Deep Dive Into Intrusion Detection And Prevention Systems (IDS/IPS)
IDS and IPS: Understanding Intrusion Detection and Intrusion Prevention Systems
In today’s digital landscape, securing networks against evolving cyber threats is crucial. Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are vital components of network security, each offering distinct yet complementary approaches to threat detection and prevention. Together, they form a robust defense mechanism for organizations of all sizes.
Introduction to Intrusion Detection and Prevention
What are IDS and IPS?
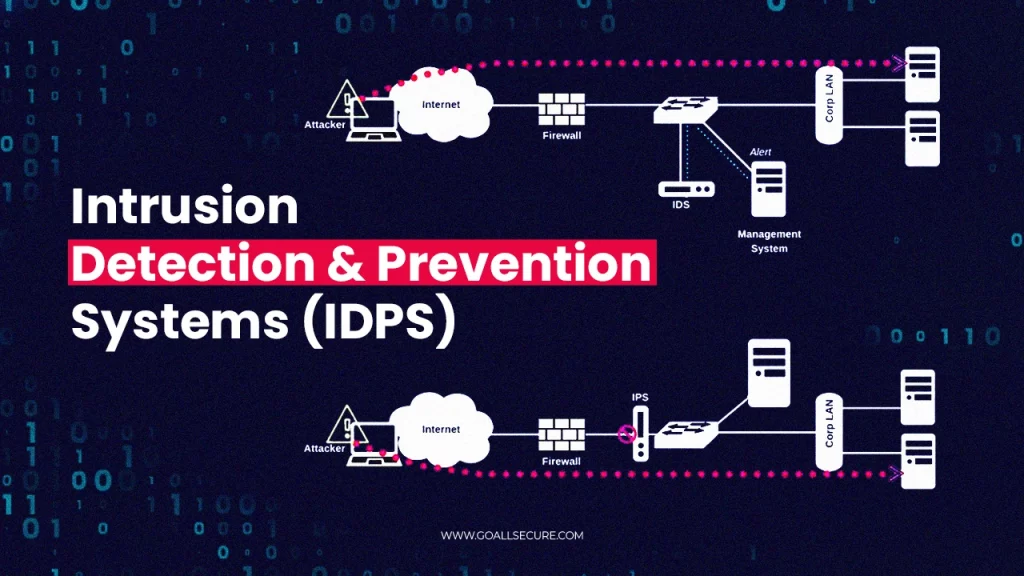
An intrusion detection system (IDS) is a security system that monitors network traffic for malicious activities or security policy violations. When an intrusion is detected, the IDS generates an alert. An intrusion prevention system (IPS), also known as an intrusion detection and prevention system (IDPS), builds upon the capabilities of an IDS by actively responding to detected threats, blocking or preventing them from causing harm. Thus, IDS and IPS enhance overall network security, as these intrusion prevention systems are considered vital for protecting networks to prevent intrusion.
Importance of Intrusion Detection Systems
The importance of an IPS is paramount in safeguarding networks to prevent intrusion from potential threats. intrusion detection systems lies in their ability to detect network intrusions, providing early warning of potential security breaches through advanced IPS functionality. By monitoring network traffic and system activity, IDS can identify malicious activities that might otherwise go unnoticed. This early threat detection allows security teams to respond quickly, mitigating the impact of cyber attacks and preventing further damage to the network and its resources.
Overview of Intrusion Prevention Systems
Intrusion prevention systems (IPS) extend the capabilities of IDS by not only detecting intrusions but also actively preventing them. The network based intrusion prevention system analyzes network traffic and takes automated actions to block or mitigate detected threats. These actions can include terminating malicious network intrusions, blocking access from malicious IP addresses, or quarantining infected systems, thereby enhancing security.
Difference Between IDS and IPS
Key Differences at a Glance
| Feature | IDS | IPS |
|---|---|---|
| Purpose | Detect threats | Detect and block threats |
| Action Taken | Alert only | Alert + Block/Prevent |
| Traffic Flow | Out-of-band | Inline |
| Latency Introduced | Minimal | Can introduce latency |
| Control | Passive monitoring | Active traffic control |
| Risk of False Positives | Alerts admin | Could block legitimate traffic |
Key Differences Explained ( Detection and Intrusion Prevention systems)
The key difference between IDS and IPS lies in their response to detected threats, where IDS monitors and alerts while IPS actively prevents. An IDS functions primarily as a monitoring system, detecting malicious activities and generating alerts for security personnel, acting as one of the essential security tools in cybersecurity, particularly in network-based intrusion detection. In contrast, an IPS actively prevents intrusions by taking automated actions such as blocking suspicious traffic or terminating malicious connections, reinforcing its role as a host intrusion prevention system. This active intervention distinguishes an IPS from the passive monitoring approach of an IDS.
