Top 3 CISO Challenges And How To Solve Them
Leading a security team when threats outpace your defensive tools is a dilemma countless Chief Information Security Officers (CISOs) confront daily. The struggle is real: constant alert fatigue, slow-moving incident response, and persistent detection gaps erode an organization’s security posture and exhaust its team. Often, the core of these problems stems from a fundamental lack of visibility into the threat landscape.
This post delves into the top three challenges CISOs face and provides actionable strategies to overcome them, ensuring your security measures are robust and your team remains effective.
Challenge 1: The Ever-Evolving Threat Landscape and Detection Gaps
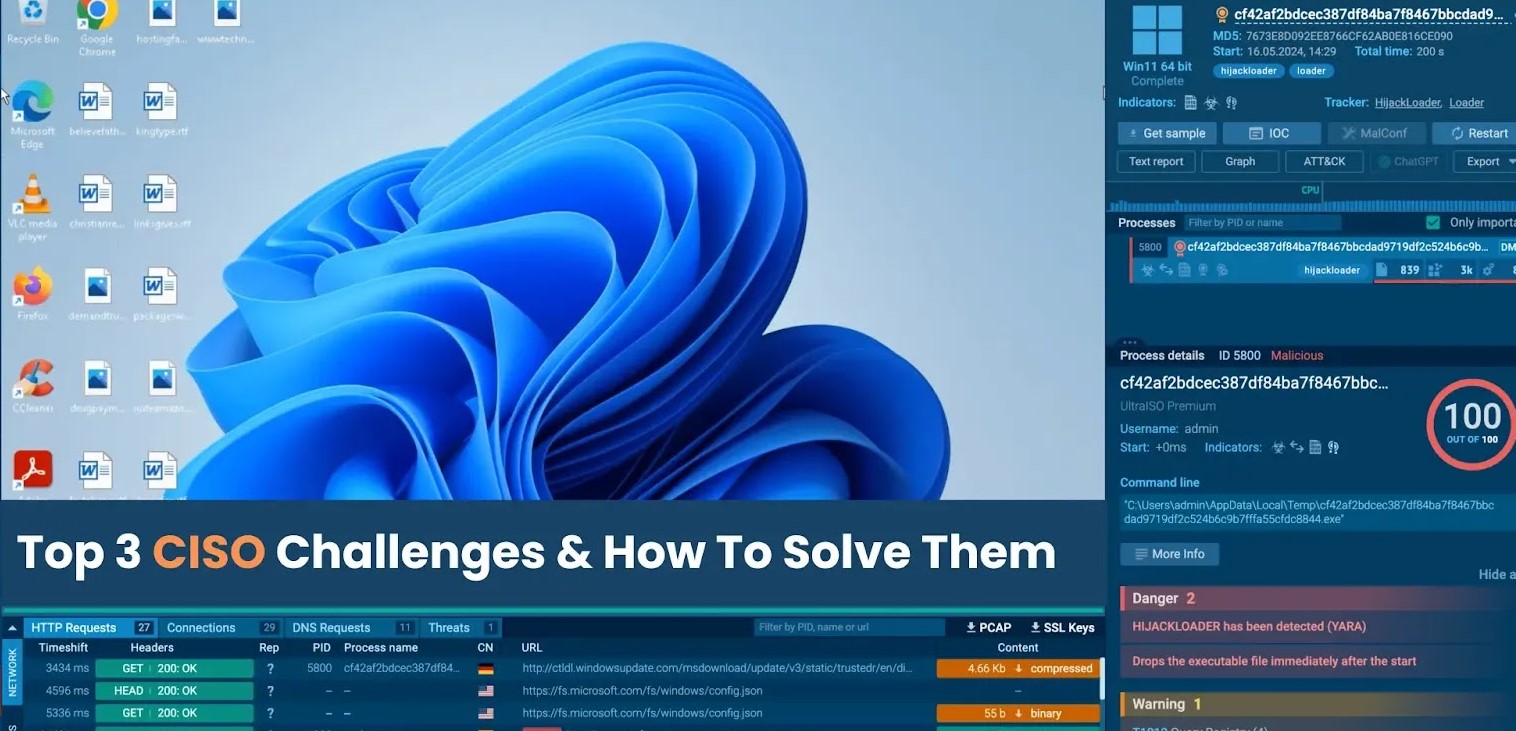
The pace at which cyber threats evolve is relentless. New attack vectors, sophisticated malware variants, and advanced persistent threats (APTs) emerge faster than many traditional security tools can adapt. This leads to critical detection gaps, leaving organizations vulnerable to zero-day exploits and novel attack methodologies. CISOs frequently find their existing security stacks are not comprehensive enough to provide the granular visibility needed to identify and neutralize these advanced threats, particularly when legacy systems are involved.
For instance, an organization might have robust perimeter defenses but lack visibility into lateral movement within its network once an initial breach occurs. This internal blindness allows attackers to establish footholds, escalate privileges, and exfiltrate data undetected for extended periods. The inability to “see how a threat actually” operates within the environment is a significant impediment to effective defense.
