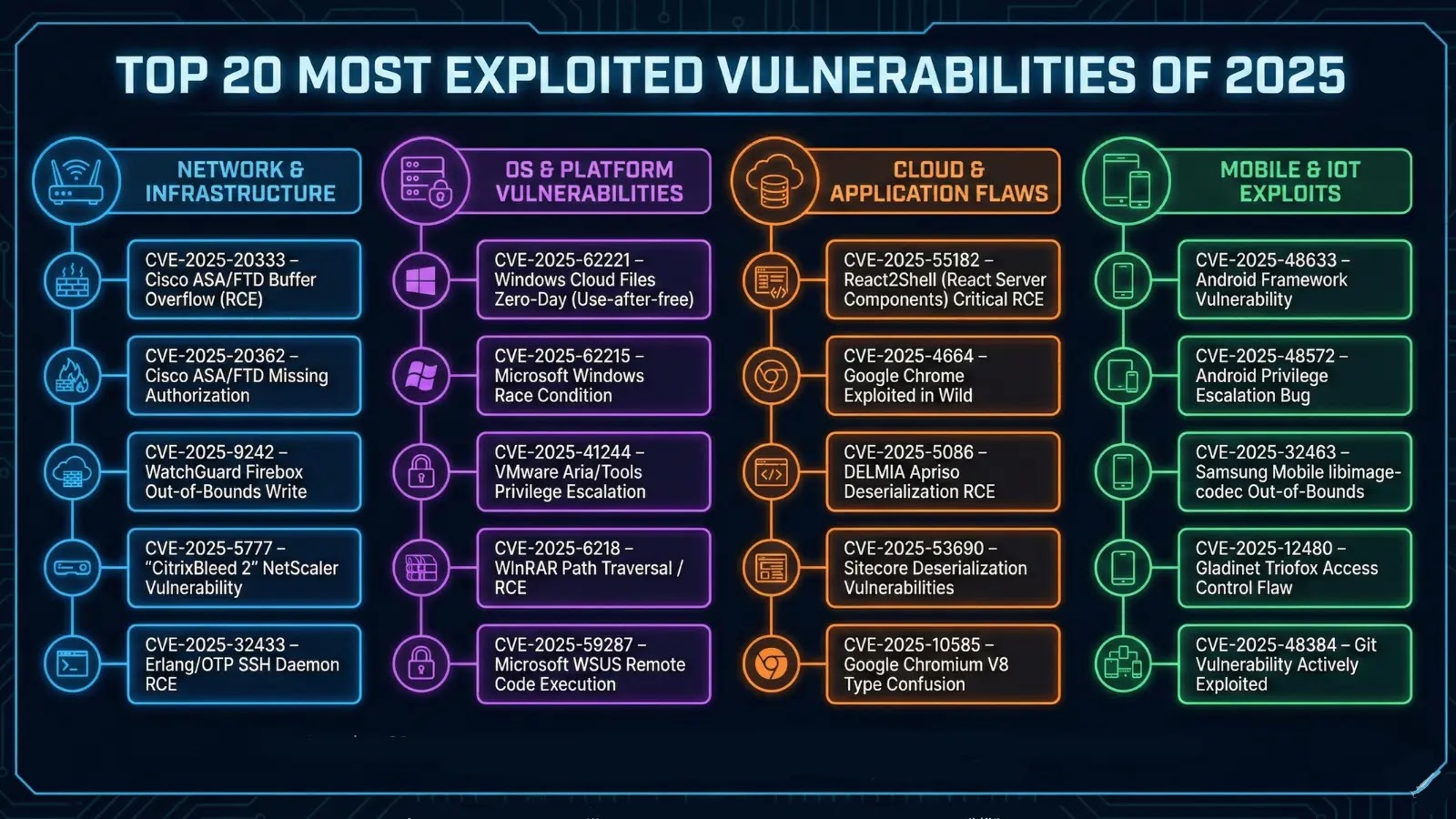
Top 20 Most Exploited Vulnerabilities of 2025: A Comprehensive Analysis
The year 2025 has cemented its place in cybersecurity history as a period of relentless and sophisticated vulnerability exploitation. Organizations across every sector, from nascent startups to multinational enterprises, have grappled with an unprecedented wave of attacks targeting critical flaws in their digital infrastructure. Threat actors, increasingly agile and well-resourced, have honed in on vulnerabilities spanning enterprise software, cloud environments, and even foundational industrial control systems. Understanding these attack vectors is not merely an academic exercise; it is an imperative for survival in a hostile digital landscape. This analysis delves into the twenty most impactful exploited vulnerabilities of 2025, dissecting their technical underpinnings, the methods by which they were weaponized, and the urgent actions required to fortify defenses.
