Threat Actors Weaponize ChatGPT and Grok Conversations to Deploy AMOS Stealer
The New Frontier of Cybercrime: Threat Actors Weaponize AI Conversations to Deploy AMOS Stealer
Cybersecurity’s battleground constantly shifts. What was once a focus on phishing emails and spoofed websites has evolved into a more insidious threat: the weaponization of trusted platforms. Threat actors are now exploiting the inherent trust users place in cutting-edge AI services like ChatGPT and Grok, leveraging genuine conversations to distribute sophisticated malware. This alarming development, highlighted by a recent campaign discovered by Huntress, marks a significant escalation in how attackers bypass traditional defenses and target unsuspecting users.
Weaponizing Trust: How AI Platforms Become Distribution Channels
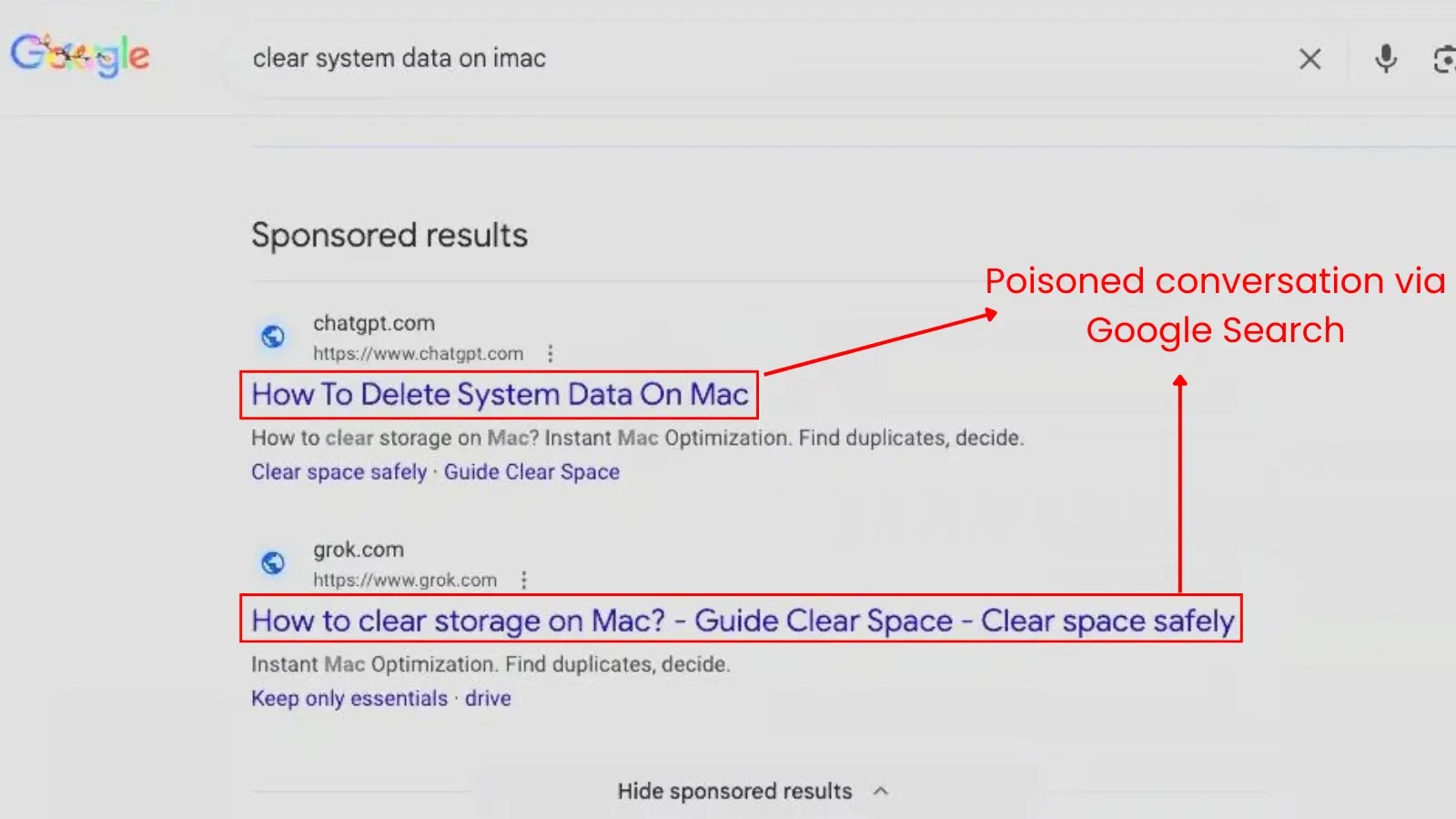
The core of this new attack vector lies in its deceptive simplicity. Instead of fabricating elaborate phishing schemes or mimicking known brands, threat actors are actively utilizing legitimate AI services to host and distribute malicious payloads. This sophisticated approach leverages the credibility of platforms like ChatGPT and Grok, making it incredibly difficult for users to discern between legitimate content and harmful links.
