What Is a Cyber Kill Chain?
What is a Cyber Kill Chain Explained: Kill Chains, Definition, & Uses
In the realm of cybersecurity, the cyber kill chain stands as a vital framework, offering a structured approach to understanding and combating cyber attacks. This model, initially developed by Lockheed Martin, provides a comprehensive view of the stages of a cyberattack, from the initial reconnaissance to the final actions on objective. By understanding each phase, security teams can proactively implement defense strategies and enhance their overall security posture. This article aims to explore the intricacies of the cyber kill chain, its significance in cybersecurity, and how it can be effectively used to protect against evolving cyber threats.
Understanding the Cyber Kill Chain
Definition of the Cyber Kill Chain
The cyber kill chain is a structured, phase-based approach that outlines the various stages of a cyberattack. It serves as a framework for understanding how an attacker progresses through an intrusion, starting with reconnaissance and culminating in data exfiltration or other malicious activities. Each phase of the cyber kill chain represents a critical step an attacker must complete to achieve their objective. Understanding the cyber kill chain involves recognizing these stages and implementing security measures to disrupt the attacker’s progress at each point. By following the cyber kill chain, security professionals can better anticipate and respond to cyber threats.
Importance of Kill Chains in Cybersecurity
Kill chains play a pivotal role in cybersecurity by providing a clear, actionable framework for understanding and mitigating cyber threats. The cyber kill chain in cybersecurity allows security teams to identify vulnerabilities and implement targeted security measures to disrupt cyberattacks. By analysing each stage of the cyber kill chain, organizations can enhance their incident response capabilities and improve their overall defense strategies. The importance of kill chains is also evident in their ability to facilitate better communication and collaboration among security professionals, ensuring a coordinated and effective approach to cybersecurity.
Overview of the Cyber Kill Chain Model
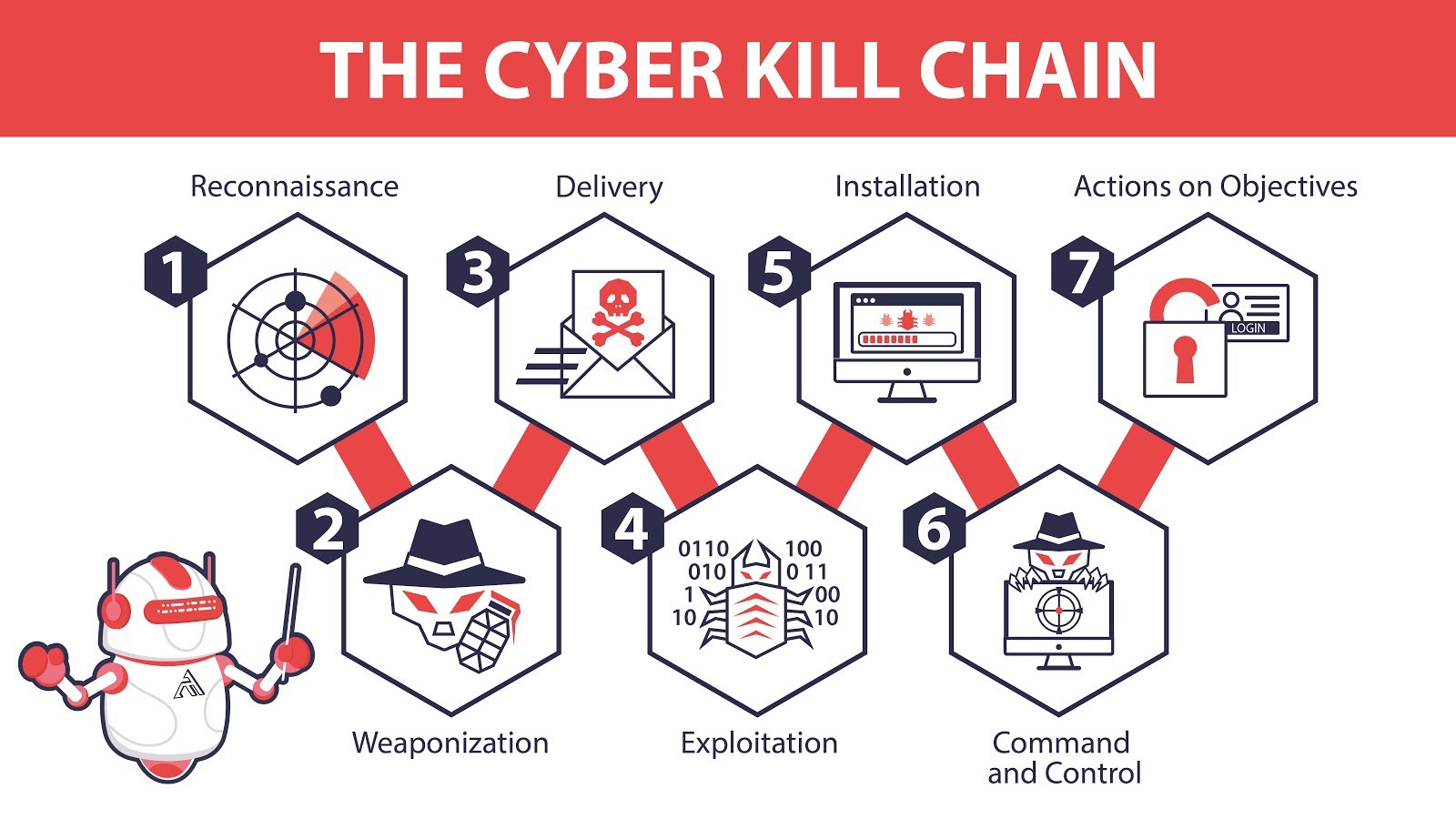
The cyber kill chain model typically consists of seven stages, each representing a critical phase of a cyberattack. These stages can be summarized as follows:
| Stage | Description |
|---|---|
| Reconnaissance | The attacker gathers information about the target. |
| Weaponization | Creating a malicious payload, such as malware or ransomware. |
| Delivery | The method used to transmit the weaponized payload to the target, often through phishing or social engineering. |
| Exploitation | Leverages a vulnerability to gain access to the system. |
| Installation | Involves planting malicious code. |
| Command and Control | Establishes communication with the compromised system. |
| Actions on Objective | Represent the attacker’s goals, such as data exfiltration or system disruption. |
Stages of the Cyber Kill Chain
Phase 1: Reconnaissance
