The Ultimate Battle: Enterprise Browsers vs. Secure Browser Extensions
The Ultimate Battle: Enterprise Browsers vs. Secure Browser Extensions
The modern enterprise landscape is defined by its reliance on the web browser. It’s the primary interface for applications, collaboration, and data access. Yet, herein lies a paradox: while the majority of work, and indeed, a significant portion of organizational risk, now resides within the browser, traditional security tools often operate with a debilitating blind spot. They struggle to gain granular visibility into browser-native activities, leaving a critical gap in an organization’s defense posture.
Security leaders grappling with this challenge typically face a strategic fork in the road: should they deploy a dedicated, purpose-built enterprise browser, or should they augment the widely adopted, familiar browsers their employees already use with an enterprise-grade control layer? This article delves into this “Ultimate Battle,” dissecting the advantages and disadvantages of each approach to empower informed decision-making.
The Browser as the New Endpoint
For decades, the endpoint was synonymous with the physical device – a laptop, a desktop, or a server. Security strategies, tools, and budgets were allocated accordingly. However, the shift to cloud-native applications, Software-as-a-Service (SaaS) consumption, and ubiquitous web access has fundamentally redefined the “endpoint” to include the browser itself. Data exfiltration, phishing attacks, credential theft, and malware delivery increasingly initiate or culminate within the browser’s confines.
Consider the recent vulnerabilities impacting browser engines. For instance, CVE-2023-4863, a heap buffer overflow in WebP, and CVE-2023-5217, an integer overflow in the vp8 encoding, both highlight how a simple image format or video codec can become an attack vector within the browser, demonstrating the critical need for robust in-browser security.
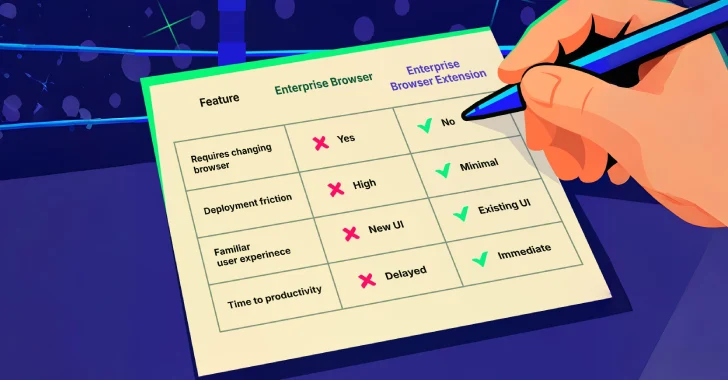
The Dedicated Enterprise Browser: A Walled Garden Approach
An enterprise browser is a hardened version of a standard browser, often built on Chromium or an alternative engine, but specifically designed for organizational use. It aims to create a tightly controlled security perimeter around browser activity from the ground up.
- Enhanced Control: Centralized management of policies, extensions, and configurations. Organizations can dictate what content is accessible, what data can be uploaded or downloaded, and even enforce specific security protocols.
- Application Segregation: Often capable of isolating sensitive applications (e.g., HR, finance) into dedicated, secure browser instances, preventing cross-contamination from less secure browsing activities.
- Built-in Security Features: May include integrated data loss prevention (DLP), threat intelligence feeds, content disarm and reconstruction (CDR), and granular access controls directly within the browser’s architecture.
- Reduced Attack Surface: By stripping unnecessary features and enforcing stringent security policies, the overall attack surface presented by the browser can be significantly reduced.
However, the enterprise browser model introduces adoption challenges. Employees are accustomed to their existing browser’s specific features, extensions, and user interface. Forcing a switch can lead to resistance, reduced productivity, and even shadow IT if users circumvent mandates to use familiar tools.
Secure Browser Extensions: Augmenting Familiarity
The alternative is to deploy secure browser extensions that sit atop existing, employee-preferred browsers like Chrome, Edge, or Firefox. These extensions act as an enterprise-grade control layer, providing security capabilities without forcing a complete browser overhaul.
- Seamless Integration: Leverages existing user habits, reducing friction and training overhead. Employees can continue using the browser they know and trust.
- Granular Control: Extensions can monitor, analyze, and control browser activities, enforce data policies, and detect threats in real-time. This can include preventing unauthorized data uploads, flagging suspicious downloads, or blocking access to malicious websites.
- Rapid Deployment: Typically easier and faster to deploy across an organization compared to a full browser replacement.
- Cost-Effective: May present a more cost-effective solution, as it leverages existing infrastructure and avoids the need for extensive migration.
The primary concern with extensions lies in their inherent limitations. They operate within the browser’s sandbox and are subject to its permissions and limitations. Furthermore, the risk of “extension fatigue” – too many extensions slowing down performance or conflicting – is a valid concern. The effectiveness also depends heavily on the robustness and comprehensiveness of the specific extension suite chosen.
Remediation Actions and Strategic Choices
Regardless of the chosen path, addressing browser-based risk requires a multi-faceted approach. Here are key remediation actions:
- Policy Enforcement: Implement strict acceptable use policies for browser usage, outlining prohibited activities, authorized extensions, and data handling procedures.
- Regular Updates and Patching: Ensure all browsers, whether enterprise-specific or commercial, are kept up-to-date with the latest security patches to mitigate known vulnerabilities like CVE-2024-0519 (a use-after-free in Chrome V8) or CVE-2024-0752 (a type confusion in WebAssembly).
- User Education: Train employees on identifying phishing attempts, recognizing suspicious downloads, and the importance of secure browsing habits. User behavior remains a critical component of browser security.
- Zero Trust Principles: Apply zero-trust principles to browser access, assuming no user or device is inherently trustworthy and requiring continuous verification.
- Integration with SIEM/SOAR: Ensure browser security solutions integrate with existing Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platforms for centralized logging, alerting, and automated response.
Conclusion
The choice between a dedicated enterprise browser and an enterprise-grade extension suite boils down to an organization’s specific risk tolerance, budget, existing infrastructure, and most importantly, its user base’s adaptability. An enterprise browser offers a comprehensive, tightly controlled environment for organizations with high-security requirements and users amenable to change. Conversely, secure browser extensions provide a pragmatic, less disruptive path to elevating browser security for organizations prioritizing user experience and familiar workflows. In either scenario, the imperative remains: to gain visibility and control over the browser, the new frontier of enterprise risk.





