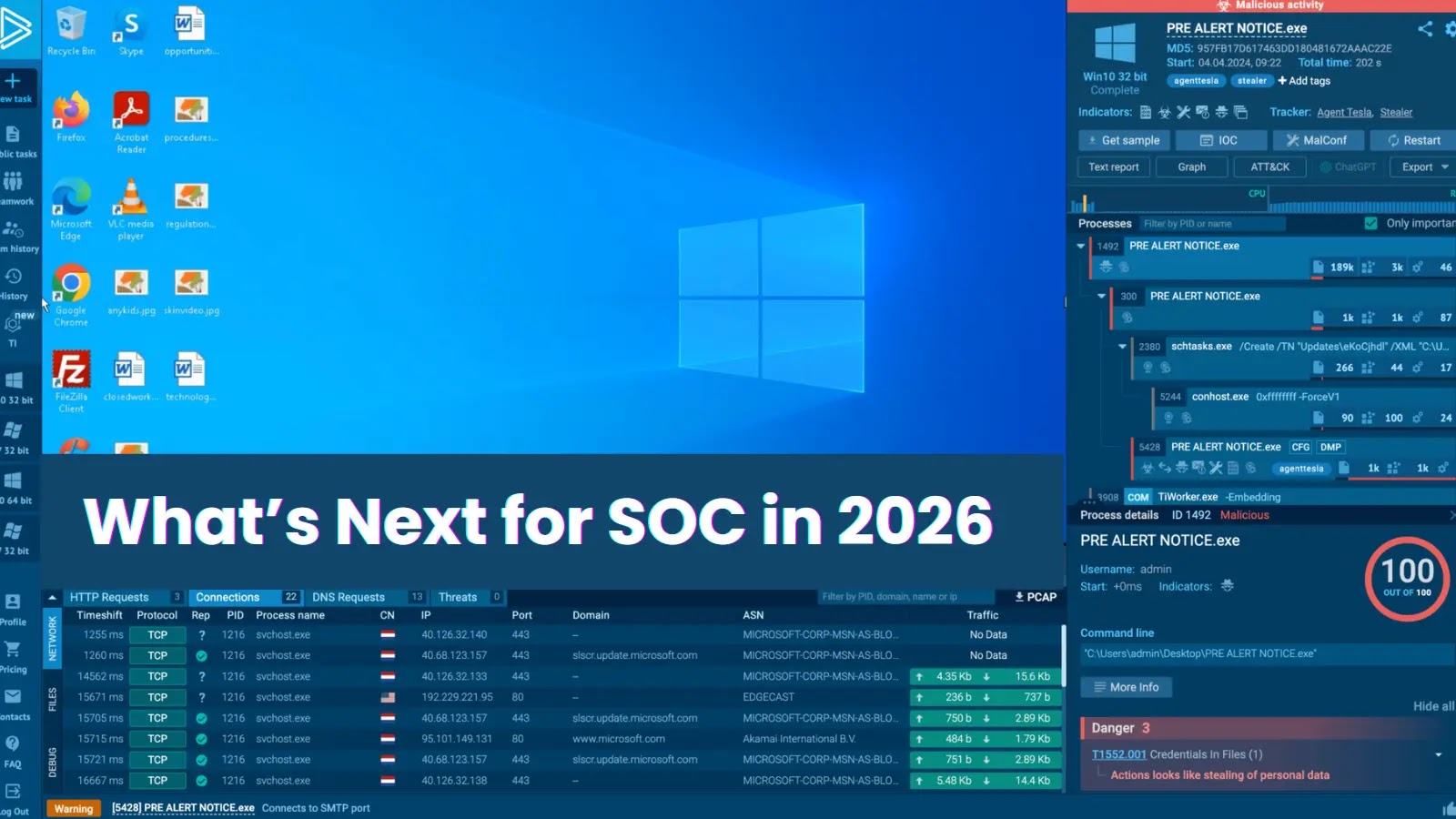
What’s Next for SOC in 2026: Get the Early-Adopter Advantage
The AI Apex Predator: What’s Next for SOC in 2026 and How to Gain the Early-Adopter Advantage
The cybersecurity landscape is on the precipice of a significant transformation. As 2026 hurtles towards us, Security Operations Centers (SOCs) face an unprecedented challenge: attackers are not just leveraging Artificial Intelligence (AI) for reconnaissance; they’re building entire campaigns around it. This evolution means threat actors now possess tooling that’s faster, more adaptive, and eerily adept at mimicking human behavior – from initial reconnaissance to sophisticated phishing attempts and gaining initial access. For SOC teams, proactive adaptation isn’t just an advantage; it’s a necessity for survival.
