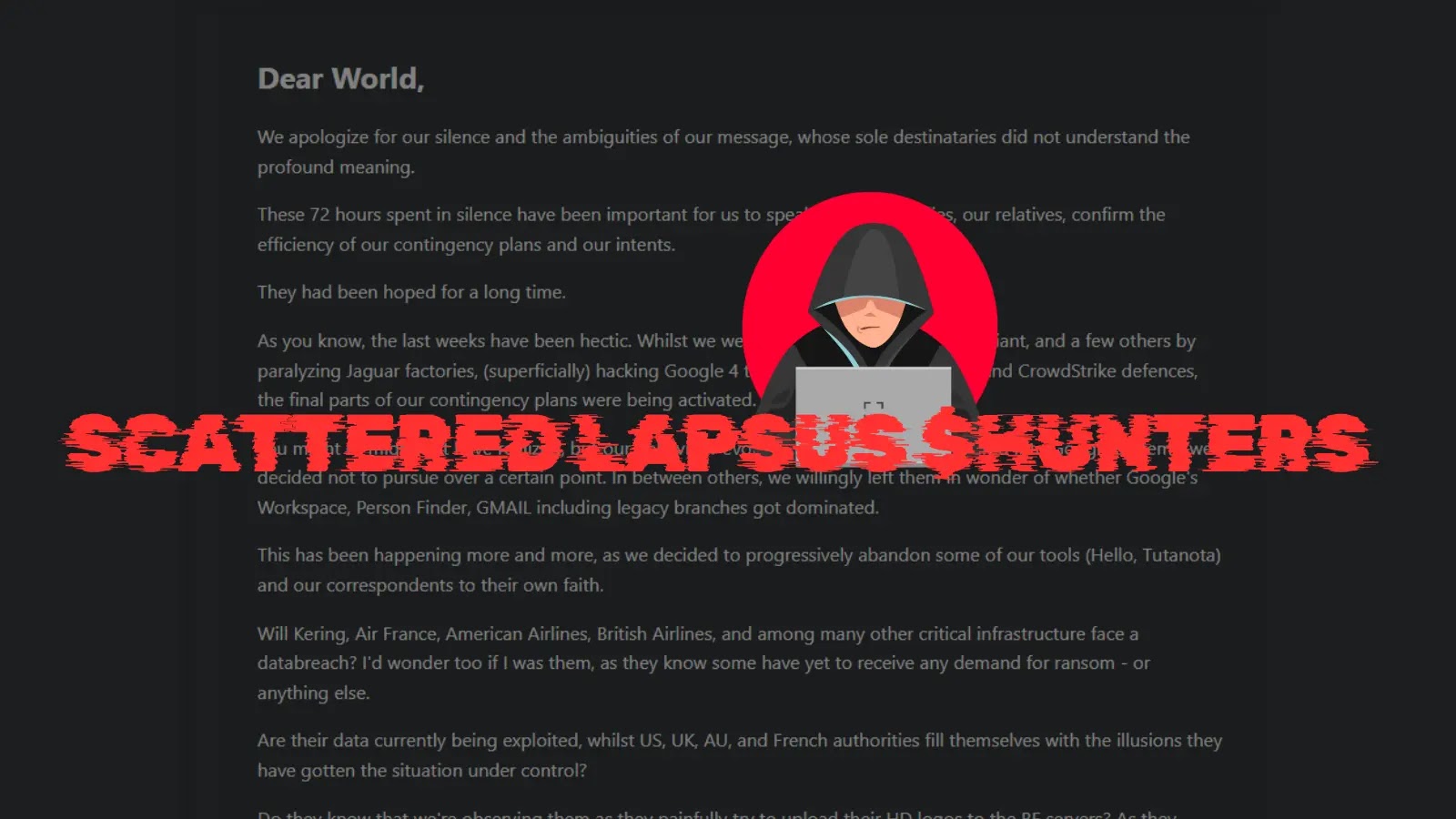
What Are The Takeaways From The Scattered LAPSUS $Hunters Statement?
The digital shadows cast by cybercriminal groups often obscure their true motives and operational strategies. However, a recent, highly unusual “farewell statement” from the notorious Scattered LAPSUS$ Hunters on BreachForums has ripped a corner off this veil. This manifesto, far from a simple adieu, is a potent cocktail of confession, strategic misdirection, and a chilling testament to the evolving cat-and-mouse game between sophisticated threat actors and global law enforcement. For cybersecurity professionals, it offers invaluable insights into the shifting landscape of modern cybercrime, demanding a re-evaluation of defensive strategies.
