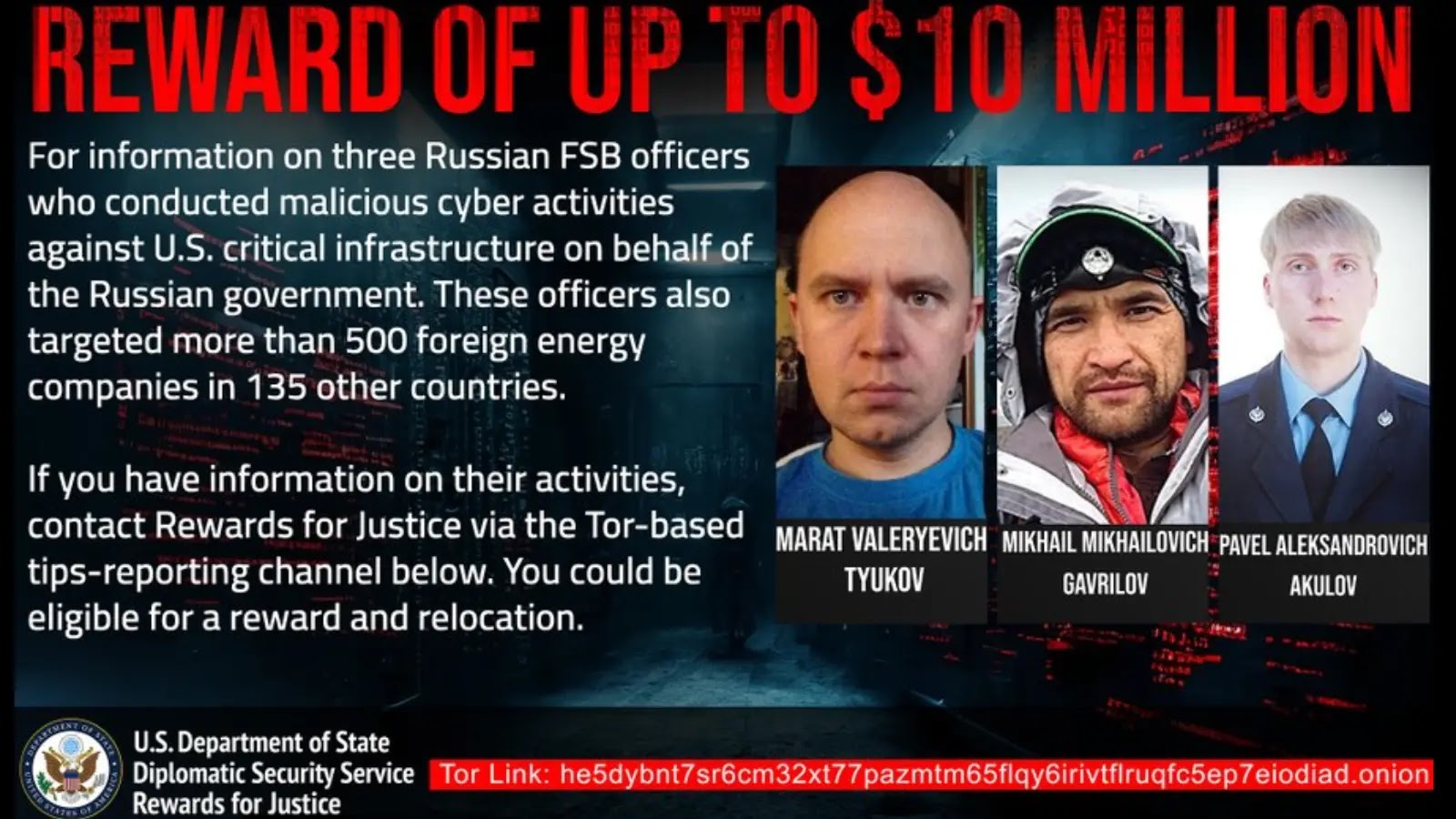
US Offers $10M Bounty For FSB Hackers Who Exploited Cisco Vulnerability To Attack Critical Infrastructure
The global cybersecurity landscape is a constant battlefield, where nation-state actors frequently engage in covert operations impacting critical infrastructure and national security. A significant development has emerged with the United States government’s announcement of a substantial bounty, up to $10 million, for information leading to the identification or location of three specific Russian intelligence officers. These individuals, affiliated with the Russian Federal Security Service (FSB), are accused of orchestrating widespread malicious cyber campaigns, notably exploiting a critical Cisco vulnerability to compromise vital networks. This unprecedented reward underscores the U.S. commitment to deterring and dismantling state-sponsored cyber threats.
The $10 Million Bounty: A Clear Message
Offered through the Department of State’s Rewards for Justice program, this bounty targets specific members of the FSB. This is not merely a financial incentive; it represents a strategic escalation in the U.S. response to persistent and damaging cyber aggressions. By naming and targeting individuals, the U.S. aims to move beyond generic condemnations, signaling a direct intent to hold specific actors accountable for their cyber crimes. The implications for international cybersecurity norms and nation-state conduct are profound, establishing a precedent for financially incentivized intelligence gathering against cyber adversaries.
