New “Daemon Ex Plist” Vulnerability Gives Attackers Root Access on macOS
Unmasking “Daemon Ex Plist”: A macOS Vulnerability Exposing Root Privileges
The digital landscape is under constant siege, and even seemingly secure operating systems like macOS are not immune to critical vulnerabilities. A recent discovery, dubbed “Daemon Ex Plist,” has sent ripples through the cybersecurity community, revealing a concerning path for attackers to gain root access on macOS devices. This vulnerability exploits fundamental weaknesses in how macOS handles background services, specifically through misconfigurations in daemon property list (plist) files. Understanding this threat is crucial for IT professionals, security analysts, and developers responsible for maintaining the integrity of macOS environments.
Understanding the “Daemon Ex Plist” Vulnerability
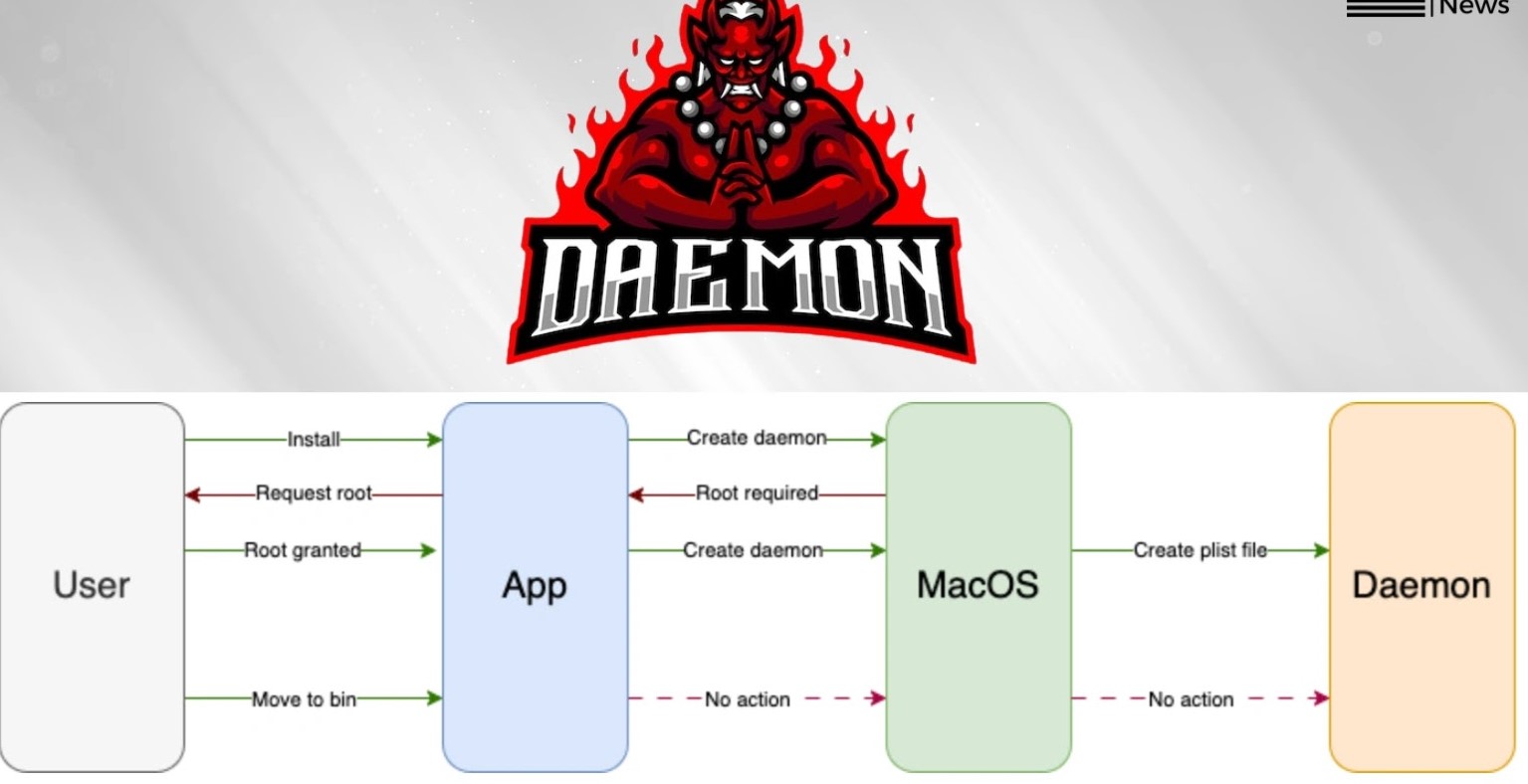
The core of the “Daemon Ex Plist” vulnerability lies in the improper handling and misconfiguration of daemon services within macOS. Daemons are essential background processes that run without direct user interaction, performing critical system functions. They are typically configured using property list (plist) files, which dictate their behavior, permissions, and execution paths. Attackers are exploiting weaknesses in how these plist files are managed and processed, particularly when these daemons are left behind in directories like /Library/LaunchDaemons/ with insecure configurations.