The Scattered LAPSUS$ Hunters: A Cryptic swansong
The Scattered LAPSUS$ Hunters, a name synonymous with high-profile data breaches and extortion, made waves not with another attack, but with an unexpected public declaration. Published on the illicit platform BreachForums, this statement is less a retirement notice and more a strategic maneuver. It reveals a group under immense pressure, yet one still capable of sophisticated operational security (OpSec) and manipulative communication. This isn’t just about a group disbanding; it’s about understanding why and how such a powerful entity acknowledges defeat, or at least, a strategic pause.
Key Takeaways for Cybersecurity Professionals
Analyzing the nuances of the Scattered LAPSUS$ Hunters’ statement provides several critical lessons for those on the front lines of cybersecurity:
- Escalating Law Enforcement Pressure: The primary catalyst for the group’s alleged cessation of activities appears to be heightened global law enforcement efforts. This underscores the growing effectiveness of international cooperation in dismantling sophisticated cybercriminal enterprises. It’s a clear signal that the net is tightening, forcing even well-resourced groups to reconsider their longevity.
- Advanced Operational Security (OpSec) Practices: Despite their eventual public retreat, the statement hints at sophisticated OpSec that allowed the group to operate effectively for an extended period. This includes methods of communication, infrastructure management, and evasion techniques that likely extend beyond conventional measures. Understanding these implied tactics can help in developing more robust threat intelligence models.
- Strategic Deception and Misdirection: The “farewell” itself might be a form of strategic deception. Cybercriminal groups are adept at manipulating narratives to reduce scrutiny, sow confusion, or even prepare for a rebranding. Professionals must view such pronouncements with skepticism, recognizing the potential for sophisticated psychological operations. The statement could be an attempt to lower defenses or divert attention while the group reorganizes or re-emerges under a new guise.
- The Human Element in Cybercrime: The statement, though veiled, still carries undertones of human decision-making, pressure, and potentially internal conflicts. Recognizing the human element – the motivations, fears, and strategic thinking of adversaries – is crucial for developing proactive defense strategies that go beyond purely technical countermeasures.
- The Enduring Threat Landscape: While one group may declare a hiatus, the underlying vulnerabilities and opportunities for cybercrime remain. The methods and targets exploited by Scattered LAPSUS$ Hunters will likely be adopted or evolved by other groups. This statement doesn’t signal the end of a threat; it signifies a dynamic shift that demands constant vigilance and adaptation.
Remediation Actions and Proactive Defense
While the Scattered LAPSUS$ Hunters statement isn’t about a specific vulnerability (e.g., CVE-2023-38831, a recently exploited WinRAR vulnerability that could be used in similar social engineering attacks), it highlights the need for robust overall cybersecurity posture. Organizations must adapt their defenses to counter the evolving tactics hinted at by the group’s operations:
- Enhance Threat Intelligence Gathering: Actively monitor dark web forums, threat intelligence feeds, and security bulletins to track emerging attacker tactics, techniques, and procedures (TTPs).
- Strengthen Operational Security (OpSec) Internally: Implement rigorous OpSec practices within your own organization. This includes secure communication channels, strict access controls, and regular training on social engineering awareness.
- Improve Employee Awareness Training: Regularly educate employees on phishing, social engineering, and the tactics used by groups like LAPSUS$ to gain initial access. Phishing simulations are invaluable tools.
- Multi-Factor Authentication (MFA) Everywhere: Enforce MFA across all critical systems and accounts. This remains one of the most effective deterrents against credential theft.
- Regular Security Audits and Penetration Testing: Continuously assess your organization’s security posture to identify and remediate weaknesses before they can be exploited.
- Incident Response Plan Review: Ensure your incident response plan is up-to-date, tested, and capable of addressing sophisticated and deceptive attacks.
The departure, or strategic retreat, of the Scattered LAPSUS$ Hunters is a significant event in the cybercrime landscape. It underlines the relentless pressure applied by law enforcement, yet it also reminds us of the sophistication and strategic depth demonstrated by these adversaries. For cybersecurity professionals, the key takeaway is not just that one threat actor might be gone, but the invaluable intelligence gleaned from their final act. This information, if properly analyzed and integrated into defensive strategies, can significantly bolster an organization’s resilience against the next wave of evolving cyber threats.