FSB’s Modus Operandi and Targeted Campaigns
The accused FSB officers are linked to pervasive cyber campaigns that have targeted a wide array of critical sectors. Their operations extend beyond data theft, aiming to disrupt, degrade, and potentially control vital infrastructure. These campaigns demonstrate a sophisticated understanding of network architecture and a willingness to exploit zero-day vulnerabilities or unpatched systems to achieve strategic objectives. The focus on critical infrastructure highlights a shift from espionage to capabilities that could cripple essential services, posing a direct threat to public safety and economic stability.
Exploiting the Cisco Smart Install Vulnerability (CVE-2018-0171)
A central component of the FSB’s alleged cyber campaigns involved the exploitation of CVE-2018-0171, a critical vulnerability in Cisco Smart Install Client. This flaw, discovered in 2018, allowed unauthenticated remote attackers to execute arbitrary code or reload a device. Its severity stemmed from the widespread deployment of Cisco devices in critical networks globally, making it a lucrative target for state-sponsored actors.
- CVE-2018-0171: A remote code execution vulnerability in Cisco Smart Install Client. Attackers could send specially crafted messages to a vulnerable device, leading to arbitrary code execution or a denial of service. For more details, refer to CVE-2018-0171.
- The vulnerability resided in the Smart Install protocol, which is typically used for zero-touch deployment of network devices. Misconfigurations often left this port (TCP 4786) exposed to the internet.
- Exploitation of this vulnerability allowed attackers to gain unauthorized access, modify device configurations, exfiltrate data, or even install persistent backdoors, effectively compromising the entire network managed by the vulnerable device.
Impact on Critical Infrastructure
The targeting of critical infrastructure through vulnerabilities like CVE-2018-0171 has severe ramifications. Critical infrastructure encompasses sectors such as energy, water, transportation, healthcare, and financial services. A successful cyberattack on these systems can lead to:
- Widespread Service Disruptions: Power outages, compromised water supply, or paralyzed transportation networks.
- Economic Damage: Significant financial losses due to system downtime, recovery efforts, and loss of business productivity.
- Public Safety Risks: Impaired emergency services, compromised healthcare systems, or hazardous material incidents.
- Erosion of Trust: Damage to public confidence in institutions and essential services.
Remediation Actions and Best Practices for Cisco Smart Install Vulnerability (CVE-2018-0171)
Even years after its disclosure, vulnerabilities like CVE-2018-0171 can still pose a risk if not properly addressed. Organizations must assume that state-sponsored actors will continue to leverage known, unpatched flaws. Immediate and ongoing remediation is paramount.
Immediate Steps:
- Patching: Apply the latest security patches and software updates from Cisco. This is the primary defense against known vulnerabilities.
- Disable Smart Install: If not actively used, disable the Cisco Smart Install feature. Run
no smart installor similar commands on your Cisco devices. - Firewall Rules: Block traffic to TCP port 4786 (Smart Install) at your network perimeter, especially if exposed to the internet or untrusted networks. Implement strict ingress and egress filtering.
- Network Segmentation: Isolate critical network segments. This limits the lateral movement of an attacker even if one device is compromised.
- Vulnerability Scanning: Regularly scan your network for devices vulnerable to CVE-2018-0171 and other known vulnerabilities.
- Auditing Configurations: Periodically review configurations of network devices to ensure unnecessary services are disabled and security best practices are followed.
Long-Term Security Posture Improvements:
- Principle of Least Privilege: Configure devices with the minimum necessary privileges.
- Strong Authentication: Implement multi-factor authentication (MFA) for administrative access to network devices.
- Intrusion Detection/Prevention Systems (IDS/IPS): Deploy and configure IDS/IPS to detect and block suspicious network traffic patterns indicative of exploitation attempts.
- Security Information and Event Management (SIEM): Centralize and analyze logs from network devices for anomalies and indicators of compromise.
- Regular Security Audits: Conduct independent security audits and penetration tests to identify weaknesses.
- Employee Training: Educate IT staff and employees about social engineering tactics and phishing attempts.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan to minimize the impact of a successful breach.
Relevant Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Nmap | Network scanning; can identify open ports like TCP 4786. | https://nmap.org/ |
| Nessus | Vulnerability scanner; identifies CVE-2018-0171 and other known vulnerabilities. | https://www.tenable.com/products/nessus |
| OpenVAS | Open-source vulnerability scanner; a robust alternative to commercial tools. | https://www.greenbone.net/en/community-edition/ |
| Cisco Vulnerability Tools | Official Cisco security advisories and patching tools. | https://tools.cisco.com/security/center/vulnerability-assessment/index.html |
The Broader Implications of State-Sponsored Cyber Warfare
The U.S. bounty on FSB hackers highlights the growing challenges posed by state-sponsored cyber warfare. Such actions erode trust in the digital ecosystem, threaten critical national infrastructure, and can lead to significant economic and social disruption. Organizations and governments must prioritize robust cybersecurity measures, intelligence sharing, and international cooperation to defend against these persistent and evolving threats.
The pursuit of these individuals, backed by a substantial reward, sends an unambiguous message: cyber operations against critical infrastructure will not go unpunished. For cybersecurity professionals, this reinforces the urgent need to stay vigilant, maintain strong security postures, and proactively remediate vulnerabilities to protect networks against increasingly sophisticated state-backed adversaries. The fight for digital sovereignty is constant, and organizations must remain at the forefront of defense.





