular revisions are vital, driven by extensive community feedback and rigorous data analysis from thousands of applications. The 2025 edition particularly emphasizes emerging attack vectors and persistent vulnerabilities that continue to plague software development.
Two New Categories Emerge
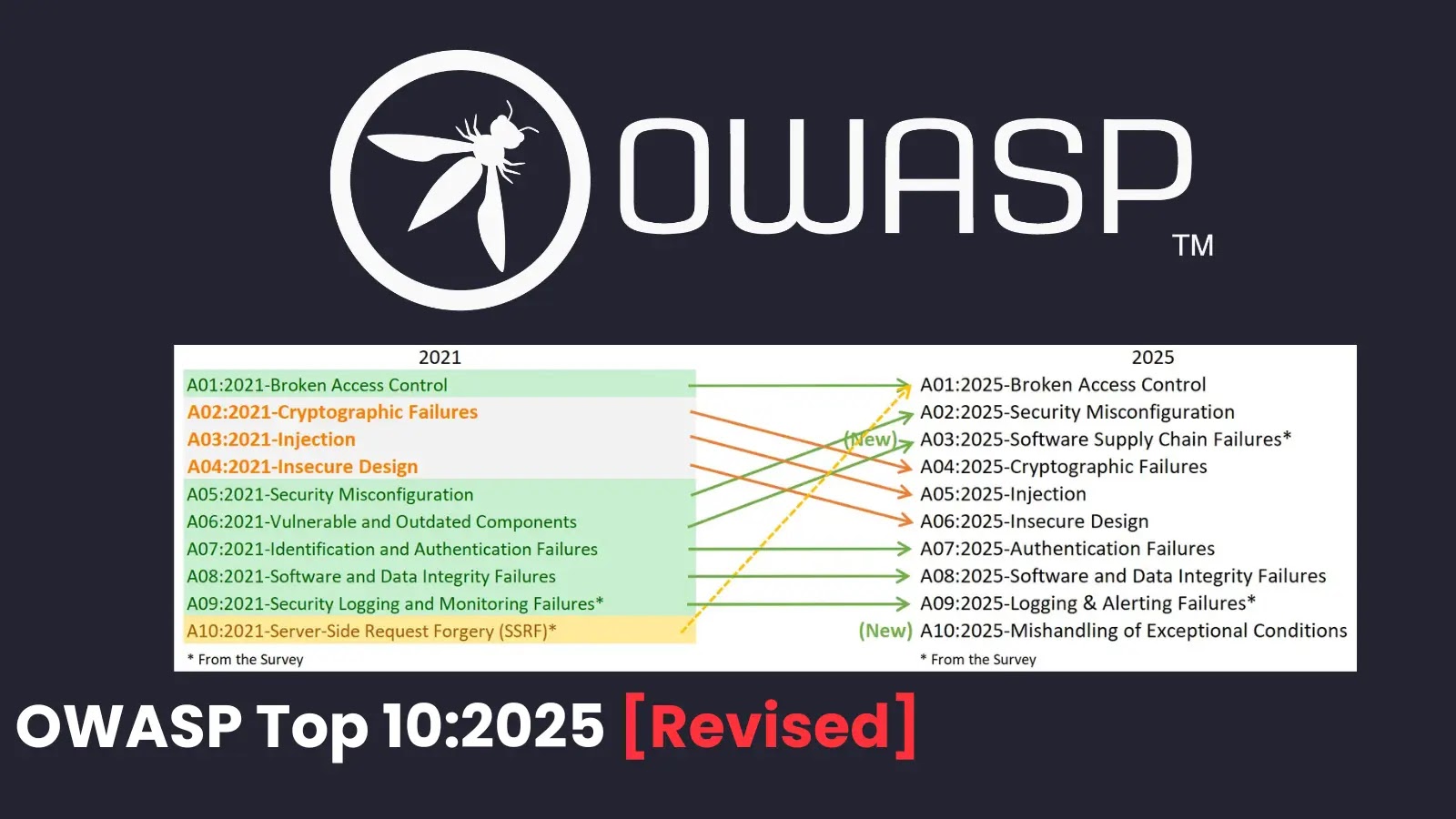
The most significant update in the OWASP Top 10 2025 is the introduction of two entirely new risk categories. While the complete list of all ten categories isn’t detailed in the provided source, the emergence of new classifications signals a shift in perceived threats. These additions likely address weaknesses that have gained prominence due to evolving architectural patterns, new technologies, or sophisticated attack methodologies. For instance, the rise of API-driven applications and complex microservices architectures often introduces new surface areas for exploitation that may not have been adequately covered by previous categories.
