Virustotal’s New Endpoint Provides Functionality Descriptions for Malware Analysts’ Code Requests
Malware analysis is a painstaking process, often likened to deciphering a complex, deliberately obscured puzzle. For cybersecurity professionals, the ability to quickly understand the intent and functionality embedded within malicious code is paramount. This speed is critical for efficient threat intelligence, incident response, and proactive defense. Recognizing this bottleneck, VirusTotal has introduced a powerful new API endpoint designed to significantly accelerate the reverse engineering workflow, providing malware analysts with immediate insights into code functionality.
VirusTotal’s Code Insight Platform: A Game Changer
VirusTotal’s Code Insight platform is already a vital resource for the cybersecurity community, offering comprehensive analysis of suspicious files and URLs. This new endpoint represents a substantial enhancement to its capabilities. It’s built to address a core challenge in malware analysis: the time and expertise required to manually dissect disassembled or decompiled code and identify its purpose.
How the New Endpoint Functions
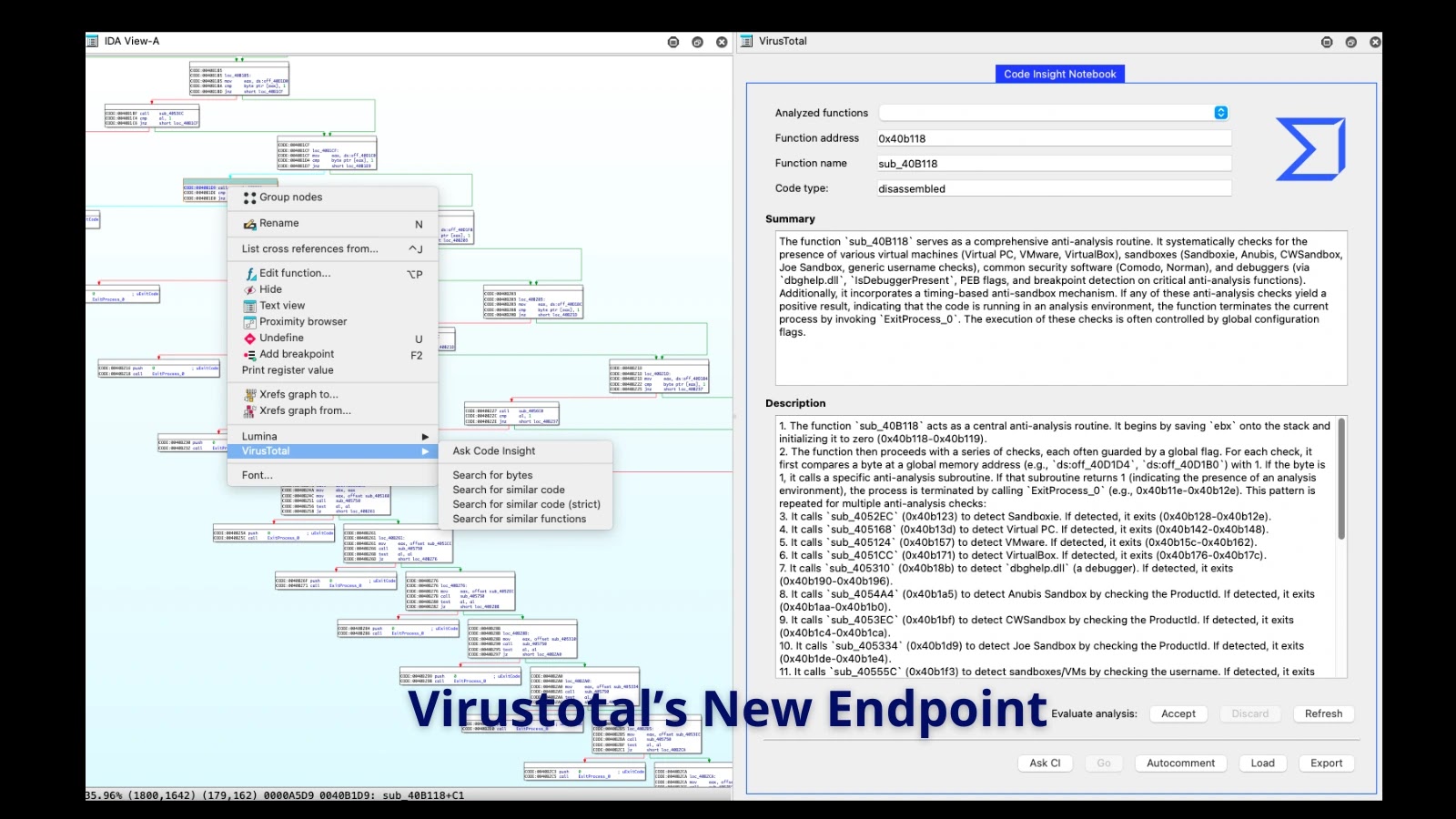
The core innovation of this new VirusTotal endpoint lies in its ability to receive raw code requests—whether disassembled or decompiled—and, in turn, provide a descriptive summary of its inherent functionality. Imagine feeding a snippet of assembly language or pseudo-C code to an intelligent system and receiving, moments later, a plain-language explanation like “This code attempts to establish persistence by modifying registry run keys” or “This module performs anti-debugging checks.”