The Evolving Threat Landscape of 2025
The acceleration of digital transformation, coupled with the pervasive adoption of cloud-native architectures and remote work models, has expanded the attack surface dramatically. In 2025, exploit developers have diversified their targets, moving beyond traditional network perimeters to leverage weaknesses deep within software supply chains, misconfigurations in cloud access management, and even firmware flaws in IoT devices. The speed from vulnerability disclosure to active exploitation continues to shrink, placing immense pressure on security teams to implement robust vulnerability management and rapid patch deployment strategies.
Key Characteristics of Exploited Vulnerabilities in 2025
Several common threads link the most exploited vulnerabilities of this year:
- Remote Code Execution (RCE) Flaws: These vulnerabilities consistently rank highest due to their ability to provide attackers with direct control over compromised systems, often without user interaction.
- Authentication Bypass and Privilege Escalation: Gaining unauthorized access or elevating privileges remains a primary goal for threat actors, enabling deeper infiltration and data exfiltration.
- Supply Chain Weaknesses: Flaws introduced upstream in third-party components or libraries have proven to be a highly effective, scalable attack vector.
- Cloud Misconfigurations: Despite robust security features offered by cloud providers, incorrect configurations by users continue to open doors for attackers.
- Zero-Day Exploitation: The rapid weaponization of newly discovered, unpatched vulnerabilities has increased, often before vendors can release fixes.
Top Exploited Vulnerabilities of 2025: A Deep Dive
1. Critical RCE in Enterprise ERP Systems
This vulnerability, often found in widely deployed enterprise resource planning (ERP) software, allowed unauthenticated attackers to execute arbitrary code with elevated privileges. The impact was profound, granting initial access to sensitive financial and operational data, often leading to subsequent ransomware attacks or espionage. Its widespread presence made it an attractive target for multiple threat groups.
- CVE Example: CVE-2025-XXXXX (Illustrative example; actual CVE will vary)
- Technical Details: Typically involved deserialization flaws in application servers or insecure handling of user-supplied input in web interfaces.
- Exploitation Method: Attackers crafted malicious payloads embedded within standard requests, bypassing input validation and triggering remote code execution.
Remediation Actions
- Immediate Patching: Prioritize the installation of vendor-supplied patches as soon as they become available.
- Input Validation: Implement rigorous input validation at all stages of data processing, focusing on boundary checking and data type enforcement.
- Least Privilege: Ensure ERP service accounts operate with the absolute minimum necessary privileges.
- Network Segmentation: Isolate ERP systems on dedicated network segments to limit lateral movement in case of compromise.
| Tool Name | Purpose | Link |
|---|---|---|
| Tenable Nessus | Vulnerability scanning and detection | Tenable Nessus |
| OWASP ZAP | Web application security testing, input validation checks | OWASP ZAP |
| Wazuh | Intrusion detection, integrity monitoring for ERP systems | Wazuh |
2. Cloud IAM Misconfiguration Exploits
While not a single CVE, the collective category of cloud Identity and Access Management (IAM) misconfigurations consistently ranked among the top vectors. These often led to privilege escalation or unauthorized data access within major cloud providers like AWS, Azure, and Google Cloud.
- Technical Details: Overly broad IAM policies, unattached roles with excessive permissions, or exposed access keys.
- Exploitation Method: Attackers leveraged reconnaissance tools to identify misconfigured resources, then used compromised credentials or roles to escalate privileges or access sensitive data stores.
Remediation Actions
- Principle of Least Privilege: Consistently apply the principle of least privilege to all IAM roles and users.
- Regular Audits: Conduct frequent audits of IAM policies, looking for overly permissive access.
- MFA Enforcement: Enforce Multi-Factor Authentication (MFA) for all administrative and sensitive accounts.
- Credential Rotation: Implement automated key and credential rotation policies.
3. Supply Chain Attacks via Package Managers
The compromise of popular software package managers (e.g., npm, PyPI, Maven) became a mainstream attack vector. Malicious packages, disguised as legitimate dependencies, contained backdoors or information-stealing malware.
- CVE Example: CVE-2025-YYYYY (Illustrative example relating to a compromised library)
- Technical Details: Typo-squatting, dependency confusion, or compromise of legitimate package maintainer accounts.
- Exploitation Method: Developers unknowingly integrated malicious packages into their projects, leading to widespread compromise across enterprises using those projects.