When to Use IDS or IPS
Deciding when to deploy an IDS or IPS depends on an organization’s specific security needs and risk tolerance. An IDS is often suitable for environments where monitoring and analysis are prioritized, allowing security teams to investigate potential threats before taking action. An IPS is preferred when immediate prevention of intrusions is critical, especially in high-risk environments where the potential impact of a successful attack is substantial, making it an intelligent system choice.
Integration of IDS and IPS in Network Security
The effective integration of intrusion detection and prevention systems into a comprehensive network security strategy is essential for robust threat protection. By combining the threat detection capabilities of IDS with the active prevention measures of IPS, organizations can create a multi-layered defense. This layered approach ensures that threats are both identified and neutralized, minimizing the risk of successful cyber attacks.
Types of Intrusion Detection and Prevention Systems
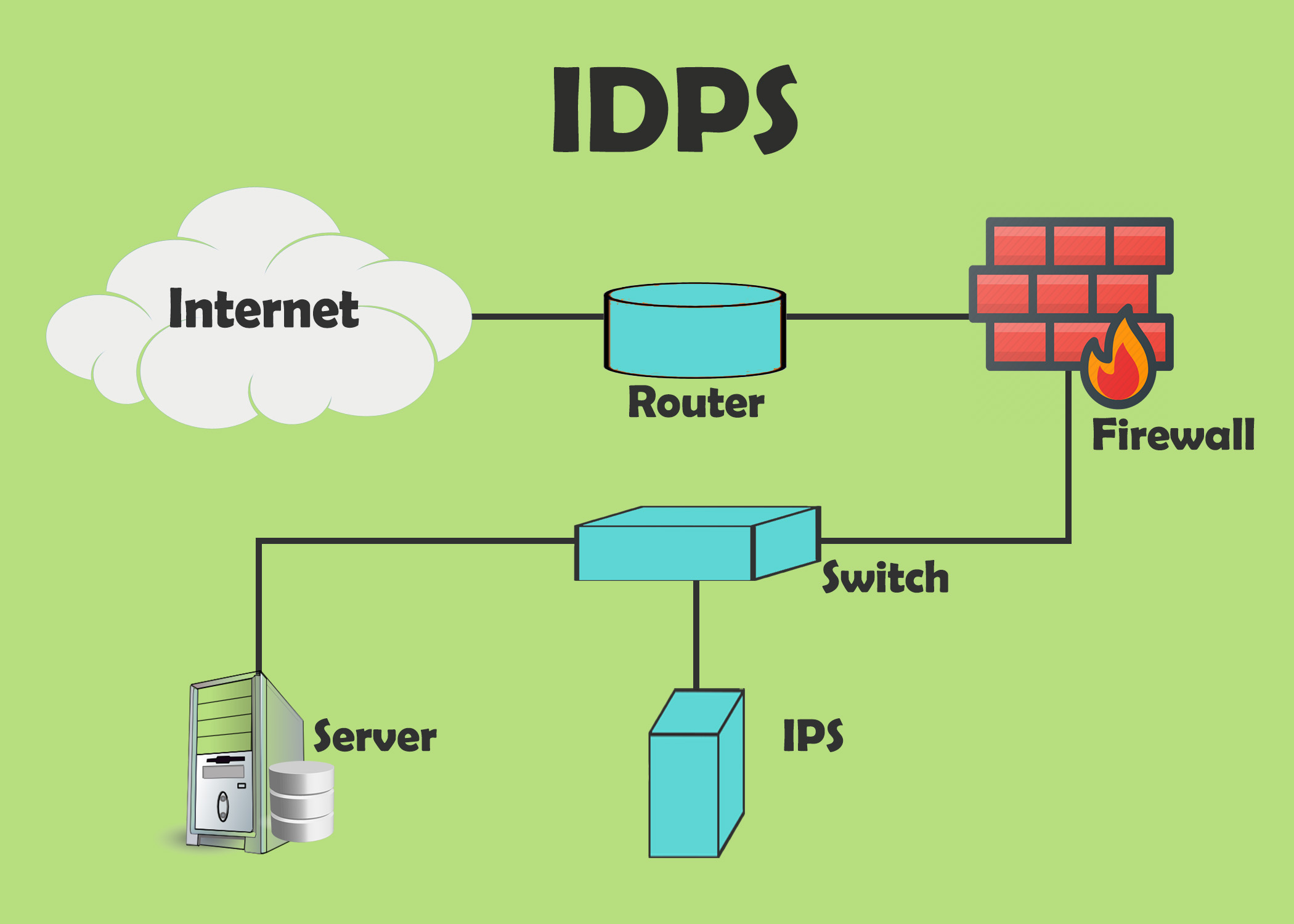
Network Intrusion Detection Systems (NIDS)
Network Intrusion Detection Systems (NIDS) are strategically deployed at key points within the network to analyze network traffic for malicious activities. These systems operate by examining packet headers and payloads, seeking known intrusion signatures or deviations from established security policies through anomaly detection. Anomaly-based detection is used when there is a need to detect zero day threats, which means the signature is unknown. The goal is to detect any malicious cyber activities at the network level, ensuring robust protection through effective security tools like network-based intrusion detection.
