What is SASE (Secure Access Service Edge) : Why it’s the future?
Secure Access Service Edge (SASE): What is it?
The digital transformation rapidly reshaping today’s business landscape demands a robust approach to network security and access. The Secure Access Service Edge (SASE) emerges as a comprehensive guide to address these challenges. By combining network and security services into a unified cloud-native architecture, SASE offers a holistic solution that streamlines and secures cloud service and network access. This innovative approach is crucial for organisations aiming to safeguard their infrastructure while ensuring seamless and secure connectivity across wide area networks and enhancing data security. Understanding SASE’s role and implementation can empower enterprises to enhance their cybersecurity posture effectively.
Understanding Secure Access Service Edge
Definition of SASE
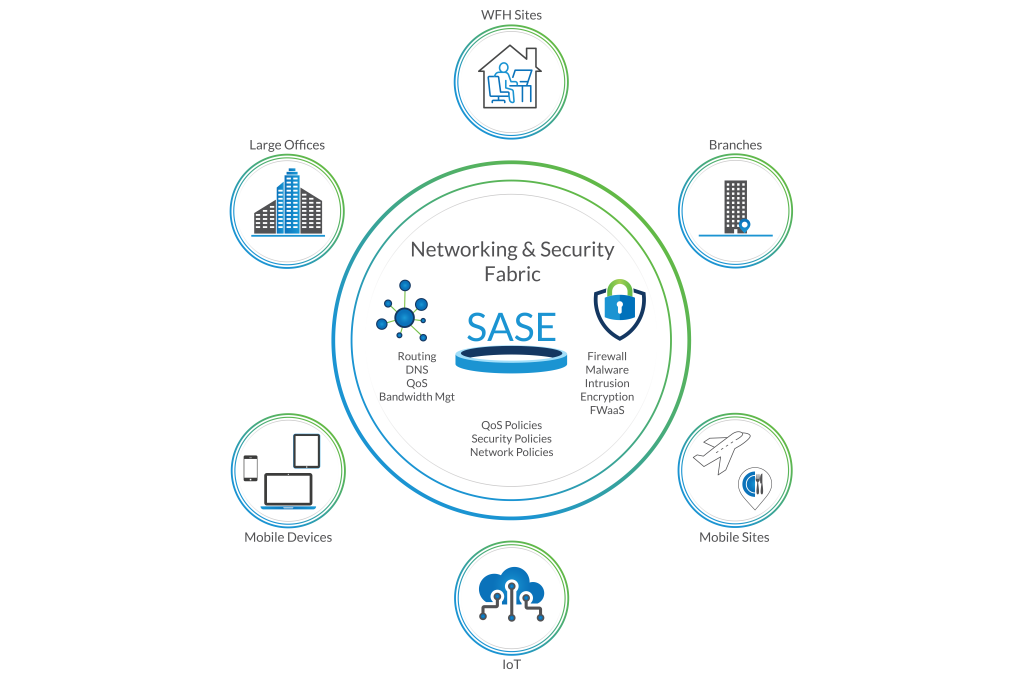
Secure Access Service Edge, or SASE, represents a transformative shift in how network and security functions are delivered. This approach integrates network security services, such as secure web gateways and cloud access security brokers, into a single, cloud-based platform. By doing so, SASE simplifies the management of security policies and network access, ensuring that security functions are consistently applied across all endpoints and data centres in a zero-trust security framework. At its core, SASE provides a secure, scalable, and flexible framework that supports zero-trust network access, allowing organisations to protect their assets while adapting swiftly to evolving cybersecurity threats.
Key Components of SASE
The key components of SASE architecture are designed to deliver comprehensive network and security solutions, including robust data security measures. These components include:
- The security service edge, which fortifies network security functions such as access control and threat protection, is essential in a zero-trust security environment.
- Secure web gateways that filter and monitor web traffic.
- Zero-trust principles that enforce strict access controls.
- Cloud-native security functions, allowing for efficient threat detection and response.
By unifying these components, SASE enables organizations to adopt a proactive and robust approach to network security, ensuring a resilient defense against potential cyber threats through a robust security model.
SASE Architecture Explained
SASE architecture seamlessly combines network and security services into a cohesive framework, delivering a streamlined security solution. This architecture shifts traditional security functions from on-premises to the cloud, leveraging a SASE cloud platform to provide flexible, scalable, and efficient security services. The SASE approach enhances network access by deploying security policies closer to the user, regardless of their location. This cloud-native SASE model ensures that security is consistent and pervasive across all network edges, aligning with the goal of SASE to deliver secure, reliable, and high-performance access to both cloud and on-premises resources. As a result, organisations can fortify their defenses while optimizing network performance.
