Researchers Detail Windows EPM Poisoning Exploit Chain Leading to Domain Privilege Escalation
Unmasking the Impersonator: Windows EPM Poisoning and Domain Privilege Escalation
In the intricate landscape of enterprise cybersecurity, a single, seemingly minor vulnerability can form a crucial link in a devastating attack chain. Recent research has shed light on just such a scenario, detailing how a now-patched flaw in Microsoft’s Windows Remote Procedure Call (RPC) communication protocol could be exploited to facilitate server impersonation, ultimately leading to domain privilege escalation. Understanding the mechanics of such exploits is paramount for security professionals tasked with defending critical infrastructure.
The Heart of the Issue: Windows EPM Poisoning
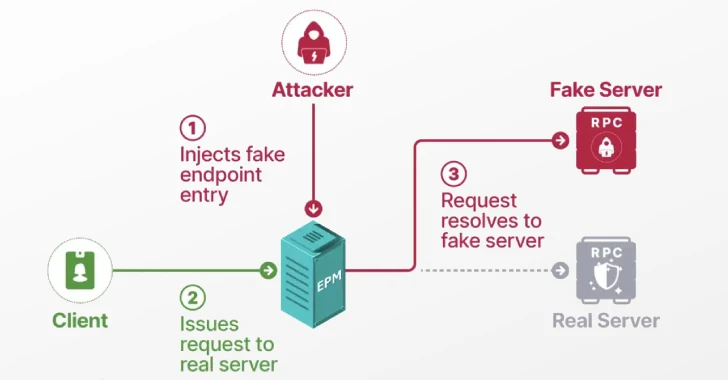
The core of this exploit chain lies within a vulnerability tracked as CVE-2025-49760. Microsoft describes this as a “Windows Storage spoofing bug” with a CVSS score of 3.5. While appearing low in severity on its own, its potential for abuse within a larger attack sequence significantly elevates its risk profile. Specifically, this vulnerability pertains to the Endpoint Mapper (EPM) service used by RPC.
RPC is fundamental to how Windows components and applications communicate across a network. When a client needs to connect to a specific RPC service, it often queries the EPM to discover the port number where that service is listening. The researchers discovered that an attacker could leverage CVE-2025-49760 to poison the EPM’s responses, causing clients to connect to a malicious server instead of the legitimate one.
From Spoofing to Privilege Escalation: The Exploit Chain
The danger of EPM poisoning isn’t just about misdirection; it’s about control. By successfully impersonating a legitimate server, an attacker gains a powerful foothold. Consider a scenario where a domain-joined client attempts to authenticate with a Domain Controller. If an attacker’s rogue server can masquerade as the Domain Controller, they can intercept authentication requests, replay them, or even trick the client into providing sensitive credentials.
This allows an attacker to:
- Intercept Network Traffic: By routing client communications through their controlled server, attackers can snoop on sensitive data.
- Perform Authentication Bypass/Relay: Intercepted authentication attempts can be replayed against the legitimate server (e.g., NTLM Relay attacks) to gain access or elevate privileges.
- Execute Malicious Code: If the spoofed server can trick clients into executing specific code or policies, it opens avenues for remote code execution.
The ultimate goal, domain privilege escalation, means an attacker can gain administrative control over the entire Active Directory domain, granting them unfettered access to all connected systems and data. This transition from a low-severity spoofing bug to a critical domain compromise highlights the importance of understanding exploit chaining.
Remediation Actions
While CVE-2025-49760 has been patched by Microsoft, proactive security measures remain essential. Organizations must ensure that their systems are continually updated and that their security posture accounts for potential attack paths that leverage seemingly minor vulnerabilities.
- Immediate Patching: Ensure all Windows systems are fully patched with the latest security updates from Microsoft. This directly addresses the vulnerability that enables EPM poisoning.
- Network Segmentation: Implement robust network segmentation to limit the blast radius of any potential compromise. Isolate critical assets and Active Directory components from less secure segments.
- Principle of Least Privilege: Enforce the principle of least privilege for all users and services. This minimizes the impact if an account is compromised.
- Advanced Threat Detection: Deploy Endpoint Detection and Response (EDR) and Network Detection and NDR solutions that can identify anomalous RPC traffic patterns, suspicious authentication attempts, and server impersonation activities.
- Regular Security Audits: Conduct regular security audits and penetration tests to identify potential vulnerabilities and misconfigurations that an attacker could exploit.
Tools for Detection and Mitigation
While patching is the primary defense, various tools can aid in detecting and mitigating exploitation attempts, as well as strengthening overall security:
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft Defender for Endpoint (MDE) | Advanced EDR capabilities for detecting anomalous network behavior, process injection, and credential theft attempts. | https://www.microsoft.com/en-us/security/business/threat-protection/microsoft-defender-for-endpoint |
| Wireshark | Network protocol analyzer for deep inspection of RPC and other network traffic to identify suspicious patterns or impersonation. | https://www.wireshark.org/ |
| BloodHound | Identifies hidden attack paths in Active Directory, helping to understand and mitigate potential privilege escalation routes. | https://bloodhoundenterprise.io/ |
| Group Policy Management Console (GPMC) | Manage and apply security policies, including those related to secure RPC communications and authentication. | Built-in Windows Tool |
Key Takeaways for Cybersecurity Professionals
The discovery and patching of CVE-2025-49760 serve as a potent reminder for cybersecurity teams. No vulnerability, regardless of its individual CVSS score, should be dismissed without considering its potential role in a multi-stage attack. The path from a seemingly low-risk spoofing bug to a full domain compromise underscores the need for a layered security approach, diligent patching, continuous monitoring, and a deep understanding of how adversaries chain vulnerabilities to achieve their objectives. Proactive defense requires thinking like an attacker to effectively fortify an organization’s digital perimeter.





