Preventing Man-in-the-Middle Attacks at Layer 2
Preventing Man-in-the-Middle Attacks at layer 2: A Security Guide
In today’s interconnected digital landscape, understanding and mitigating cyber threats is paramount. This guide provides essential insights into preventing man-in-the-middle attacks, a common cyber attack that poses a significant risk to network security. We aim to empower security teams and individuals with the knowledge needed to safeguard sensitive information and ensure secure communication between two parties.
Understanding Man-in-the-Middle Attacks
What is a Man-in-the-Middle Attack?
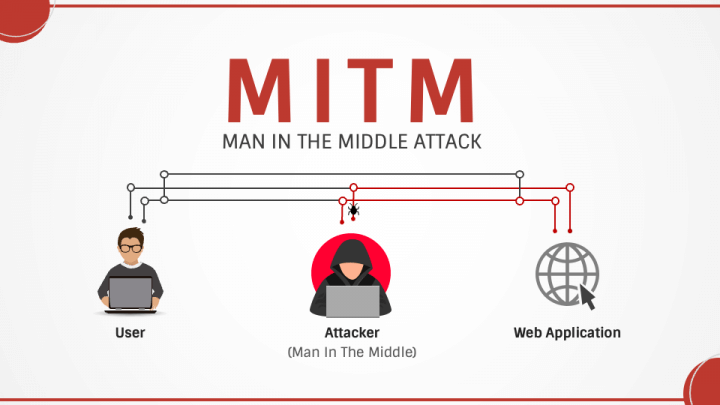
A man-in-the-middle attack (MitM attack) is a type of attack where an attacker secretly intercepts and potentially alters the communication between two parties who believe they are directly communicating with each other. In essence, the attacker inserts themselves into the communication channel, acting as a “man in the middle.” This interception allows the malicious actor to eavesdrop on conversations, steal sensitive data like login credentials and passwords, or even manipulate the data being exchanged through techniques like DNS spoofing attack. Understanding this type of attack is the first step toward implementing effective security measures and man-in-the-middle attack prevention. The risk of MitM attacks is increasing, so prevent man-in-the-middle attacks to avoid potential cyber threats.
Types of Man-in-the-Middle Attacks
Here are several common types of man-in-the-middle (MitM) attacks that exploit network vulnerabilities:
- DNS spoofing, where attackers alter DNS records to redirect network traffic to a malicious server.
- Wi-Fi interception, where attackers create fake Wi-Fi networks to intercept user traffic.
- ARP spoofing.
- SSL stripping is a common mitm technique used by attackers to intercept secure connections.
Recognizing these different types of MitM attacks is crucial for developing targeted detection and prevention strategies. It is important to always use safe Wi-Fi networks to prevent such attacks.
Common Attack Techniques
Attack techniques employed in man-in-the-middle attacks often involve spoofing, interception, and redirection of network traffic. Attackers may use techniques to spoof IP addresses or DNS entries, effectively redirecting victims to malicious websites. Once traffic is intercepted, attackers can steal credentials, sensitive data, or manipulate data in transit. SSL stripping is another common technique, where attackers downgrade secure HTTPS connections to unsecured HTTP, making the communication vulnerable to interception. Effective man-in-the-middle attack prevention requires understanding these attack techniques and implementing security measures to counter them. Attack prevention is crucial for network security, especially when dealing with protocols that transmit sensitive information and could be vulnerable to MitM attacks, which can gain access to confidential data.
Best Practices to Prevent Man-in-the-Middle Attacks
Network Security Measures
Effective network security measures are paramount in preventing man-in-the-middle attacks. Teamwin Global Technologica recognizes this and provides solutions such as enterprise AI-driven next-generation firewalls. These firewalls act as a critical layer of security, meticulously examining network traffic to detect and prevent malicious activity. Teamwin Global Technologica also provides robust endpoint security through endpoint protection management (EPM) and privileged access management (PAM), ensuring that all devices accessing the network are secure and authorized. Implementing advanced cyber security and employing both passive and active networking capabilities bolsters defenses against potential threats. TeamWin offers a comprehensive suite of end-to-end IT infrastructure and security services, designed to protect businesses of all sizes, ensuring seamless connectivity. By actively monitoring and analyzing network traffic, we can effectively detect and prevent MitM attack attempts, thus protecting sensitive information and login credentials from potential MitM attackers.
