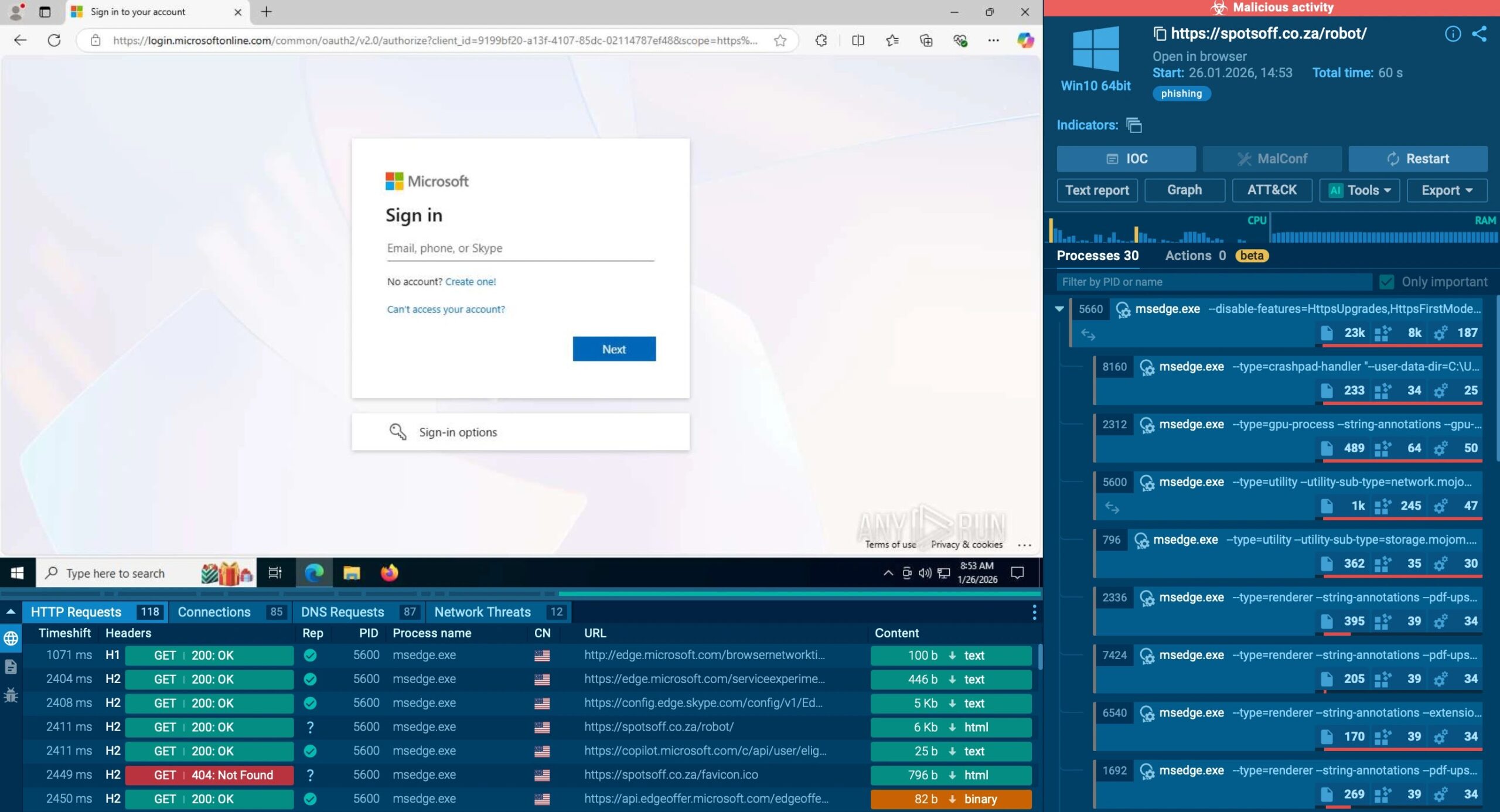
Threat Actors Leverage Real Enterprise Email Threads to Deliver Phishing Links
The Deceptive Thread: When Legitimate Enterprise Emails Become Phishing Lures
Imagine a critical business discussion unfolding in your inbox, complete with trusted colleagues and familiar subject lines. Now, imagine a malicious actor seamlessly inserting themselves into that very conversation, weaponizing its legitimacy to steal your credentials. This isn’t a hypothetical scare tactic; it’s a rapidly evolving threat highlighted by a recent report detailing how threat actors are leveraging real enterprise email threads to deliver sophisticated phishing links. This insidious technique bypasses traditional defenses by exploiting trust, making it a critical concern for every organization.
