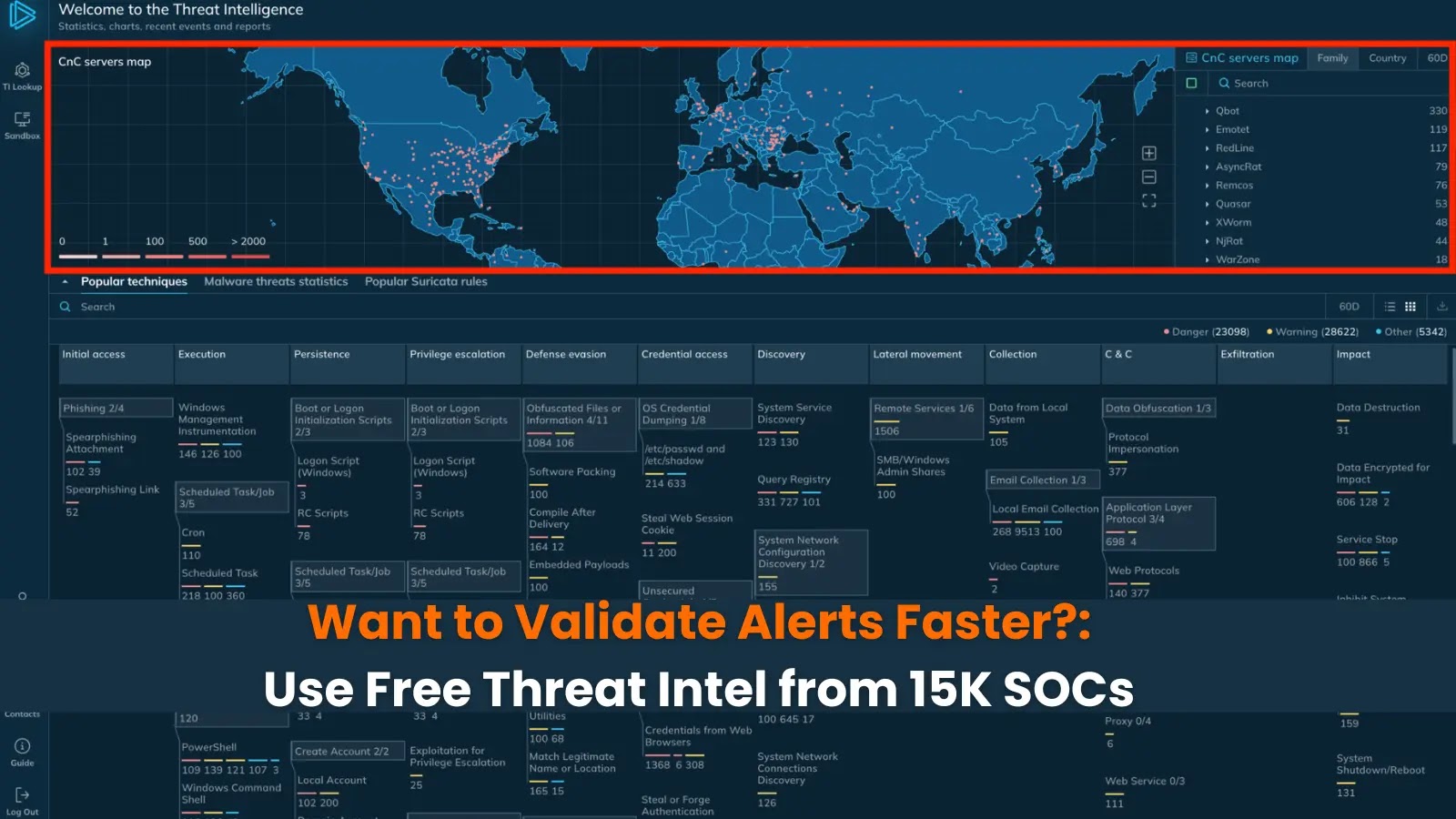
Want to Validate Alerts Faster? Use Free Threat Intel from 15K SOCs
Tired of Alert Fatigue? Unlock Faster Validation with Free Threat Intel from 15,000 SOCs
Alex stared at his SIEM dashboard, the glow reflecting in his tired eyes. The clock barely registered midnight, yet another wave of security alerts crashed over him. As a Level 2 threat analyst, this wasn’t a rare occurrence. He was drowning in false positives, painstakingly sifting through each suspicious hash, IP address, and domain, wishing for a faster, more accurate way to distinguish genuine threats from benign activity. Sound familiar? Many security operations centers (SOCs) face this daily challenge: overwhelming alert volumes and limited resources for investigation. The good news? A powerful, often overlooked resource can dramatically accelerate your alert validation process: free threat intelligence derived from the collective insights of thousands of other SOCs.
The Alert Validation Bottleneck: A Common SOC Pain Point
Modern security infrastructures generate an astounding volume of alerts. Firewalls, EDRs, IDS/IPS, and cloud security tools all feed a central SIEM, creating a constant stream of potential incidents. The sheer scale makes it nearly impossible for human analysts to investigate each alert with the same depth. This leads to:
- Alert Fatigue: Analysts become desensitized to warnings, increasing the risk of missing critical threats.
