Cybersecurity Implications of STP Misconfigurations.
Cybersecurity Implications of STP Security Misconfigurations and Vulnerability Protocol
In today’s complex network environments, the Spanning Tree Protocol (STP) plays a crucial role in maintaining network stability. However, STP security misconfigurations within STP can introduce significant security risks. This article delves into the cybersecurity implications of STP security misconfigurations and vulnerability protocol. The report highlights the importance of regular security audits in maintaining a strong security posture. common security misconfigurations, potential vulnerabilities, and essential security measures to mitigate these risks. Our goal is to provide a comprehensive understanding of how to implement security patches and updates. configure and protect your network from potential security threats arising from STP misconfiguration vulnerabilities.
Understanding STP and Its Importance
What is Spanning Tree Protocol (STP)?
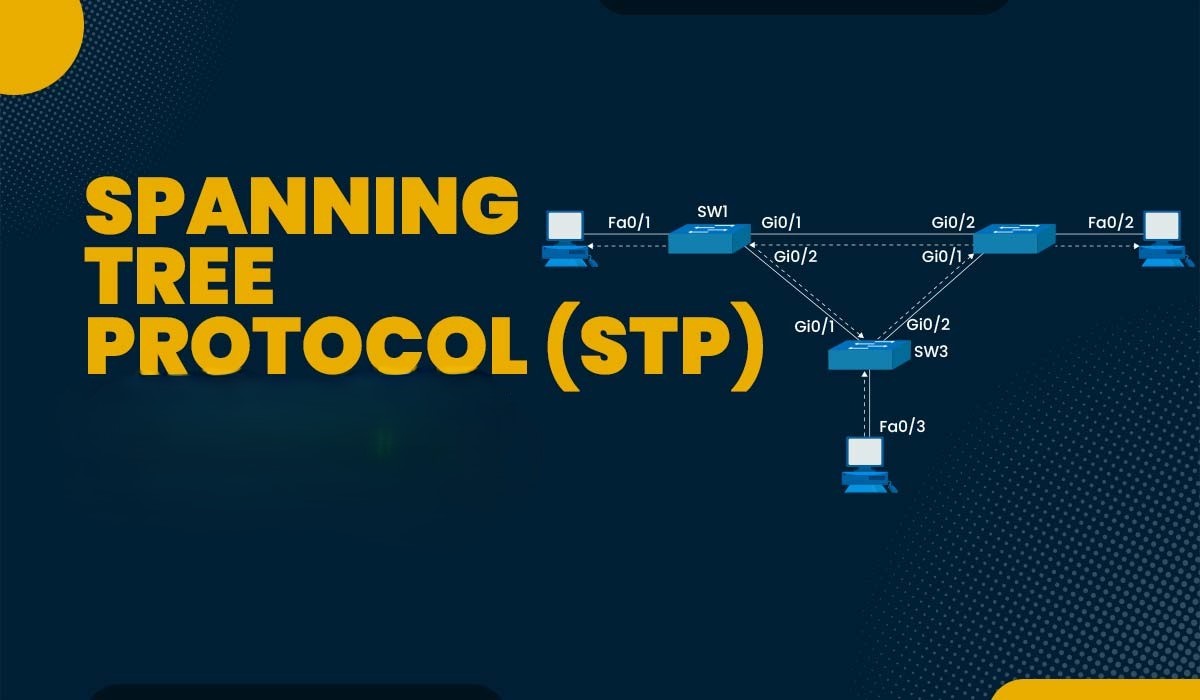
Spanning Tree Protocol (STP) is a network protocol designed to prevent loops in network topologies. By logically blocking redundant paths, STP ensures that there is only one active path between any two network devices. This protocol operates by exchanging bridge protocol data units (BPDUs) to identify and disable redundant links, thereby preventing broadcast storms and ensuring network stability. Properly configured STP is essential for maintaining a healthy and efficient network environment, but A misconfiguration can lead to security vulnerabilities that make systems vulnerable to attacks..
