Securing VLANs Against Cyber Threats
VLAN Security Against Cyber Threats: Network Segmentation and VLAN Hopping Mitigation
In today’s landscape of escalating cyber threats, securing your network is more critical than ever. Virtual Local Area Networks (VLANs) offer a powerful means to enhance network security through network segmentation. This article delves into how VLANs function, the security risks they address, and best practices for VLAN configuration to mitigate vulnerabilities like VLAN hopping.
Understanding VLANs and Their Role in Network Security
What is a Virtual Local Area Network (VLAN)?
A Virtual Local Area Network (VLAN) is a logical network that segments a physical network without requiring physical rearrangement of network devices. VLANs enable network administrators to segment networks based on departments, project teams, or security requirements, irrespective of their physical location. By implementing VLANs, a physical network can be divided into multiple broadcast domains, improving network performance and enhancing security by isolating network traffic and limiting the attack surface.
How VLANs Work in Network Infrastructure
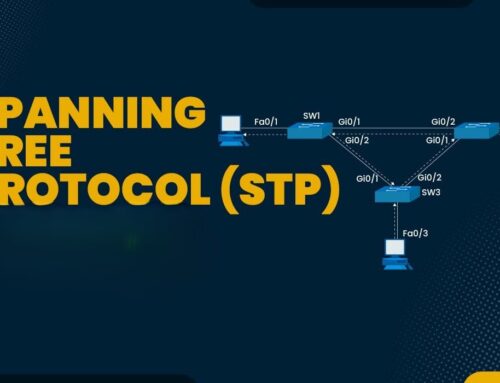
VLANs operate by adding a VLAN tag to network traffic, which identifies the VLAN to which a packet belongs, allowing for better management within a VLAN. Network switches use these tags to forward network traffic only to ports that are members of the specific VLAN. This segmentation is crucial for network security, as it prevents network traffic from one VLAN from being visible to devices in another VLAN. VLAN configuration is typically managed through network management tools, allowing network administrators to easily create and modify VLAN assignments.
Types of VLANs and Their Uses
There are several types of VLANs, each designed for specific purposes, which can help separate VLANs within a network. Data VLANs carry user-generated network traffic, while voice VLANs are optimized for VoIP traffic, ensuring quality of service. Management VLANs are used for network device administration. The native VLAN carries untagged network traffic. Implementing VLANs involves careful network design to ensure that VLAN assignments align with security and operational needs, reducing security vulnerabilities and improving overall network security. Using VLANs effectively is a best practice, as they provide a means to separate VLANs for different types of traffic.
Network Segmentation: A Key to Enhanced Security
The Importance of Network Segmentation
Network segmentation is a crucial aspect of modern network security, and Virtual Local Area Networks (VLANs) are a cornerstone technology for achieving this within the network. Network segmentation involves dividing a network into smaller, isolated segments, each functioning as its own virtual local area network. This approach enhances security by limiting the attack surface. Should one network segment be compromised, the attacker’s access to network resources is restricted, preventing lateral movement to other parts of the network. Implementing VLANs effectively improves network performance and simplifies network management, ensuring that network traffic is contained and controlled.
Best Practices for Effective Network Segmentation
Effective network segmentation relies on well-defined VLAN configuration and adherence to best practices. It’s crucial to separate network traffic based on sensitivity and function. For example, isolating sensitive data in one VLAN and guest network access in another using multiple VLANs provides a clear separation of traffic types. Regular reviews of VLAN assignments and network configuration are essential to mitigate security vulnerabilities. Proper network design also includes disabling unused ports and implementing strict access control lists (ACLs) to further enhance security. Implementing VLANs correctly and making use of VLAN technologies contributes significantly to overall network security.
Improving Network Performance through Segmentation
Beyond security, network segmentation through VLANs can significantly improve network performance. By segment a network into smaller broadcast domains, network traffic is reduced, and network congestion is minimized. This isolation ensures that network traffic-intensive applications or services do not negatively impact other parts of the network, providing an additional layer of security. Furthermore, VLANs allow for prioritization of specific network traffic, such as voice or video, by assigning them to dedicated VLANs with appropriate quality of service (QoS) settings within a VLAN. The use VLANs in this way enhances network performance and the user experience by optimizing network resource allocation and management.
VLAN Hopping: Understanding the Threat
What is VLAN Hopping?