This automated pre-analysis capability significantly reduces the initial investigative burden on malware analysts. Instead of painstakingly stepping through every instruction or function call, analysts can now quickly pinpoint the most relevant behaviors within a code sample. This highlights critical aspects such as network communication, file system manipulation, process injection, or cryptographic operations, allowing analysts to focus their deeper examination on suspicious areas already identified.
Streamlining Reverse Engineering Workflows
The immediate benefit of this new endpoint is the dramatic acceleration of the reverse engineering process. Traditionally, reverse engineering is a highly skilled and time-consuming endeavor. Analysts often spend hours, if not days, meticulously tracing code execution paths to understand a malware’s capabilities. By providing instant functionality descriptions, VirusTotal empowers analysts to:
- Prioritize Investigations: Quickly identify high-impact or novel behaviors in new malware samples.
- Enhance Efficiency: Reduce the manual effort involved in understanding routine or well-known malware behaviors.
- Improve Accuracy: Gain a quicker, high-level understanding that informs subsequent, more granular analysis.
- Scale Operations: Process a larger volume of suspicious code with greater speed.
Early adopters of this endpoint have reportedly seen significant reductions in the time required for their analysis tasks, validating its impact on operational efficiency.
Implications for Cybersecurity Professionals
For IT professionals, security analysts, and developers working in cybersecurity, this new VirusTotal endpoint is more than just a convenience; it’s a strategic advantage. It shifts the paradigm from purely reactive, manual analysis to a more proactive and automated approach. This can lead to:
- Faster identification and understanding of new threat vectors.
- More rapid development of detection signatures and defensive countermeasures.
- Improved incident response times by quickly understanding the capabilities of compromise binaries.
- Enhanced threat intelligence by allowing analysts to extract actionable insights from malware samples with greater speed.
Consider a scenario involving a newly discovered vulnerability, perhaps CVE-2023-XXXXX, for which a proof-of-concept (PoC) exploit code is released. An analyst could feed this PoC code into the new VirusTotal endpoint to quickly understand its exploitation technique, even before a full patch or signature is available. This immediate insight facilitates faster defensive hardening.
Remediation Actions for Organizations
While this new endpoint primarily aids in analysis, its existence underscores the persistent threat posed by sophisticated malware. Organizations can leverage the improved understanding gained from tools like VirusTotal’s Code Insight by implementing robust security practices:
- Invest in Skilled Personnel: Ensure your security team has the skills not only to use advanced tools but also to interpret the deeper implications of malware analysis.
- Implement Advanced Endpoint Detection and Response (EDR): EDR solutions can detect and respond to malicious activities identified through sophisticated analysis.
- Prioritize Threat Intelligence: Integrate insights from platforms like VirusTotal into your threat intelligence feeds to stay updated on emerging threats.
- Regularly Patch and Update Systems: Proactive patching remains a fundamental defense against known vulnerabilities, even those exploited by complex malware.
- Conduct Regular Security Awareness Training: Educate users about phishing, social engineering, and safe computing practices to reduce initial infection vectors.
Conclusion
VirusTotal’s new API endpoint, providing functionality descriptions for code requests, marks a significant leap forward in empowering malware analysts. It automates a critical, time-intensive aspect of reverse engineering, allowing cybersecurity professionals to gain rapid insights into malicious code. This innovation fosters greater efficiency, accelerates threat intelligence, and ultimately strengthens our collective defense against evolving cyber threats.