Role of STP in Network Configuration
The role of STP in network configuration is pivotal in ensuring network security and stability. By managing and preventing loops, STP ensures that network traffic flows efficiently without causing congestion or downtime. Accurate STP configuration is also vital for maintaining access control and preventing unauthorized access to sensitive data. When STP is configured correctly, it enhances the overall security posture of the network. Conversely, security misconfigurations in STP can be exploited by an attacker to gain access to the network.
Common Security Misconfigurations in STP
Common security misconfigurations in STP can create significant security threats. These misconfiguration vulnerabilities often arise from human error, such as failing to properly set security settings or neglecting to implement adequate security controls. Security misconfiguration examples include:
- Leaving default configuration values unchanged
- Failing to disable unnecessary ports
- Not implementing proper authentication mechanisms
These misconfigurations can allow an attacker to manipulate STP, potentially leading to a man-in-the-middle attack, unauthorized access control, or even a data breach of sensitive information. We at Teamwin Global Technologica recommend you audit your systems regularly to prevent security misconfiguration.
Types of Security Misconfigurations
Common Security Misconfiguration Examples
Security misconfiguration examples are plentiful and can range from simple oversights to complex errors in security configurations. Common security misconfigurations often involve leaving default passwords unchanged, failing to apply necessary security patches, or not properly configuring firewall rules. These misconfigurations can create security vulnerabilities that attackers can easily exploit to gain access to sensitive information. As Teamwin Global Technologica, we advise you to regularly audit all security settings and security controls to prevent security misconfiguration and maintain a strong security posture. Addressing these misconfiguration vulnerabilities promptly is essential for reducing security risk and protecting against potential security breaches.
Impact of Security Misconfigurations on Network Devices
The impact of security misconfigurations on network devices can be severe, leading to security breaches and unauthorized access. When security features are not properly configured, network devices become susceptible to STP attacks. An attacker can exploit these vulnerabilities to gain access, disrupt services, or steal sensitive data. Unpatched misconfigurations can also lead to ransomware attacks, causing significant financial and operational damage. We at Teamwin Global Technologica emphasize that implementing robust security policies and conducting regular Conducting regular security testing is a key component of our security solutions. Regular security audits are crucial steps in mitigating the risk of unauthorized access. impact of security misconfigurations on network infrastructure.
Types of Security Vulnerabilities Associated with STP
Several types of security vulnerabilities are associated with STP, each posing a unique security risk to the network. These vulnerabilities can arise from different attack vectors, including:
- The ability of an attacker to manipulate bridge protocol data units (BPDUs) to influence STP topology, leading to a man-in-the-middle attack or unauthorized access.
- Failure to implement proper authentication mechanisms, which can allow unauthorized network devices to inject malicious BPDUs, disrupting network operations.
Regularly auditing security configurations and deploying security measures to mitigate these misconfiguration vulnerabilities are essential steps to strengthen network security and prevent security misconfiguration. Identifying and addressing these known vulnerabilities should be a top priority to mitigate potential security incidents.
Exploring STP Attacks
Common STP Attack Vectors
Common STP attack vectors often involve attackers exploiting security vulnerabilities within the Spanning Tree Protocol. One prevalent method is the use of web applications that are designed with security in mind. bridge protocol data unit (BPDU) attack, where a malicious network device injects bridge protocol data units with manipulated parameters to influence the STP The network topology must be designed with cloud security principles in mind. By claiming to be the root bridge, an attacker can redirect network traffic through their compromised device, facilitating a man-in-the-middle attack Security patches and updates are essential to prevent systems from becoming vulnerable to attacks. unauthorized access. Properly configured security controls, such as BPDU guard and root guard, are essential security measures to mitigate such potential security threats. Teamwin Global Technologica recommends that you implement security policies to prevent security misconfiguration.
