How to Secure APIs Against Cyber Attacks
API Security Best Practices: How to Secure APIs and Improve Security Against Cyber Attack
In today’s interconnected digital world, APIs (Application Programming Interfaces) have become the backbone of modern software development, enabling seamless communication and data exchange between various applications and services. However, this increased reliance on APIs has also introduced new and complex security challenges. Securing your APIs is not just a best practice; it’s a necessity to protect sensitive data, maintain user trust, and ensure the overall integrity of your systems. This article delves into API security best practices to help you secure APIs and improve your security posture.
Understanding API Security
API security is a specialized area of application security focused on protecting APIs from various threats and vulnerabilities, including those outlined in the OWASP API Top 10. Unlike traditional web application security, API security addresses the unique characteristics and attack vectors associated with APIs. Understanding API security is crucial because APIs often handle sensitive data and business logic, making them attractive targets for malicious actors. A robust API security strategy involves implementing various security measures to safeguard APIs throughout their lifecycle, from design and development to deployment and maintenance.
Importance of API Security
The importance of API security cannot be overstated, given the pivotal role APIs play in modern applications. APIs are the conduits through which data flows, and if they are not adequately protected, the consequences can be severe. A single vulnerable API can expose an entire system to attacks, leading to data breaches, financial losses, and reputational damage. Implementing API security best practices is essential for maintaining the confidentiality, integrity, and availability of your data and services. Furthermore, strong API security demonstrates a commitment to protecting user data, fostering trust and loyalty against cyber threats.
Common API Security Risks
Several common API security risks, including unique vulnerabilities and security risks, can compromise the integrity and security of your APIs. Injection attacks, such as SQL injection, can occur if API endpoints are not properly validated, allowing attackers to inject malicious code into database queries. Broken authentication and authorization mechanisms can enable unauthorized access to sensitive data and resources. API vulnerabilities, such as cross-site scripting (XSS) and cross-site request forgery (CSRF), can be exploited to compromise user sessions and perform unauthorized actions, highlighting the need for robust API security solutions. A comprehensive API security strategy should address these common API risks through robust security testing and the implementation of appropriate security features, including the use of an API key..
Overview of OWASP API Security Top 10
The OWASP (Open Web Application Security Project) API Security Top 10 is a widely recognized list of the most critical API security risks. It serves as a valuable resource for security teams and developers to understand and mitigate potential vulnerabilities. The OWASP API Security Top 10 includes issues such as broken object-level authorization, broken user authentication, excessive data exposure, lack of resources and rate limiting, and security misconfiguration. By understanding and addressing these top 10 API security risks, organizations can significantly improve their security posture and protect their APIs from attacks. Implementing the recommendations provided by OWASP is a crucial step in any API security project.
