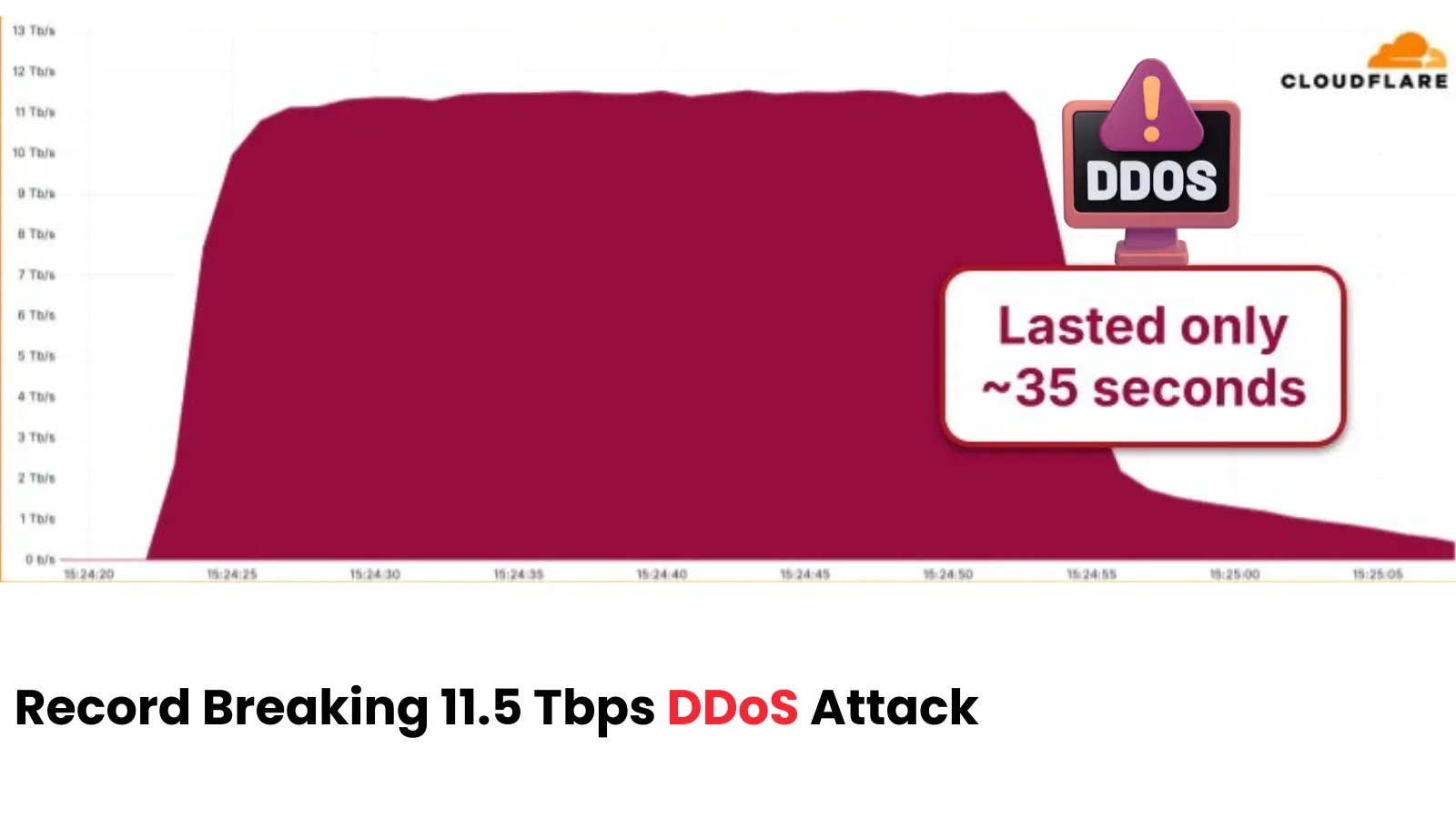
Record-breaking 11.5 Tbps UDP Flood DDoS Attack Originated from Google Cloud Platform
The digital landscape is a constant battleground, with cyber attackers perpetually seeking new ways to disrupt, exploit, and compromise. While many threats evolve discreetly, some manifest with a force that shatters previous records, sending shockwaves through the cybersecurity community. Such was the case with a recent Distributed Denial-of-Service (DDoS) attack that registered an unprecedented 11.5 Terabits per second (Tbps), originating predominantly from compromised resources within the Google Cloud Platform.
This isn’t merely an abstract statistic; it represents a significant escalation in the scale and sophistication of cyber warfare. Understanding the mechanics of this record-breaking incident, its implications, and the strategies for defense is paramount for every organization operating online.
Understanding DDoS Attacks and UDP Floods
A Distributed Denial-of-Service (DDoS) attack aims to overwhelm a target server, service, or network with a flood of internet traffic, rendering it inaccessible to legitimate users. Imagine a popular store suddenly being swamped by so many people that real customers cannot enter. In the digital realm, this translates to service outages, financial losses, and reputational damage.