How Attackers Exploit Misconfigurations
Attackers often exploit misconfigurations by identifying and leveraging security vulnerabilities in STP implementations. Security misconfiguration examples include failing to enable BPDU guard on ports connected to end-user devices, allowing unauthorized devices to inject malicious BPDUs and disrupt the network security. Additionally, default configuration settings and weak authentication mechanisms can be easily bypassed. By gaining access to these vulnerable network devices, attackers can manipulate STP behavior, redirecting traffic and intercepting sensitive information. Regular auditing and implementing security best practices are crucial to address these misconfiguration vulnerabilities. We at Teamwin Global Technologica can help troubleshoot these security threats.
Real-World Examples of STP Attacks
Real-world examples of STP attacks highlight the impact of security misconfigurations and vulnerabilities. In one instance, an attacker successfully launched a man-in-the-middle attack by injecting malicious BPDUs into a poorly configured network, allowing them to intercept sensitive data transmitted between users and servers. In another case, a rogue network device exploited unauthorized access to a port to become the root bridge, disrupting network connectivity and leading to a significant data breach. These incidents underscore the need for robust security configurations, continuous monitoring, and prompt response to potential threats to mitigate these security threats. Teamwin Global Technologica emphasizes implementing real-time monitoring and critical security to prevent security misconfiguration.
Mitigating STP Security Misconfigurations
Best Practices to Prevent Security Misconfigurations
To prevent security misconfiguration, implementing security best practices is crucial. Regularly audit all security settings and security controls to identify and rectify any misconfiguration vulnerabilities. Specifically, consider implementing safeguards such as:
- Enable BPDU guard on all ports connected to end-user devices to disable unauthorized devices from injecting malicious bridge protocol data units.
- Configure root guard on designated root ports to prevent Preventing unauthorized devices from becoming the root cause of security breaches is essential. bridge.
These proactive security measures significantly enhance network security and mitigate potential security threats. We at Teamwin Global Technologica emphasize proactive critical security in preventing any security breaches.
Tools and Techniques to Troubleshoot STP Configuration
Effective troubleshooting of STP configuration requires utilizing specialized tools and techniques. Network administrators can use command-line interface (CLI) commands to examine STP status, port roles, and bridge protocol data units exchanges. Packet capture tools can analyze network traffic to identify anomalies or malicious BPDUs injected by an attacker. Regular security testing, including penetration testing, can help identify security vulnerabilities and misconfiguration vulnerabilities in the STP configuration. Teamwin Global Technologica recommends using these tools to ensure real-time monitoring and quick resolution of security issues that may arise from the spanning tree protocol.
Implementing Access Control to Enhance Security
Implementing robust access control mechanisms is essential for enhancing network security. Restricting unauthorized access to network devices and configuration settings can mitigate Understanding the risk of data security breaches is vital for effective information security. security misconfigurations. Employ strong authentication methods, such as multi-factor authentication, to verify the identity of users before granting access control. Regularly review and update access control lists to ensure that only authorized personnel have the necessary permissions to configure STP Security solutions and other protective measures are necessary for comprehensive data security. security settings. Proper access control can significantly reduce the likelihood of human error and malicious activity, bolstering the overall security posture. As Teamwin Global Technologica, we implement proactive security measures for you to mitigate these security threats.
The Impact of Security Misconfigurations
Understanding the Security Risks Involved
Understanding the security risks involved with STP security misconfigurations is vital for maintaining a secure network environment. Common security misconfigurations can lead to security breaches, allowing an attacker to exploit security vulnerabilities and gain access to sensitive information. Unauthorized manipulation of STP can result in man-in-the-middle attacks, data breaches, and denial-of-service (DoS) attacks, disrupting network operations and compromising sensitive data. Teamwin Global Technologica emphasizes that a thorough understanding of these security threats is the first step toward implementing effective security measures to mitigate the impact of security misconfigurations.