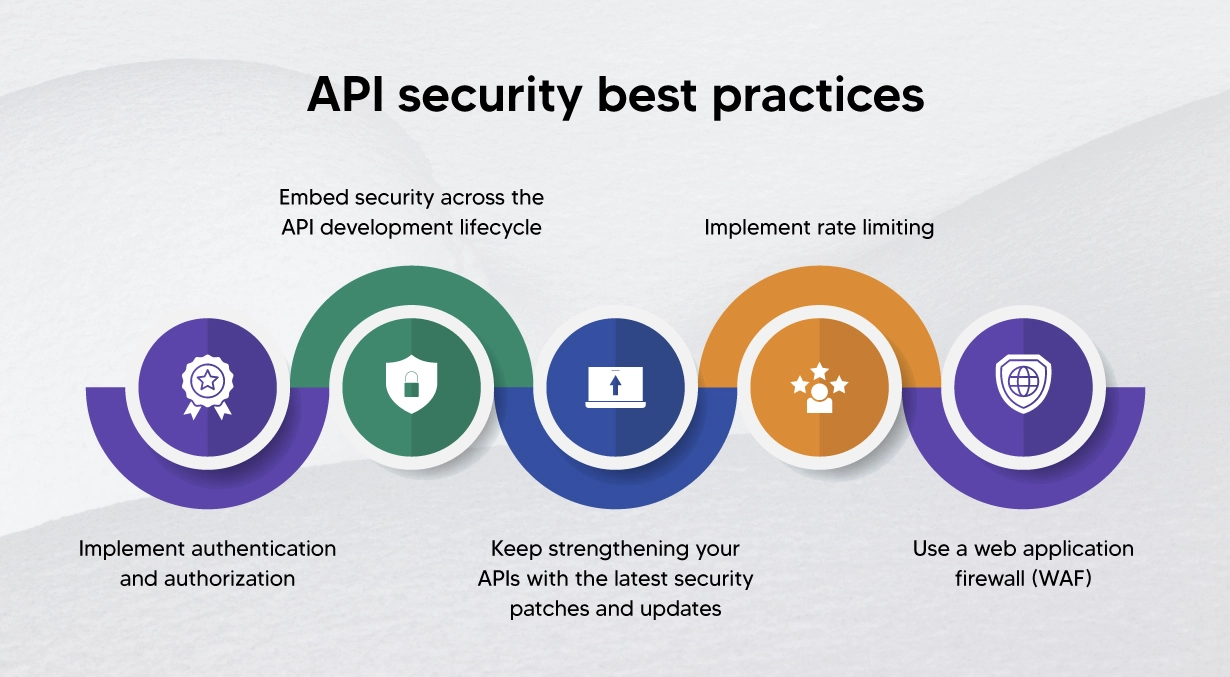
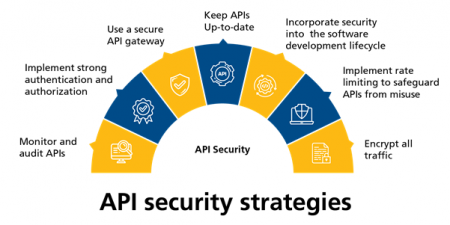
Best Practices for Securing APIs
Authentication and Authorization Strategies
Effective authentication and authorization are fundamental API security best practices. Authentication verifies the identity of the client making an API request, while authorization determines what resources the client is allowed to access. Strong authentication mechanisms, such as multi-factor authentication, should be implemented to prevent unauthorized access. Authorization should follow the principle of least privilege, granting users only the permissions necessary to perform their tasks. Proper implementation of authentication and authorization mechanisms is crucial to address OWASP Top 10 API security risks. protect your APIs against vulnerable to attacks and prevent api attacks on APIs. We at Teamwin Global Technologica know that robust authentication protocols are essential security measures.
Implementing API Gateways for Protection
API gateways are essential components in defending against security threats and unauthorized access. play a vital role in API protection is essential in a landscape where APIs have become increasingly targeted play a vital role in API protection is essential in a landscape where APIs have become increasingly targeted. by acting as a central point of control for all API traffic. An API gateway can enforce security measures such as authentication, authorization, rate limiting, and threat detection. By routing all API calls through the API gateway, organizations can effectively manage and secure APIs while reducing the attack surface. API gateways also provide valuable insights into API usage patterns, enabling security teams to detect and respond to suspicious activity. Implementing API gateways is a security best practice for protecting APIs from various API threat and ensuring application security. At Teamwin Global Technologica, we consider API gateways a critical component for rest APIs secure APIs.
Utilizing JSON Web Tokens for Secure APIs
JSON Web Tokens (JWTs) are a widely adopted security standard for securely transmitting information between parties as a JSON object. In the context of API security, JWTs are commonly used for authentication and authorization. When a user authenticates, the API server issues a JWT containing information about the user’s identity and permissions. Subsequent API requests include the JWT and an api key, which the API server validates to ensure the request is authorized using a secure communication method. JWTs provide a stateless and scalable authentication mechanism, making them a valuable tool for securing APIs. Adopting JWTs is a security best practice that enhances rest api security best practices API protection. JWTs offer a secure way to manage authentication in your API security strategy.
Mitigating Injection Attacks
Understanding SQL Injection Attacks
One of the most prevalent API security risks is SQL injection. SQL injection attacks on APIs occur when an attacker is able to insert malicious SQL code into an API request, causing the API server to execute unintended commands on the underlying database. This can lead to sensitive data being exposed, modified, or deleted. To prevent SQL injection, it is crucial to validate and sanitize all user inputs to API endpoints. Parameterized queries and stored procedures should be security best practices, ensuring that user-supplied data is treated as data and not executable code. Understanding the mechanics of SQL injection attacks is essential for implementing effective security measures.
