Understanding Cybersecurity Compliance Standards.
Understanding Cybersecurity Compliance Standards: A Framework Overview
In today’s digital landscape, cybersecurity compliance is not merely an option but a necessity. Organizations must navigate a complex web of cybersecurity regulations and industry standards to protect sensitive data, maintain customer trust, and avoid hefty fines. This article provides a comprehensive overview of cybersecurity compliance, exploring its importance, key standards, and how organizations can establish a robust compliance framework.
Understanding Cybersecurity Compliance
What is Cybersecurity Compliance?
Cybersecurity compliance refers to the adherence to cybersecurity laws, regulatory requirements, and industry standards related to cybersecurity and information security. It involves implementing security measures and security controls to protect sensitive data from cyber threats and ensuring that an organization’s overall security posture meets the established compliance requirements. The goal is to achieve compliance with relevant cybersecurity standards and maintain compliance through ongoing monitoring and improvement of security practices.
Importance of Cybersecurity Compliance
Cybersecurity compliance is critical for protecting an organization’s assets, reputation, and financial stability. Failure to comply with cybersecurity regulations can result in significant financial penalties, legal repercussions, and damage to an organization’s brand. Moreover, compliance with cybersecurity frameworks and regulations demonstrates a commitment to security and builds trust with customers, partners, and stakeholders. By prioritizing security and compliance, organizations can mitigate security risks and enhance their competitive advantage.
Key Cybersecurity Compliance Standards
Numerous cybersecurity standards and cybersecurity frameworks exist to help organizations establish and maintain a strong security posture. Several prominent examples guide organizations in this area, including:
- The NIST Cybersecurity Framework, which provides a comprehensive guide to cybersecurity compliance.
- The Payment Card Industry Data Security Standard (card industry data security standard), which focuses on protecting payment card data.
Organizations may also need to comply with regulations such as HIPAA, GDPR, and others, depending on their industry and location. Understanding and implementing these standards is essential for achieving cybersecurity compliance.
Frameworks for Achieving Cybersecurity Compliance
Overview of Compliance Frameworks
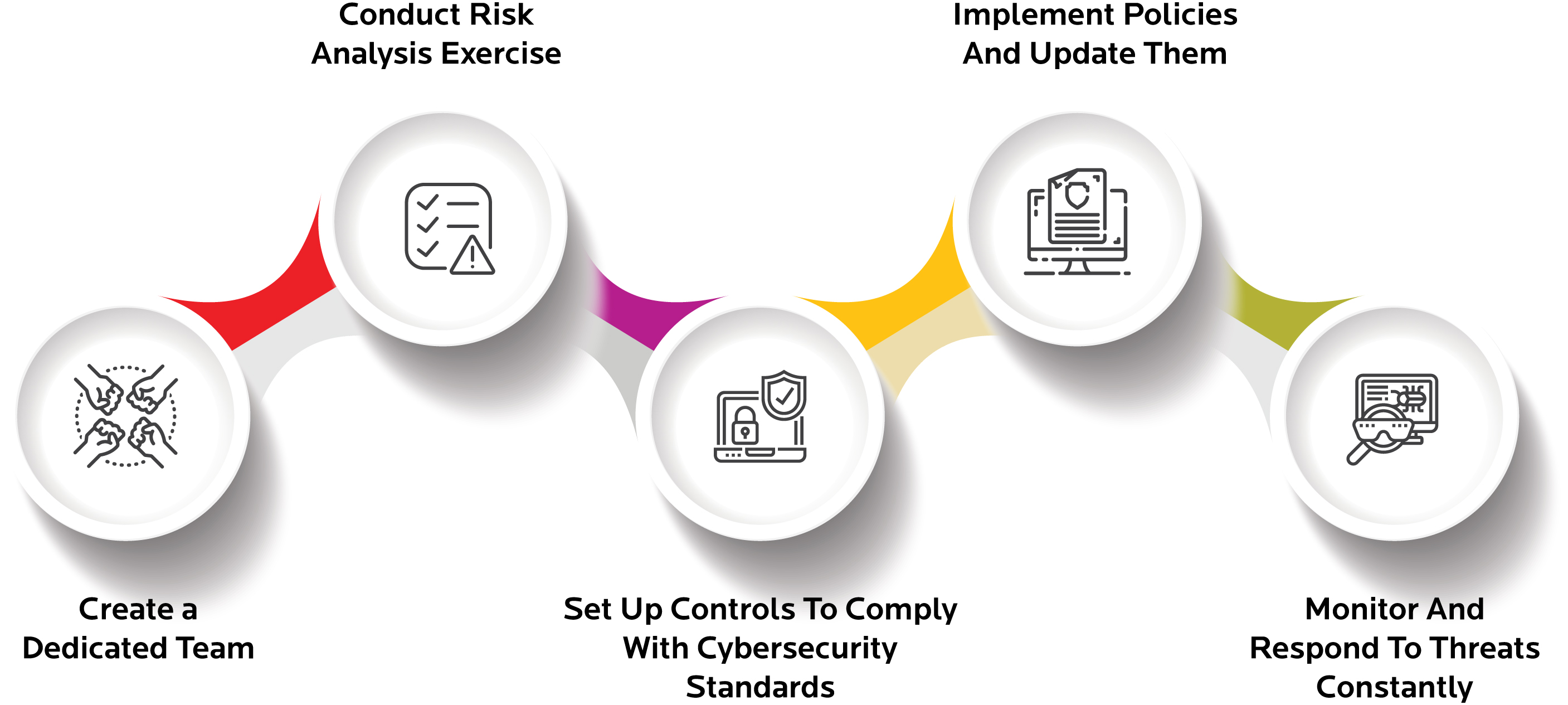
