Cybersecurity in Automotive Manufacturing: Lessons from JLR.
Cyber in JLR Cyber attack: Automotive Manufacturing Cybersecurity Lessons from Learned Jaguar Land Rover
In an era where the automotive sector increasingly relies on digital infrastructures, the Cyber JLR Cyberattack serves as a cautionary tale of the vulnerabilities that can arise within complex supply chains. This incident underscores the critical importance of fortifying cybersecurity measures to protect automotive operations from potential cyber threats. As automotive giants like Jaguar Land Rover (JLR) integrate advanced technologies into manufacturing operations, the need for a robust security posture becomes paramount. This article delves into the specifics of the cyber incident, analyzing the immediate impacts and the response measures undertaken. It aims to provide valuable insights into how companies can bolster their defenses against such disruptive forces, ensuring both operational resilience and customer trust.
Overview of the Cyber JLR Cyberattack
What Happened During the Attack on JLR
The cyber attack on JLR, a subsidiary of Tata Motors, unfolded as a sophisticated breach that targeted the company’s digital infrastructure, exposing significant vulnerabilities within its supply chain. This cyberattack, attributed to the notorious group Scattered Spider, unveiled the fragility of legacy systems often found in the automotive industry. The attackers exploited these weaknesses, gaining unauthorized access to sensitive data and disrupting key manufacturing operations. As a result, the company faced a severe implications arise from inadequate cyber security measures. data breach, compromising both operational efficiency and customer data integrity. This breach highlighted the urgency for automotive companies to adopt a zero trust architecture to preemptively combat such cyber threats and safeguard essential assets.
Immediate Impact of the Jaguar Land Rover Cyberattack
The immediate impact of the Jaguar Land Rover cyberattack was profoundly felt across the company’s global operations. The cyber incident led to the shutdown of several factories, causing significant downtime and operational and brand damage. This disruption not only affected JLR’s ability to produce vehicles but also strained relationships with suppliers, revealing critical supply chain vulnerabilities. The ripple effect of this breach extended beyond production delays, as the company portals faced potential compromise, threatening the security of customer data and cloud services. Consequently, this event served as a wake-up call for the automotive industry, emphasizing the necessity of robust security measures to mitigate the risks posed by sophisticated cyber attacks.
Response Measures Taken by Jaguar Land Rover
In response to the cyberattack, Jaguar Land Rover swiftly enacted a series of defense measures to contain the breach and restore operational continuity. Emphasizing a proactive approach, the company prioritized the implementation of a zero trust cybersecurity framework to enhance its overall security posture. Immediate actions included:
- Reinforcing supply chain defenses and collaborating with cybersecurity experts like Darren Williams and Larry Ponemon to evaluate and fortify existing infrastructures.
- Leveraging cutting-edge technologies such as BlackFog to monitor and neutralize ongoing threats, ensuring that all potential vulnerabilities were addressed.
By adopting a comprehensive suite of cybersecurity solutions, JLR has aimed to safeguard its operations against future cyber incidents, reinforcing trust with its stakeholders.
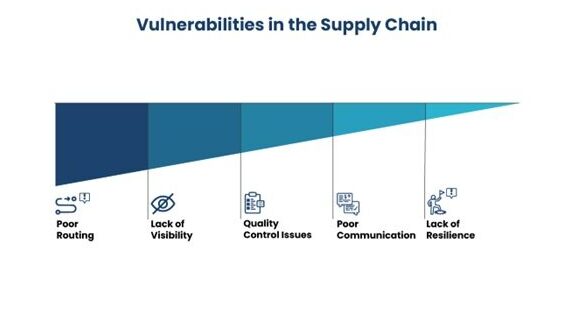
Understanding the Vulnerabilities in the Automotive Supply Chain
Common Supply Chain Vulnerabilities in the Automotive Industry
In the modern automotive industry, supply chain vulnerabilities have emerged as a critical focal point for cybersecurity. With intricate networks connecting various suppliers, manufacturers, and distributors, the automotive sector faces unique challenges in maintaining a robust security posture. These complex supply chains often involve legacy systems that are susceptible to cyber threats, such as data breaches and cyber attacks. The reliance on digital infrastructures increases the risk of disruptions, potentially leading to significant downtime and operational and brand damage. As automotive companies like Jaguar Land Rover (JLR) have experienced, a single vulnerability can cascade through the supply chain, affecting production schedules and customer satisfaction. Safeguarding these intricate networks requires an unwavering commitment to cybersecurity, ensuring resilience against potential breaches.
