Researchers Created a Linux Rootkit that Evades Elastic Security EDR Detection
A New Threat: Linux Rootkit Evades Elastic Security EDR Detection
In the highly dynamic landscape of cybersecurity, the arms race between defensive technologies and sophisticated attack vectors continues unabated. A recent development has sent ripples through the security community: a newly disclosed Linux kernel rootkit designed specifically to bypass the formidable defenses of Elastic Security’s Endpoint Detection and Response (EDR) platform. This unsettling discovery highlights the persistent challenges in kernel-level threat detection and the ever-present need for multi-layered security strategies.
Introducing Singularity: A Stealthy Linux Rootkit
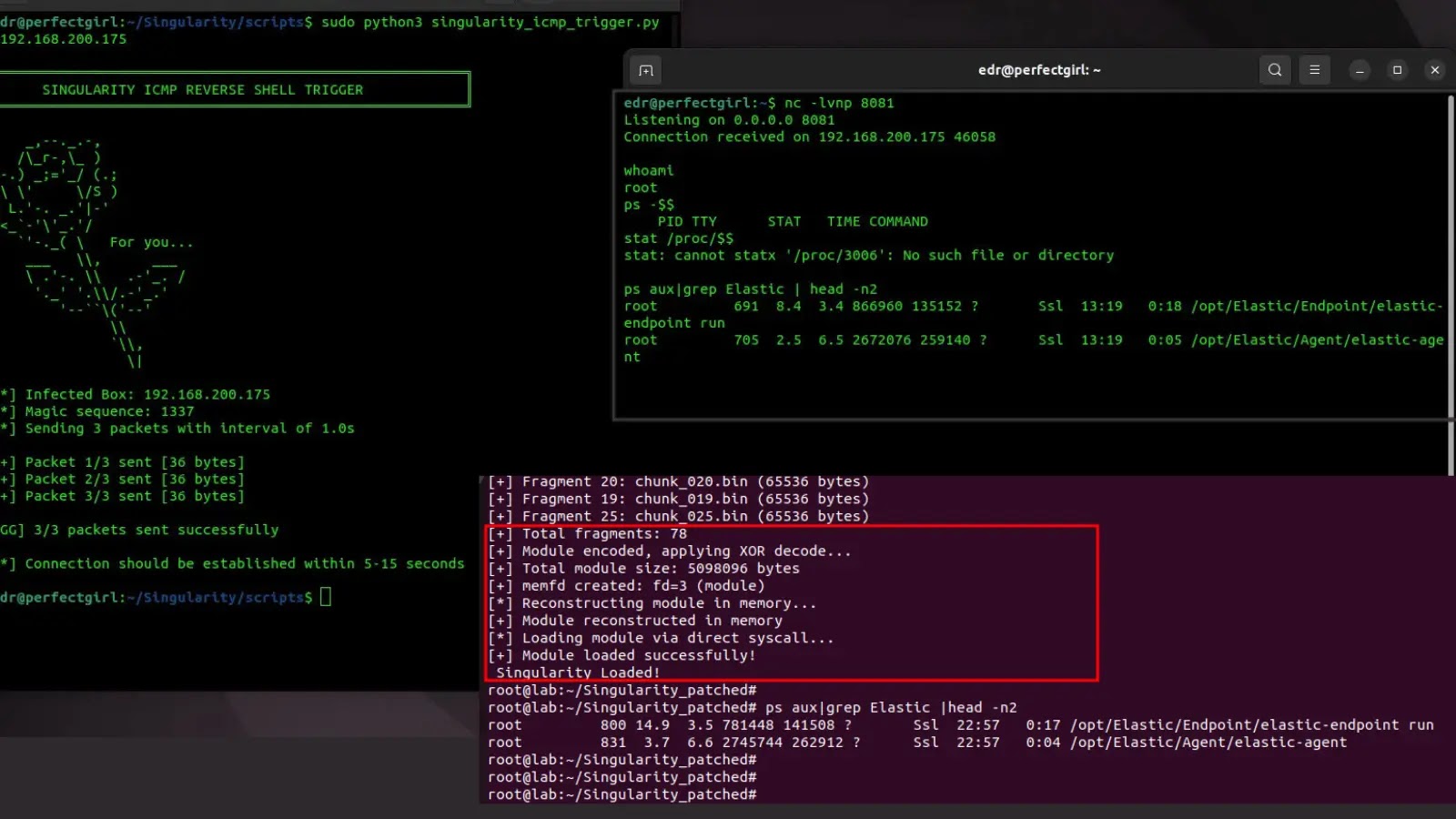
The rootkit, dubbed Singularity, was unveiled by researcher 0xMatheuZ and subsequently released on GitHub. While presented strictly for educational and research purposes, its capabilities are a stark reminder of the advanced tactics employed by threat actors. Singularity’s primary objective is to achieve stealth and persistence on Linux systems, making it exceptionally difficult for traditional EDR solutions to identify its presence.