Anatomy of a Supply Chain Phishing Attack
The reported incident involved a highly targeted supply chain phishing attack. Threat actors infiltrated an ongoing email conversation among C-suite executives, focusing on a document awaiting final approval. This specific context is crucial: it targets individuals with high-level access and exploits the urgency often associated with executive-level communication.
- Compromised Account: The attack originated from a compromised sales manager account belonging to an enterprise contractor. This highlights the vulnerability inherent in supply chain relationships, where a weak link at a partner organization can directly impact your own security posture.
- Impersonation and Trust: Posing as a legitimate participant in the thread, the intruder replied directly, maintaining the illusion of a trusted communication. This familiarity is the cornerstone of the attack’s effectiveness.
- Malicious Payload: The reply contained a phishing link expertly crafted to mimic a Microsoft authentication form. By leveraging the ongoing conversation, the threat actor significantly increased the likelihood of the recipients clicking the malicious link, believing it to be a genuine request related to the document approval.
Why “Thread Hijacking” is So Dangerous
This method, often referred to as “thread hijacking” or “conversation hijacking,” presents several unique challenges:
- Bypasses Traditional Filters: Because the email originates from a seemingly legitimate sender and is part of an ongoing, trusted thread, it often bypasses standard email security filters that might flag external or suspicious links.
- Exploits Human Trust: Users are conditioned to trust emails within existing conversations, especially those involving known colleagues or partners. This trust is the attacker’s most potent weapon.
- Increased Credibility: The context of the conversation lends immense credibility to the phishing attempt. If a link appears in a thread about “Project X Document Final Review,” a user is far more likely to believe it’s legitimate than if it arrived in an unsolicited email.
- Supply Chain Vulnerability: As seen in the example, a compromise at a third-party vendor can directly lead to attacks on the primary organization, underscoring the interconnectedness of modern business environments.
Remediation Actions: Fortifying Your Defenses
Defending against these sophisticated attacks requires a multi-layered approach that combines technical controls with robust security awareness training.
Technical Controls:
- Multi-Factor Authentication (MFA) Everywhere: Implement strong MFA for all enterprise accounts, especially those with privileged access. Even if credentials are compromised, MFA acts as a crucial second line of defense.
- Advanced Email Security Gateways: Deploy email security solutions with advanced threat protection, behavioral analysis, and sandboxing capabilities. These tools can often detect anomalies even within trusted threads, such as suspicious links or unusual sender behavior.
- Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): These solutions can detect and respond to suspicious activity on endpoints, such as attempts to access malicious websites after clicking a phishing link.
- Conditional Access Policies: Implement policies that restrict access to sensitive resources based on user location, device health, and other contextual factors.
- Regular Security Audits and Penetration Testing: Proactively identify vulnerabilities in your systems and applications, including those related to third-party integrations.
Security Awareness and Training:
- Continuous Phishing Simulations: Regularly conduct simulated phishing attacks, including those mimicking thread hijacking scenarios, to train employees to recognize and report suspicious emails.
- Verify Unexpected Requests: Educate users to verify any unexpected requests for login credentials or sensitive information, even if they appear to come from a known sender or within an ongoing conversation. Encourage out-of-band verification (e.g., a phone call using a known number, not one from the email).
- “Think Before You Click”: Reinforce the importance of scrutinizing URLs, even if they look legitimate. Hovering over links can reveal the true destination.
- Reporting Mechanisms: Ensure employees know how to quickly and easily report suspicious emails to the IT security team.
Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft Defender for Office 365 | Advanced threat protection for email and collaboration tools, including phishing detection and sandboxing. | Official Website |
| Proofpoint Email Security | Comprehensive email threat protection, including advanced phishing and imposter threat detection. | Official Website |
| Mimecast Email Security | Cloud-based email security for inbound/outbound email, archiving, and business continuity. | Official Website |
| KnowBe4 Security Awareness Training | User training platform specializing in phishing simulations and security awareness education. | Official Website |
Protecting Your Organization from Conversational Scams
The evolution of phishing attacks from simple spam to sophisticated thread hijacking underscores the critical need for vigilance and adaptive security strategies. By understanding how threat actors exploit trust and legitimate communication channels, organizations can implement more effective defenses. Strong technical controls combined with continuous security awareness training are not merely best practices; they are essential safeguards in the ongoing battle against cyber adversaries who are constantly refining their tactics to breach the most secure perimeters.





