Windows User Account Control Bypassed Using Character Editor to Escalate Privileges
Unmasking the UAC Bypass: Private Character Editor Exploited for Privilege Escalation
System administrators and cybersecurity professionals globally are no stranger to the persistent challenge of User Account Control (UAC) in Windows. Designed as a foundational security measure to prevent unauthorized changes to the operating system, UAC’s effectiveness is paramount. Now, a sophisticated new technique has emerged, leveraging an unexpected built-in Windows utility to bypass UAC and achieve privilege escalation without direct user intervention. This revelation has sent ripples through the security community, prompting an urgent re-evaluation of defense strategies.
The Clever Exploit: How EUDCEDIT.EXE Becomes a Weapon
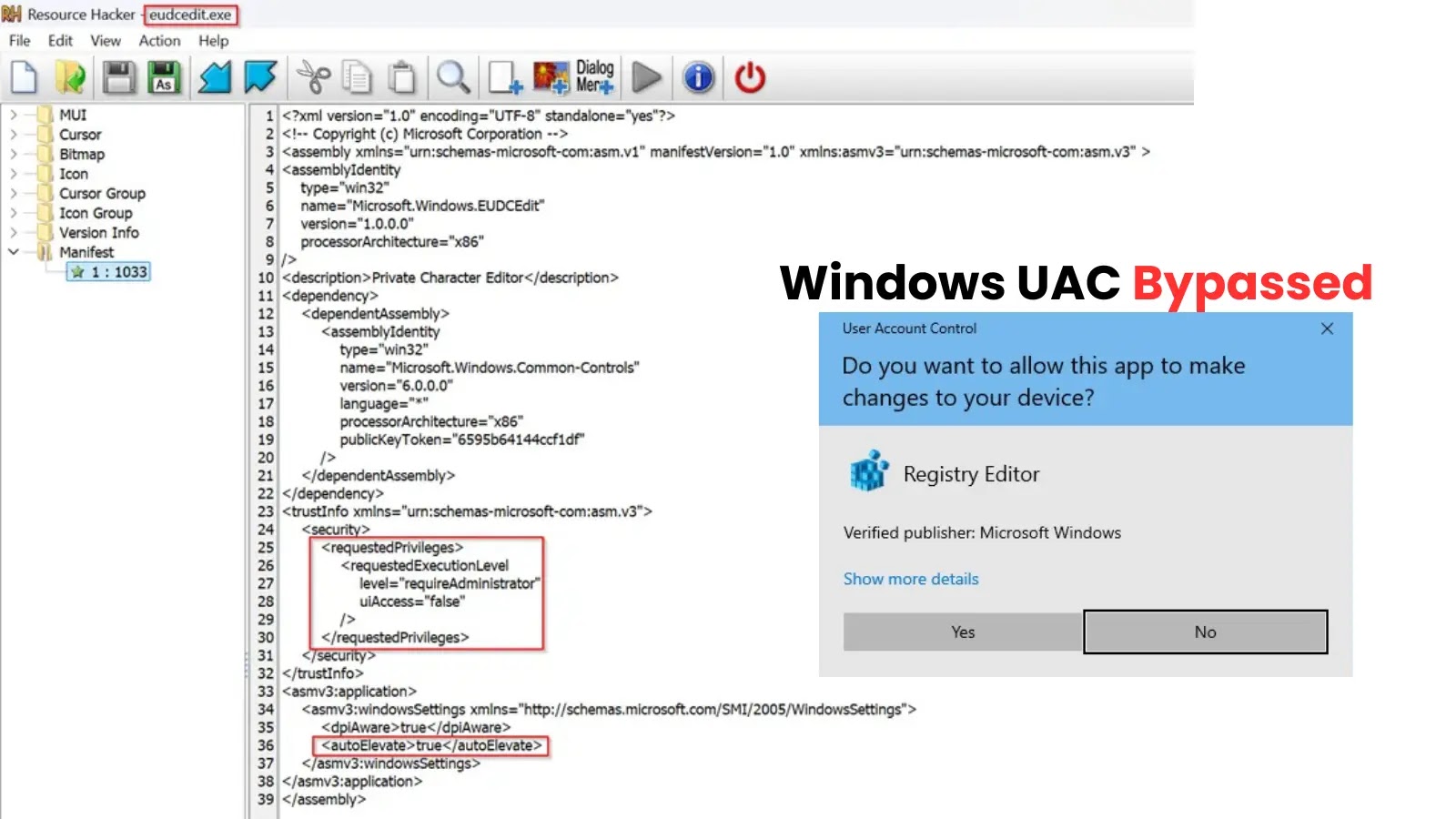
The attack, disclosed by security researcher Matan Bahar, targets Microsoft’s own Private Character Editor, eudcedit.exe, located within C:\Windows\System32. This seemingly innocuous tool, originally intended to allow users to create and modify custom characters for specialized fonts, possesses a critical vulnerability. Bahar’s technique exploits the predictable behavior of this executable to trick Windows into running malicious code with elevated privileges.