A cybersecurity compliance framework serves as a structured approach for organizations to achieve cybersecurity compliance and manage cyber risks effectively. These frameworks typically outline security controls, policies, and procedures necessary to meet regulatory requirements and industry standards. A compliance program based on a well-defined framework helps organizations establish a baseline for their security posture, identify gaps in their security measures, and prioritize efforts to improve their overall security. By adopting a suitable framework, organizations can streamline their compliance efforts and demonstrate a commitment to information security.
Popular Cybersecurity Compliance Frameworks
Several popular cybersecurity frameworks offer guidance and best practices for achieving cybersecurity compliance. When choosing a framework, organizations might consider options such as:
- The NIST Cybersecurity Framework, developed by the National Institute of Standards and Technology, which provides a comprehensive guide to cybersecurity compliance.
- The Payment Card Industry Data Security Standard (card industry data security standard), focusing on protecting payment card data.
Organizations may also consider frameworks like ISO 27001, an international standard for information security management systems. Understanding the strengths and weaknesses of each framework is crucial for selecting the one that best aligns with an organization’s needs and compliance requirements.
Choosing the Right Compliance Framework
Selecting the appropriate compliance framework is a critical decision that should align with an organization’s specific needs, industry regulations and standards, and risk profile. Organizations should assess their current security posture and compliance requirements before evaluating different frameworks. Factors to consider include the framework’s scope, applicability, cost, and the level of effort required for implementation and maintaining compliance. A well-chosen framework provides a roadmap for achieving cybersecurity compliance, reducing security risks, and demonstrating ongoing compliance to stakeholders. Prioritizing security and compliance is essential for protecting an organization’s assets and reputation in today’s threat landscape, as compliance is crucial for mitigating risks.
Compliance Regulations and Requirements
Overview of Compliance Regulations
Organizations must navigate a complex landscape of cybersecurity regulations to maintain compliance and protect sensitive data. An overview of these regulations is crucial for understanding the legal and regulatory environment in which businesses operate. These regulations often mandate specific security controls and security measures, requiring organizations to implement robust security practices. A deep understanding of these laws and regulatory requirements forms the foundation of a strong security and compliance program, enabling businesses to proactively address cyber threats and security risks while maintaining compliance standards.