Host Intrusion Detection Systems (HIDS)
Host Intrusion Detection Systems (HIDS), conversely, focus on individual hosts within the network, monitoring system logs, file integrity, and processes for suspicious behavior. Host intrusion detection methods provide a granular view of activity on critical servers or workstations, enabling the detection of malicious activities that might bypass network-level defenses. Therefore, HIDS is best at detecting any intrusion on host level by analyzing logs and suspicious behavior, making it a key component of host-based intrusion detection systems.
Network Intrusion Prevention Systems (NIPS)
Network Intrusion Prevention Systems (NIPS) enhance security by actively blocking or mitigating malicious network intrusions in real-time. Sitting inline within the network path, a network intrusion prevention system analyzes network traffic, comparing it against known intrusion signatures and anomaly detection to identify and neutralize threats before they reach their intended targets. NIPS take immediate actions to prevent intrusions, showcasing their critical role in IPS software.
Deep Dive into Intrusion Prevention / Deep understanding of how traffic flows
How IPS Works
An intrusion prevention system (IPS) functions by performing real-time deep packet inspection of network traffic, using signature-based detection and anomaly-based detection to identify malicious activities. When a potential threat is detected, the IPS is designed to immediate action based on pre-configured policies, such as blocking the traffic, terminating the session, or quarantining the affected system. Therefore, the IPS needs to be configured to detect and prevent malicious behavior.
IPS Tools and Technologies
Intrusion Prevention Systems (IPS) are powered by a variety of tools and technologies. These include:
- Signature-based detection engines that match network traffic against known intrusion signatures.
- Anomaly-based detection systems that identify deviations from normal behavior are crucial for effective host-based intrusion detection systems.
Heuristic analysis techniques that detect new or unknown threats, and deep packet inspection capabilities, allowing the IPS to examine the contents of packets and identify malicious payloads, are also crucial.
Common Features of IPS Systems
Intrusion Prevention Systems (IPS) share several common features. The best IPS also allows for customizable security policies, tailoring the system to specific security needs. Keeping the signature database updated is critical for defending against new cyber threats and ensuring continuous management.
| Common IPS Features | Key Considerations for implementing an intelligent system include the integration of IPS and IDS for comprehensive protection. |
|---|---|
|
Signature database updates are essential. |
Threat Detection and Response
Detection Methods Used in IDS and IPS
Here’s how intrusion detection and prevention systems (IDS/IPS) identify malicious activities. They employ several detection methods, including anomaly detection using advanced algorithms.
- Signature-based detection, which matches network traffic against known intrusion signatures.
- Anomaly-based detection, establishing a baseline of normal network behavior and flagging deviations.
Furthermore, heuristic analysis can detect previously unknown malicious cyber threats, enhancing attack detection and prevention strategies. These combined methods help ensure network security.
Alerting Mechanisms for Intrusion Events
When an intrusion is detected, both IDS and IPS generate alerts to notify security personnel. The alerts can range from simple log entries to detailed reports, including information about the intrusion, source IP address, destination IP address, and the security policies violated. Effective alert mechanisms are crucial for timely response, allowing security teams to investigate and mitigate potential cyber threats before they cause significant damage, especially through the use of IDS detects. We want to provide value to detect and remove the potential malicious behaviors with an IPS policies set.
Response Strategies for Detected Threats
The response strategies of intrusion detection systems (IDS) and intrusion prevention systems (IPS) diverge significantly, with IDS detecting while IPS actively prevents threats. An intrusion detection system primarily generates alerts and logs incidents, relying on human analysis and intervention, while an IPS constantly monitors for immediate threats. An intrusion prevention system, however, takes automated actions to block or mitigate threats. These actions can include terminating malicious connections, blocking network traffic from suspicious IP addresses, or quarantining infected systems. Therefore, it is very important to have an intrusion detection and prevention environment.