Here’s a simplified breakdown of the attack vector:
- The Private Character Editor, when executed, attempts to load a specific font file.
- By manipulating the environment or specific file paths, an attacker can force
eudcedit.exeto load a malicious DLL instead of its intended legitimate font file. - Crucially, since
eudcedit.exeitself runs with certain elevated permissions – even when UAC is active – Windows then executes the malicious DLL with those same elevated privileges, effectively bypassing UAC.
This method is particularly concerning because it relies on a signed Microsoft executable, making it inherently more difficult for traditional antivirus and endpoint detection and response (EDR) solutions to flag as malicious without sophisticated behavioral analysis.
Understanding the Impact: Why This Matters to You
The successful exploitation of this UAC bypass mechanism carries significant implications:
- Unconstrained Access: An attacker initially operating with standard user privileges can quickly escalate to administrative or root-level access. This grants them the ability to install malware, modify system configurations, exfiltrate sensitive data, or establish persistence.
- Stealthy Execution: Because the attack leverages a legitimate Windows binary, it can be executed with a lower footprint, making detection more challenging. Traditional UAC prompts, which normally alert users to elevated operations, are entirely circumvented.
- Ransomware Implications: The ability to escalate privileges silently provides a prime opportunity for ransomware operators to deploy their payloads with maximum impact, encrypting system files and disabling security software.
- Insider Threats: Malicious insiders could leverage this technique to gain unauthorized access to critical systems, bypassing security controls from within.
Remediation Actions and Proactive Defense
While a specific CVE for this particular technique hasn’t been widely publicized as of the knowledge cutoff, the underlying principles often fall under broader categories of privilege escalation and UAC bypasses. For example, similar vulnerabilities have been tracked under classifications like CVE-2022-26923 related to local privilege escalation or UAC bypass through specific system functionalities.
Addressing this UAC bypass requires a multi-layered approach:
- Patch Management: Ensure all Windows systems are kept up-to-date with the latest security patches. While this specific method may not yet have a direct patch, Microsoft regularly addresses system vulnerabilities that could be indirectly related or provide similar attack surfaces.
- Principle of Least Privilege: Enforce strict adherence to the principle of least privilege. Users should only have the minimum necessary permissions to perform their job functions. This limits the blast radius of any successful privilege escalation.
- Application Whitelisting: Implement application whitelisting solutions (e.g., Windows Defender Application Control, AppLocker) to restrict the execution of unauthorized executables and DLLs. This can prevent the malicious DLL from running even if the UAC bypass is achieved.
- Enhanced Monitoring: Deploy robust endpoint detection and response (EDR) solutions capable of behavioral analysis. Look for anomalous process launches, particularly those involving
eudcedit.exein unusual contexts or attempts by non-privileged accounts to interact with system binaries in an unexpected manner. Monitor for the creation or modification of files in system-critical directories by non-system processes. - User Education: While this attack doesn’t rely on user interaction, educating users about phishing, social engineering, and the importance of reporting suspicious activity remains a critical defense layer. An initial compromise often precedes privilege escalation.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify weaknesses in your current security posture, including potential UAC bypass vectors.
Tools for Detection and Mitigation
Leveraging the right tools is crucial for identifying and mitigating threats like the EUDCEDIT bypass.
| Tool Name | Purpose | Link |
|---|---|---|
| Sysmon | Advanced monitoring of system activity, process creation, network connections, and file access. Custom rules can detect suspicious eudcedit.exe behavior. |
https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon |
| Windows Defender Application Control (WDAC) | Application whitelisting and code integrity policies to control what applications can run on a system. | https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/wdac-design-guide |
| EDR Solutions (e.g., CrowdStrike Falcon, SentinelOne) | Behavioral analysis, threat hunting, and automated response capabilities to detect and block sophisticated attacks. | (Vendor-specific links – e.g., https://www.crowdstrike.com/) |
| AppLocker | Policy-based control over which applications can run, providing a level of application whitelisting. | https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/applocker/applocker-overview |
Conclusion: Stay Vigilant, Stay Secure
The discovery of this UAC bypass technique using the Private Character Editor underscores a critical reality in cybersecurity: attackers will continually innovate, finding new and unexpected ways to exploit legitimate system functionalities. For cybersecurity professionals and system administrators, this serves as a stark reminder that even seemingly benign built-in tools can become attack vectors. Proactive defense, stringent security hygiene, and continuous monitoring are not just recommendations; they are imperatives in the ongoing battle against evolving threats. By understanding these new attack surface, organizations can fortify their defenses and maintain a robust security posture against privilege escalation attempts.