Lessons from JLR: Identifying Cyber Threats
The cyberattack on JLR serves as a poignant lesson in identifying and mitigating cyber threats within the automotive supply chain. This incident underscored the necessity for companies to adopt a proactive approach in recognizing potential vulnerabilities before they escalate into full-fledged breaches. Through the analysis of the JLR cyberattack, it becomes evident that understanding the tactics employed by groups like Scattered Spider is crucial. By doing so, automotive companies can anticipate similar cyber incidents and implement zero trust architecture to fortify their defenses. Learning from such events empowers organizations to enhance their cybersecurity measures, ensuring that their supply chains remain resilient and their operations secure against future threats.
Proactive Measures for Supply Chain Security
To safeguard the automotive supply chain against cyber threats, adopting proactive measures is paramount. Companies must prioritize the integration of comprehensive cybersecurity frameworks, such as zero trust, to build a defense-in-depth strategy. This approach involves several key actions:
- Continuous monitoring for unusual activities across the network
- Employing advanced tools like BlackFog to neutralize potential threats
Collaboration with cybersecurity experts, such as Darren Williams and Larry Ponemon, can provide invaluable insights into emerging threats and effective response strategies. By fortifying their digital infrastructures, automotive companies can mitigate the risk of disruptions and ensure the integrity of their operations. Proactive investment in cybersecurity not only protects against immediate threats but also builds long-term resilience and trust with stakeholders.
Implementing Cybersecurity Strategies: A Wake-Up Call
The Importance of Zero Trust Architecture
In the realm of automotive cybersecurity, the adoption of a zero trust architecture stands as a pivotal defense against cyber incidents. This strategy, which fundamentally operates on the principle of “never trust, always verify,” is integral to shielding complex supply chains from potential breaches. By ensuring that every access request is authenticated and authorized, this architecture minimizes vulnerabilities, particularly in legacy systems that are prevalent in the automotive sector. Companies like Jaguar Land Rover have recognized the necessity of this approach, implementing it to fortify their operations against sophisticated cyber threats. Zero trust not only enhances the security posture of an organization but also builds a resilient framework that anticipates and mitigates risks before they escalate, safeguarding both operational efficiency and customer data integrity.
Building Resilience Against Cyber Incidents
For companies within the automotive industry, building resilience against cyber incidents is not merely a strategic option but a necessity. As demonstrated by the cyberattack on JLR, disruptions can lead to significant downtime and operational damage, with far-reaching impacts on brand reputation and supplier relationships. Companies must proactively invest in robust security measures to protect their manufacturing operations and supply chains. This involves continuous monitoring of cloud services and company portals to detect and neutralize threats promptly. By cultivating a culture of cybersecurity awareness and engaging with experts like Darren Williams and Larry Ponemon, organizations can enhance their defenses. Such resilience ensures that businesses remain operationally secure and maintain customer trust, even amidst evolving cyber threats.
Defense Strategies Against Cyberattacks
In an era where cyberattacks are increasingly sophisticated, implementing effective defense strategies is crucial for safeguarding the automotive sector. A comprehensive approach involves several key components:
- Reinforcing existing cybersecurity frameworks and leveraging cutting-edge technologies such as BlackFog to monitor and respond to threats in real-time.
- Collaborating with cybersecurity leaders to gain invaluable insights into emerging cyber threats and strategic responses.
As evidenced by the Jaguar Land Rover cyberattack, proactive measures are essential to prevent disruptions that could lead to factory shutdowns and data breaches. By fortifying their cyber defenses, automotive companies can protect their supply chain infrastructures, ensuring operational continuity and customer satisfaction. Ultimately, a resilient cybersecurity strategy empowers organizations to anticipate and counteract threats, preserving their integrity and reputation in the industry.
Long-Term Implications for Automotive Cybersecurity
How the JLR Cyberattack Affects Future Cybersecurity Policies
The Jaguar Land Rover cyberattack serves as a critical wake-up call for the automotive sector, highlighting the urgent need to reassess and bolster cybersecurity policies. As the industry continues to integrate advanced technologies, the vulnerabilities exposed by the JLR incident underscore the necessity for a robust security posture. Companies are now compelled to adopt zero trust architectures as a foundational policy, ensuring that all access points within their networks are meticulously verified. By learning from the JLR breach, automotive manufacturers can preemptively address potential vulnerabilities, safeguarding their operations against future disruptions. This proactive approach not only fortifies individual businesses but also reinforces the overall resilience of the automotive industry, fostering a secure and reliable environment for innovation and growth.
