UNC3944 Attacking VMware vSphere and Enabling SSH on ESXi Hosts to Reset ‘root’ Passwords
A disturbing new campaign has emerged, highlighting the increasing sophistication of financially motivated threat actors. UNC3944, a group with known ties to “0ktapus,” “Octo Tempest,” and “Scattered Spider,” has launched targeted attacks against VMware vSphere environments, leveraging social engineering and hypervisor-level incursions to compromise critical infrastructure. This campaign, impacting sectors such as retail, airline, and insurance, serves as a stark reminder of the persistent and evolving threats to core IT systems. Google Threat Intelligence Group (GITG) identified this campaign in mid-2023, following initial FBI alerts, underscoring the urgency for organizations to understand and mitigate these threats.
Understanding UNC3944’s Modus Operandi
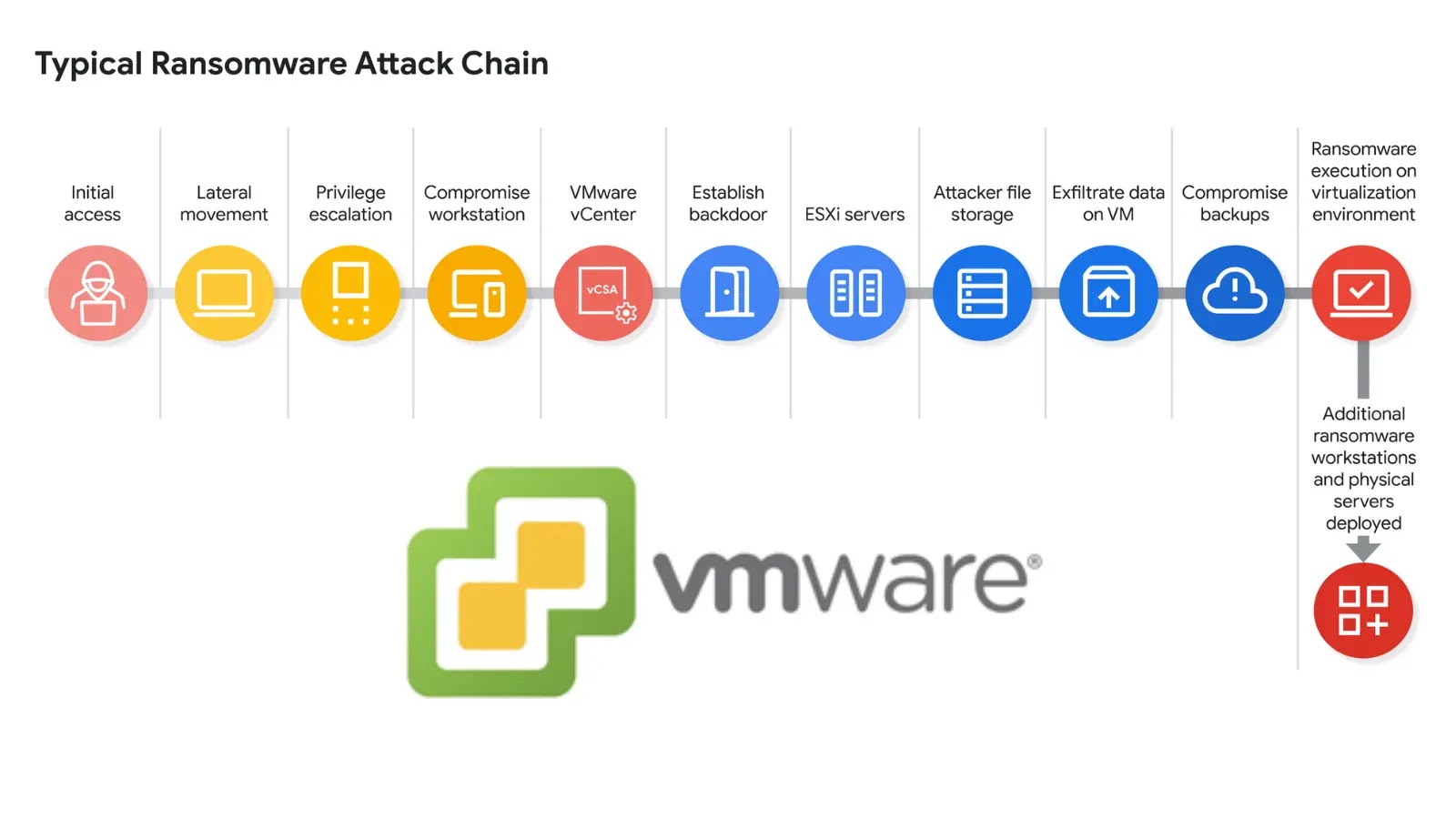
UNC3944, a financially driven threat organization, distinguishes itself through a multi-faceted attack approach. Their recent campaign against VMware vSphere environments is particularly concerning due to its focus on critical virtualization infrastructure. This group utilizes highly effective social engineering tactics to gain initial access, often targeting credentials that can then be used to pivot into more sensitive systems. Once initial access is achieved, their objective appears to be disruption and extortion, aiming to impact business continuity for financial gain.