Long-Term Effects of Vulnerability Protocols
The long-term effects of vulnerability protocols. We must focus on vulnerabilities, particularly those related to cloud security. STP, can have lasting consequences on network security and stability. Unaddressed security vulnerabilities can accumulate over time, creating a greater security risk of security incidents and data breaches. Network devices with security misconfigurations may become increasingly susceptible to STP attacks, leading to prolonged downtime and financial losses. Regular updates and security patches are essential to address known vulnerabilities and maintain a strong security posture. We at Teamwin Global Technologica can conduct routine security testing to make sure your configuration is correct.
Strategies to Mitigate the Impact of Security Vulnerabilities
Implementing effective strategies to mitigate the impact of security vulnerabilities is crucial for maintaining network security. Regularly audit security configurations to identify and address misconfiguration vulnerabilities. Deploy intrusion detection and prevention systems (IDPS) to monitor network traffic for malicious activity and automatically respond to security threats. Implement real-time monitoring to detect and respond to potential security incidents. Configure firewall rules to restrict unauthorized access to sensitive ports and services. By implementing a multi-layered approach to security, organizations can effectively mitigate the impact of security incidents and prevent security misconfiguration. Teamwin Global Technologica is dedicated to helping you gain access to the best security measures.
What are the common types of security misconfigurations in STP?
Common types of security misconfigurations in Spanning Tree Protocol (STP) include improper VLAN configurations, incorrect bridge priority settings, and lack of port security. These misconfigurations can lead to network vulnerabilities, allowing attackers to exploit weaknesses and gain unauthorized access to sensitive data.
How can security professionals mitigate STP misconfiguration vulnerabilities?
Security professionals can mitigate STP misconfiguration vulnerabilities by implementing best practices such as regularly auditing network device configurations, setting up proper access control measures, and using security scanners to detect potential security misconfigurations. Additionally, they should ensure that the STP process is correctly configured to prevent network loops and denial-of-service attacks.
What impact do STP misconfigurations have on network security?
STP misconfigurations can have severe security impacts, including increased exposure to denial-of-service attacks, unauthorized access, and data breaches. A lack of security in STP configurations can lead to network instability and performance issues, compromising the overall integrity of the network.
What are some examples of security misconfiguration issues related to STP?
Examples of security misconfiguration issues related to STP include using default configurations that leave ports open, misconfiguring rapid STP settings that can allow loop creation, and failing to implement filtering rules that manage traffic effectively. These issues can create security vulnerabilities that attackers can exploit.
How can organizations prevent security misconfigurations in STP?
Organizations can prevent security misconfigurations in STP by adopting appropriate security practices, such as training staff on STP configuration, regularly reviewing and updating network policies, and utilizing security information and event management (SIEM) tools to monitor for anomalies. Implementing a robust change management process can also help address security misconfigurations before they are exploited.
What tools can be used to identify security vulnerabilities in STP?
Security tools such as security scanners and network monitoring software can be employed to identify security vulnerabilities in STP configurations. These tools analyze network traffic and configurations, helping to pinpoint misconfigurations and potential security weaknesses that need to be addressed.
What is the role of access control in preventing STP misconfigurations?
Access control plays a critical role in preventing STP misconfigurations by ensuring that only authorized personnel can make changes to network device configurations. By implementing strict access controls, organizations can reduce the risk of accidental or malicious modifications that could lead to security vulnerabilities.
How does the lack of security in STP configurations lead to vulnerabilities?
The lack of security in STP configurations can lead to vulnerabilities by allowing unauthorized changes or access to network devices. Without proper security measures in place, attackers can exploit these weaknesses, potentially causing network disruptions or compromising sensitive data.
What are the latest security practices for configuring STP?
The latest security practices for configuring STP include enabling features like BPDU guard, root guard, and port security to enhance the security of STP operations. Regular updates to firmware and patches, as well as continuous monitoring of STP configurations, are also essential to maintaining a secure network environment.