- Increased Mean Time To Respond (MTTR): Lengthy investigation times delay incident containment and remediation.
- Resource Drain: Valuable analyst time is spent on false positives instead of proactive threat hunting or strategic security improvements.
- Inconsistent Validation: Manual processes can lead to subjective and inconsistent alert prioritization.
The core problem isn’t necessarily a lack of alerts, but a lack of context and rapid validation mechanisms.
Enter Collective Threat Intelligence: The Power of 15,000 SOCs
Imagine having real-time insights from over 15,000 different Security Operations Centers globally, aggregating their detection data and verified indicators of compromise (IOCs). This isn’t just a hypothetical scenario; it’s the reality of platforms that facilitate shared, community-driven threat intelligence. By contributing to and consuming from such a vast network, individual SOCs gain an unparalleled advantage:
- Instant Context: Instead of laboriously researching each suspicious IP or domain, your SIEM or SOAR platform can instantly query these intelligence feeds. If an IP address has been flagged as malicious by hundreds of other SOCs in the last hour, its threat score skyrockets, demanding immediate attention.
- Reduced False Positives: If an internal domain or legitimate external service IP keeps appearing as suspicious in your alerts but is not present in widespread threat intel feeds, it’s a strong indicator of a false positive, saving valuable investigation time.
- Early Warning System: Before a widespread attack hits your specific sector, other SOCs may have already detected and reported related IOCs, providing you with an early warning to fortify defenses or proactively hunt for those indicators.
- Democratization of Threat Intel: High-quality, timely threat intelligence often comes with a hefty price tag. Community-driven platforms make advanced threat insights accessible to organizations of all sizes, leveling the playing field.
How Free Threat Intel Transforms Alert Validation Workflows
Integrating collective threat intelligence into your alert validation process fundamentally changes how your analysts operate:
- Automated Enrichment: Configure your SIEM or SOAR solution to automatically query threat intelligence platforms for every suspicious IP, domain, URL, or hash encountered in an alert.
- Triage Prioritization: Alerts associated with IOCs widely reported as malicious by the community are automatically elevated in priority, ensuring critical threats get immediate attention.
- Contextualized Investigations: Analysts receive alerts pre-enriched with threat scores, associated malware families, known attack campaigns, and reputation data, significantly shortening investigation times.
- Proactive Hunting: Threat hunting teams can leverage these aggregated IOCs to proactively search their environments for signs of compromise that might have bypassed initial detection.
For instance, if your SIEM flags an outbound connection to an IP address (e.g., 203.0.113.42) and a quick check against a community threat intelligence feed reveals this IP was reported by 500+ SOCs within the last 24 hours for hosting ransomware command-and-control (C2) activity, the alert’s priority shifts from “investigate when free” to “IMMEDIATE ACTION REQUIRED.”
Example: Validating a Suspicious Hash
Consider an EDR alert flagging a suspicious executable with a specific MD5 hash: e4d1f2a3c5b6d8e0f7a9b1c2d3e4f5a6. Manually researching this hash could take minutes to hours, checking various online sandboxes and reputation services. However, if your alert validation workflow includes a query to a community-sourced threat intelligence platform, it could instantly return information like:
- Reputation: Malicious, High Confidence.
- Associated Malware: Known variant of Emotet/TrickBot.
- Detection Count: Detected by 1,200+ other SOCs in the last 48 hours.
- Related CVEs: Often exploited via CVE-2017-11882 (Microsoft Office memory corruption vulnerability).
This rich context allows the analyst to validate the alert faster, understand the potential impact, and initiate appropriate response actions much more rapidly, potentially preventing a full-scale breach.
Actionable Steps to Leverage Free Threat Intel
Integrating free, community-driven threat intelligence doesn’t require a complete overhaul of your security stack. Here’s how to begin:
- Identify Relevant Feeds: Research reputable, community-driven threat intelligence platforms that offer free or freemium access (e.g., MISP, abuse.ch, certain open-source projects, or platforms described in the referenced article).
- Integrate with Existing Tools: Many SIEM, SOAR, and EDR platforms have built-in connectors or APIs to ingest external threat feeds. Prioritize integration with your primary alert aggregation platform.
- Automate Enrichment and Prioritization: Configure rules within your SIEM or SOAR to automatically query threat intel feeds for indicator reputation and to adjust alert priorities based on the findings.
- Start Small, Iterate: Don’t try to integrate every feed at once. Start with one or two high-impact feeds, monitor their effectiveness, and then expand.
- Consider Contributing: If feasible and appropriate for your organization’s policy, consider contributing anonymized or sanitized IOCs back to the community. This strengthens the collective defense for everyone.
Conclusion: The Future of Faster, Smarter Alert Validation
The constant battle against cyber threats demands efficiency and speed. Relying solely on manual investigation of every alert is unsustainable and ineffective. By harnessing the collective power of free threat intelligence sourced from thousands of other SOCs, organizations can dramatically improve their alert validation processes. This shift not only reduces analyst fatigue and false positives but also enables faster incident response, ultimately strengthening the organization’s overall security posture. Embrace community intelligence to move beyond constantly reacting to alerts, and start making more informed, proactive security decisions.





