Salty2FA and Tycoon2FA Phishing Kits Attacking Enterprise Users to Steal Login Credentials
The Evolving Threat: Salty2FA and Tycoon2FA Phishing Kits Converge
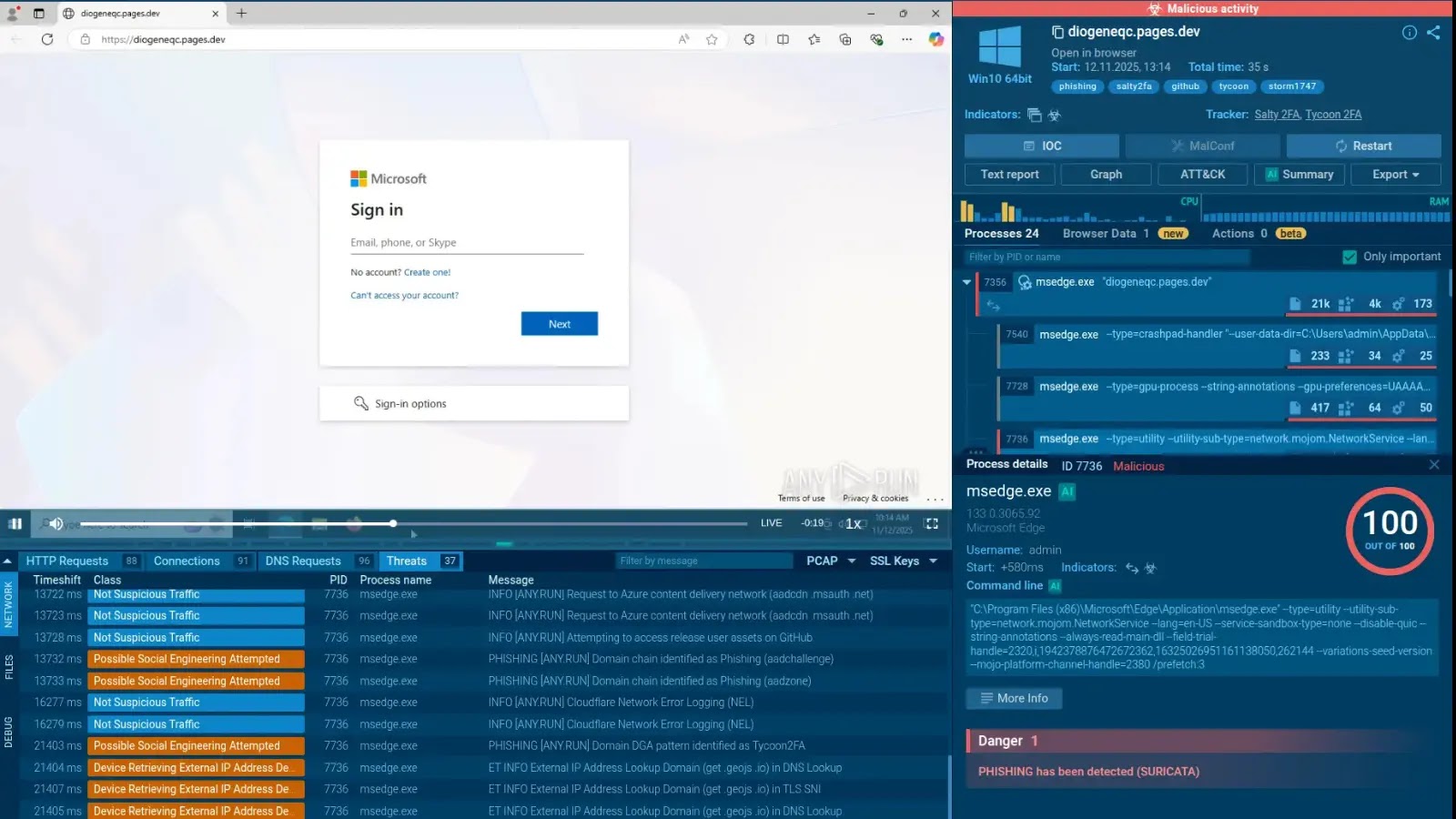
The landscape of cyber threats is in constant flux, with attackers continuously refining their methodologies. A new and concerning development has emerged in the realm of phishing: the convergence of two distinct Phishing-as-a-Service (PhaaS) kits, Salty2FA and Tycoon2FA. This fusion marks a significant shift in how sophisticated phishing campaigns are executed, particularly when targeting enterprise users. Traditionally, phishing kits maintain unique signatures in their code and delivery mechanisms. However, recent campaigns demonstrate a dangerous trend where payloads combine elements from both Salty2FA and Tycoon2FA, creating more adaptable and potent attacks designed to steal critical login credentials.
Understanding Salty2FA and Tycoon2FA Phishing Kits
Salty2FA and Tycoon2FA are both prominent PhaaS offerings, each with its own set of features and targeted attack vectors. PhaaS platforms lower the barrier to entry for cybercriminals, allowing even less technically skilled individuals to launch sophisticated phishing campaigns. These kits typically provide pre-built templates, automated credential harvesting capabilities, and often include modules for bypassing multi-factor authentication (MFA).
