PoC Exploit Released For Nothing Phone Code Execution Vulnerability
A significant cybersecurity alert has emerged concerning the secure boot chain in specific smartphone models, presenting a critical code execution vulnerability. A proof-of-concept (PoC) exploit, dubbed “Fenrir,” has been publicly released, demonstrating arbitrary code execution at the highest privilege level on affected devices. This development underscores the persistent challenges in securing embedded systems and the importance of robust vulnerability management.
The Fenrir Exploit: Breaking Secure Boot on Nothing Phones
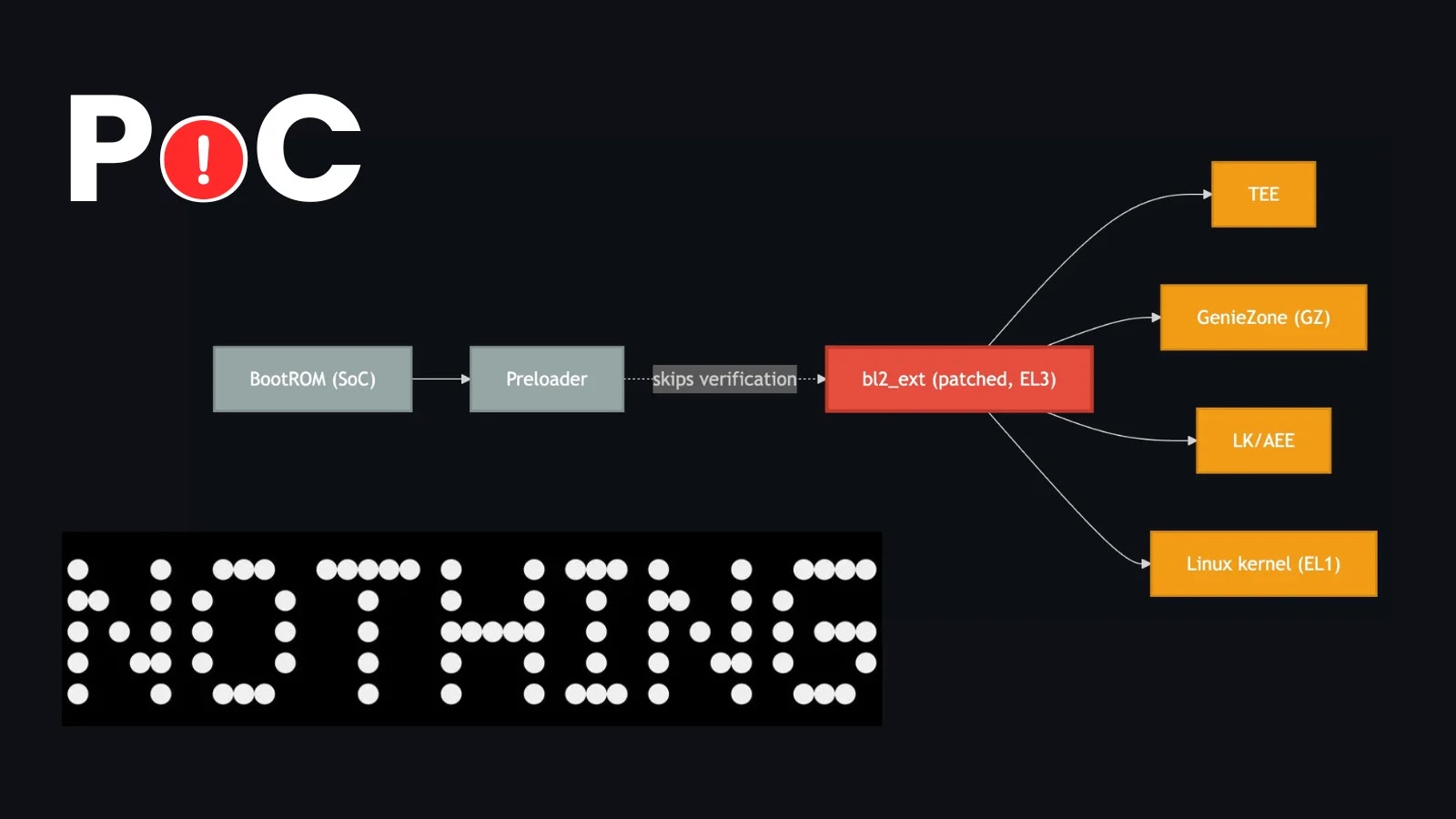
The recently disclosed Fenrir PoC exploit targets a critical vulnerability within the secure boot process of certain smartphones. Specifically, the Cyber Security News report highlights its impact on the Nothing Phone (2a) and the CMF Phone 1. This exploit, developed by researcher R0rt1z2, is particularly concerning because it enables arbitrary code execution with root privileges, effectively bypassing the foundational security mechanisms designed to protect device integrity from startup.