Benefits of SASE
| Benefit | Description | Impact |
|---|---|---|
| Flexibility | Offers direct access to cloud or network from any location, enabling simple implementation of novel digital business models. | Reduces network access time by 75% |
| Cost Savings | Security-as-a-service model eliminates the need for on-premises equipment and provides reduced, predictable operational expenses. | Saves 85% of annual expenditure |
| Reduced Complexity | Cloud-based integration removes the need for a complex stack of legacy solutions, reducing operational effort. | Increases productivity by 55% |
| Increased Performance | Speeds up access to online resources using a global network architecture optimized for: • Low latency • High capacity • High availability |
[Impact not provided] |
| Threat Protection | Prevents cloud and online threats such as: • Malware • Cloud phishing • Ransomware • Malevolent insiders |
[Impact not provided] |
| Data Protection | Secures data flow between public and private networks. | [Impact not provided] |
Advantages of SASE for Organizations
Secure Access Service Edge (SASE) presents numerous advantages for organizations seeking to enhance their network and security infrastructure. By integrating security and network services into a unified SASE platform, businesses can benefit from streamlined operations and improved security posture, leveraging advanced security capabilities. This comprehensive SASE solution simplifies the management of security policies, ensuring consistent application across all endpoints and data centers. Organizations adopting SASE enjoy enhanced scalability and flexibility, allowing them to adapt swiftly to evolving threats while maintaining seamless network access. With SASE, enterprises are empowered to fortify their defenses, ensuring reliable and secure connectivity across their wide area networks.
SASE vs Traditional Security Solutions
When comparing SASE to traditional security solutions, the differences are profound. Traditional approaches often involve disparate security functions spread across multiple vendors, leading to complexity and potential security gaps. In contrast, SASE combines network and security functions into a single, cohesive framework, offering a more integrated and efficient approach to network security. The SASE architecture leverages cloud-native capabilities, providing scalable and flexible security service delivery. This ensures that security policies are enforced consistently, regardless of user location, which is a key aspect of zero trust security. By adopting SASE, organizations can achieve a higher level of protection and operational efficiency, mitigating risks more effectively than with conventional methods.
Pivotal SASE Benefits for Network Security
SASE’s pivotal benefits for network security lie in its ability to enhance both protection and performance. By choosing a SASE provider, organizations can leverage these capabilities to achieve a proactive stance on cybersecurity. Some of the key components of the SASE framework include:
- Integration of zero trust network access and secure web gateways, ensuring robust access control and threat detection across all network edges.
- Cloud access security broker component, which secures cloud service interactions.
This security service edge fortifies defenses against cyber threats, reducing vulnerabilities and enhancing resilience. The SASE approach aligns with the goal of delivering comprehensive network security solutions, ensuring the safety and success of enterprises in a digital landscape.
How SASE Works?
Mechanisms of SASE Functionality
The Secure Access Service Edge (SASE) operates by integrating network and security functions into a cohesive framework that integrates both SSE and SASE to enhance overall security capabilities. This integration is achieved through the deployment of a cloud-native SASE platform, where security policies are consistently enforced across all network edges. By leveraging secure web gateways and cloud access security brokers, SASE ensures that data and applications are protected in real-time from potential threats, irrespective of user location. The platform seamlessly combines network and security services, creating an environment where security functions are optimized and threats are mitigated efficiently, thereby empowering organizations to maintain a robust security posture.
Integration of Network and Security Functions
SASE distinguishes itself through the seamless integration of network and security functions, offering a unified approach to IT infrastructure. By consolidating these functions, SASE simplifies the management of security service delivery, ensuring that security policies are applied uniformly across all endpoints and data centers, ultimately improving network and security capabilities. This integration is facilitated by the SASE cloud platform, which supports a wide array of security services such as access control, threat detection, and secure network access. The resulting SASE architecture not only enhances security but also optimizes network performance, enabling organizations to adapt quickly to evolving cybersecurity challenges while ensuring secure and efficient access to resources.
Zero Trust Approach within SASE
A cornerstone of the SASE solution is its implementation of a zero trust approach, which fundamentally redefines how access and security are managed. Zero trust network access within SASE means that trust is never assumed; instead, verification is required for every access request, regardless of the user’s location or device. This approach ensures that only authenticated users gain access to sensitive data and applications, significantly reducing the risk of unauthorized access. By incorporating zero trust principles, SASE fortifies an organization’s defenses and enhances its security capabilities, ensuring that security functions are aligned with the highest standards of protection and reliability. This comprehensive approach is critical in safeguarding your enterprise against emerging cyber threats.
