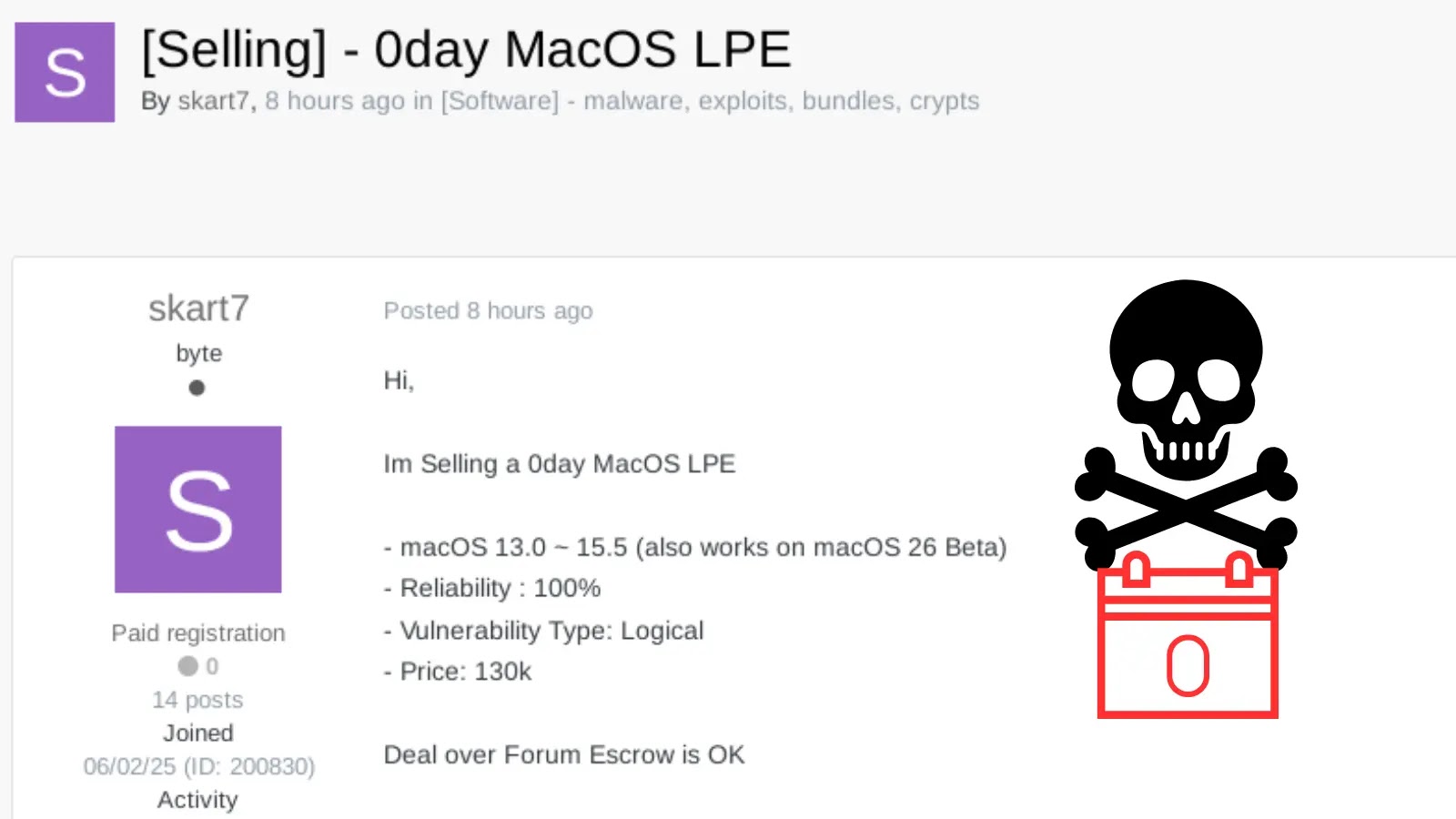
Threat Actors Allegedly Selling macOS 0-day LPE Exploit on Hacker Forums
A disturbing development has surfaced in the underground cybercrime landscape: a threat actor, operating under the moniker “skart7,” is reportedly offering a zero-day Local Privilege Escalation (LPE) exploit for Apple’s macOS operating system on prominent hacker forums. This alleged sale of a high-impact vulnerability poses a significant and immediate threat to macOS users, particularly within enterprise environments and organizations designated as high-value targets. The potential for an unpatched LPE in macOS to be leveraged in sophisticated attacks underscores the critical need for vigilance and robust security posture.