VLAN hopping is a cyber attack that allows network traffic from one VLAN to be seen by another, despite VLANs being designed to isolate network traffic and provide separate VLANs.. This security risk bypasses network segmentation and can lead to unauthorized access to network resources and data. VLAN hopping typically exploits misconfigurations or vulnerabilities in VLAN configuration and network infrastructure, highlighting the need for robust security within the network. Understanding how VLAN hopping works is crucial for network administrators to mitigate this security threat and implement effective security measure to protect their physical network.
Common VLAN Hopping Attacks
Several VLAN hopping attack methods exist, with switch spoofing and double tagging being the most prevalent within a network environment. Switch spoofing involves an attacker configuring their network device to mimic a network switch, thereby negotiating a trunk link and gaining access to network all VLAN traffic. Double tagging occurs when an attacker adds two VLAN tag to a packet. The first VLAN tag directs the packet to a trunk port, while the second VLAN tag allows the packet to enter the target VLAN. Proper VLAN configuration and network security practices are essential to defend against these cyber threats and ensure secure VLAN access..
Security Risks Associated with VLAN Hopping
The security risks associated with VLAN hopping are significant, potentially leading to data breaches, security incidents, and significant financial losses. By bypassing network segmentation, attackers can gain unauthorized access to network sensitive data, compromise critical systems, and disrupt network operations. Furthermore, successful VLAN hopping attacks can undermine trust in the organization’s cyber security posture, affecting reputation and customer confidence. Implementing VLANs with robust security controls is essential to mitigate these risks and protect the network from cyber intrusions. Employing best practice in VLAN management and network configuration can enhance security and prevent VLAN hopping attempts.
Mitigating VLAN Hopping Attacks
Effective VLAN Configuration Strategies
To effectively mitigate VLAN hopping attacks, rigorous VLAN configuration strategies are paramount. Network administrators should implement several key measures, including:
- Ensuring that all network ports are explicitly assigned to a specific VLAN, disabling dynamic trunking protocol negotiation to prevent unauthorized network devices from establishing trunk links.
- Carefully reviewing the native VLAN settings, ensuring it is different from all used VLANs and is not used for any active network traffic or network management.
These meticulous VLAN settings act as a security measure, fortifying the physical network against cyber threats.
Implementing Security Protocols and VLAN Tags
Enhance VLAN security by implementing robust security protocols and proper VLAN tag management to ensure effective VLAN access. Several actions can improve the security posture of your VLANs, including:
- Employ IEEE 802.1Q VLAN tag standard correctly to ensure accurate VLAN identification and network traffic segregation.
- Enable port security features on network switches to limit the number of Media Access Control (MAC) addresses allowed on each port, preventing MAC address flooding attacks.
Implementing VLANs with appropriate security controls is essential to mitigate unauthorized network access and maintain the integrity of the local area network. These security measures bolster the network security.
Network Design for Enhanced Security
A well-thought-out network design is fundamental for enhanced security against VLAN hopping, particularly by ensuring separate VLANs are configured correctly. Segment a network into smaller, manageable network segments based on function and sensitivity. Avoid default VLAN assignments and separate network traffic to minimize the attack surface. Consider the types of VLANs that best suit the network’s needs, and ensure that all network devices are regularly updated with the latest firmware and security patches to maintain VLAN access. Segmenting networks using a carefully designed network infrastructure can significantly improve network performance and mitigate security vulnerabilities.
Best Practices for VLAN Security Management
Here are 5 simple points about Best Practices for VLAN Security Management:
-
Limit VLAN access – Allow only authorized devices and users to connect to specific VLANs.
-
Use separate VLANs – Keep sensitive systems (servers, management, finance) on separate VLANs.
-
Disable unused ports – Turn off switch ports that are not in use to prevent unauthorized access.
-
Implement VLAN access controls – Use ACLs or firewall rules to control traffic between VLANs.
-
Regularly monitor and audit – Check VLAN configurations and logs to detect misconfigurations or attacks.
Monitoring Network Traffic for Security Threats
Continuous monitoring of network traffic is crucial for detecting and responding to security threats. Implement intrusion detection systems (IDS) and intrusion prevention systems (IPS) to analyze network traffic for suspicious patterns indicative of VLAN hopping attacks. Regularly review network logs and audit trails to identify anomalous activities and potential security incidents. Ensure that the network management systems have capabilities that support real-time monitoring of network traffic analysis and alerting, enabling prompt responses to cyber threats against VLAN security.
