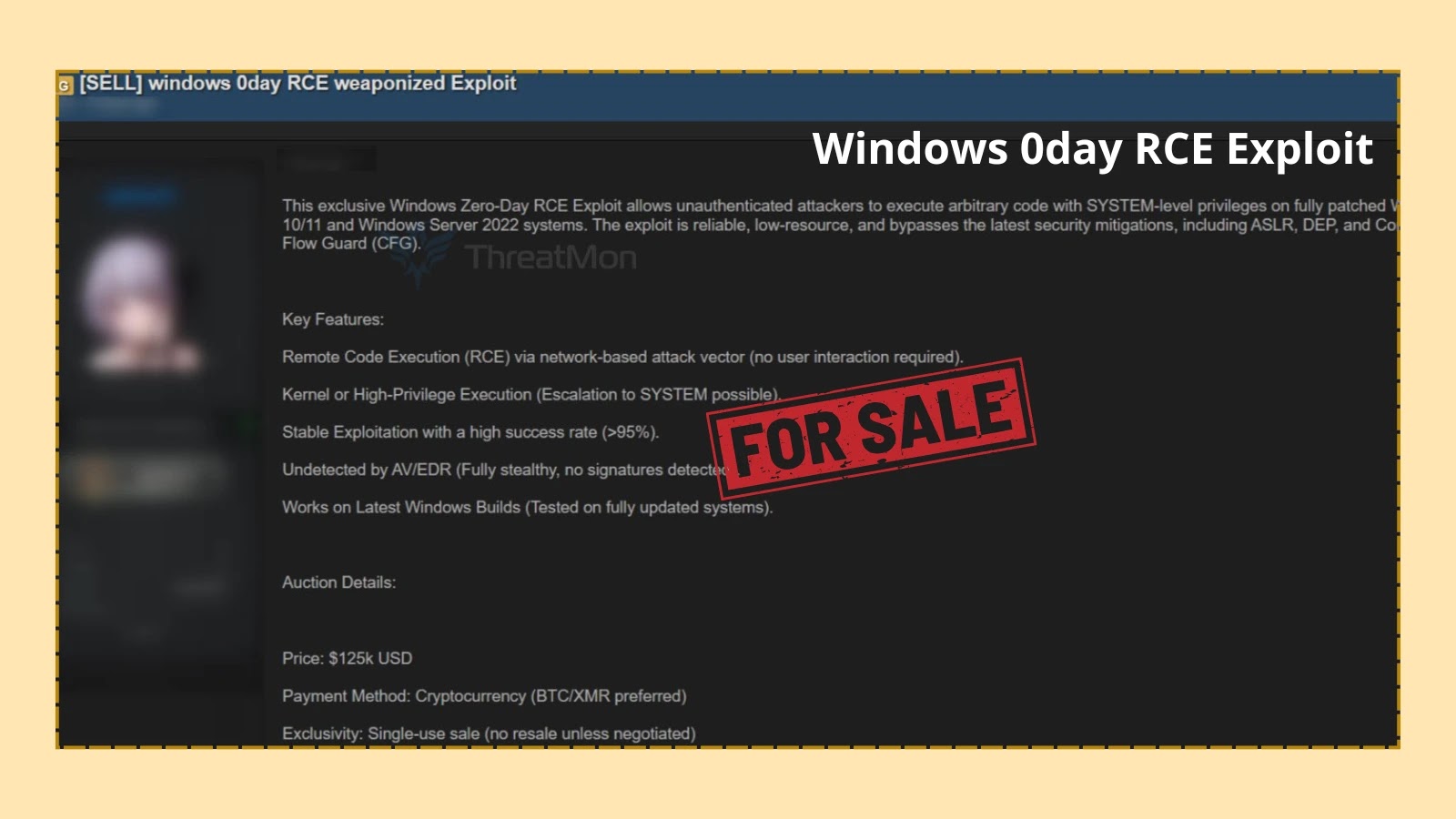
Threat Actors Allegedly Listed Windows Zero-Day RCE Exploit For Sale on Dark Web
Unsettling Revelation: Windows Zero-Day RCE Exploit Allegedly for Sale on Dark Web
A disturbing report has surfaced, indicating that an alleged threat actor is advertising a critical Windows Zero-Day Remote Code Execution (RCE) exploit for sale on the dark web. This development sends a shiver down the spines of cybersecurity professionals, as the exploit purportedly targets fully updated versions of Windows 10, Windows 11, and Windows Server 2022. If legitimate, this offering represents a severe and immediate threat to a vast number of systems globally, bypassing current security measures and potentially granting attackers unfettered access.
The Alleged Exploit: A Deep Dive into Its Capabilities
The dark web posting, initially reported by ThreatMon, claims this weaponized exploit code can achieve SYSTEM-level privileges. What makes this particularly alarming is the assertion that it requires no prior authentication or user interaction. This means an attacker could potentially execute malicious code on a vulnerable system merely by reaching it over the network, without needing to trick a user into clicking a link or opening a file. Such a capability aligns with the most dangerous forms of RCE vulnerabilities, often referred to as “wormable” due to their potential for rapid self-propagation across networks.
