Stronger Incident Prevention Takes Just One CISO Decision
In the complex theater of cybersecurity, a persistent and often misleading narrative suggests that when the digital battleground gets noisy, the immediate solution is more boots on the ground. More security analysts, more shifts, a larger team – it feels like a proactive, responsible move. Leadership teams often find comfort in the optics of increased headcount, reflecting decisive action to stakeholders.
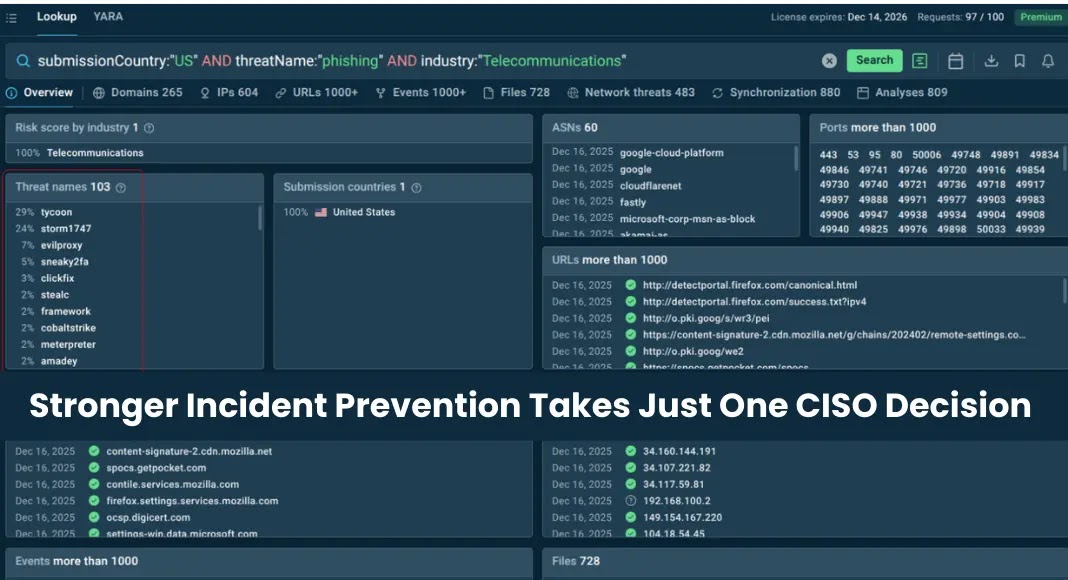
However, as seasoned cybersecurity professionals understand, this approach frequently misses the mark. The core issue behind an inefficient Security Operations Center (SOC) is rarely a shortage of personnel. Instead, it’s a fundamental problem with the signal. Too much noise, too little actionable intelligence – that’s the real adversary.
The Illusion of More: Why Headcount Isn’t the Answer to Incident Prevention
Across various industries, organizations frequently fall into the trap of believing that scaling their security team linearly with the perceived threat level will automatically lead to better security outcomes. This ‘more people’ philosophy, while intuitively appealing, often masks deeper, systemic inefficiencies. The article from CybersecurityNews.com aptly highlights this as a “comforting illusion.” When an organization is flooded with alerts, many of which are false positives or low-priority, simply adding more analysts to sift through the deluge doesn’t solve the underlying problem. It merely shifts the burden and rapidly leads to burnout, reduced morale, and continued exposure to genuine threats.
The problem isn’t the capacity to respond; it’s the clarity of what to respond to. This ‘signal problem’ manifests as alert fatigue, stretched resources, and an inability to distinguish critical incidents from background chatter. Without a clear signal, even the most dedicated and skilled teams will struggle to maintain effective incident prevention and response capabilities.
The CISO’s Pivotal Decision: Shifting Focus to Signal Clarity
The single crucial decision a Chief Information Security Officer (CISO) can make to dramatically improve incident prevention isn’t about budgeting for more staff; it’s about investing in the intelligence pipeline. This means prioritizing technologies and processes that refine the signal – making relevant threats stand out and irrelevant noise recede. It’s about empowering the existing team with better tools and a clearer scope, rather than just expanding the team’s size.
Consider the impact of intelligent automation and orchestration on incident prevention. For instance, a well-implemented Security Orchestration, Automation, and Response (SOAR) platform can automatically triage common alerts, correlate data from disparate sources, and even initiate initial containment steps without human intervention. This frees up analysts to focus on truly complex and high-impact incidents, thereby enhancing the overall effectiveness of incident prevention.
Refining the Signal: Strategic Investments for Proactive Security
To move from a reactive “more people” strategy to a proactive “clearer signal” strategy, CISOs should focus on several key areas:
- Threat Intelligence Platforms (TIPs): Integrating up-to-date threat intelligence helps contextualize alerts, identifying known malicious indicators and reducing the noise from benign activities. This proactive knowledge can prevent incidents before they fully escalate.
- Automated Triage and Prioritization: Implementing systems that automatically score and prioritize security events based on criticality and potential impact allows analysts to focus their efforts where they matter most. This directly addresses the signal problem by highlighting true threats.
- Behavioral Analytics: Advanced analytics tools that baseline normal user and system behavior can detect anomalies that indicate insider threats or sophisticated attacks, often catching incidents that traditional signature-based methods miss.
- Security Orchestration, Automation, and Response (SOAR): Platforms that integrate various security tools and automate routine tasks significantly reduce the manual burden on analysts, allowing for faster and more consistent responses to verified threats.
- Contextual Enrichment: Automatically enriching alerts with relevant context from CMDBs, vulnerability scanners, and identity management systems provides analysts with a complete picture, enabling quicker and more informed decisions.
Remediation Actions: Empowering Your Existing Security Team
Instead of merely adding headcount, focus on strategic improvements that empower your current team and enhance prevention capabilities:
- Audit Current Alerting Mechanisms: Regularly review and fine-tune your security information and event management (SIEM) rules. Eliminate redundant or low-value alerts.
- Implement SOAR Playbooks: Develop and automate playbooks for common incident types to streamline response and reduce manual effort.
- Invest in Advanced Analytics: Deploy tools that leverage machine learning and AI to detect sophisticated, unknown threats.
- Prioritize Training on New Technologies: Ensure your security team is proficient in using the advanced tools implemented to improve signal clarity.
- Foster Communication and Feedback: Create open channels for analysts to provide feedback on alert effectiveness and tool usability, driving continuous improvement.
- Focus on Proactive Threat Hunting: With reduced alert noise, allocate resources to proactive threat hunting, seeking out adversaries before they can cause significant damage.
The shift from a headcount-driven approach to a signal-driven strategy is not just about efficiency; it’s about efficacy. It’s about ensuring that your cybersecurity investments yield tangible improvements in incident prevention and response.
Conclusion: The Smart CISO’s Path to Stronger Prevention
The notion that more people automatically equals better security is a pitfall many organizations stumble into. As the CybersecurityNews.com article illuminates, the real leverage for stronger incident prevention lies not in expanding the team but in refining the signal. A single, decisive choice by the CISO to prioritize intelligent tools and processes that cut through the noise can transform a reactive, overwhelmed SOC into a proactive, highly effective command center. This strategic pivot empowers existing security professionals to focus on genuine threats, leading to a more resilient and secure enterprise.





