Weaponized PuTTY Via Bing Ads Exploit Kerberos and Attack Active Directory Services
The Silent Compromise: Weaponized PuTTY, Bing Ads, and the Active Directory Assault
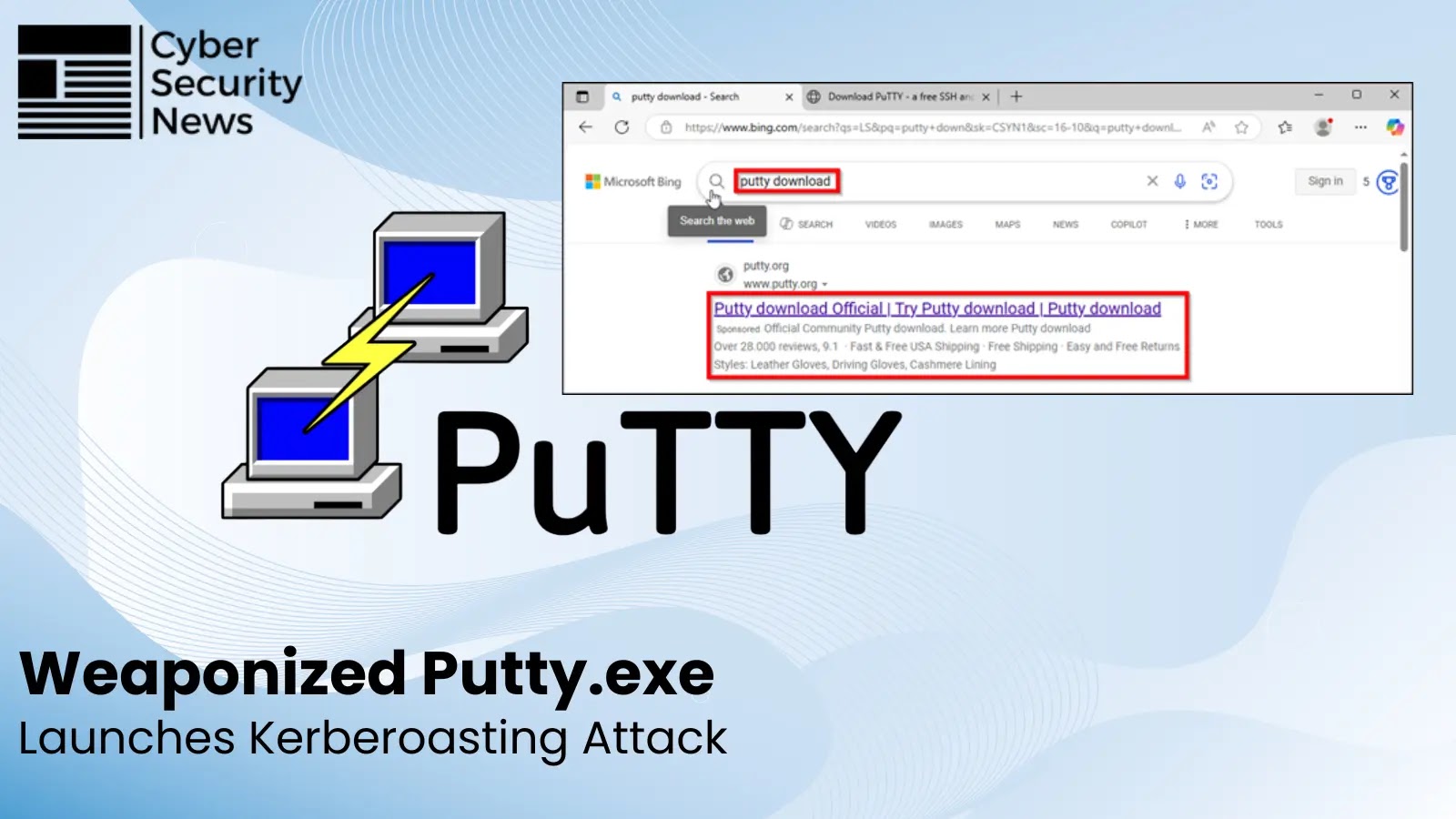
In the evolving landscape of cyber threats, the sophistication of attack vectors continues to escalate. A recent and alarming campaign leveraged trusted platforms and widely used tools to achieve a critical compromise: weaponized PuTTY delivered via Bing Ads, targeting Active Directory services through Kerberoasting. This incident serves as a stark reminder that even seemingly reliable avenues can be exploited, demanding heightened vigilance from cybersecurity professionals.
Anatomy of the Attack: Malvertising to Domain Dominance
This malvertising campaign exploited the inherent trust users place in search engine results. By sponsoring malicious advertisements on Microsoft’s Bing platform, threat actors managed to present their weaponized software as legitimate versions of PuTTY, a ubiquitous SSH and Telnet client. Unwitting users clicking these sponsored results downloaded a trojanized version of PuTTY, initiating a multi-stage attack:
- Initial Compromise and Persistence: The weaponized PuTTY established persistence on the victim’s system, laying the groundwork for subsequent malicious activities.
- Hands-on-Keyboard Control: The attackers gained remote access, enabling “hands-on-keyboard” control over the compromised machine. This level of access grants significant operational flexibility to the threat actors.