Adapting to Evolving Cyber Threats in the Automotive Sector
As cyber threats continue to evolve, the automotive sector must remain vigilant and adaptive to protect against potential attacks. The JLR cyberattack exemplifies the dynamic nature of these threats, necessitating ongoing updates to cybersecurity measures. Companies like Jaguar Land Rover must invest in cutting-edge technologies such as BlackFog and continuously monitor their digital infrastructures for anomalies. This vigilance extends to understanding the tactics of cyber threat actors like Scattered Spider and anticipating their next moves. By fostering a culture of cybersecurity awareness and engaging in continuous education, automotive manufacturers can ensure their defenses remain one step ahead. Adaptation is key to maintaining operational integrity and customer trust in an increasingly digital landscape.
The Role of Industry Collaboration in Enhancing Cyber Resilience
In the face of sophisticated cyber threats, industry collaboration emerges as a crucial strategy for enhancing cyber resilience within the automotive sector. The JLR cyberattack illustrates the interconnected nature of supply chains and the shared vulnerabilities that exist across the industry. By fostering collaboration among manufacturers, suppliers, and cybersecurity experts, the automotive industry can develop unified defense strategies. Engaging with thought leaders like Darren Williams and Larry Ponemon provides access to invaluable insights and innovative solutions. Collaborative efforts not only bolster individual company defenses but also contribute to a more secure industry ecosystem. Through shared knowledge and resources, the automotive sector can build a resilient front against cyber threats, ensuring the safety and reliability of its operations.
5 Surprising Facts About Cybersecurity in Automotive Manufacturing: Lessons from JLR
- 1. JLR faced over 50,000 attempted cyber attacks in a single year, highlighting the scale of threats in the automotive industry.
- 2. The integration of IoT devices in vehicles has increased vulnerability, with JLR implementing advanced encryption to protect data.
- 3. JLR has invested heavily in employee training programs, revealing that human error accounts for a significant portion of security breaches.
- 4. The company collaborates with cybersecurity firms to conduct regular penetration testing, ensuring that their systems are resilient against evolving threats.
- 5. Lessons learned from JLR’s experiences are being shared across the industry, influencing the development of new cybersecurity standards for automotive manufacturing.
What are the main lessons from the Jaguar Land Rover cyberattack?
The Jaguar Land Rover cyberattack serves as a wake-up call for the automotive industry, highlighting the need for robust cybersecurity measures. Key lessons include the importance of proactive cybersecurity strategies, addressing vulnerabilities within supply chains, and enhancing the cybersecurity posture of manufacturers operating legacy systems.
How did the JLR breach affect supply chains?
The JLR breach exposed significant supply chain vulnerabilities, affecting not only Jaguar Land Rover’s operations but also its suppliers and partners. This incident underscored the necessity for manufacturers to implement strong supply chain security measures to protect against rising cyber threats.
What role does zero trust architecture play in automotive cybersecurity?
Zero trust architecture is essential in automotive cybersecurity as it ensures that all users and devices are continuously authenticated and authorized. This approach helps mitigate risks associated with cyber incidents by eliminating implicit trust and enforcing strict access controls throughout the digital platforms used by manufacturers.
Who are the key figures in Jaguar Land Rover’s cybersecurity initiatives?
Notable figures include Katie Barnett, who has played a crucial role in shaping Jaguar Land Rover’s cybersecurity strategies, and John Kindervag, a thought leader in the zero trust framework. Their contributions help enhance the automotive cybersecurity landscape, especially in light of the challenges posed by cyber threats.
What are the key cybersecurity gaps identified in the automotive sector?
The automotive sector has several key cybersecurity gaps, including inadequate defenses against advanced cyber threats and reliance on outdated technology. Manufacturers, including Jaguar Land Rover, need to address these gaps to improve their resilience against potential cyberattacks.
How can manufacturers ensure the security of their digital platforms?
Manufacturers can ensure the security of their digital platforms by adopting a proactive cybersecurity approach, implementing regular security assessments, and training equipment and support engineers to recognize and respond to cyber threats. This comprehensive strategy helps safeguard sensitive data and vehicle registration information.
What impact did the cyberattack have on Jaguar Land Rover’s operations?
The cyberattack paralyzed Jaguar Land Rover’s operations temporarily, highlighting the critical need for manufacturers to develop a robust defense strategy. The incident prompted a reevaluation of their cybersecurity posture, leading to investments in advanced cyber defense mechanisms to prevent future breaches.
What strategies can automotive manufacturers adopt to improve cybersecurity resilience?
Automotive manufacturers can improve cybersecurity resilience by implementing a multi-layered security approach, investing in robust cybersecurity infrastructures, and fostering a culture of cyber awareness among employees. Collaborating with experts, such as IBM X-Force, can also provide valuable insights into emerging threats and best practices.