Future Trends in IDS and IPS Technologies
Emerging Threats and Security Challenges
The evolving cyber threat landscape presents ongoing challenges for intrusion detection and prevention systems (IPS). New malicious activities are constantly emerging, requiring continuous updates to signature-based detection databases and the development of more sophisticated anomaly-based detection algorithms. The rise of encrypted network traffic also poses significant challenges, demanding deep packet inspection and advanced threat detection techniques for effective IPS functionality. We make sure to offer the latest intrusion prevention system solutions that integrate with firewalls and IPS for enhanced security.
Advancements in IPS Engines
Advancements in IPS engines are focusing on enhancing threat detection accuracy, reducing false positives, and improving performance. Machine learning algorithms are increasingly being used in intelligent systems to detect malicious activities and adapt to changing network behavior. Furthermore, deep packet inspection capabilities are being enhanced to analyze encrypted network traffic without compromising privacy. We provide a constant deep dive into latest technology of intrusion prevention system.
Impact of AI and Machine Learning on Intrusion Systems
Machine learning and artificial intelligence (AI) are transforming intrusion detection and prevention systems (IPS), making them more efficient and effective security tools. AI-powered IPS systems can automatically learn normal network behavior, detect anomalies, and predict potential intrusions. Machine learning algorithms can also analyze vast amounts of data to identify subtle patterns and correlations that human analysts might miss, improving threat detection accuracy and reducing response times. We assure you that our network intrusion detection systems are AI-ready and keep learning.
5 Surprising Facts About Intrusion Detection and Prevention Systems (IDS/IPS)
- Many organizations still rely on legacy IDS/IPS solutions, which may not effectively combat modern threats.
- Some IDS/IPS systems can analyze encrypted traffic, providing insights into malicious activities without decrypting the data.
- Machine learning algorithms are increasingly integrated into IDS/IPS to enhance threat detection and reduce false positives, improving the overall efficacy of attack detection and prevention.
- Not all IDS/IPS solutions provide real-time protection; some operate in passive mode, alerting administrators after an intrusion has occurred.
- Hybrid approaches that combine both signature-based and anomaly-based detection are proving to be more effective than traditional methods alone.
What is the difference between an Intrusion Detection System (IDS) and an Intrusion Prevention System (IPS)?
An Intrusion Detection System (IDS) is designed to monitor network traffic and system activities for malicious activity, alerting administrators to potential threats. In contrast, an Intrusion Prevention System (IPS) not only detects but also takes action to prevent these threats by blocking or rejecting malicious traffic based on predefined security policies, serving as a vital prevention service.
How do IPS systems monitor traffic for intrusion attempts?
IPS systems monitor traffic by analyzing data packets in real-time, utilizing algorithms and detection methods to identify patterns that indicate potential intrusions, which is essential for protocol-based intrusion detection. These systems can leverage techniques such as statistical anomaly detection and signature-based detection to differentiate between normal and malicious traffic.
What are the types of intrusion prevention systems available?
There are several types of intrusion prevention systems, including network-based intrusion prevention systems (NIPS), host-based intrusion prevention systems (HIPS), and wireless intrusion prevention systems (WIPS). Each type serves a specific purpose, with NIPS monitoring all traffic across the network, HIPS focusing on individual devices, and WIPS protecting wireless networks, all contributing to a comprehensive approach to intrusion detection.
How do IDS and IPS work together in threat detection?
IDS and IPS work in tandem to enhance threat detection and prevention. An IDS can identify potential threats and alert administrators, while an IPS takes proactive measures to block these threats. By integrating both systems, organizations can create a robust defense strategy that monitors, detects, and mitigates potential intrusions effectively.
What is the role of a next-generation firewall in conjunction with IPS?
A next-generation firewall can complement the functionality of an IPS by providing advanced threat prevention capabilities. These firewalls can inspect traffic at a deeper level, offering additional security layers, such as application awareness and integrated IPS features, to prevent intrusions and maintain network security.
What are some common tools used in intrusion detection and prevention?
Common tools used in intrusion detection and prevention include Snort, Suricata, and Bro/Zeek. These tools can help organizations monitor traffic, analyze system activities for malicious activity, and implement an effective approach to intrusion prevention by identifying and responding to potential threats.
How do IPS solutions handle false positives in detection?
IPS solutions utilize advanced detection models and machine learning techniques to minimize false positives during threat detection, enhancing their effectiveness as security tools. By continuously analyzing traffic patterns and refining their algorithms, these systems can improve their accuracy, ensuring that legitimate traffic is not mistakenly flagged as an intrusion attempt, thereby enhancing IPS functionality.
What is the importance of monitoring system activities for malicious activity?
Monitoring system activities for malicious activity is crucial for maintaining the security and integrity of networks. By employing systems like IDS and IPS, organizations can detect intrusions early, respond to threats in real-time, and ultimately prevent data breaches and other security incidents that could result in significant financial and reputational damage.