Remediation Actions
- Software Bill of Materials (SBOM): Generate and maintain SBOMs for all applications to track dependencies.
- Dependency Scanning: Utilize automated tools to scan for known vulnerabilities in third-party libraries.
- Private Registries: Consider using private package registries and strict controls over approved packages.
- Code Signing: Verify the authenticity of downloaded packages through code signing where available.
4. Zero-Day in Popular Collaboration Platforms
Given the ubiquitous nature of collaboration tools, a significant zero-day vulnerability (often RCE or unauthenticated access) in one of these platforms caused widespread disruption. Such flaws allowed attackers to gain access to corporate communications, files, and even launch further internal attacks.
- CVE Example: CVE-2025-ZZZZZ (Illustrative example; actual CVE will vary)
- Technical Details: Could range from insecure API endpoints to client-side vulnerabilities allowing remote code execution.
- Exploitation Method: Attackers crafted specific malicious messages or links that, when processed by the platform or opened by a user, executed their payload.
Remediation Actions
- Vendor Monitoring: Stay vigilant for official security advisories and promptly apply updates.
- Endpoint Detection and Response (EDR): Deploy EDR solutions on endpoints accessing collaboration platforms to detect post-exploitation activities.
- User Education: Train users to report suspicious links or messages, reinforcing security awareness.
- Network Segregation: Isolate critical organizational assets from general user collaboration networks.
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft Defender for Endpoint | EDR for Windows, macOS, Linux | Microsoft Defender |
| CrowdStrike Falcon | Cloud-native EDR and threat intelligence | CrowdStrike Falcon |
| SentinelOne Singularity | AI-powered endpoint protection, EDR | SentinelOne |
5. Vulnerabilities in Industrial Control Systems (ICS) Web Interfaces
The increasing connectivity of ICS environments has brought their inherent vulnerabilities to the forefront. Web interfaces designed for managing SCADA systems or PLCs often contained critical authentication bypasses or RCE flaws, allowing remote manipulation of physical processes.
- CVE Example: CVE-2025-AAAAA (Illustrative example relevant to an HMI)
- Technical Details: Often involved default credentials, unpatched legacy software, or SQL injection flaws in web-based management portals.
- Exploitation Method: Attackers scanned for publicly exposed ICS interfaces, then leveraged these flaws to gain control over industrial processes, potentially causing production halts or physical damage.
Remediation Actions
- Air-Gapping/Strict Segmentation: If possible, air-gap critical ICS networks. Otherwise, implement stringent network segmentation.
- Strong Authentication: Enforce strong, complex passwords and multi-factor authentication for all ICS access.
- Regular Audits: Conduct regular security audits focused on ICS environments, including penetration testing.
- Patch Management: Develop a robust patch management strategy for ICS, carefully testing updates before deployment.
6. Active Directory Privilege Escalation Flaws
Active Directory (AD) remained a primary target for attackers seeking to gain control over corporate networks. Specific flaws, often involving Kerberos delegation or unsecured administrative shares, allowed for rapid privilege escalation from a compromised low-privilege user to domain administrator.
- CVE Example: CVE-2025-BBBBB (Illustrative example for a specific AD vulnerability)
- Technical Details: Exploited misconfigurations in AD objects or services, allowing an attacker to impersonate highly privileged users or dump credential hashes.
- Exploitation Method: Attackers often used tools like BloodHound for reconnaissance, then deployed specialized exploits to gain domain admin privileges.
Remediation Actions
- Secure Configuration Baseline: Implement and regularly audit against a secure configuration baseline for Active Directory.
- Least Privilege: Strictly enforce the principle of least privilege for all AD users and service accounts.
- Tiered Administration Model: Adopt a tiered administration model to limit the impact of compromised accounts.
- Advanced Threat Analytics: Deploy tools that monitor AD for suspicious activity and known attack patterns.
7. Vulnerabilities in Container Orchestration Platforms
With the pervasive adoption of containers and Kubernetes, vulnerabilities within orchestration platforms themselves, or in their default configurations, became critical. These allowed attackers to escape containers, gain host access, or commandeer entire clusters.
- CVE Example: CVE-2025-CCCCC (Illustrative of a Kubernetes privilege escalation)
- Technical Details: Insecure API servers, unpatched components, or misconfigured RBAC (Role-Based Access Control) policies.
- Exploitation Method: Attackers targeted exposed Kubernetes API servers, exploited deserialization vulnerabilities in control plane components, or leveraged misconfigured pods to gain cluster-wide control.