- Kerberoasting for Active Directory Service Account Credentials: A critical phase of the attack involved Kerberoasting. This technique targets Active Directory service accounts by requesting Kerberos Service Tickets (specifically, TGS_REQ messages) for these accounts. When a service account uses a weak password, its hashed password can be easily cracked offline from the retrieved ticket, providing the attacker with credentials that often grant privileged access within the domain.
This method bypasses typical network-based intrusion detection by exploiting legitimate Kerberos functionality, making it particularly insidious.
The Role of PuTTY and Kerberoasting
PuTTY’s Unfortunate Role: PuTTY itself is not inherently vulnerable in this scenario. The issue stems from attackers distributing a modified, malicious version of the legitimate software. This tactic, often referred to as “software supply chain attack” or “trojanized legitimate software,” preys on user reliance and the difficulty in discerning authentic binaries from malicious ones.
Kerberoasting Explained: Kerberoasting is a post-exploitation technique used to extract hashes of Active Directory service account passwords. Attackers, with sufficient privileges to request service tickets (even as a standard domain user), can request a ticket for any service principal name (SPN) registered in Active Directory. When the domain controller returns the ticket, parts of it are encrypted with the service account’s NTLM hash. This hash can then be extracted and cracked offline, commonly through brute-force or dictionary attacks, without triggering alerts on the domain controller.
Impact and Implications for Active Directory Security
The successful execution of Kerberoasting against Active Directory service accounts can have devastating consequences:
- Privilege Escalation: Cracked service account credentials often lead directly to privilege escalation, granting attackers elevated access within the domain.
- Lateral Movement: With these credentials, attackers can move laterally across the network, accessing sensitive systems and data controlled by those service accounts.
- Domain Compromise: In the worst-case scenario, compromise of highly privileged service accounts (e.g., those used by database servers, backup systems, or management tools) can lead to full domain compromise.
- Data Exfiltration and Ransomware Deployment: Once domain control is established, attackers are free to exfiltrate sensitive data, deploy ransomware, or establish long-term persistence.
Remediation Actions and Proactive Defenses
Protecting against such sophisticated attacks requires a multi-layered approach, focusing on prevention, detection, and rapid response:
- User Education and Awareness: Train users to be suspicious of sponsored ads, especially for free or open-source software. Emphasize downloading software only from official vendor websites or trusted repositories.
- Strong Password Policies for Service Accounts: Implement strict password policies for all Active Directory service accounts. Passwords should be long (18+ characters), complex, unique, and frequently rotated. Avoid using the same password for multiple service accounts.
- Service Principal Name (SPN) Hygiene: Regularly audit and clean up SPNs. Remove unnecessary SPNs and ensure valid SPNs are correctly associated with their respective service accounts.
- Least Privilege Principle: Ensure service accounts operate with the absolute minimum necessary privileges. Avoid granting administrative rights to service accounts unless absolutely critical.
- Monitoring Kerberos Traffic: Implement robust logging and monitoring for suspicious Kerberos ticket requests. Look for an unusually high volume of TGS_REQ messages for service accounts, especially from atypical source IPs.
- Endpoint Detection and Response (EDR): Deploy EDR solutions that can detect malicious processes, persistence mechanisms, and suspicious activity on endpoints, including the execution of trojanized software.
- Web Gateway and DNS Filtering: Utilize secure web gateways and DNS filtering to block access to known malicious domains and prevent users from reaching sites hosting weaponized software.
- Application Whitelisting: Implement application whitelisting (e.g., through AppLocker or Windows Defender Application Control) to restrict the execution of unauthorized software on endpoints.
- Threat Intelligence Integration: Stay updated with the latest threat intelligence on malvertising campaigns, specific attack vectors (like the Oyster/Broomstick backdoor activity mentioned in the source), and trojanized tools.
Relevant Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| BloodHound | Identifies complex attack paths, including Kerberoasting opportunities, in Active Directory environments. | https://bloodhound.github.io/ |
| Mimikatz | While an attacker tool, defenders can use it in a controlled environment to simulate Kerberoasting attacks for testing detection capabilities. | https://github.com/gentilkiwi/mimikatz |
| ADRecon | Gathers information about the Active Directory environment to assess security posture and identify misconfigurations. | https://github.com/sensepost/ADRecon |
| Microsoft Defender for Identity | Detects advanced threats, including Kerberoasting, by monitoring Active Directory traffic and events. | https://learn.microsoft.com/en-us/defender-for-identity/ |
Conclusion: Continuous Vigilance is Paramount
The weaponization of PuTTY via Bing Ads, culminating in Kerberoasting attacks against Active Directory, underscores a critical shift in attacker methodology: leveraging trusted channels and techniques to achieve deep network compromise. This incident is not an isolated event but part of a broader trend where attackers exploit human trust and legitimate system functionalities.
For cybersecurity professionals, the key takeaway is the absolute necessity of holistic security. This includes rigorous endpoint security, intelligent network monitoring, robust Active Directory hygiene, and, most importantly, a well-informed and security-conscious user base. Proactive defense, continuous monitoring, and rapid incident response are no longer optional but foundational to safeguarding organizational assets against these sophisticated and often stealthy attacks.
Stay vigilant, stay secure.