Understanding the macOS 0-day LPE Threat
The term “zero-day” signifies a vulnerability that is unknown to the software vendor (in this case, Apple) and thus has no readily available patch. A Local Privilege Escalation (LPE) exploit allows a malicious actor with limited access to a system to gain higher-level permissions, often administrative or root privileges. This escalation is a crucial step in many advanced persistent threats (APTs) and targeted attacks, enabling attackers to install malware, steal sensitive data, modify system configurations, or establish persistence.
The alleged availability of a macOS 0-day LPE on hacker forums means that sophisticated attack techniques could rapidly proliferate, putting a vast user base at risk. Threat actors could integrate this exploit into their toolkits, enhancing the effectiveness of their phishing campaigns, supply chain attacks, or other initial compromise vectors.
Who is skart7 and What Does This Mean?
“skart7” is the alias of the individual or group claiming to possess and sell this critical macOS LPE exploit. While their true identity and capabilities remain unconfirmed, the public offering of such a valuable exploit on hacker forums suggests a clear intent to profit from the vulnerability. The sale of zero-day exploits is a lucrative business in the cybercriminal underworld, with prices often reflecting the exploit’s impact, reliability, and potential targets.
For organizations, this development implies an elevated risk of compromise. macOS is a prevalent operating system in creative, executive, and development roles, making it a prime target for corporate espionage and data theft. An LPE allows an attacker to move laterally within a network, access sensitive systems, and bypass standard security controls once an initial foothold is established.
Potential Impact and Enterprise Risk
An unpatched macOS LPE has severe implications across various sectors:
- Data Exfiltration: Attackers can gain root access to steal highly sensitive intellectual property, financial data, or personal identifiable information (PII).
- Ransomware Campaigns: Elevated privileges enable ransomware deployment across an entire network, encrypting critical data and demanding payment.
- System Sabotage: Threat actors could disrupt operations by corrupting data, disabling security systems, or injecting malicious code into critical applications.
- Establishing Persistence: LPE allows for the installation of rootkits or backdoors that are difficult to detect and remove, ensuring long-term access for the attacker.
- Lateral Movement: From an exploited macOS device, attackers can often pivot to other systems on the network, expanding their compromise.
Remediation Actions and Mitigations
While a patch from Apple is the definitive solution, organizations and individual users can take proactive steps to mitigate the risks associated with this alleged macOS 0-day LPE:
- Prompt Patching: As soon as Apple releases security updates for macOS (even if not explicitly for this alleged 0-day, regular patching is crucial), apply them immediately. Stay informed by subscribing to Apple’s security advisories.
- Principle of Least Privilege: Ensure all users and applications operate with the minimum necessary permissions. This limits the blast radius if an account or process is compromised.
- Endpoint Detection and Response (EDR): Deploy and configure EDR solutions on all macOS endpoints. EDR can detect anomalous behavior indicative of privilege escalation attempts or post-exploitation activities.
- Application Whitelisting: Implement and strictly enforce application whitelisting policies. This prevents unauthorized executables, including potential exploit payloads, from running on macOS systems.
- Regular Backups: Maintain comprehensive and isolated backups of all critical data. This helps in recovery efforts following a successful attack.
- Network Segmentation: Segment your network to restrict lateral movement. If one macOS device is compromised, strong segmentation can prevent the attack from spreading to other critical systems.
- User Awareness Training: Educate users about phishing, social engineering, and safe browsing practices, as initial access often begins with user interaction.
- Disable Unnecessary Services: Reduce the attack surface by disabling any macOS services or features that are not essential for business operations.
Relevant Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Apple Security Updates | Official patches and security advisories from Apple. | support.apple.com/en-us/HT201222 |
| Osquery | Endpoint visibility and detection of suspicious activity on macOS. | osquery.io |
| Jamf Protect | Endpoint security for macOS, including behavioral analysis and threat prevention. | jamf.com/products/jamf-protect |
| Carbon Black Cloud (VMware) | NGAV and EDR for macOS, offering threat detection and response. | vmware.com/security/products/carbon-black.html |
Conclusion
The reported sale of a macOS 0-day LPE exploit by “skart7” presents a formidable challenge for cybersecurity professionals. While unofficial and unconfirmed by Apple, the mere possibility demands immediate attention and a proactive security stance. Organizations must prioritize their macOS endpoint security, implement robust EDR capabilities, enforce the principle of least privilege, and prepare for potential exploitation attempts. Staying informed through official security channels and maintaining a vigilant security posture are paramount to defending against this evolving threat landscape.