Remediation Actions: Enhancing Threat Visibility
- Implement Extended Detection and Response (XDR): Move beyond isolated security tools. XDR unifies and correlates data from endpoints, networks, cloud environments, and applications, providing a holistic view of potential threats. This integrated approach significantly improves detection capabilities by identifying patterns and anomalies that individual tools might miss.
- Leverage Threat Intelligence Platforms (TIPs): Integrate real-time threat intelligence feeds into your security operations. TIPs provide insights into emerging threats, attacker tactics, techniques, and procedures (TTPs), and indicators of compromise (IoCs). This proactive knowledge allows security teams to anticipate and defend against new threats before they become widespread.
- Adopt Deception Technologies: Deploy honeypots and other deception tools within your network to bait attackers. These tools provide early warnings of malicious activity and offer valuable intelligence on attacker methodologies, helping to close detection gaps by luring and observing adversaries in a controlled environment.
- Regularly Assess and Update Security Controls: Conduct frequent vulnerability assessments and penetration tests to identify weaknesses in your current security infrastructure. Ensure your security tools are regularly updated and configured to detect the latest threats. For example, staying current on vulnerability patches for common enterprise software, such as those addressed by CVE-2023-38831 (related to WinRAR vulnerability), is crucial for preventing exploitation.
Challenge 2: Overwhelming Alert Noise and Analyst Burnout
Modern security operations centers (SOCs) are often swamped with an incessant deluge of alerts. This “alert noise” is a significant CISO challenge, leading to analyst fatigue, missed critical incidents, and inefficient resource allocation. The sheer volume of low-fidelity alerts makes it difficult for security teams to distinguish genuine threats from false positives, diluting their effectiveness and risking burnout.
Every security tool generates its own set of alerts, and without proper aggregation, correlation, and context, analysts spend an inordinate amount of time chasing phantom threats. This not only wastes valuable time but also delays response to legitimate incidents, exacerbating the impact of a breach.
Remediation Actions: Streamlining Alert Management
- Implement Security Orchestration, Automation, and Response (SOAR): SOAR platforms automate repetitive tasks, orchestrate workflows, and standardize incident response processes. This significantly reduces manual effort, filters out low-priority alerts, and allows analysts to focus on complex investigations. SOAR can automatically enrich alerts with context, facilitating faster triage and decision-making.
- Refine SIEM Rules and Tuning: Regularly review and tune your Security Information and Event Management (SIEM) rules to reduce false positives and enhance the fidelity of alerts. Collaboration between security analysts and engineers is vital to optimize these rules based on observed threat patterns and organizational risk profiles.
- Prioritize Risk-Based Alerting: Implement a risk-based approach to alerting, prioritizing incidents based on asset criticality, potential impact, and threat severity. This ensures that the most dangerous threats receive immediate attention, while less critical alerts can be handled systematically.
- Develop Clear Standard Operating Procedures (SOPs): Establish well-defined SOPs for alert triage, investigation, and response. Consistent processes help minimize confusion, reduce errors, and accelerate incident resolution.
Challenge 3: Slow Incident Response and Remediation
Even with robust detection capabilities, a slow incident response can negate many security investments. Protracted investigation times, manual remediation processes, and a lack of coordinated action during a breach can significantly increase the financial and reputational damage to an organization. When an incident occurs, the clock is ticking, and every minute of delay contributes to potential data loss, operational disruption, and compliance penalties.
The absence of clear playbooks, insufficient cross-departmental communication, and a lack of automation in the response phase are common culprits behind sluggish incident remediation. The “dwell time” – the period an attacker remains undetected within a network – dramatically increases the potential impact of a breach.
Remediation Actions: Accelerating Response Times
- Develop and Practice Incident Response Playbooks: Create detailed, actionable playbooks for various types of security incidents (e.g., malware infection, data exfiltration, insider threat). Regularly conduct tabletop exercises and simulated breach drills to test these playbooks and identify areas for improvement.
- Automate Response Actions: Leverage automation for common response actions, such as isolating infected endpoints, blocking malicious IPs, or automatically initiating forensic data collection. This can drastically reduce response times and minimize the damage during an active attack.
- Establish Cross-Functional Communication Channels: Foster strong communication and collaboration between security, IT operations, legal, and public relations teams. A unified command structure during an incident ensures that all stakeholders are informed and coordinated.
- Utilize Security Analytics and Context: Implement tools that provide deep contextual information during investigations, such as user behavior analytics (UBA) or network traffic analysis (NTA). Understanding the full scope of an attack, including its origins and lateral movement, is crucial for effective containment and eradication. For instance, understanding the broader context of a vulnerability like CVE-2023-38646 (related to GitLab) would involve not just patching but also assessing its potential impact on user accounts and data within the organization’s specific environment.
The challenges facing CISOs are formidable, but not insurmountable. By strategically investing in better visibility, streamlining alert management, and automating incident response, organizations can significantly enhance their security posture. The key lies in creating an agile, proactive, and resilient security operation that can adapt to the ever-changing threat landscape and keep valuable assets protected.