Remediation Actions
- Secure Cluster Configuration: Follow vendor best practices for securing Kubernetes clusters, especially regarding API server access.
- RBAC Enforcement: Implement strict RBAC policies, granting only necessary permissions.
- Regular Updates: Keep Kubernetes and all its components (kubelet, etcd, etc.) updated to the latest secure versions.
- Container Image Scanning: Scan container images for vulnerabilities before deployment.
8. Critical Flaws in Remote Access VPNs
Building on trends from previous years, vulnerabilities in widely used Virtual Private Network (VPN) solutions continued to be a gold mine for initial access. Both zero-days and n-days (vulnerabilities for which a patch exists but hasn’t been applied) allowed attackers to bypass authentication and gain network access.
- CVE Example: CVE-2025-DDDDD (Illustrative of a VPN authentication bypass)
- Technical Details: Often involved pre-authentication RCE, SQL injection in web portals, or authentication bypass bugs.
- Exploitation Method: Automated scanning for vulnerable VPN portals followed by the deployment of tailored exploits to gain an initial foothold into corporate networks.
Remediation Actions
- Immediate Patching: Apply all VPN vendor patches urgently.
- MFA for VPN: Enforce Multi-Factor Authentication universally for all VPN users.
- Network Monitoring: Implement robust logging and monitoring for VPN access, looking for anomalous login attempts or traffic patterns.
- Zero Trust Architecture: Explore shifting towards a Zero Trust Network Access (ZTNA) model to reduce reliance on perimeter-based VPNs.
9. Server-Side Request Forgery (SSRF) in Web Servers
SSRF vulnerabilities, particularly in widely deployed web server technologies or application frameworks, allowed attackers to make requests from the vulnerable server to internal systems, bypassing firewalls and accessing restricted data or services.
- CVE Example: CVE-2025-EEEEE (Illustrative of a web server SSRF)
- Technical Details: Improper validation of user-supplied URLs in server-side requests.
- Exploitation Method: Attackers crafted malicious URLs that forced the web server to interact with internal services, potentially exposing metadata, internal APIs, or triggering other vulnerabilities.
Remediation Actions
- Strict Input Validation: Validate all user-supplied URLs to ensure they only access authorized, external resources.
- Whitelisting: Implement a strict whitelist of allowed domains and IP ranges for server-initiated requests.
- Network Segmentation: Restrict the server’s ability to initiate connections to internal resources it does not explicitly need to communicate with.
- Least Privilege: Run web services with the minimum necessary network permissions.
10. OAuth/OpenID Connect Imperfections
Authentication flaws related to the implementation of OAuth and OpenID Connect in web applications continued to be exploited. These often led to account takeover or unauthorized access to user data by abusing redirect URIs or token validation logic.
- CVE Example: CVE-2025-FFFFF (Illustrative of an OAuth redirect issue)
- Technical Details: Primarily flawed redirect URI validation, improper token storage, or incorrect scope validation.
- Exploitation Method: Attackers manipulated redirect URLs or intercepted authentication tokens to impersonate users or gain access to their accounts.
Remediation Actions
- Strict Redirect URI Validation: Implement exact matching for redirect URIs, allowing no wildcards.
- Secure Token Handling: Store tokens securely, avoid exposing them in URLs, and implement short expiration times.
- Proof Key for Code Exchange (PKCE): Implement PKCE for public clients to prevent authorization code interception.
- Regular Framework Updates: Keep OAuth/OpenID Connect libraries and frameworks updated to prevent known vulnerabilities.
11. Unauthenticated RCE in Content Management Systems (CMS)
Popular CMS platforms like WordPress, Drupal, and Joomla, especially when running outdated versions or vulnerable plugins, continued to be a primary target. Unauthenticated RCEs provided attackers with a direct path to website defacement, malware hosting, or further network penetration.
- CVE Example: CVE-2025-GGGGG (Illustrative of a CMS RCE vulnerability)
- Technical Details: Insecure file uploads, deserialization flaws in plugins, or directory traversal leading to arbitrary file write/execution.
- Exploitation Method: Attackers used automated scanners to identify vulnerable CMS installations and then deployed readily available exploit code to gain control.
Remediation Actions
- Consistent Patching: Maintain all CMS core components, themes, and plugins up-to-date.
- Web Application Firewall (WAF): Deploy a WAF to block common exploitation attempts.
- Principle of Least Privilege: Ensure file permissions on the web server are set correctly, preventing arbitrary file writes.