VLAN Management and Access Control
Effective VLAN management and strict access control to network controls are vital for maintaining VLAN security. To achieve this, consider implementing the following measures to enhance the network environment.
- Implement role-based access control (RBAC) to limit network access to authorized personnel only.
- Regularly review and update VLAN assignments and network configuration to ensure they align with current security policies.
- Enforce strong authentication and authorization mechanisms for network device access, preventing unauthorized modification of VLAN settings.
These security controls can greatly enhance network protection and mitigate security risks.
Physical Security Measures to Support VLAN Security
Physical security measures are an integral part of VLAN security. Secure network infrastructure, including network switches and cabling, in locked and access-controlled rooms to prevent unauthorized physical access. Implement surveillance systems and monitor entry points to deter and detect potential intruders. Conduct regular physical security audits to identify and address vulnerabilities. Integrating physical security measures with logical VLAN security practices provides a comprehensive defense against cyber threats and ensures the integrity of the network.
5 Surprising Facts about Securing VLANs Against Cyber Threats
- VLANs are not security boundaries: VLAN segmentation isolates broadcast domains but does not encrypt or prevent an attacker on the same physical network from sniffing or exploiting routed paths—you still need firewalls, ACLs, and encryption.
- VLAN hopping is simple if misconfigured: Techniques like 802.1q double-tagging or poorly configured trunk ports can let an attacker escape their VLAN and access others, often without advanced tools.
- Using the default management VLAN is dangerous: Keeping switches and network gear on VLAN 1 (or any obvious ID) makes them easy targets; moving management to a dedicated, restricted VLAN reduces exposure.
- Private VLANs (PVLANs) have limits: PVLANs can restrict east‑west communication at layer 2 but rely on proper router/firewall enforcement for full isolation—misapplied PVLANs can give a false sense of protection.
- Trunk and native VLAN mismatches leak traffic: Inconsistent native VLAN settings between switches or between switch and router can result in untagged frames leaking into unexpected VLANs, exposing sensitive traffic.
How does the native VLAN affect securing vlans against cyber threats in a modern network?
The native vlan is the VLAN to which untagged frames are assigned and plays a critical role when securing vlans against cyber threats. Misconfigured native VLANs can enable unauthorized access and VLAN hopping, allowing attackers to move from one vlan to another. To improve the security posture, set the native vlan to an unused ID, avoid using default values, and ensure switches tag all trunked traffic where possible so that the vlan to which the frame belongs is explicit and the flow of network traffic is controlled.
What VLAN access control methods can enhance network security and prevent unauthorized access and VLAN hopping?
VLAN access control combines access control lists (ACLs), private VLANs, port security, and 802.1X network access to restrict devices within the same vlan and between vlans. ACLs filter traffic flow inside each vlan and between vlans, while 802.1X ensures devices can access the network only after authentication. Implementing these controls helps segment the single physical network into separate broadcast domains and reduces the risk that devices can access the network resources they shouldn’t.
How should network management practices be adapted to secure VLANs inside the network?
Effective network management includes centralized monitoring, strict device credential policies, and using tools like SNMP (simple network management protocol) with secure versions (SNMPv3) for configuration and telemetry. Regularly audit switch configurations for vlan registration protocol settings and native vlan assignments, enforce change control, and log routing between vlans to detect anomalous traffic flow inside the network early.
Why is segmentation and security important when you want to improve the security of one network?
Segmentation and security reduce attack surfaces by splitting a single physical network into separate broadcast domains so that traffic used to separate network traffic can be controlled and inspected at boundaries. When a vlan operates as an independent domain, compromised devices are contained and cannot freely reach resources in another vlan to which the frame would otherwise be forwarded. Proper segmentation enforces policies for traffic flow and limits lateral movement.
How can routing between VLANs be secured to control traffic from one VLAN to another?
Secure routing between vlans requires firewalls or ACLs on layer 3 devices, strict inter-vlan access policies, and microsegmentation for sensitive workloads. Only allow necessary services and ports between vlans, and inspect traffic using intrusion detection/prevention. Monitoring of routing between vlans helps detect unusual patterns, and policies should ensure that devices always connect to that vlan intended for their role.