Windows 11 And Server 2025 Will Start Caching Plaintext Credentials By Enabling WDigest Authentication
The Resurgence of WDigest: A Critical Look at Plaintext Credential Caching in Windows 11 and Server 2025
The cybersecurity landscape is a relentless tug-of-war between innovation and vulnerability. Even as operating systems advance, legacy configurations can introduce unexpected risks. A critical finding highlighted by Horizon Secure reveals a concerning potential exposure in upcoming Windows versions: the re-emergence of WDigest authentication’s ability to cache plaintext passwords in memory when enabled. This isn’t just a theoretical vulnerability; it’s a direct pathway for credential theft that organizations must understand and mitigate.
While WDigest was disabled by default since Windows 10 version 1703 specifically to prevent this very issue, its potential re-enablement in Windows 11 and Windows Server 2025—whether intentionally or inadvertently through misconfiguration—poses a significant threat. For IT professionals, security analysts, and developers, understanding the implications and implementing robust remediation strategies is paramount to safeguarding sensitive user credentials.
Understanding WDigest Authentication
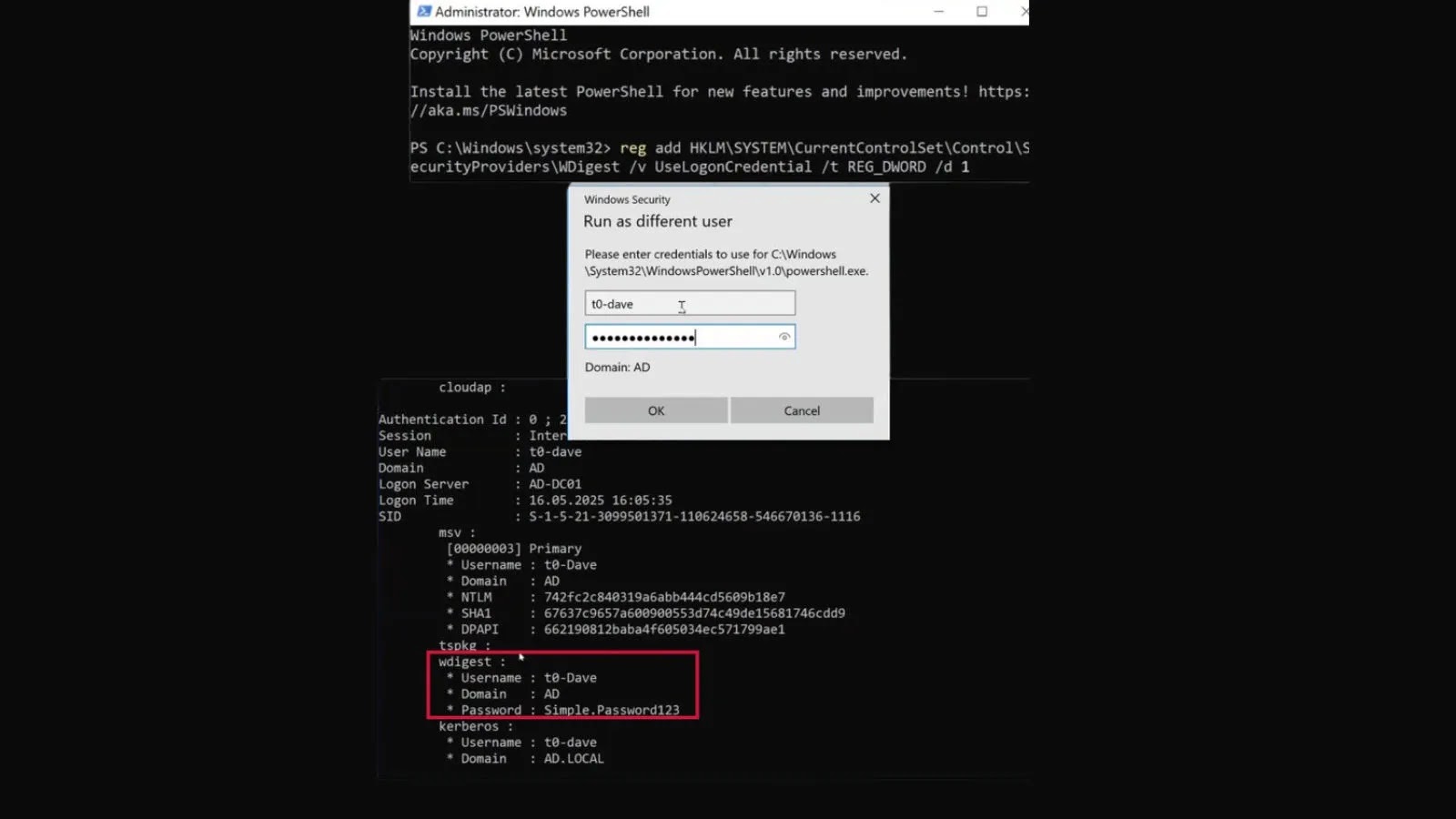
WDigest, or Windows Digest, is an authentication protocol designed to provide HTTP digest authentication services. When active and configured to do so, it can store a user’s plaintext password in the Local Security Authority (LSA) process memory. This in-memory storage is a goldmine for attackers who manage to achieve local system privileges, as tools like Mimikatz can easily extract these credentials.