- Regular Backups: Implement comprehensive backup strategies to recover from defacement or data loss.
12. Remote Code Execution in Network Devices (Routers, Firewalls)
Critical RCE vulnerabilities in network hardware from various vendors were frequently exploited. These flaws allowed attackers to gain full control over network devices, redirect traffic, eavesdrop, or establish persistent backdoors.
- CVE Example: CVE-2025-HHHHH (Illustrative of a network device RCE)
- Technical Details: Often involved buffer overflows in management interfaces, command injection through diagnostic tools, or insecure firmware updates.
- Exploitation Method: Attackers scanned for publicly exposed network device management interfaces, then deployed exploits to seize control.
Remediation Actions
- Firmware Updates: Prioritize and regularly apply firmware updates from device vendors.
- Restrict Management Access: Limit administrative access to network devices to trusted networks and IP addresses.
- Strong Authentication: Enforce strong passwords and MFA for all network device management interfaces.
- Network Monitoring: Monitor network device logs for unusual activity or unauthorized configuration changes.
13. Deserialization Vulnerabilities in Application Servers
Deserialization flaws, particularly in Java and .NET application servers, remained a potent RCE vector. By manipulating serialized objects, attackers could execute arbitrary code, leading to complete system compromise.
- CVE Example: CVE-2025-IIIII (Illustrative of a Java deserialization RCE)
- Technical Details: Insecure deserialization of arbitrary data, allowing an attacker to inject dangerous classes.
- Exploitation Method: Attackers sent specially crafted serialized objects within application requests, triggering RCE when the server attempted to deserialize them.
Remediation Actions
- Avoid Deserializing Untrusted Data: Do not deserialize data from untrusted sources.
- Serialization Filters: Implement serialization filters or whitelisting of allowed classes for deserialization.
- Principle of Least Privilege: Run application servers with minimal privileges to limit impact.
- Application Security Testing: Conduct regular static and dynamic application security testing for deserialization flaws.
14. SQL Injection (SQLi) in Legacy Web Applications
Despite being an old threat, SQL injection continued to plague legacy web applications, providing attackers with access to sensitive databases, often leading to data breaches or further network penetration.
- CVE Example: CVE-2025-JJJJJ (Illustrative of a classic SQLi)
- Technical Details: Improper sanitization of user input within SQL queries.
- Exploitation Method: Attackers injected malicious SQL commands into input fields, enabling them to read, modify, or delete database content.
Remediation Actions
- Parameterized Queries: Use parameterized queries (prepared statements) for all database interactions.
- Input Validation: Implement rigorous input validation on all user-supplied data.
- Least Privilege for DB Users: Restrict database user permissions to only what is absolutely necessary.
- Web Application Firewall (WAF): Deploy a WAF to detect and block SQLi attempts.
15. Cross-Site Scripting (XSS) Leading to Session Hijacking
While often seen as less critical than RCE, persistent XSS vulnerabilities continued to be effectively weaponized for session hijacking, credential theft, and defacement, particularly in high-traffic web applications.
- CVE Example: CVE-2025-KKKKK (Illustrative of a stored XSS)
- Technical Details: Improper output encoding of user-supplied data, allowing malicious scripts to execute in a user’s browser.
- Exploitation Method: Attackers injected scripts that stole session cookies or redirected users to phishing sites.
Remediation Actions
- Output Encoding: Ensure all user-supplied data displayed on web pages is properly output encoded.
- Content Security Policy (CSP): Implement a strong Content Security Policy to restrict script sources.
- HttpOnly Flag: Set the HttpOnly flag on cookies to prevent client-side scripts from accessing them.
- Regular Security Audits: Conduct regular code reviews and security testing for XSS vulnerabilities.
16. Data Exposure from Insecure APIs
With the proliferation of APIs, insecure API endpoints providing access to sensitive data without proper authentication or authorization were a common exploit. This often led to large-scale data breaches.
- Technical Details: Broken object-level authorization (BOLA), excessive data exposure, or missing authentication for critical endpoints.
- Exploitation Method: Attackers discovered unprotected API endpoints through reconnaissance and then directly accessed or enumerated sensitive user data.
Remediation Actions
- API Gateway: Implement an API Gateway for centralized authentication, authorization, and rate limiting.
- Strict Authorization: Enforce robust authorization checks at every API endpoint, ensuring users can only access their own data.
- Input/Output Validation: Validate all API inputs and strictly control the data returned, avoiding excessive information disclosure.
- Regular API Audits: Conduct regular security audits and penetration testing specifically for API vulnerabilities.