The reference to bypassing “intrinsic Windows” security features suggests the exploit leverages a fundamental flaw or misconfiguration that current security patches do not address. This underscores the difficulty in defending against zero-day threats, as their existence is unknown to vendors and security researchers until they are actively exploited in the wild or, as in this case, publicly advertised.
Understanding Zero-Day Exploits and RCE
A zero-day exploit refers to a cyberattack that occurs on the same day a software vulnerability becomes publicly known. This means developers have had zero days to patch it, leaving users exposed. In this context, the alleged sale of a Windows zero-day means there is no official patch or workaround available from Microsoft at this time, making immediate defense extremely challenging.
Remote Code Execution (RCE) is a severe type of vulnerability that allows an attacker to run arbitrary code on a remote machine. When an RCE vulnerability grants SYSTEM-level privileges, it essentially gives the attacker complete control over the compromised system, including the ability to install malware, modify data, create new user accounts, and move laterally within a network. This particular alleged RCE is even more concerning due to the claimed bypass of authentication and user interaction, minimizing the attack surface and increasing its potential impact.
Potential Impact and Threat Landscape
The availability of such an exploit on the dark web could significantly escalate the threat landscape. Here’s why:
- Widespread Targeting: Windows 10, Windows 11, and Windows Server 2022 are widely deployed operating systems across enterprises, government agencies, and individual users.
- Ease of Use: Weaponized exploit code lowers the barrier to entry for less sophisticated threat actors, enabling more widespread attacks.
- Sophisticated Attacks: Advanced Persistent Threat (APT) groups and state-sponsored actors could leverage this for highly targeted and stealthy operations.
- Ransomware and Data Exfiltration: RCE with SYSTEM privileges is ideal for deploying ransomware, exfiltrating sensitive data, or establishing long-term persistence within compromised networks.
Remediation Actions and Proactive Defense
Given the unconfirmed nature of the exploit and the lack of an official patch, specific remediation steps are difficult. However, organizations and individuals must adopt a proactive and layered defense strategy:
- Vigilant Monitoring: Continuously monitor network traffic for anomalous behavior, especially outbound connections from systems that typically do not initiate them. Look for signs of unauthorized access or peculiar process execution.
- Network Segmentation: Implement strong network segmentation to limit the lateral movement of an attacker if a system is compromised. Isolate critical assets.
- Principle of Least Privilege: Ensure all users and applications operate with the minimum necessary permissions. This can limit the impact even if SYSTEM-level RCE is achieved.
- Endpoint Detection and Response (EDR): Utilize EDR solutions to detect and respond to suspicious activities on endpoints that might indicate exploit attempts or post-exploitation activities.
- Application Whitelisting: Implement application whitelisting where feasible, allowing only authorized programs to run, thereby preventing execution of malicious payloads.
- Regular Backups: Maintain comprehensive, offline, and tested backups of all critical data to facilitate recovery in the event of a successful attack.
- Employee Training: Reinforce security awareness training to minimize phishing and social engineering vectors, even though this exploit allegedly requires no user interaction. It’s still a critical defense layer.
- Stay Informed: Closely monitor official advisories from Microsoft and reputable cybersecurity sources for any updates or patches related to potential zero-day vulnerabilities.
Tools for Detection and Mitigation
While specific detection for an unknown zero-day is challenging, these tools can bolster your overall security posture and help detect post-exploitation activities:
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft Defender for Endpoint | Comprehensive EDR for Windows systems, detecting suspicious behaviors and post-exploitation activities. | https://www.microsoft.com/en-us/security/business/threat-protection/microsoft-defender-for-endpoint |
| Wireshark | Network protocol analyzer for deep packet inspection, useful for identifying unusual network traffic patterns. | https://www.wireshark.org/ |
| Sysinternals Suite (Process Monitor, PsExec) | Advanced utilities for monitoring, managing, and troubleshooting Windows systems, aiding in forensic analysis. | https://learn.microsoft.com/en-us/sysinternals/ |
| SIEM Solutions (e.g., Splunk, Elastic Security) | Centralized log management and security information and event management for correlation and anomaly detection. | https://www.splunk.com/ |
| Nessus (Vulnerability Scanner) | Identifies known vulnerabilities and misconfigurations, though it won’t detect this specific zero-day, it helps improve overall security hygiene. | https://www.tenable.com/products/nessus |
Conclusion: A Call for Heightened Vigilance
The alleged listing of a Windows zero-day RCE exploit on the dark web serves as a stark reminder of the continuous and evolving threats in the cybersecurity landscape. While the authenticity of the exploit remains unverified, the mere claim warrants extreme caution and a renewed focus on robust defensive strategies. Organizations and individuals must prioritize layered security, proactive monitoring, and incident response planning to mitigate the potential impact of such critical vulnerabilities. Staying informed and prepared is paramount in navigating these high-stakes scenarios.