Advanced Evasion Techniques and the Limits of YARA Rules
Singularity distinguishes itself through its sophisticated evasion techniques. The rootkit employs advanced obfuscation to mask its malicious activities, allowing it to operate under the radar of many existing security mechanisms. A key target of its evasion is YARA-based detection. YARA rules, often referred to as “the pattern matching Swiss knife for malware researchers,” are widely used by EDRs, including Elastic Security, to identify known malware families based on specific patterns or characteristics within files or memory. By employing obfuscation, Singularity effectively scrambles these patterns, rendering many YARA rules ineffective. Furthermore, its design suggests an ability to bypass behavioral monitoring, a cornerstone of modern EDR solutions that aims to detect anomalous system activities.
The Implications for Elastic Security Users
Elastic Security, a prominent player in the EDR space, offers robust capabilities for threat detection, prevention, and response. The existence of a rootkit specifically engineered to evade its defenses poses a significant concern for organizations relying on this platform. This revelation underscores that even leading EDR solutions are not impenetrable and that advanced, kernel-level threats continue to evolve at a rapid pace. While Elastic Security continuously updates its detection mechanisms, exploits like Singularity demonstrate the constant need for vigilance and adaptation.
Kernel-Level Threats: A Persistent Challenge
Kernel rootkits operate at the deepest layers of an operating system, granting them ultimate control and the ability to completely subvert security controls. Because they load within the kernel space, they can manipulate core system functions, hide processes, files, and network connections, and effectively become invisible to user-mode applications and even many security tools. Detecting such threats requires highly specialized techniques, often involving introspection at a lower level than what most EDRs are designed for. This challenge is magnified in complex Linux environments, where the open-source nature can lead to diverse configurations and potential attack surfaces.
Remediation Actions and Enhanced Defenses
While a direct CVE number isn’t associated with the rootkit itself (as it’s a demonstration tool, not a specific vulnerability in software), the implications for system security demand proactive measures. Organizations leveraging Linux systems, particularly those using Elastic Security, should consider the following remediation and enhancement strategies:
- Implement a layered security approach: Relying solely on a single EDR solution is insufficient. Integrate host-based intrusion detection systems (HIDS), network intrusion detection/prevention systems (NIDS/NIPS), and strong perimeter defenses.
- Regular Kernel Patching and Updates: Ensure that all Linux kernels are kept up-to-date with the latest security patches. Many rootkits exploit known kernel vulnerabilities to gain initial access or facilitate their installation.
- Kernel Module Signing: Enforce kernel module signing to ensure that only trusted and verified kernel modules can be loaded. This significantly hinders the ability of unauthorized rootkits to inject malicious code.
- File Integrity Monitoring (FIM): Deploy robust FIM solutions to monitor critical system files and directories (especially in
/boot,/etc, and kernel module paths) for unauthorized modifications. - Behavioral Analytics and Anomaly Detection: While Singularity aims to evade behavioral monitoring, continuously refine and tune behavioral analytics within your EDR and SIEM solutions to detect unusual system calls, process lineage anomalies, or unexpected network connections.
- Memory Forensics: Develop capabilities for regular memory forensics analysis. Kernel rootkits often leave traces in memory that can be uncovered through deep memory inspection tools.
- Least Privilege Principle: Adhere strictly to the principle of least privilege, limiting administrative access and ensuring that system users and services only have the necessary permissions to perform their functions.
Tools for Detection and Mitigation
Securing Linux environments against advanced threats requires a suite of specialized tools. Here are some categories and examples of tools that can assist in detection, scanning, and mitigation:
| Tool Category/Name | Purpose | Link |
|---|---|---|
| YARA (Generic) | Malware pattern matching, rule development for custom rootkit signatures. | https://virustotal.github.io/yara/ |
| chkrootkit | Scans for common rootkit traces and modifications on Linux systems. | http://www.chkrootkit.org/ |
| Rootkit Hunter (rkhunter) | Performs checks to detect rootkits, backdoors, and local exploits. Compares file hashes with known good ones. | http://rkhunter.sourceforge.net/ |
| Volatility Framework | Advanced memory forensics tool for extracting artifacts from RAM, crucial for kernel-level threat analysis. | https://www.volatilityfoundation.org/ |
| OSSEC HIDS | Open-source Host-based Intrusion Detection System providing FIM, log analysis, and rootkit detection. | https://www.ossec.net/ |
| Integriti (FIM) | File Integrity Monitoring solution for detecting unauthorized changes to critical system files. | (Varies, commercial and open-source options available) |
| Linux Auditd | Native Linux auditing system for tracking security-relevant information about system calls, access attempts, etc. | (Built into Linux kernels) |
Key Takeaways
The emergence of Singularity, a Linux kernel rootkit designed to evade Elastic Security EDR detection, highlights several critical points for cybersecurity professionals. Advanced obfuscation techniques, particularly those targeting YARA-based detection and behavioral monitoring, continue to challenge even leading security platforms. This development reinforces the necessity of a layered security architecture, robust file integrity monitoring, diligent kernel patching, and the ongoing integration of advanced threat hunting and memory forensics capabilities. As threat actors sharpen their tools, so too must our defenses evolve, recognizing that no single security solution offers a silver bullet against determined adversaries operating at the kernel level.