This vulnerability allows for privilege escalation to root, which means an attacker can gain complete control over the compromised macOS system. This level of access grants the ability to install malware, steal sensitive data, modify system configurations, or launch further attacks. While a specific CVE ID for this broader vulnerability discovery isn’t referenced in the source, similar privilege escalation flaws via insecure file permissions or misconfigured services have been documented, such as CVE-2022-26694 (though not directly related to this specific discovery, it illustrates the class of vulnerabilities).
How the Vulnerability Works: Misconfigured Daemon Services
The “Daemon Ex Plist” vulnerability capitalizes on misconfigurations in how applications and services deploy and manage their associated daemon plist files. When software is uninstalled, or even when it’s installed incorrectly, it can leave behind remnants of daemon configurations in system directories. If these leftover plist files have insecure permissions or contain vulnerabilities in their execution parameters, an attacker with lower-level access can manipulate them. For instance, if a daemon is configured to run an executable from a user-writable path, a malicious actor could replace that executable with their own, leading to arbitrary code execution with root privileges when the daemon starts or restarts.
The issue has been observed affecting various popular applications, including multiple VPN services. This highlights a significant concern, as VPN applications often require elevated privileges to manage network connections, making their associated daemons prime targets if not secured properly.
Impact of Root Access on macOS Devices
Gaining root access on a macOS device presents a catastrophic security breach. The implications include:
- Complete System Compromise: Attackers can bypass all security controls, essentially owning the machine.
- Data Exfiltration: Sensitive personal data, intellectual property, and credentials stored on the device become easily accessible.
- Malware Installation: Persistent backdoors, ransomware, and other malicious software can be installed without user knowledge.
- Espionage and Surveillance: The compromised device can be used for spying, keylogging, and capturing screen activity.
- Lateral Movement: The compromised Mac can serve as a launchpad for attacks against other systems within the network.
Remediation Actions and Best Practices
Mitigating the “Daemon Ex Plist” vulnerability requires a multi-faceted approach, combining proactive system hygiene with diligent security practices:
- Regular System Audits: Periodically inspect directories like
/Library/LaunchDaemons/and/Library/LaunchAgents/for outdated or unneeded plist files. Only legitimate and actively used daemons should reside there. - Permission Checks: Ensure that all plist files and the executables they reference have appropriate permissions, restricting write access to authorized users and root only. Insecure permissions (e.g., world-writable) are a significant red flag.
- Software Hygiene: Encourage users to fully uninstall applications when no longer needed, using dedicated uninstaller tools if available, to ensure all related files, including daemons, are removed.
- Principle of Least Privilege: Developers creating macOS applications should adhere strictly to the principle of least privilege, ensuring their daemons and associated files have only the minimum necessary permissions.
- Secure Coding Practices: Implement robust input validation and secure path handling in daemon processes to prevent path traversal or arbitrary code execution vulnerabilities.
- Software Updates: Keep macOS and all installed applications updated to their latest versions. Software vendors often release patches for such vulnerabilities.
- Endpoint Detection and Response (EDR): Deploy EDR solutions to monitor for suspicious activity, such as unauthorized modifications to system files or unusual process execution.
Tools for Detection and Mitigation
Several tools can assist in identifying and mitigating issues related to macOS daemons and potential vulnerabilities:
| Tool Name | Purpose | Link |
|---|---|---|
| LaunchControl | GUI for managing system-wide and user-specific launch agents and daemons. | https://www.soma-zone.com/LaunchControl/ |
| KnockKnock | Reveals persistently installed software on macOS. | https://objective-see.com/products/knockknock.html |
| fs_usage | Monitor filesystem activity to identify what files processes are accessing. | Built-in macOS command-line tool |
| DTrace | Dynamic tracing framework useful for debugging and observing system behavior. | Built-in macOS framework (command-line tools like dtruss) |
| Endpoint Security Solutions | Advanced threat detection, response, and behavioral analysis. | Various vendors (e.g., CrowdStrike, SentinelOne, Microsoft Defender for Endpoint) |
Conclusion: Fortifying macOS Against Privilege Escalation
The “Daemon Ex Plist” vulnerability serves as a stark reminder that robust security requires constant vigilance and proactive measures, even on platforms generally considered secure. The ability for an attacker to escalate privileges to root on macOS through misconfigured daemons presents a severe risk. By understanding the underlying mechanisms of this vulnerability, thoroughly auditing system configurations, uninstalling unused software responsibly, and implementing the recommended security practices, users and organizations can significantly reduce their exposure to this and similar privilege escalation attacks. Staying informed and adopting a proactive security posture is paramount to defending against the evolving threat landscape.





