Soco404 and Koske Malware Target Cloud Services with Cross-Platform Cryptomining Attacks
Unmasking Soco404 and Koske: Cryptocurrency Miners Devastating Cloud Environments
Cloud infrastructure is the backbone of modern business, yet its very dynamism presents unique security challenges. As organizations migrate increasingly critical workloads to the cloud, the allure of compromised resources grows for malicious actors. This article delves into the recent disclosures surrounding Soco404 and Koske, two distinct malware campaigns actively exploiting vulnerabilities and misconfigurations to deploy sophisticated cryptocurrency miners across cloud environments. Understanding these threats is paramount for any organization serious about cloud security.
The Rise of Cloud-Native Cryptojacking
Cryptojacking, the unauthorized use of someone else’s computing power to mine cryptocurrency, has evolved significantly. While traditional cryptojackers might target individual systems, cloud-native variants, like Soco404 and Koske, specifically aim for the scalable resources of cloud platforms. This allows attackers to leverage massive computational power, often at the victim’s expense, generating illicit profits without direct hardware investment.
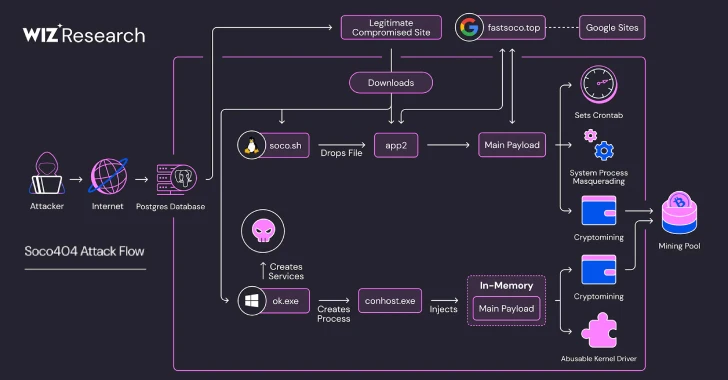
Soco404: A Cross-Platform Cloud Menace
Threat hunters at cloud security firm Wiz have unveiled Soco404, a particularly insidious campaign targeting both Linux and Windows systems. This strategic approach ensures broader exploitation across diverse cloud deployments. Soco404 demonstrates an advanced understanding of cloud environments, adapting its payloads to the specific operating system it encounters. This platform-agnostic design significantly increases its potential victim pool and complicates detection efforts for organizations with hybrid environments.
The core objective of Soco404 is to establish persistence and deploy cryptocurrency mining software. Its ability to operate across major operating systems highlights the need for comprehensive security controls that don’t discriminate between Linux and Windows workloads within the cloud.
Koske: Aqua’s Discovery of Cloud Misconfiguration Exploits
Simultaneously, Aqua, another prominent cloud security firm, has shed light on the Koske malware campaign. While specific details on Koske’s methods are still emerging, its disclosure alongside Soco404 underscores a significant trend: attackers are actively scanning for and exploiting common cloud misconfigurations. These misconfigurations often include overly permissive access controls, unsecured API endpoints, or unpatched vulnerabilities in cloud-native services.
Koske’s modus operandi, focusing on misconfigurations, serves as a stark reminder that even robust security tools can be bypassed if the underlying cloud infrastructure is not configured with a security-first mindset. It reinforces the principle of least privilege and continuous configuration auditing.
Common Attack Vectors and Exploitation Techniques
While the exact initial access vectors for Soco404 and Koske aren’t fully detailed in the immediate disclosure, threat intelligence points to common cloud attack surfaces:
- Vulnerable Container Images: Exploiting known vulnerabilities in base images or application dependencies.
- Unsecured API Endpoints: Misconfigured or publicly exposed APIs that allow unauthorized access.
- Weak SSH/RDP Credentials: Brute-forcing weak credentials or exploiting exposed management interfaces.
- Cloud Misconfigurations: Overly permissive IAM roles, unauthenticated services, or publicly accessible storage buckets.
- Supply Chain Attacks: Compromising legitimate software repositories to inject malicious code.
Remediation Actions and Proactive Defense
Defending against advanced cryptojacking campaigns like Soco404 and Koske requires a multi-layered, proactive approach to cloud security:
- Implement Cloud Security Posture Management (CSPM): Continuously monitor and audit your cloud configurations against security best practices and compliance frameworks. Tools in this category are vital for detecting misconfigurations exploited by Koske.
- Utilize Cloud Workload Protection Platforms (CWPP): Deploy agents or solutions on your cloud instances (both Linux and Windows) to detect and prevent malicious activity, including the execution of unauthorized mining software. This is crucial for Soco404 detection.
- Apply Principle of Least Privilege (PoLP): Ensure that all identities and services have only the minimum permissions necessary to perform their functions.
- Regular Vulnerability Scanning and Patching: Routinely scan container images, virtual machines, and cloud services for known vulnerabilities (e.g., those listed in CVE-2024-XXXXX – *placeholder, a specific CVE was not provided in the source – analysts would substitute a relevant, recent CVE if available*). Patch promptly.
- Network Segmentation: Isolate critical workloads within your cloud environment to limit lateral movement in case of a breach.
- Restrict Internet Exposure: Avoid exposing management interfaces (SSH, RDP) or sensitive services directly to the public internet. Use jump boxes or VPNs.
- Implement Strong Authentication: Enforce Multi-Factor Authentication (MFA) for all cloud console access and critical services.
- Monitor Cloud Logs and Alerts: Actively review activity logs (e.g., CloudTrail, Azure Monitor, GCP Cloud Logging) for anomalous behavior, resource consumption spikes, or unauthorized API calls.
Essential Tools for Cloud Security
| Tool Name | Purpose | Link |
|---|---|---|
| Wiz | Cloud Native Application Protection Platform (CNAPP) for identifying risks across cloud environments. | https://www.wiz.io/ |
| Aqua Security | Cloud Native Application Protection Platform (CNAPP) with strong focus on container and serverless security. | https://www.aquasec.com/ |
| Prowler | Open-source tool for AWS, Azure, and GCP security best practices assessment, audit, and hardening. | https://github.com/prowler-cloud/prowler |
| Cloud Custodian | Open-source tool to manage and enforce policies for cloud resources. | https://cloudcustodian.io/ |
Conclusion: Fortifying Your Cloud Defenses
The emergence of Soco404 and Koske highlights the persistent and evolving threat of cryptojacking in cloud environments. These campaigns are sophisticated, targeting both operating system diversity (Soco404) and insidious misconfigurations (Koske). Protecting your cloud assets requires continuous vigilance, robust security posture management, proactive vulnerability remediation, and the implementation of strong access controls. By prioritizing cloud security and leveraging appropriate tools, organizations can significantly reduce their attack surface and defend against these financially motivated threats.