The 11.5 Tbps attack was specifically a UDP Flood. User Datagram Protocol (UDP) is a connectionless communication protocol that doesn’t require a handshake to establish a connection before sending data. This makes it fast but also vulnerable to abuse. In a UDP flood, attackers send a massive number of UDP packets to random ports on the target server. The server then tries to respond to these packets, often with “Destination Unreachable” messages. This process consumes server resources, including CPU, memory, and bandwidth, eventually leading to a denial of service. The sheer volume of packets generated in this attack highlights the critical need for robust defense mechanisms.
The Record-Breaking Scale: 11.5 Tbps
To put 11.5 Tbps into perspective: this is an astronomical amount of data. Previous record-holding DDoS attacks were significantly smaller, though still potent. For instance, a 2018 attack against GitHub peaked at 1.35 Tbps, and another against Amazon Web Services by an unamed organization reached 2.3 Tbps. The recent 11.5 Tbps incident represents a nearly five-fold increase over the previous known high, demonstrating a disturbing trend towards larger, more impactful attacks. This massive scale suggests highly organized and well-resourced attackers leveraging a substantial botnet infrastructure.
Google Cloud Platform as the Origin Point
A particularly concerning aspect of this attack was its primary origin: compromised resources within the Google Cloud Platform (GCP). This does not imply that Google Cloud itself was maliciously involved, but rather that attackers successfully exploited vulnerable resources hosted on GCP to launch their assault. This often occurs when virtual machines, containers, or services provisioned by legitimate GCP customers are compromised due to misconfigurations, weak credentials, unpatched software, or other vulnerabilities. Once compromised, these resources essentially become unwitting participants in the attacker’s botnet, amplifying the attack traffic and lending it a degree of legitimacy due to its origin from a reputable cloud provider.
Cloudflare’s Role in Mitigation
Cloudflare, a leading provider of web security and infrastructure services, successfully detected and mitigated this colossal attack. Their advanced DDoS protection systems, designed to absorb and filter out malicious traffic, proved effective in preventing outages for their customers. This highlights the critical importance of leveraging specialized DDoS mitigation services that possess the global capacity and intelligent filtering capabilities necessary to withstand such unprecedented onslaughts.
Implications for Cybersecurity
The 11.5 Tbps UDP flood originating from a major cloud provider carries several significant implications:
- Escalating Scale of Attacks: This incident solidifies the trend of increasingly larger and more destructive DDoS attacks. Organizations must prepare for scenarios where their current mitigation strategies might be insufficient.
- Cloud Platform Vulnerability: While cloud providers invest heavily in security, the incident underscores that even their infrastructure can be leveraged by attackers if customer resources are compromised. This places a shared responsibility on both cloud providers and their customers to secure their cloud environments diligently.
- Sophistication of Attackers: Orchestrating an attack of this magnitude requires significant resources, technical expertise, and potentially novel exploitation techniques.
- Need for Advanced Mitigation: Standard firewalls and basic rate limiting are no longer adequate. Organizations require advanced, multi-layered DDoS protection that can scale to terabit levels and intelligently differentiate legitimate traffic from malicious floods.
Remediation Actions and Best Practices
Given the escalating threat landscape, organizations must adopt robust strategies to defend against such sophisticated DDoS attacks. Here are key remediation actions and best practices:
- Implement Multi-Layered DDoS Protection: Engage with specialized DDoS mitigation services (like Cloudflare, Akamai, or others) that can absorb massive traffic volumes and filter malicious packets at the network edge.
- Utilize WAFs (Web Application Firewalls): While not solely for DDoS, WAFs can help protect against application-layer DDoS attacks and filter malicious requests before they reach the application servers.
- Strengthen Cloud Security Posture:
- Regular Audits: Conduct frequent security audits of your cloud configurations, including network rules, access controls, and resource permissions.
- Principle of Least Privilege: Ensure that all cloud resources and user accounts operate with the minimum necessary permissions.
- Patch Management: Maintain a rigorous patch management program for all operating systems, applications, and services running within your cloud instances. Unpatched vulnerabilities (e.g., those found in common services that might be exploited, though no specific CVE is publicly linked to this generalized UDP flood’s origin) are prime targets for compromise. While no specific CVE for the compromised GCP resources was released for this attack, general vulnerabilities like those related to insecure remote access protocols or unpatched system services are always a risk.
- Network Segmentation: Segment your cloud networks to limit the blast radius if one segment is compromised.
- Anomaly Detection: Implement robust logging and monitoring solutions with anomaly detection capabilities to quickly identify unusual traffic patterns or unauthorized access.
- Ingress/Egress Filtering: Configure firewalls and security groups to filter incoming and outgoing traffic, blocking known malicious IP ranges and preventing compromised instances from participating in attacks.
- Resource Scalability: Design your infrastructure to be highly scalable, allowing it to temporarily absorb spikes in traffic (though this cannot fully mitigate a Tbps-level attack without dedicated DDoS protection).
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan specifically for DDoS attacks, outlining roles, responsibilities, and communication protocols.
Conclusion
The record-breaking 11.5 Tbps UDP flood DDoS attack serves as a stark reminder of the persistent and evolving threat landscape. Its origin from compromised cloud resources further underscores the shared responsibility in securing digital assets. For organizations, the path forward involves embracing advanced DDoS mitigation, fortifying cloud security postures, and maintaining an unwavering commitment to proactive defense. Only through such vigilance can we hope to withstand the escalating tide of cyberattacks and ensure the continuous availability of critical online services.