The Inevitable Shift: Geopolitical Tensions and Accelerating Technology
The world’s geopolitical climate is becoming increasingly volatile, directly impacting the cyber threat landscape. Nation-state actors and sophisticated cybercriminal groups are constantly refining their tactics, techniques, and procedures (TTPs). Concurrently, technological advancements, particularly in AI and machine learning (ML), are accelerating at a dizzying pace. This confluence of factors creates a perfect storm for SOCs, demanding a fundamental rethink of traditional defense strategies. The reactive “detect and respond” model, while still crucial, is no longer sufficient against adversaries powered by adaptive AI.
AI-Driven Adversaries: Mimicking User Behavior with Uncanny Accuracy
The days of easily identifiable, templated phishing emails are fading. Attackers are now employing AI to craft hyper-personalized and contextually relevant attacks. Imagine phishing emails perfectly tailored to an individual’s job role, recent projects, or even their social media activity. This advanced impersonation extends beyond email to social engineering, malware delivery, and even lateral movement within compromised networks. AI allows threat actors to:
- Automate Reconnaissance: AI can rapidly sift through vast amounts of open-source intelligence (OSINT) to identify vulnerabilities, employee contact information, and organizational structures.
- Generate Convincing Phishing Lures: Natural Language Processing (NLP) models can create grammatically flawless, contextually appropriate, and emotionally manipulative phishing emails, texts, and social media messages.
- Develop Adaptive Malware: AI-powered malware can learn from its environment, evade detection, and adapt its behavior to achieve its objectives, making traditional signature-based defenses less effective.
- Automate Initial Access: From brute-forcing common login combinations to exploiting newly discovered vulnerabilities, AI can accelerate the initial breach process.
The Proactive SOC: Embracing Automation and Augmented Intelligence by 2026
To counter AI-driven threats, SOCs must adopt an offense-informs-defense mindset, leveraging AI and automation themselves. The “early-adopter advantage” for 2026 lies not in replacing human analysts, but in augmenting their capabilities with intelligent systems. This means:
- AI-Powered Threat Intelligence: Moving beyond static threat feeds, SOCs need AI that can analyze emerging TTPs, predict attack vectors, and identify attacker infrastructure with greater speed and accuracy.
- Advanced Analytics and Behavioral Anomaly Detection: Machine learning algorithms can Baselli normal user behavior across endpoints, networks, and applications, flagging deviations that indicate compromise far faster than human analysis alone. This helps detect zero-day exploits or novel attack methods that don’t have existing signatures. For example, anomaly detection could help identify suspicious activity related to a vulnerability like the Log4Shell flaw (CVE-2021-44228: CVE-2021-44228) even before specific exploitation patterns are known.
- Security Orchestration, Automation, and Response (SOAR): Automating mundane tasks like incident triage, data correlation, and initial response actions frees up analysts to focus on complex investigations and strategic threat hunting.
- Proactive Threat Hunting with AI: AI can assist human threat hunters by identifying subtle patterns and weak signals within massive datasets that might otherwise go unnoticed, significantly reducing dwell times.
Remediation Actions for 2026 Readiness
Preparing your SOC for the AI-driven threat landscape of 2026 requires strategic investment and a shift in operational philosophy. Here are key remediation and preparatory actions:
- Invest in AI/ML-Driven Security Tools: Prioritize solutions that offer advanced behavioral analytics, predictive threat intelligence, and automated response capabilities. Look for platforms that integrate seamlessly with your existing security stack.
- Enhance Security Awareness Training: As AI makes phishing and social engineering more sophisticated, human vigilance remains critical. Training must evolve to educate users about highly personalized and context-aware threats.
- Develop Incident Response Playbooks for AI-Driven Attacks: Update and test your incident response plans to account for faster, more adaptive attacks. Focus on automated containment and rapid analysis.
- Embrace a Zero Trust Architecture: Assume breach and segment your network aggressively. Implement strict access controls and continuous verification for all users and devices, minimizing the impact of successful initial access.
- Foster a Culture of Continuous Learning: The threat landscape is dynamic. Encourage your SOC team to continuously learn about new AI-powered attack techniques and defensive strategies.
- Practice Proactive Threat Hunting: Move beyond reactive defense. Utilize threat intelligence and AI-powered insights to actively search for compromises within your environment before they escalate.
Key Takeaways for Future-Proofing Your SOC
The cybersecurity battlefield is changing, with AI emerging as a powerful weapon for both defenders and attackers. By 2026, SOCs that embrace AI and automation will gain a significant early-adopter advantage, transforming from reactive guardians into proactive threat hunters. The key lies in augmenting human intelligence with machine capabilities, fostering a resilient security posture, and continuously adapting to the evolving tactics of adversarial AI. Prepare now, and position your organization to thrive in the new era of cyber warfare.