SSL and Encryption Techniques
SSL and encryption techniques form a cornerstone of man-in-the-middle attack prevention. Encryption protocols, such as Transport Layer Security (TLS) and its predecessor Secure Sockets Layer (SSL), are used to encrypt the communication between two parties, making it unreadable to an attacker who might intercept the network traffic. Ensuring that websites and applications use strong encryption protocols is crucial for maintaining strong security against potential threats. Enforcing HTTP Strict Transport Security (HSTS) further enhances security by instructing browsers to only access the server over HTTPS, preventing SSL stripping attacks. Regularly updating security certificates is essential to maintaining a secure connection and preventing spoofing attacks. The use of encryption ensures that sensitive information, such as passwords and financial details, remains confidential, even if a MitM attack occurs.
Authentication Strategies
Strong authentication strategies are essential to prevent MitM attacks. Multi-factor authentication (MFA) adds an extra layer of security beyond passwords, requiring users to verify their identity through multiple channels, such as a one-time code sent to their mobile device. Implementing robust access control policies and regularly reviewing user access rights minimizes the attack surface for unauthorized access to the network and data. Certificate-based authentication can also provide a secure method of verifying the identity of users and devices, enhancing overall security tools within the local network. By implementing these best practices, organizations can significantly reduce the risk of attackers intercepting login credentials and gaining unauthorized access to sensitive data. Strong authentication acts as a vital deterrent, making it significantly more difficult for attackers to successfully execute a MitM attack.
Detecting Man-in-the-Middle Attacks
Signs of a Man-in-the-Middle Attack
Detecting a man-in-the-middle attack (MitM attack) can be challenging, as attackers often try to remain undetected. However, certain signs can indicate a potential compromise. One common sign is unusual network behavior, such as slow loading times or frequent disconnections. Examining SSL certificates is important to ensure the certificate is valid and issued by a trusted certificate authority. Browser warnings about insecure connections or invalid certificates should never be ignored, as they may indicate a spoofing attack. By being vigilant and aware of these signs, security teams can quickly detect and respond to potential MitM threats, reducing the risk of sensitive data and login credentials theft. Effective detection strategies form a crucial layer of security, ensuring that any suspicious activity is promptly investigated and mitigated.
Tools for Detection
Several security tools are available to help security teams detect man-in-the-middle attacks more efficiently. Specifically, some useful tools include:
- Network intrusion detection systems (IDS) which can analyze network traffic for suspicious patterns and anomalies.
- Wireshark, a popular network protocol analyzer, allowing security professionals to capture and analyze network packets.
- SSL scan tools that can verify the validity and security of SSL certificates.
Implementing these tools is a valuable defense-in-depth strategy, enhancing an organization’s ability to detect and prevent MitM attacks. The earlier that detection tools can identify and prevent MitM attacks, the better the business network security is.
Network Traffic Monitoring
Continuous network traffic monitoring is essential for man-in-the-middle attack prevention and detection. Analyzing network traffic patterns can help identify anomalies and suspicious activities that may indicate a MitM attack in progress. Security Information and Event Management (SIEM) systems can aggregate and correlate security data from various sources, providing a comprehensive view of the network security posture. By proactively monitoring network traffic, security teams can quickly detect and respond to potential MitM threats, minimizing the impact of a successful attack. This proactive approach is a critical component of any effective cyber security strategy, ensuring that sensitive information remains protected. Effective network traffic monitoring helps detect if a network is vulnerable to MitM attacks.
Ways to Prevent Man-in-the-Middle Attacks
Secure Wi-Fi Networks
Securing Wi-Fi networks is crucial to prevent MitM attacks, especially those targeting local network connections. Using strong encryption protocols, such as WPA3, can protect data transmitted over Wi-Fi from interception. Always use a strong Wi-Fi password and change it regularly to prevent unauthorized access to the network. Avoid using public Wi-Fi networks without a virtual private network (VPN), as these networks are often unsecured and vulnerable to MitM attacks. Implementing these best practices enhances network security and reduces the risk of attackers intercepting sensitive data and login credentials. When connecting to a Wi-Fi network, always ensure that the connection is secure and encrypted, protecting against potential spoofing attacks.