Traditional attack methods often rely on social engineering tactics that raise red flags, such as suspicious email addresses or poorly designed fake login pages. However, when the malicious payload is delivered via a seemingly harmless conversation within a trusted AI interface, the psychological barrier to engagement is significantly lowered. Users are conditioned to trust the responses from these AI models, making them more susceptible to clicking on embedded links or downloading files recommended by the AI.
The Infection Chain: From AI Chat to AMOS Stealer
The campaign, identified by Huntress on December 5, 2025, reveals a clear infection chain. Attackers are embedding links within ChatGPT and Grok conversations that, when clicked, initiate the download of the Atomic macOS Stealer (AMOS). AMOS is a particularly dangerous piece of malware designed to exfiltrate sensitive information from macOS systems. This includes:
- Saved passwords from browsers and keychains.
- Cryptocurrency wallet data.
- Browser cookies and browsing history.
- System information and files.
The seamless integration of the malicious link within an AI conversational flow makes it less likely for users to question its legitimacy. This method bypasses many email and web filtering solutions that are designed to flag suspicious domains or attachments, as the initial interaction originates from a reputable source.
Understanding Atomic macOS Stealer (AMOS)
The Atomic macOS Stealer (AMOS) is not a new threat, but its distribution method is. AMOS is a potent information stealer specifically designed to target macOS environments. Its capabilities extend to a wide range of sensitive data, posing a significant risk to individuals and organizations running Apple’s operating system. The malware’s ability to siphon off credentials, financial data, and personal files makes it a prime tool for financial fraud, identity theft, and corporate espionage. The threat actors behind this campaign are clearly aiming for high-value targets or mass data exfiltration.
Remediation Actions and Proactive Defense
Given the evolving nature of these attacks, a multi-layered defense strategy is paramount:
- User Education: Implement rigorous security awareness training for all users. Emphasize the importance of verifying links, even those originating from seemingly trusted sources like AI chat platforms. Users should be taught to hover over links to check the URL before clicking and to question unexpected downloads or requests.
- Endpoint Detection and Response (EDR): Deploy robust EDR solutions capable of detecting abnormal process behavior, unauthorized file access, and suspicious network connections on macOS endpoints.
- Network Traffic Monitoring: Implement advanced network monitoring to identify outbound connections to known command-and-control (C2) servers or suspicious IPs often associated with malware activity.
- Software Updates: Ensure all operating systems, applications, and security software are kept up to date with the latest patches. This helps mitigate vulnerabilities that AMOS or similar malware might exploit.
- Strong Authentication: Enforce multi-factor authentication (MFA) for all critical accounts, especially those accessing sensitive data or financial services. This adds an extra layer of security even if credentials are stolen.
- Regular Backups: Maintain regular, encrypted backups of critical data offline. This minimizes the impact of data loss in case of a successful compromise.
- Antivirus/Anti-Malware: Utilize a reputable antivirus or anti-malware solution specifically designed for macOS that includes real-time protection and behavioral analysis capabilities.
Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Endpoint Detection and Response (EDR) Solutions | Detects and responds to advanced threats on endpoints, including malware infections and suspicious activities. | https://www.gartner.com/en/reviews/market/endpoint-detection-response-solutions |
| Network Intrusion Detection/Prevention Systems (NIDS/NIPS) | Monitors network traffic for malicious activity and can block known threats. | https://www.snort.org/ |
| Malwarebytes for Mac | Anti-malware solution offering real-time protection and threat detection for macOS. | https://www.malwarebytes.com/mac |
| Little Snitch | Firewall application for macOS that monitors outbound network connections, alerting users to suspicious activity. | https://www.obdev.at/products/littlesnitch/index.html |
| OSQuery | Open-source tool for querying operating system data using SQL, useful for incident response and threat hunting. | https://osquery.io/ |
Conclusion: Adapting to the AI-Empowered Threat Landscape
The weaponization of ChatGPT and Grok conversations to deploy AMOS Stealer represents a sophisticated evolution in cyberattack methodologies. It underscores a critical shift from traditional malicious channels to leveraging trusted platforms, making detection more challenging. Organizations and individuals must prioritize robust security awareness programs, implement advanced endpoint and network protection, and maintain agile incident response capabilities. The future of cybersecurity demands a proactive stance, continuously adapting defenses to counter threats that increasingly exploit user trust in emerging technologies.