The first phase of the cyber kill chain is reconnaissance, where the attacker gathers information about the target. This stage of the attack involves intelligence gathering to identify potential vulnerabilities and entry points. Attackers may use various techniques, including social engineering, network scanning, and open-source intelligence (OSINT), to gather information about the target’s systems, employees, and security posture. Effective perimeter security and understanding the cyber kill chain framework are essential during this phase to detect and prevent potential cyber attacks using the steps of the cyber kill. This initial stage sets the foundation for subsequent phases in the kill chain process.
Phase 2: Weaponization
Weaponization is the second phase of the cyber kill chain model. In this stage, the attacker creates a malicious payload, such as malware or ransomware, designed to exploit the identified vulnerabilities. The attacker combines an exploit with a delivery mechanism to create a weaponized package. This phase requires technical expertise and a deep understanding of the target’s systems. Organizations must enhance their detection capabilities to identify and neutralize weaponized payloads before they can be delivered. Understanding the cyber kill chain at this stage helps security teams anticipate and mitigate potential cyber threats.
Phase 3: Delivery
The delivery phase involves transmitting the weaponized payload to the target environment. Attackers often use various methods, including phishing emails, malicious websites, and infected USB drives, to deliver the payload. Social engineering plays a significant role in this phase, as attackers manipulate individuals into opening malicious attachments or clicking on harmful links. Effective security measures, such as email filtering and employee training, are crucial to prevent successful delivery. The ability to detect and block malicious payloads during the delivery phase is vital to disrupting the cyber kill chain and protecting sensitive data from potential breaches.
Phase 4: Exploitation
During the exploitation phase, the attacker leverages a vulnerability to gain unauthorized access to the target system or network. This phase involves executing the malicious code to trigger the vulnerability and compromise the system. Successful exploitation often leads to privilege escalation and further access within the network. Patch management and vulnerability scanning are essential security measures to minimize the risk of exploitation. By identifying and remediating vulnerabilities, organizations can significantly reduce the likelihood of a successful cyberattack and disrupt the cyber kill chain.
Phase 5: Installation
The installation phase involves planting persistent malware or other malicious code on the compromised system. This stage of the cyber kill chain ensures that the attacker maintains long-term access to the system, even if it is rebooted or patched. Attackers often use techniques such as creating backdoors or modifying system files to establish persistence. Detecting and removing malicious installations requires advanced threat hunting and incident response capabilities. Effective endpoint detection and response (EDR) solutions are crucial for identifying and mitigating malicious installations and preventing further damage.