For years, the cybersecurity community has advocated for the deprecation and disabling of WDigest due to this inherent risk. Microsoft responded by disabling it by default in modern Windows versions. However, administrative actions or third-party applications can still explicitly re-enable WDigest, inadvertently resurrecting a major security loophole.
The Threat: Plaintext Passwords in Memory
The primary danger lies in the caching of plaintext passwords. When a user authenticates via WDigest, their password is processed and stored in an unencrypted format within the LSA process. An attacker who gains administrative access to a compromised system can leverage various post-exploitation tools to dump the contents of the LSA process. If WDigest is active, these tools can readily extract the plaintext passwords of any user who has authenticated via WDigest since the system started or since their last authentication.
This bypasses many modern security controls that rely on hashed or encrypted password storage, as the “keys to the kingdom” are available in cleartext. The impact can be severe, leading to lateral movement within a network, privilege escalation, and full compromise of an organization’s resources.
Remediation Actions: Securing Your Environment
Addressing the WDigest vulnerability requires a proactive and multi-layered approach. Organizations must assume that WDigest could be re-enabled and implement continuous monitoring and enforcement.
- Verify WDigest Status: Regularly check the status of WDigest authentication on all Windows 11 and Windows Server 2025 systems. This can be done by examining the registry key
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest. The value forUseLogonCredentialshould be0or completely absent, indicating WDigest is disabled. - Implement Group Policy Objects (GPOs): Enforce WDigest disabling across your entire domain using Group Policy. Create a GPO that sets
UseLogonCredentialto0and link it to the appropriate OUs. - Monitor Registry Changes: Configure security information and event management (SIEM) systems to alert on changes to the WDigest registry key. Unusual modifications could indicate malicious activity or misconfiguration.
- Restrict Administrative Privileges: Adhere to the principle of least privilege. Reducing the number of users with administrative access limits the potential for an attacker to exploit this vulnerability.
- Advanced Credential Protection: Implement Windows Defender Credential Guard (available on Windows 10/11 Enterprise and Server 2016+). Credential Guard uses virtualization-based security to isolate and protect LSA secrets, significantly complicating the extraction of credentials even with administrative access.
- Behavioral Monitoring: Deploy endpoint detection and response (EDR) solutions that can detect and prevent credential dumping techniques, regardless of the underlying authentication mechanism.
Tools for Detection and Mitigation
Several tools can assist in detecting WDigest re-enablement and mitigating the associated risks.
| Tool Name | Purpose | Link |
|---|---|---|
| Group Policy Management Console (GPMC) | Centralized management of GPOs to disable WDigest across domains. | Microsoft GPMC |
| Sysmon | Advanced monitoring of system activity, including registry changes. Rule out specific registry modifications related to WDigest can be created. | Microsoft Sysmon |
| Mimikatz (Detection/Testing) | While an adversarial tool, Mimikatz can be used by security teams to test for plaintext credential exposure on systems where WDigest is suspected to be enabled. (Use with extreme caution in test environments only.) | GitHub: Mimikatz |
| Windows Defender Credential Guard | Built-in Windows feature to protect LSA secrets. | Microsoft Credential Guard |
Conclusion: Stay Vigilant Against Legacy Threats
The potential for Windows 11 and Windows Server 2025 to cache plaintext credentials via an re-enabled WDigest authentication is a stark reminder that even advanced operating systems can harbor vulnerabilities stemming from historical configurations. Organizations must remain vigilant, actively verifying the status of WDigest, enforcing its disabled state through robust Group Policies, and leveraging advanced security features like Credential Guard. Proactive posture management and continuous monitoring are essential to prevent credential theft and protect your digital assets from this persistent threat.