Consolidation and Refinement of Existing Risks
Concurrently with the new categories, OWASP has also undertaken a consolidation effort. This often involves merging similar vulnerabilities or redefining categories to better encompass a broader range of related risks. This strategic consolidation aims to streamline the Top 10, making it more digestible and actionable while ensuring comprehensive coverage of critical threats. Such an approach reflects a maturing understanding of how vulnerabilities interact and often stem from common underlying security hygiene failures.
Implications for Developers and Security Teams
The release of OWASP Top 10 2025 demands immediate attention from anyone involved in web application development and security. Development teams must review their secure coding practices, vulnerability scanning routines, and architectural designs against these updated priorities. Security analysts need to re-evaluate their threat models and penetration testing methodologies to ensure they’re adequately covering the newly emphasized risks. Ignoring these updates could leave applications vulnerable to the most prevalent and impactful attacks.
Proactive Remediation is Key
While specific new categories aren’t detailed in the provided snippet, the general principle of remediation remains critical. For any OWASP Top 10 vulnerability, proactive measures are paramount. Here’s a general framework for addressing modern application security risks:
- Secure Design Principles: Integrate security considerations from the very beginning of the software development lifecycle (SDLC). Adopt threat modeling and security-by-design methodologies.
- Input Validation and Output Encoding: Rigorously validate all user input and properly encode all output to prevent injection attacks (e.g., SQL Injection, Cross-Site Scripting CVE-2023-XXXXX).
- Authentication and Authorization: Implement robust authentication mechanisms (e.g., multi-factor authentication) and adhere to the principle of least privilege for authorization.
- Dependency Management: Regularly scan and update third-party libraries and frameworks to mitigate risks from known vulnerabilities (e.g., Log4Shell CVE-2021-44228).
- Error Handling and Logging: Implement comprehensive logging for security events and ensure error messages do not disclose sensitive information.
- Configuration Management: Maintain secure configurations across all components of the application stack, from servers to databases.
- Security Testing: Employ a combination of static application security testing (SAST), dynamic application security testing (DAST), and interactive application security testing (IAST) throughout the SDLC.
Tools for Detection and Mitigation
Effective defense against OWASP Top 10 risks requires a blend of tools and practices. Here are categories of tools essential for mitigating common web application vulnerabilities:
| Tool Category | Purpose | Example Tools / Link |
|---|---|---|
| Static Application Security Testing (SAST) | Identifies vulnerabilities in source code before execution. | SonarQube, Semgrep |
| Dynamic Application Security Testing (DAST) | Simulates attacks against a running application to find vulnerabilities. | OWASP ZAP, Burp Suite |
| Interactive Application Security Testing (IAST) | Analyzes application behavior from within during runtime. | Contrast Security |
| Software Composition Analysis (SCA) | Identifies vulnerabilities in open-source components and dependencies. | Synopsys Black Duck, Mend.io (WhiteSource) |
| Web Application Firewall (WAF) | Filters HTTP traffic to protect web applications from common attacks. | Cloudflare WAF, ModSecurity |
Looking Ahead with OWASP Top 10 2025
The OWASP Top 10 2025 reinforces a fundamental truth: application security is a continually evolving challenge. The introduction of new categories and the ongoing refinement of existing ones underscore the necessity for continuous learning, adaptation, and a proactive security posture. Organizations that embrace these updates will be better positioned to defend their applications against the most pressing threats, safeguarding data and maintaining user trust in an increasingly complex digital world.