Essential Compliance Requirements for Organizations
Essential compliance requirements vary based on industry, location, and the type of data handled, but some fundamental principles apply broadly. Organizations must implement comprehensive security policies, conduct regular security risk assessments, and provide employee training on cybersecurity awareness. Data protection measures, incident response planning, and security incident management are critical components of meeting compliance requirements. Adhering to these requirements ensures that organizations implement effective security measures to protect data, minimize security risks, and achieve cybersecurity compliance.
Cybersecurity Regulations Impacting Compliance
Here’s how several cybersecurity regulations impact compliance. Key examples include:
- GDPR, which mandates strict data protection requirements for organizations processing personal data of EU citizens.
- HIPAA, setting standards for protecting sensitive patient health information.
- PCI DSS, focusing on protecting payment card data to prevent fraud and data breaches, is a key component of cybersecurity compliance requirements.
These regulations and standards necessitate that organizations implement robust security controls, maintain compliance, and demonstrate ongoing compliance through regular audits and assessments, ensuring overall security.
Benefits of Cybersecurity Compliance
Enhancing Security Posture
Enhancing security posture is a primary benefit of cybersecurity compliance. By adhering to industry standards and cybersecurity frameworks, organizations can implement robust security controls that significantly reduce security risks. The NIST cybersecurity framework and other cybersecurity compliance standards offer a structured approach to identifying vulnerabilities and strengthening overall security. A strong security posture, achieved through security compliance, not only protects against cyber threats but also enhances an organization’s resilience in the face of evolving security challenges, ensuring cybersecurity compliance.
Building Trust with Stakeholders
Building trust with stakeholders is another crucial benefit of cybersecurity compliance. When organizations demonstrate adherence to cybersecurity regulations and standards, they signal a commitment to information security. This commitment fosters confidence among customers, partners, and investors. By meeting compliance requirements, organizations prove they take cybersecurity seriously, safeguarding sensitive data and maintaining compliance standards. This, in turn, enhances reputation, strengthens relationships, and contributes to long-term sustainability and success, knowing they maintain compliance, following the regulations and standards.
Reducing Cyber Risk
Reducing cyber risk is a fundamental benefit of achieving cybersecurity compliance. By implementing security measures and security controls required by frameworks and cybersecurity compliance standards, organizations can mitigate potential threats and vulnerabilities. Frameworks like the Payment Card Industry Data Security Standard (card industry data security standard) provide specific guidance for protecting sensitive data, reducing the likelihood of data breaches and cyber attacks. The compliance program helps organizations identify and address security risks proactively, minimizing the potential impact of security incidents, ensuring overall security.
Maintaining Cybersecurity Compliance
Establishing a Compliance Program
Establishing a compliance program is a vital step in maintaining cybersecurity compliance. This involves developing a comprehensive framework that aligns with relevant regulations and industry standards. The compliance program should include policies, procedures, and security controls designed to protect sensitive data and mitigate cyber threats. Regular security risk assessments, employee training, and incident response planning are essential components of a robust compliance program. By implementing a well-defined framework, organizations can streamline their compliance efforts and achieve compliance effectively.
Regular Audits and Assessments
Regular audits and assessments are crucial for maintaining cybersecurity compliance. These activities help organizations evaluate the effectiveness of their security controls and identify any gaps or vulnerabilities. Internal audits and external assessments ensure that the organization continues to meet compliance requirements and adheres to relevant standards. The NIST cybersecurity framework and other frameworks often include specific guidance on conducting regular audits and assessments. By proactively identifying and addressing security weaknesses, organizations can maintain compliance and reduce security risks.
Continuous Improvement in Compliance Practices
Continuous improvement in compliance practices is essential for maintaining cybersecurity compliance in the face of evolving cyber threats. Organizations should regularly review and update their security measures and security controls to address emerging vulnerabilities and changes in regulations. A commitment to ongoing training, monitoring, and incident response ensures that the organization remains resilient and adaptive. By fostering a culture of continuous improvement, organizations can maintain compliance standards, enhance their overall security posture, and protect against increasingly sophisticated cyber attacks, knowing they maintain compliance.
5 Surprising Facts About Understanding Cybersecurity Compliance Standards
- Compliance does not equal security. Meeting a standard (e.g., PCI DSS, HIPAA, NIST) proves a baseline of controls but does not guarantee that systems are actually secure from targeted or novel attacks.