Strategies to Prevent Injection Attacks
To effectively protect your APIs from injection attacks, several security best practices should be followed. Input validation is key; always validate and sanitize user inputs before processing them to prevent malicious code from being injected. Implement the principle of least privilege, ensuring that database users only have the necessary permissions to perform their tasks. Regularly perform security testing and security audits to identify and address potential API vulnerabilities. Consider security solutions such as web application security firewalls (WAFs) to filter out malicious requests. By implementing these security features, you can significantly reduce the risk of security vulnerabilities in your applications. attack surface and protect your APIs from injection attacks.
Monitoring and Responding to API Vulnerabilities
Continuous monitoring is vital for maintaining API security. Implement robust logging and monitoring systems to detect suspicious API activity and potential API threat. Set up alerts for unusual patterns or unauthorized access attempts. When API vulnerabilities are identified, respond promptly to mitigate the security risk. Patch any identified issues and update your security measures. Regularly review and update your security strategy to adapt to evolving threats. Incident response plans should be in place to handle security breaches effectively. Regularly scheduled security audits are a security best practice that will help protect APIs from various API risks and ensure overall application security.
Developing an API Security Strategy
Integrating Security into the API Lifecycle
Integrating security best practices into the API lifecycle is crucial for secure APIs. This involves incorporating security considerations during the design, development, testing, deployment, and maintenance phases. Performing security testing throughout the API lifecycle helps identify and address security vulnerabilities and cyber threats. api vulnerabilities early on, reducing the risk of attacks on APIs. By making security an integral part of the API development process, organizations can protect your APIs from various api risks and ensure application security. This proactive approach is a cornerstone of a robust api security strategy. Teamwin Global Technologica advises that early integration is key to API protection.
Creating a Comprehensive Security Project Plan
A comprehensive security project plan is essential for effectively managing and mitigating security vulnerabilities in your API ecosystem. api security risks. This plan should outline the security measures that will be implemented, the roles and responsibilities of the security teams, and the timelines for completing various security tasks. The plan should also include procedures for incident response and disaster recovery to address potential API security vulnerabilities. Regular security audits should be scheduled to assess the effectiveness of the security measures and identify any potential weaknesses in the context of security threats. Creating a detailed security project plan ensures that api security is addressed in a systematic and organized manner. Teamwin Global Technologica emphasizes that a well-defined plan is vital for secure APIs.
Regularly Updating Security Best Practices
Given the evolving nature of api threat, it is crucial to regularly update security best practices. Stay informed about the latest api vulnerabilities and attacks on APIs, and adapt your security strategy accordingly. Participate in industry forums and conferences to learn from other security professionals. Continuously assess and improve your security measures to address new and emerging threats. Regularly updating security best practices ensures that your APIs remain secure and resilient. This proactive approach is a hallmark of a strong api security strategy. Teamwin Global Technologica recommends ongoing vigilance to mitigate the risks of API attacks. protect your APIs from the latest api security risk.
Conclusion
Recap of API Security Best Practices
In summary, securing APIs requires a multi-faceted approach encompassing strong authentication and authorization mechanisms, the implementation of API gateways, the utilization of JSON Web Tokens, and the mitigation of injection attacks. Following security best practices and addressing the OWASP API Security Top 10 are critical for secure APIs. Continuous monitoring, regular security audits, and prompt incident response are essential for maintaining a strong security posture. By implementing these measures, organizations can effectively protect your APIs and ensure the confidentiality, integrity, and availability of their data. Teamwin Global Technologica reinforces that diligence is essential for API protection.
Future Trends in API Security
Looking ahead, several trends are shaping the future of API security, particularly in relation to REST APIs. API security. The increasing adoption of microservices architectures is driving the need for more granular and dynamic authentication and authorization mechanisms, including transport layer security, are vital for securing APIs. The rise of API-first development is emphasizing the importance of security by design. The growing use of artificial intelligence and machine learning is enabling more sophisticated threat detection and response capabilities. Staying abreast of these trends is crucial for maintaining effective API security. Teamwin Global Technologica notes that innovation is key to staying ahead of API threat.
Final Thoughts on Protecting Your APIs
Protecting your APIs is not just a technical challenge; it is a business imperative. A strong API security strategy is essential for maintaining user trust, ensuring compliance, and safeguarding your organization’s reputation. By implementing security best practices, staying informed about emerging threats, and continuously improving your security measures, you can effectively secure APIs and mitigate API risks. Remember, implementing dynamic application security testing can help in identifying potential security threats early. API security is an ongoing process that requires diligence, expertise, and a commitment to excellence. Teamwin Global Technologica emphasizes that safeguarding your APIs is vital for long-term success in today’s interconnected digital landscape.