- Salty2FA: Known for its robust credential harvesting capabilities and often employed in spear-phishing attacks against specific organizations or high-value targets. Its designs are often tailored to mimic enterprise login portals with high fidelity.
- Tycoon2FA: This kit is frequently associated with sophisticated MFA bypass techniques. It often leverages proxy-based phishing, where the attacker’s server acts as a man-in-the-middle, relaying legitimate login requests and intercepting session cookies or MFA tokens in real-time.
The merging of these two kits represents a tactical evolution. Attackers can now leverage the high-fidelity mimicry of Salty2FA alongside the advanced MFA bypass capabilities of Tycoon2FA, creating a hybrid threat that is significantly harder to detect and defend against.
The Convergence: A New Phishing Paradigm
The practice of combining elements from Salty2FA and Tycoon2FA shifts the PhaaS paradigm. Instead of relying on a single, identifiable kit, threat actors are now crafting bespoke phishing payloads by integrating the most effective components of each. This hybridization makes attribution more challenging and allows for a more dynamic attack chain. For instance, an attacker might use Salty2FA’s front-end design to deceive users into entering their credentials, while Tycoon2FA’s backend infrastructure handles the real-time interception of session tokens or MFA codes.
This convergence means security teams can no longer solely rely on detecting the unique signatures of a single known phishing kit. Instead, they must adopt more comprehensive detection strategies that look for broader patterns of malicious activity, including unusual login attempts, suspicious redirects, and anomalous network traffic that might indicate a man-in-the-middle attack facilitated by kits like Tycoon2FA.
Targeting Enterprise Users and Credential Theft
Enterprise users are prime targets for these combined phishing kits due to the high value of their access. Compromised enterprise credentials can lead to:
- Data Breaches: Access to sensitive company information, intellectual property, and customer data.
- Ransomware Attacks: Initial access foothold for deploying ransomware across internal networks.
- Business Email Compromise (BEC): Impersonation of executives or employees to conduct fraudulent financial transactions.
- Supply Chain Attacks: Gaining access to partner or client systems through compromised enterprise accounts.
The primary goal remains credential theft. By successfully harvesting usernames, passwords, and bypassing MFA, attackers gain unauthorized access to corporate networks, cloud services, and other critical resources, paving the way for further malicious activities.
Remediation Actions and Proactive Defense
Defending against these evolving phishing threats requires a multi-layered and proactive approach. Organizations must prioritize both technical controls and robust employee education.
- Enhanced Email Security Gateways: Implement advanced email security solutions that can detect sophisticated phishing attempts, including those using URL redirects, polymorphic links, and dynamic content. Configure DMARC, DKIM, and SPF records rigorously to prevent email spoofing.
- Multi-Factor Authentication (MFA) Stronger Than SMS: While MFA is crucial, not all MFA is created equal. Implement FIDO2/WebAuthn hardware tokens or app-based authenticator codes preferentially over SMS-based MFA, which is more susceptible to interception (e.g., SIM swapping attacks).
- Employee Security Awareness Training: Conduct regular, up-to-date training sessions emphasizing the dangers of phishing, how to identify suspicious emails (even seemingly legitimate ones), and the importance of reporting anomalies. Simulate phishing attacks to test user vigilance.
- Endpoint Detection and Response (EDR) Solutions: Deploy EDR tools to monitor endpoint activity for suspicious processes, network connections, and file modifications that might indicate a successful phishing compromise.
- Network Traffic Analysis: Utilize network monitoring tools to detect unusual traffic patterns, especially connections to known malicious domains or deviations from baseline user behavior.
- Regular Penetration Testing and Vulnerability Assessments: Proactively identify weaknesses in your security posture that could be exploited by phishing attacks.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan for phishing attacks to ensure rapid detection, containment, eradication, and recovery.
Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Proofpoint / Mimecast | Advanced Email Security, Phishing Protection | Proofpoint / Mimecast |
| YubiKey | Hardware FIDO2/WebAuthn MFA Tokens | Yubico |
| ThreatConnect / Anomali | Threat Intelligence Platforms for Phishing Indicators | ThreatConnect / Anomali |
| KnowBe4 / Cofense | Security Awareness Training & Phishing Simulations | KnowBe4 / Cofense |
| Microsoft Defender for Endpoint / CrowdStrike Falcon | EDR for Endpoint Monitoring and Threat Detection | Microsoft / CrowdStrike |
Conclusion
The emergence of hybrid phishing kits combining elements of Salty2FA and Tycoon2FA signifies a more sophisticated and adaptable threat landscape. Enterprise users are squarely in the crosshairs, making robust defenses more critical than ever. Organizations must move beyond basic phishing detection and invest in advanced email security, stronger MFA mechanisms, continuous employee education, and comprehensive endpoint and network monitoring. Remaining vigilant and proactive in adopting multi-layered security strategies is essential to protect against these evolving PhaaS-driven attacks and safeguard valuable organizational assets.