- Different standards can conflict. Organizations that operate across regions or industries often must reconcile overlapping or contradictory requirements, forcing trade-offs between technical controls, data residency, and operational practices.
- Documentation often matters more than technical perfection when it comes to meeting cybersecurity compliance requirements. Auditors frequently flag gaps because policies, procedures, and evidence are missing—even when the technical controls exist and function correctly.
- Small changes can break compliance, emphasizing that cybersecurity compliance is crucial for maintaining security integrity. Minor configuration tweaks, software updates, or cloud service changes can inadvertently invalidate evidence or controls, creating compliance drift without obvious system failures.
- Compliance frameworks evolve faster than many expect. New threats, regulations, and technologies (cloud, AI, IoT) drive rapid updates to standards, so continuous monitoring and governance are essential to stay compliant.
What is security compliance and why is cybersecurity compliance essential?
Security compliance refers to meeting a set of cybersecurity compliance requirements, regulatory standards, and security requirements established by laws, industry bodies, and internal policies. Cybersecurity compliance is essential because it ensures compliance with PCI DSS, HIPAA (Insurance Portability and Accountability Act), CMMC and other rules designed to protect data, privacy and critical infrastructure. Compliance ensures organizations implement cybersecurity measures that reduce exposure to cybersecurity incidents and strengthen overall cybersecurity posture.
How do regulations and standards like HIPAA and PCI DSS shape a security program?
Regulations and standards impose specific security requirements and controls that a security program must adopt. For example, HIPAA focuses on privacy and security of health data while PCI DSS mandates cardholder data protections. Integrating these standards into a risk management framework and security framework allows a security team to design a set of security controls, document compliance processes and demonstrate compliance with regulatory compliance audits.
How can organizations achieve compliance through a security framework?
Achieve compliance by adopting a security framework such as NIST, ISO 27001 or the CIS Controls to create repeatable compliance strategies. A framework helps map regulatory standards to technical and administrative controls, defines compliance management workflows and supports the compliance process from gap assessment to remediation and continuous monitoring to improve cybersecurity maturity.
What are common compliance strategies to maintain compliance over time?
Common compliance strategies include performing regular risk assessments, implementing a compliance management system, continuous monitoring, staff training and incident response planning. Compliance efforts should tie into change management and configuration management so cybersecurity measures remain effective; this approach helps with compliance posture, demonstrates managing cybersecurity risks, and prepares the organization to respond to cybersecurity incidents.
How does a compliance process address cybersecurity incidents and risk management?
The compliance process should include detection, reporting and remediation procedures for cybersecurity incidents, aligned with a risk management framework that prioritizes remediation based on impact and likelihood. Incident handling procedures and logging support regulatory reporting requirements and insurance claims, while root cause analysis and corrective actions improve the security program and reduce future cybersecurity risk.
What role does a security team play in compliance management and cybersecurity maturity?
A security team leads implementation of compliance measures, operates the security framework, manages compliance management tools and coordinates audits. They drive cybersecurity maturity by establishing policies, conducting assessments, training staff, and demonstrating compliance. A mature security team integrates compliance into daily operations and improves the organization’s compliance posture and cybersecurity maturity model certification readiness.
How do standards designed to protect data influence compliance in cyber security?
Standards designed to protect data—such as ISO 27001, NIST SP 800-53, PCI DSS, and HIPAA—define security controls and best practices that compliance involves organizations to implement. These standards and regulations create a set of security standards for encryption, access control, monitoring and incident response, all intended to protect sensitive data and ensure compliance in cyber security across industries.
What practical steps can organizations take to comply with cybersecurity laws and improve compliance efforts?
Practical steps include conducting gap analyses against applicable regulatory compliance and standards, implementing a tailored security framework, documenting policies and procedures, training employees on cybersecurity practices, performing continuous risk assessments and engaging external auditors when needed. Compliance requires coordinated efforts between IT, security, legal and business units to embed compliance into operations and maintain robust cybersecurity and regulatory alignment.