5 Surprising Facts About How to Secure APIs Against Cyber Attacks
- Most breaches start with misconfigured APIs, not zero‑day exploits. Simple configuration mistakes—open endpoints, improper CORS settings, or excessive permissions—are more commonly exploited than novel vulnerabilities, so how to secure APIs against cyber attacks often begins with configuration hygiene.
- Rate limiting and throttling can stop sophisticated attacks. Techniques like credential stuffing and API abuse are often automated; properly implemented rate limits, dynamic throttling, and anomaly detection are surprisingly effective first lines of defense.
- Strong authentication beats custom token schemes. Rolling your own auth is risky—adopting proven standards (OAuth 2.0, OpenID Connect) and adding MFA dramatically reduces attack surface and is a key part of how to secure APIs against cyber attacks.
- Encrypted fields and granular access control matter even inside the network. Even internal APIs can be breached; encrypting sensitive fields, using mutual TLS, and enforcing least privilege for service-to-service calls are often overlooked but critical measures.
- Proper observability uncovers attacks faster than perfect prevention. Robust logging, distributed tracing, and real-time alerting enable rapid detection and response—making observability a core strategy for how to secure APIs against cyber attacks rather than an optional add‑on.
How can I protect APIs from common api attacks?
Protecting apis from common api attacks requires layered security controls: enforce strong authentication (use api keys and OAuth tokens), implement rate limiting and throttling at the api gateway level, validate and sanitize all input to prevent injection, use TLS for transport encryption, and carry out regular api security testing. Tools like web application firewalls and API security solutions help block malicious traffic, while monitoring and anomaly detection identify security threats such as credential stuffing, DDoS, and broken object level authorization attempts.
Why is api security important and what risks associated with api should I prioritize?
Api security important because APIs expose data and functionality that attackers can exploit, affecting api users, data from an api, and backend systems. Prioritize risks associated with api such as broken authentication, excessive data exposure, injection vulnerabilities, improper asset management (api sprawl), and insufficient logging. A security policy that covers api discovery, dedicated api security, and access to an api reduces the chance of breaches.
What practical api protection steps should I take for rest apis?
To protect REST apis, use secure api design: apply least privilege, version your endpoints (api versions) to manage changes, enforce authentication and authorization (api keys for authentication or OAuth), validate payloads, and return minimal data. Implement api management for lifecycle control, use TLS, and perform automated api security testing (including fuzzing and schema validation) to catch issues before production.
How do api keys for authentication fit into ways to secure my APIs?
Api keys are a common method to authenticate and track access to an api, but they should not be the only control. Use API keys with scoped permissions, rotate them regularly, store them securely (not in client-side code), and combine them with stronger measures like OAuth, mTLS, or short-lived tokens as part of a comprehensive API security solution. Tools like api gateways can enforce key validation and rate limits to reduce abuse.
Can even internal apis be vulnerable and how do I protect the api infrastructure?
Yes, even internal apis are vulnerable and can be a major source of risk if not managed. Protect the api infrastructure by segmenting networks, enforcing mutual TLS, applying identity-based access controls, cataloging apis to prevent api sprawl, and using internal api gateways to apply consistent security controls. Regular api discovery and dedicated api security reviews help ensure internal endpoints are not overlooked.
What api security features and tools should be used to mitigate api attacks?
Key api security features include authentication and authorization, rate limiting, logging and monitoring, input validation, and payload encryption. Use tools like api gateways, service meshes, API management platforms, and security scanning tools for static and dynamic api security testing. Implement an incident response plan and integrate security controls into CI/CD to catch vulnerabilities early.
How do I balance api usability for api users while applying strict api protection?
Balancing usability and protection means using unique security mechanisms that are transparent to legitimate api users: provide clear API documentation, support token-based auth and scopes, offer developer onboarding for use an api, and use API clients or SDKs to handle auth flows. Apply progressive enforcement (monitoring then stricter limits) and versioning (api versions) to minimize disruption while maintaining security.
What ongoing practices should experienced api teams adopt to learn how to secure every api?
Experienced api teams should adopt continuous practices: perform regular api security testing, maintain a security policy covering api integrations and management, run threat modeling for new endpoints, track api versions, and reduce api sprawl through discovery and governance. Use telemetry to monitor how apis are used, update controls based on incidents, and train developers in secure api design to ensure APIs are used safely across the organization.