The VMware vSphere Attack Vector Explained
The core of UNC3944’s attack against VMware vSphere involves gaining privileged access to ESXi hosts. VMware ESXi is a bare-metal hypervisor, meaning it runs directly on server hardware, acting as the foundation for virtual machines. Compromising an ESXi host grants an attacker control over all virtual machines running on it, potentially leading to data exfiltration, system destruction, or deployment of ransomware.
A key technique observed in this campaign is the enabling of SSH on ESXi hosts. SSH (Secure Shell) is a cryptographic network protocol that allows secure remote access to a computer. While SSH is a legitimate and often necessary tool for system administration, its unauthorized activation, especially on critical infrastructure like ESXi, creates a significant backdoor. Once SSH is enabled, UNC3944 can then attempt to reset the ‘root’ password for the ESXi host. The ‘root’ user has ultimate administrative privileges, essentially giving the attacker full control over the hypervisor and all guest VMs.
Impact on Targeted Industries
The selection of retail, airline, and insurance industries by UNC3944 is strategic. These sectors rely heavily on continuous operation and data integrity. Disruption of their VMware vSphere environments can have catastrophic consequences:
- Retail: Supply chain disruption, point-of-sale system failures, and customer data breaches.
- Airline: Flight cancellations, operational paralysis, and compromise of sensitive passenger information.
- Insurance: Inability to process claims, access customer policies, and manage critical financial data.
Such disruptions can lead to massive financial losses, reputational damage, and potential regulatory penalties.
Remediation Actions: Protecting Your VMware vSphere Environment
Defending against advanced persistent threats like UNC3944 requires a multi-layered security strategy. For organizations utilizing VMware vSphere, immediate action is paramount:
- Strict Access Control and Least Privilege: Implement robust identity and access management (IAM) policies. Ensure administrators have only the necessary permissions to perform their duties. Avoid using the ‘root’ account for daily operations.
- Multi-Factor Authentication (MFA) Everywhere: Enforce MFA for all administrative interfaces, especially for vCenter Server and ESXi hosts. This significantly reduces the risk of successful social engineering or credential stuffing attacks.
- Regular Patching and Updates: Keep all VMware vSphere components (ESXi, vCenter Server, NSX, etc.) up-to-date with the latest security patches. VMware regularly releases advisories for vulnerabilities, even if specific CVEs related to UNC3944’s observed tactics aren’t publicly disclosed yet, proactive patching mitigates known weaknesses.
- Disable Unnecessary Services: Periodically review and disable any services on ESXi hosts, such as SSH, that are not strictly necessary for operation. If SSH is required, enable it only for short, controlled periods, and ensure access is restricted to specific IP addresses.
- Network Segmentation: Isolate management networks that host vCenter Server and ESXi hosts from general user networks. Implement strict firewall rules to control traffic flow to and from these critical assets.
- Monitor for Anomalous Activity: Deploy robust logging and security information and event management (SIEM) solutions to monitor ESXi and vCenter logs for unusual activity, such as SSH enablement, unauthorized ‘root’ password changes, or abnormal login attempts.
- Regular Backups: Implement a comprehensive backup strategy for all virtual machines and vSphere configuration data. Test these backups regularly to ensure they are recoverable.
- Employee Security Awareness Training: Educate employees, particularly those with administrative privileges, on social engineering tactics like phishing, pretexting, and baiting. Emphasize the importance of verifying unexpected requests for credentials or system changes.
- Incident Response Plan: Develop and regularly exercise an incident response plan specifically for hypervisor-level compromises. This plan should detail steps for detection, containment, eradication, recovery, and post-incident analysis.
Essential Tools for VMware Security and Monitoring
To aid in the detection, monitoring, and mitigation of threats targeting VMware vSphere, several tools can be highly effective:
| Tool Name | Purpose | Link |
|---|---|---|
| VMware vRealize Log Insight / Aria Operations for Logs | Centralized log management and analysis for vSphere environments. Essential for detecting anomalous activity. | VMware Aria Operations for Logs |
| VMware Carbon Black Cloud Workload | Endpoint detection and response (EDR) for virtual machines and deep visibility into ESXi. | VMware Carbon Black Cloud Workload |
| Nessus / Qualys VM | Vulnerability scanning for ESXi hosts and guest VMs to identify misconfigurations and missing patches. | Nessus Professional / Qualys Vulnerability Management |
| Security Information and Event Management (SIEM) solutions (e.g., Splunk, Microsoft Sentinel) | Aggregates security logs from vSphere and other systems for correlated threat detection and alerting. | Splunk / Microsoft Sentinel |
| VMware vSphere Hardening Guide | Official security configuration best practices from VMware. | VMware Security Hardening Guides |
Conclusion
The UNC3944 campaign against VMware vSphere environments is a significant development in the threat landscape. It underscores the critical need for organizations to secure their virtualization infrastructure with the same rigor applied to other core assets. By combining robust technical controls, continuous monitoring, and comprehensive employee training, organizations can significantly bolster their defenses against financially motivated and highly sophisticated threat actors like UNC3944. Staying informed of emerging threats and pro-actively hardening systems are no longer options, but necessities in today’s interconnected world where your hypervisor is a prime target.