Phase 6: Command and Control
In the command and control (C2) phase, the attacker establishes communication with the compromised system to remotely control and manage it. This stage of the attack allows the attacker to issue commands, exfiltrate data, and perform other malicious activities. C2 channels are often disguised to evade detection, using techniques such as encryption and steganography. Monitoring network traffic and analysing communication patterns are essential for detecting C2 activity. Implementing network segmentation and access controls can help limit the impact of a successful C2 connection and prevent further damage.
Phase 7: Actions on Objectives
The final phase of the cyber kill chain, actions on objective, represents the attacker’s ultimate goals. These actions may include data exfiltration, system disruption, financial theft, or intellectual property theft. Understanding the attacker’s objectives helps security teams prioritize their defense strategies and implement targeted security measures. Incident response plans should be designed to quickly contain and mitigate the impact of these actions. By focusing on protecting critical assets and sensitive data, organizations can minimize the damage caused by a successful cyberattack and ensure business continuity.
Applying the Cyber Kill Chain Framework
Using the Cyber Kill Chain to Strengthen Cybersecurity
To use the cyber kill chain effectively, security teams must integrate it into their overall security posture. Understanding the cyber kill chain helps security professionals identify potential vulnerabilities and implement targeted defense strategies to disrupt cyber attacks. By analysing each phase of the cyber kill chain, organizations can enhance their incident response capabilities and improve their overall security strategy. The cyber kill chain framework in cybersecurity allows for better communication and collaboration among security teams, ensuring a coordinated and effective approach to the steps of the cyber kill chain. Incorporating the cyber kill chain offers an organization’s ability to anticipate and mitigate cyber threats, ensuring more robust cybersecurity.
How Organizations Can Benefit from the Kill Chain Process
Organizations can significantly benefit from the kill chain process by gaining a structured approach to understanding and mitigating cyber threats. The cyber kill chain model provides a clear framework for identifying and addressing vulnerabilities at each stage of an attack. By following the cyber kill chain methodology, organizations can enhance their detection capabilities, improve their incident response plans, and strengthen their overall security posture. The kill chain process facilitates better resource allocation, enabling security teams to focus on the most critical threats and vulnerabilities. Using the cyber kill chain helps organizations proactively protect sensitive data and critical assets, reducing the risk of a successful cyberattack.
Integrating the Cyber Kill Chain in Incident Response
Integrating the cyber kill chain in incident response is crucial for effectively managing and mitigating cyber attacks. Incident response teams can use the cyber kill chain to understand the attacker’s progression, identify compromised systems, and contain the breach. By mapping the stages of a cyberattack to the cyber kill chain, incident responders can prioritize their actions and implement targeted security measures to disrupt the attacker’s progress. The cyber kill chain framework helps incident response teams anticipate the attacker’s next moves and proactively defend against further exploitation. This integration enhances the effectiveness of incident response efforts and reduces the overall impact of cyber incidents, ensuring business continuity and data protection.
Advanced Persistent Threats and the Cyber Kill Chain
Understanding APTs in the Context of the Cyber Kill Chain
Advanced Persistent Threats (APTs) represent a sophisticated type of cyberattack. They are characterized by their prolonged and stealthy nature, which is often detailed in the seven steps of the cyber kill. These attacks often target specific organizations or industries with the goal of stealing sensitive data or disrupting critical systems. In the context of the cyber kill chain framework, understanding APTs involves recognizing how these attackers operate across each kill chain stage. APT groups often exhibit a high degree of patience and employ advanced techniques to evade detection. Therefore, organizations must use the cyber kill chain proactively, focusing on early detection and disruption to counter these persistent threats. Our cybersecurity solution is designed to safeguard your enterprise, ensuring tomorrow’s success.