SASE Implementation
| Step 1 –> | Step 2 –> | Step 3 –> | Step 4 |
| Assessment and Planning | Vendor Selection and Roadmap Definition | Implementation and Transition | Testing, Monitoring, and Continuous Improvement |
| Assessment of Current Infrastructure | Vendor Selection | User Training and Communication | Testing and Quality Assurance |
| Set Clear Objectives and Goals | Pilot Phase Planning | Deployment Phases | Monitoring and Maintenance Plan |
| Identify Key Stakeholders | Policy Development | ||
| Budget and Resource Planning | |||
| Regulatory and Compliance Considerations |
Choosing a SASE Provider
Choosing a SASE provider is a critical step in the successful implementation of a Secure Access Service Edge (SASE) solution. Organizations must prioritize providers that offer a comprehensive SASE platform, integrating network and security services seamlessly. The ideal provider should deliver robust network security functions, including secure web gateways and cloud access security brokers, within a cloud-native SASE framework. Additionally, emphasis should be placed on the provider’s ability to enforce consistent security policies across all network edges. By selecting a trustworthy and proficient SASE vendor, enterprises can assure their infrastructure is secure and reliable, safeguarding their operations in a rapidly evolving digital landscape.
Potential SASE Implementation Challenges
Implementing SASE can present several challenges, which organizations must anticipate and address proactively. The integration of network and security functions into a single platform may require significant adjustments in existing IT infrastructure and processes. Companies might encounter difficulties in aligning security policies across diverse endpoints and data centers, especially within a wide area network. Additionally, ensuring seamless network access while maintaining robust security poses a challenge. To overcome these hurdles, a well-planned SASE deployment, supported by a knowledgeable security team, is essential. Understanding potential SASE implementation challenges empowers organizations to mitigate risks, ensuring a smooth transition to a more secure and efficient network architecture.
Strategies for Successful SASE Implementation
To ensure a successful SASE implementation, organizations should adopt a strategic approach that encompasses comprehensive planning and execution. Begin by conducting a thorough assessment of current security and network infrastructure to identify areas for improvement in traditional network security. Collaborate closely with your chosen SASE provider to tailor solutions that align with specific business needs and enhance the enterprise network. Emphasize the importance of zero trust network access to bolster security measures. It’s crucial to implement robust access control mechanisms and ensure that security functions are optimized for performance. By adopting these strategies, businesses can effectively leverage SASE capabilities, fortifying their defenses and enhancing overall network security.
Secure Access Service Edge Solutions
SASE Platforms in the Market
In the dynamic landscape of cybersecurity, various SASE platforms have emerged, each offering distinct capabilities to address the security needs of modern enterprises. These platforms integrate key components of SASE, such as secure web gateways and cloud access security brokers, into a unified framework. By providing cloud-native security services, these platforms enable organizations to enhance their network security posture while ensuring efficient and secure network access. The diverse offerings in the market allow businesses to choose a SASE solution that aligns with their specific requirements, empowering them to adopt SASE and achieve comprehensive security across their network environments.
Single-Vendor SASE vs Multi-Vendor Approaches
When evaluating SASE solutions, organizations often face the decision between single-vendor and multi-vendor approaches can impact the effectiveness of a SASE deployment.. Here are some considerations for each approach:
- A single-vendor SASE solution offers the advantage of a cohesive and integrated platform, simplifying the management of security policies and network functions. This approach ensures seamless coordination of security service delivery, bolstering the organization’s overall cybersecurity strategy.
- A multi-vendor approach allows for greater flexibility and customization, enabling businesses to select best-of-breed components. However, it may introduce complexity in integration and management.
Ultimately, the choice between single-vendor and multi-vendor SASE depends on the organization’s unique needs and priorities, as well as their capacity to manage potential challenges.
Evaluating SASE Security Services
Evaluating SASE security services requires a comprehensive understanding of the offered network and security solutions. Organizations should assess the provider’s ability to deliver robust security functions, including zero trust network access, secure web gateways, and cloud access security brokers. Additionally, it’s essential to evaluate the scalability and flexibility of the SASE architecture, ensuring it can adapt to evolving cybersecurity threats. By scrutinizing the SASE platform’s capabilities and assessing its alignment with the organization’s security objectives, businesses can make informed decisions. This evaluation process is crucial to fortifying the organization’s defenses, ensuring optimal protection and performance in a digitally connected world through enhanced network and security capabilities.
5 Surprising Facts About SASE (Secure Access Service Edge)
- SASE integrates networking and security services into a single cloud-based solution, simplifying management and deployment.
- It enables secure access to applications regardless of the user’s location, making it ideal for remote workforces.