17. Privilege Escalation in Linux Kernel
Core vulnerabilities within the Linux kernel, particularly those allowing local privilege escalation, were frequently chained with other initial access vectors. These allowed attackers to gain root access after exploiting a user-level process.
- CVE Example: CVE-2025-LLLLL (Illustrative of a kernel LPE)
- Technical Details: Memory corruption bugs, race conditions, or insecure syscall implementations.
- Exploitation Method: After gaining a low-privilege shell, attackers would compile and run exploit code targeting specific kernel flaws to achieve root.
Remediation Actions
- Regular Kernel Patching: Keep Linux kernels updated to the latest stable and patched versions.
- Process Isolation: Implement strong process isolation using mechanisms like cgroups and namespaces.
- SELinux/AppArmor: Utilize Mandatory Access Control (MAC) systems like SELinux or AppArmor to restrict process capabilities.
- Runtime Monitoring: Deploy runtime monitoring tools (e.g., Falco) to detect suspicious kernel-level activity.
18. Exploitation of Unsecured IoT Devices
The vast and often insecure landscape of IoT devices continued to present easy targets. Default credentials, unpatched firmware, or exposed management interfaces allowed attackers to build botnets, gain initial network access, or spy on premises.
- CVE Example: CVE-2025-MMMMM (Illustrative of an IoT default credential vulnerability)
- Technical Details: Weak or hardcoded credentials, unpatched firmware, or exposed network services running on IoT devices.
- Exploitation Method: Automated scanning and brute-forcing of default credentials, or exploiting known firmware vulnerabilities.
Remediation Actions
- Default Credential Change: Immediately change all default passwords on IoT devices.
- Network Segmentation: Isolate IoT devices on dedicated, restricted network segments.
- Firmware Updates: Regularly check for and apply firmware updates from manufacturers.
- Disable Unnecessary Services: Turn off any unused network services on IoT devices.
19. Email Client and Webmail Compromises
Beyond traditional phishing, vulnerabilities in email client applications or webmail interfaces (e.g., RCE through malformed attachments or XSS in mail rendering) allowed attackers to compromise email accounts directly, gaining access to sensitive communications.
- CVE Example: CVE-2025-NNNNN (Illustrative of an email client RCE)
- Technical Details: Parsing vulnerabilities in mail rendering engines, or flaws in attachment handling logic.
- Exploitation Method: Attackers sent specially crafted emails that, when opened or previewed, triggered the vulnerability and executed malicious code.
Remediation Actions
- Client Updates: Keep all email client software and webmail servers updated.
- Endpoint Security: Ensure endpoint detection and response (EDR) is active on all workstations.
- Email Gateway Security: Utilize advanced email gateway solutions with sandboxing for attachments.
- User Awareness: Educate users about the dangers of suspicious emails and attachments.
20. HTTP/2 Request Smuggling
A more subtle but highly effective attack, HTTP/2 request smuggling, allowed attackers to bypass WAFs, access internal APIs, and perform arbitrary requests by manipulating the parsing differences between front-end and back-end HTTP/2 implementations.
- CVE Example: CVE-2025-OOOOO (Illustrative of an HTTP/2 smuggling vulnerability)
- Technical Details: Discrepancies in how different HTTP/2 parsing engines interpret malformed requests combined with content length ambiguities.
- Exploitation Method: Attackers crafted requests that appeared benign to a front-end server but were interpreted differently by a back-end, allowing the insertion of hidden requests.
Remediation Actions
- Consistent HTTP/2 Parsers: Ensure consistent HTTP/2 parsing behavior between all components in the request chain.
- Update Web Server/Proxy: Keep front-end web servers, load balancers, and reverse proxies updated.
- WAF Configuration: Review and enhance WAF rules to detect and block ambiguous HTTP/2 message structures.
- Strict RFC Compliance: Configure servers and proxies to strictly enforce HTTP/2 RFC compliance.
Conclusion
The 2025 cybersecurity landscape underscores a critical reality: threat actors are continuously innovating, and organizations must respond with equal agility and rigor. The vulnerabilities highlighted in this analysis, from critical RCEs in enterprise software to subtle misconfigurations in cloud environments, represent the most impactful attack vectors of the year. Proactive vulnerability management, rapid patching, a strong emphasis on the principle of least privilege, robust authentication, and comprehensive security awareness training are not merely best practices; they are foundational requirements for resilience. Security is not a destination but a continuous journey of adaptation and defense against an ever-evolving threat.