Strategies to Mitigate APTs Using Cyber Kill Chain Steps
To effectively mitigate APTs, security teams must implement targeted defense strategies at each stage of the cyber kill chain. The following table outlines some defense strategies for specific stages:
| Cyber Kill Chain Stage | Defense Strategies |
|---|---|
| Reconnaissance | Enhanced perimeter security measures, such as advanced intrusion detection systems. |
| Weaponization and Delivery | Robust email filtering and endpoint detection and response (EDR) solutions. |
| Exploitation and Installation | Patch management and vulnerability scanning. |
| Command and Control | Network monitoring and anomaly detection. |
| Actions on Objective | Data loss prevention (DLP) tools. |
Case Studies: Successful Implementations of the Cyber Kill Chain
Numerous organizations have successfully implemented the cyber kill chain to defend against cyberattacks, including APTs. For example, Lockheed Martin used the kill chain framework to analyze and improve its incident response capabilities, resulting in faster detection and mitigation of cyber threats. Another case study involves a financial institution that integrated the cyber kill chain can help enhance its security operations center (SOC). This integration helped security professionals identify and disrupt advanced attacks, preventing significant financial losses and reputational damage. These examples demonstrate how understanding the cyber kill chain and using the cyber kill chain proactively can enhance an organization’s security posture. Safeguarding Your Enterprise, Ensuring Tomorrow’s Success.
What is the cyber kill chain in cybersecurity and how does it work?
The cyber kill chain in cybersecurity is a framework developed by Lockheed Martin that describes the original cyber kill chain process as a sequence of stages attackers follow during a cyberattack. The original cyber kill chain model outlines seven stages — reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives — which help security teams identify attack patterns, plan security controls, and design defense strategies such as perimeter security and malware prevention and modern security monitoring.
What are the seven stages of a cyber and why are the seven steps important?
The seven stages of the cyber kill chain break an attack chain into seven steps: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. These seven steps are important because the framework developed by Lockheed Martin helps security experts and security teams identify where to interrupt an attack, enabling targeted security controls, detection rules, and security awareness training to stop cyber threats earlier in the lifecycle.
How does the cyber kill chain process help organizations stop cyberattack activity?
The cyber kill chain process helps organizations by mapping attacker behaviour to actionable stages so security teams can implement layered security solutions and defenses. By knowing the stage of the kill chain you can prioritize controls — for example, strengthening perimeter security and malware defenses during delivery, improving patching and endpoint controls for exploitation and installation, and monitoring network traffic to detect command and control and lateral movement when attackers move laterally or attempt data exfiltration.
Can the original cyber kill chain model address insider threats and credential abuse?
Yes, while the original cyber kill chain focused on external attack chains, it can be adapted to account for insider threats and credential compromise. The stages can include scenarios where an insider misuses credentials or an attacker gains legitimate access and then moves laterally through the steps of the cyber kill. Integrating identity monitoring, privileged access management, and security awareness training helps detect anomalous behaviour at stages like exploitation, installation, and actions on objectives.
How do security controls map to the stages in the cyber kill chain to improve cybersecurity?
Security controls map to stages in the cyber kill chain by targeting specific techniques used at each step. For reconnaissance and delivery, use threat intelligence and email/web filtering; for exploitation and installation, deploy endpoint protection and patch management; for command and control and actions on objectives, use network segmentation, anomaly detection, and data security measures. This mapping helps security teams identify gaps and apply defense strategies throughout the steps of the cyber kill chain.
What is the unified kill chain and how does it relate to mitre attack or other frameworks?
The unified kill chain expands the original cyber kill chain by incorporating modern attack patterns and linking stages to granular techniques, similar to the mitre attack framework. While the kill chain is a high-level attack chain concept, mitre attack provides detailed tactics and techniques for each stage or step in the cyber lifecycle. Combining the unified kill chain and mitre attack helps security experts build comprehensive detection and response playbooks and better prioritize security solutions.
How can security teams identify and stop an attacker who moves laterally during a breach using the cyber security kill chain?
Security teams identify lateral movement by monitoring for suspicious authentication patterns, credential usage, and unusual inter-host communications, which often appear after initial foothold and installation stages. Implementing strong logging, endpoint detection and response (EDR), network segmentation, and multi-factor authentication reduces the risk of attackers moving laterally. The cyber kill chain outlines context so teams can focus detection and response on the likely step in the chain and stop further actions on objectives.
Does the cyber kill chain provide guidance for modern security and how does it inform defence strategies?
The cyber kill chain provides a conceptual methodology that informs modern security by breaking attacks into discrete stages so defenders can place controls, detection, and response at each point. It helps security experts and teams identify where security solutions, security awareness training, and data security investments will be most effective. While the kill chain is a concept, when combined with frameworks like mitre attack and practical tools, it becomes a powerful way to design defence strategies and stop cyber threats before they achieve their objectives.