- SASE is not just a trend; it’s a fundamental shift in how organizations approach cybersecurity and network architecture.
- According to research, organizations adopting SASE can reduce their overall IT costs by consolidating multiple services into one platform.
- SASE supports zero trust principles, ensuring that every user and device is verified before accessing resources, enhancing security significantly.
What is SASE and why is it important for secure access to applications?
SASE, or Secure Access Service Edge, is a cloud-based security architecture that combines network and security functions into a unified framework. It is important because it provides secure access to applications and data, especially in remote work environments where traditional corporate networks may not suffice.
How does SASE work to optimize remote access?
SASE works by leveraging cloud-delivered services to optimize remote access. It integrates various security components, such as secure web gateways and zero trust network access, to ensure that users have secure access to applications regardless of their location.
What are the key components of SASE architecture?
The key components of SASE architecture include a cloud-delivered security stack, secure web gateways, cloud access security brokers, and zero trust network access solutions. These components work together to provide secure access to applications and data across the organization.
What are the benefits of SASE for organizations?
The benefits of SASE include enhanced security posture, improved user experience, and reduced complexity in managing multiple security solutions. By converging network and security functions, SASE allows organizations to provide secure access to applications without compromising performance.
How does SASE compare to traditional security solutions?
SASE differs from traditional security solutions by combining network and security functions into a single, cloud-based service. This approach allows for greater flexibility and scalability, ensuring that organizations can adapt to changing security needs without the constraints of a traditional corporate network.
What challenges may arise during SASE implementation?
Potential SASE implementation challenges include integration with existing security solutions, managing user experience across diverse locations, and ensuring compliance with industry regulations. Organizations should carefully plan their SASE strategy to address these challenges effectively.
How can organizations choose the right SASE provider?
When choosing a SASE provider, organizations should evaluate the provider’s ability to deliver a comprehensive security solution, including key security functions and support for zero trust principles. It’s also important to consider the provider’s track record in delivering cloud-delivered services and their ability to integrate with existing security components.
What is the future potential of SASE in the evolving security landscape?
The future potential of SASE is significant as organizations increasingly move towards cloud-based environments. SASE allows for seamless integration of security services and network functions, creating a more agile security architecture that can respond effectively to new threats and the demands of a remote workforce.
What are the key components of SASE (Secure Access Service Edge)?
The key components of SASE include a cloud-based architecture that integrates network and security functions into a single service. This architecture typically consists of SD-WAN (Software-Defined Wide Area Networking), secure web gateways, firewall-as-a-service, and zero trust network access. By converging these elements, SASE delivers a comprehensive security solution that optimizes performance and enhances security posture.
Why is SASE important for modern enterprises?
SASE is important because it addresses the challenges of securing remote workforces and cloud applications. As businesses move towards cloud services, the traditional network perimeter dissolves, making it crucial to have a framework that combines security with network connectivity. SASE enhances the security posture of organizations by ensuring secure access regardless of location.
How does SASE work to secure networks?
SASE works by leveraging a cloud-based model that delivers network and security capabilities directly to users, regardless of their location. By utilizing a zero trust approach, it ensures that every device and user is authenticated and authorized before accessing resources. This model not only optimizes network performance but also extends security across all endpoints.
What are the benefits of using a SASE solution?
The benefits of using a SASE solution include improved security, enhanced user experience, and reduced costs. By combining network and security functions into a single platform, organizations can streamline their operations and reduce the complexity associated with managing multiple security services. Additionally, SASE helps in scaling security measures without compromising performance.
How can organizations choose a SASE provider?
Organizations can choose a SASE provider by evaluating their specific needs, assessing the provider’s capabilities in delivering SASE services, and understanding their approach to integrating network and security functions. It is important to consider the provider’s expertise in zero trust architecture and their ability to optimize security solutions for diverse environments.
What potential challenges come with SASE implementation?
Potential SASE implementation challenges include integration with existing infrastructure, managing a diverse range of security service functions, and ensuring seamless user experience during the transition. Organizations must also be prepared to educate their teams on the new security framework and address any resistance to change as they adopt this new model.
How does SASE optimize network performance?
SASE optimizes network performance by utilizing a distributed cloud infrastructure that brings services closer to the user, reducing latency and improving access speed. By leveraging SD-WAN technology, SASE can intelligently route traffic based on real-time conditions, ensuring efficient use of bandwidth and enhancing the overall user experience.
What does the future hold for SASE?
The future of SASE looks promising as more organizations recognize its potential to streamline network and security functions. With the increasing reliance on cloud services and remote work, SASE will likely become a standard in enterprise networking. As technology evolves, SASE will continue to adapt, delivering better integration and optimization for security solutions.