The underlying issue is believed to reside within the secure boot chain, a critical sequence of checks that verifies the authenticity and integrity of software loaded during device startup. A compromise at this level means an attacker could inject malicious code before the operating system even fully loads, gaining complete control over the device and its data. While the immediate impact is on the Nothing Phone (2a) and CMF Phone 1, the report suggests that other devices utilizing MediaTek systems-on-a-chip (SoCs) could also be at risk, given the commonality of hardware components and bootloader implementations across various manufacturers.
Understanding the Threat: Arbitrary Code Execution and Privilege Escalation
Arbitrary Code Execution (ACE) is one of the most severe types of vulnerabilities. It allows an attacker to run any code of their choosing on the target system. When combined with Privilege Escalation to the highest level (often referred to as “root” or “kernel” privileges), the attacker gains unfettered access. This means they can:
- Access and exfiltrate sensitive user data.
- Install persistent malware or spyware.
- Modify system settings or firmware.
- Take complete control of the device, potentially rendering it unusable or transforming it into a botnet member.
The secure boot chain is designed precisely to prevent such scenarios by cryptographically verifying each stage of the boot process. The Fenrir exploit’s ability to circumvent this process represents a fundamental security bypass, posing a significant risk to user privacy and data integrity.
Affected Devices and Potential Broader Implications
The primary named devices affected are the Nothing Phone (2a) and the CMF Phone 1. The mention of MediaTek SoCs is crucial, as MediaTek is a major supplier of smartphone chipsets. Many Android devices from various manufacturers rely on MediaTek processors. This raises concerns that the underlying vulnerability exploited by Fenrir might not be isolated to Nothing and CMF devices but could potentially affect a wider range of Android smartphones sharing similar MediaTek secure boot implementations. Users of MediaTek-powered devices should monitor cybersecurity news closely for updates from their respective manufacturers.
Remediation Actions
Addressing a secure boot chain vulnerability requires vendor intervention. Users and organizations with affected devices should take the following steps:
- Apply Vendor Patches Immediately: Monitor for official security updates from Nothing and CMF. As soon as a patch is released, install it without delay. This is paramount for mitigating the risk posed by Fenrir.
- Exercise Caution with Unofficial ROMs or Modifications: Avoid installing custom ROMs, rooting tools, or unofficial firmware, especially from unverified sources. These activities can inadvertently introduce new vulnerabilities or bypass critical security checks that the vendor has implemented.
- Back Up Your Data: Regularly back up all critical data from your device to a secure, external location. In the event of a compromise, this ensures data recovery is possible.
- Enable All Available Security Features: Utilize strong passwords/PINs, biometric authentication, and device encryption where available. While these may not prevent a secure boot exploit, they add layers of protection once the device is running.
- Be Wary of Phishing and Malicious Links: As a general security best practice, be cautious about clicking on suspicious links or downloading files from untrusted sources, which could be vectors for other types of attacks.
Detection and Mitigation Tools
While direct detection of a secure boot chain exploit at the user level can be challenging without specialized tools, some general security practices and tools can help identify compromised devices or prevent other forms of attack.
| Tool Name | Purpose | Link |
|---|---|---|
| Mobile Threat Defense (MTD) Solutions | Detects sophisticated mobile threats, including malware, phishing, and device configuration vulnerabilities. | Gartner MTD Guide |
| Android SafetyNet Attestation | Google’s API that helps determine the integrity and compatibility of an Android device, indicating if it has been rooted or altered. | Google SafetyNet Attestation |
| Endpoint Detection and Response (EDR) for Mobile | Provides advanced threat hunting, detection, and response capabilities for mobile devices. | Gartner EDR Guide |
Conclusion
The public release of the Fenrir PoC exploit for Nothing Phone (2a) and CMF Phone 1 highlights the critical importance of secure boot implementations in modern mobile devices. Arbitrary code execution at the highest privilege level poses a severe threat to user data and device integrity. While vendor patches are the definitive solution, users should proactively implement recommended security practices and remain vigilant against potential exploitation attempts. This incident reinforces the need for continuous security research and prompt vulnerability remediation across the entire hardware and software supply chain, especially for devices relying on common SoC platforms like MediaTek.