Using Strong Passwords
Employing strong passwords is a fundamental security measure to prevent MitM attacks. Strong passwords should be complex, consisting of a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable passwords or reusing the same password across multiple accounts. Password managers can help generate and store strong, unique passwords for each account, reinforcing strong security measures against unauthorized access. Regularly changing passwords further enhances security, making it more difficult for attackers to crack them. Strong passwords protect against unauthorized access to accounts and sensitive data, reducing the risk of successful MitM attacks. Using a strong password with multi-factor authentication is crucial to prevent MitM attacks.
Certificate Management
Effective certificate management is crucial to prevent MitM attacks that exploit vulnerabilities in SSL certificates and can increase the attack surface for security breaches. Ensuring that all SSL certificates are valid, properly configured, and issued by trusted certificate authorities is essential. Regularly monitor certificates for expiration and renew them promptly to avoid security vulnerabilities. Implement Certificate Authority Authorization (CAA) records to restrict which certificate authorities can issue certificates for your domain. By maintaining proper certificate management practices, organizations can mitigate the risk of attackers using fraudulent or compromised certificates to intercept communication between two parties and conduct man-in-the-middle attacks. Expired certificates or invalid certificates can be easily targeted in phishing attacks, so it’s important to maintain good certificate management in order to prevent MitM attacks.
5 Surprising Facts About Preventing Man-in-the-Middle Attacks at Layer 2
- Layer 2 attacks can often go unnoticed, as they do not typically trigger traditional network security alerts.
- Many Layer 2 protocols, such as ARP, are inherently insecure, making them prime targets for man-in-the-middle attacks.
- Implementing port security on switches can significantly reduce the risk of unauthorized access and man-in-the-middle attacks at Layer 2.
- Using VLAN segmentation can help contain the impact of a man-in-the-middle attack, limiting its spread across the network.
- Regularly updating network device firmware can patch vulnerabilities that could be exploited in Layer 2 attacks.
What is a man-in-the-middle attack and how does it occur?
A man-in-the-middle attack (MITM) is a cyber attack where a malicious actor intercepts communication between two parties without their knowledge. This can occur within a local network, especially when users connect to unsecured access points or use outdated security protocols, allowing attackers to eavesdrop or alter the data being transmitted.
What are the best practices for preventing man-in-the-middle attacks?
Best practices for preventing MITM attacks include implementing strong encryption methods, using secure SSL connections, and employing effective security policies. Regular security awareness training for employees can also help in identifying potential threats and securing sensitive information.
How can I detect man-in-the-middle attacks on my network?
Detection of MITM attacks can be achieved through monitoring network traffic for unusual patterns, using intrusion detection systems, and employing tools that alert administrators to potential ARP spoofing attacks. Regular audits of network security can also help in identifying vulnerabilities.
What types of man-in-the-middle attacks should I be aware of?
There are several types of MITM attacks, including passive eavesdropping, session hijacking, and ARP spoofing. Each type exploits different vulnerabilities in the network and requires specific defenses against MITM to mitigate the risks effectively.
What security measures can stop MITM attacks?
To stop MITM attacks, organizations should implement security solutions such as VPNs, strong authentication methods, and encryption for data in transit. Additionally, educating users about the risks associated with public Wi-Fi networks can enhance protection against MITM attacks.
How can stronger security practices mitigate MITM threats?
Stronger security practices, such as keeping software up to date, using multi-factor authentication, and enforcing strict security policies, can significantly mitigate MITM threats. By eliminating vulnerabilities in the network, organizations can reduce the likelihood of successful attacks.
What role does encryption play in preventing man-in-the-middle attacks?
Encryption plays a critical role in preventing MITM attacks by ensuring that any intercepted data remains unreadable to the attacker. Using protocols like SSL/TLS helps secure communications and protect sensitive information from being compromised during transmission.
Why is security awareness training important for preventing MITM attacks?
Security awareness training is vital for preventing MITM attacks as it educates employees about the risks and signs of such attacks. By fostering a culture of security awareness, organizations can empower their staff to recognize potential threats and adhere to best practices that enhance overall network security.





