How to Build a Secure Software Supply Chain.
How Guide to Build A Secure Software Supply Chain Security: Best Practices Guide to Software Supply Chain
In the digital era, secure software development is more important than ever to combat emerging security issues. securing the software supply chain has become a critical priority for organizations across the globe. As the complexity of software development and deployment increases, so does the potential for security vulnerabilities. This guide aims to empower businesses to navigate the intricacies of software supply chains, providing best practices, including security checks, to fortify your defenses and ensure the security of your applications. Our professional and dedicated approach ensures your enterprise is safeguarded today, securing tomorrow’s success.
Understanding Software Supply Chains
What are Software Supply Chains?
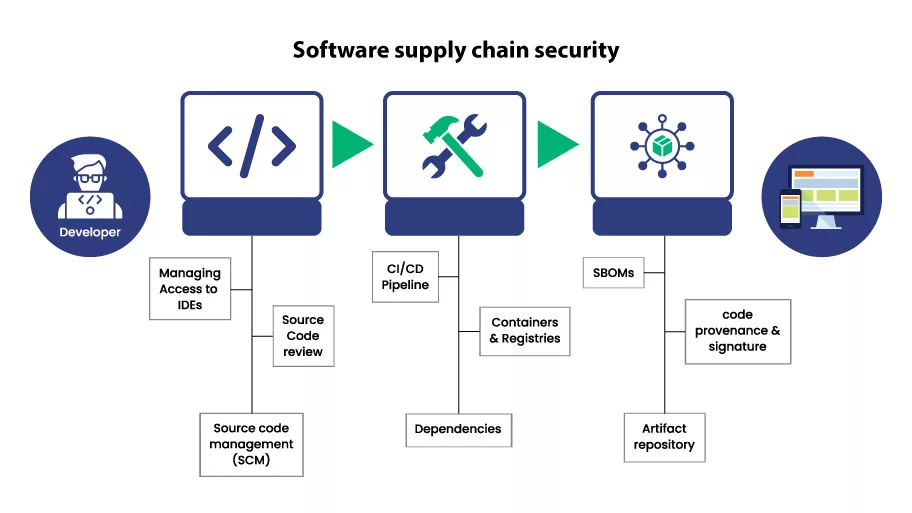
Software supply chains encompass the entire network of processes and components involved in the creation and delivery of software applications, including open source software. These chains include everything from the development of source code to the integration of open-source software and third-party components. Understanding the full scope of your software supply chain is essential to identify potential security risks and implement effective security measures. By recognizing the interconnected nature of these components, organizations can better anticipate and mitigate supply chain attacks that threaten their infrastructure.
Components of Software Supply Chains
The modern software supply chain comprises various components, including open source software, each playing a pivotal role in the software development lifecycle. This includes the software bill of materials, build processes, and security controls that govern the integration of open-source software and proprietary solutions. Application security testing, both dynamic and static, is crucial to ensure that each software component is secure. By maintaining rigorous security best practices, organizations can enhance their security posture, minimizing the risk of security breaches and ensuring that their software applications are reliable and secure.
The Importance of Supply Chain Security
Supply chain security is paramount in safeguarding your enterprise against potential threats. As supply chain attacks become increasingly sophisticated, organizations must prioritize securing the software supply chain to protect their assets and maintain trust with their customers. A robust security posture not only prevents security vulnerabilities but also fosters a culture of security awareness within the organization. By adopting comprehensive supply chain security best practices, businesses can fortify their defenses, ensuring that security teams are equipped to handle evolving risks and protect the integrity of the entire software supply chain.
Software Supply Chain Security Overview
What is Software Supply Chain Security?
Software supply chain security refers to the comprehensive set of measures and best practices designed to protect the entire lifecycle of software development and distribution. This includes securing the software bill of materials, ensuring robust application security testing, and implementing stringent security controls at every stage. By understanding and managing the various security risks associated with software components, including open source software, organizations can enhance their security measures., including open-source software and proprietary solutions, organizations can fortify their defenses against potential supply chain attacks. Our approach emphasizes a secure software supply chain, ensuring that your business infrastructure remains resilient and trustworthy.
Common Security Threats in Software Supply Chains
In the modern landscape of software development, common security threats within software supply chains include malicious code injection, compromised open-source dependencies, and vulnerabilities in the build process. These threats can lead to devastating software supply chain attacks, compromising sensitive data and disrupting business operations. By recognizing these potential security vulnerabilities, organizations can implement proactive security measures and adopt supply chain security best practices. Our vigilant approach, coupled with comprehensive security tools, empowers security teams to anticipate and mitigate these threats effectively, ensuring that your software applications remain secure and reliable.
Impact of Supply Chain Attacks
Supply chain attacks can have far-reaching consequences, affecting not just the targeted organization but also its customers and partners, highlighting the need for secure software development practices. Such attacks can lead to severe financial losses, reputational damage, and breaches of sensitive data. They underscore the importance of securing the software supply chain to protect the integrity of your software applications and maintain customer trust. By adopting a proactive security posture and implementing robust security practices By prioritizing secure software development practices, organizations can mitigate the impact of these attacks. Our commitment to safeguarding your enterprise ensures that you are well-equipped to handle supply chain risks and secure your software assets.
Identifying Software Supply Chain Risks
Types of Supply Chain Risks
In the realm of software development, various types of supply chain risks pose significant threats to organizations. These risks encompass security vulnerabilities arising from open-source software components, such as outdated libraries and malicious code injections. The build process itself can also be a source of concern if not adequately secured, potentially allowing unauthorized access or tampering. Organizations must be vigilant in identifying potential security risks within their software supply chains to prevent supply chain attacks, which can lead to severe data breaches and disrupt business operations.
Assessing Your Software Supply Chain Risk
Assessing software supply chain risk is a crucial step in securing your software assets. This involves evaluating each component within the supply chain, from software vendors to open-source dependencies, to identify potential security vulnerabilities through software composition analysis. By conducting thorough risk assessments, including software updates and security checks, organizations can better protect their software supply chains. By implementing security checks, organizations can prioritize security measures and allocate resources effectively. Such assessments should consider both internal and external factors, ensuring a comprehensive understanding of the entire software supply chain. This proactive approach enables organizations to fortify their defenses, safeguarding against potential threats and enhancing their overall security posture.
Tools for Risk Assessment
To efficiently identify and mitigate software supply chain risks, organizations can leverage a variety of specialized tools. These tools include static and dynamic application security testing solutions, which are instrumental in detecting security vulnerabilities within software components. Additionally, utilizing a software bill of materials can provide transparency, enabling security teams to track and assess the integrity of third-party and open-source software. By employing these advanced security tools, organizations can bolster their defenses, ensuring that their software supply chains remain resilient against potential supply chain attacks and other security threats.
Best Practices for Securing the Software Supply Chain
Implementing Security Best Practices
Adopting comprehensive security best practices is essential for securing the software supply chain. Organizations should establish robust security controls throughout the software development lifecycle, ensuring that every stage is fortified against potential threats. This includes implementing secure coding practices, conducting regular security audits, and continuously monitoring for anomalies. By instilling a culture of security awareness among development teams, businesses can enhance their security posture, minimizing the risk of security breaches. Our guide to software supply chain security emphasizes these best practices, empowering your enterprise to remain secure and resilient.
Using Software Bill of Materials for Transparency
A software bill of materials (SBOM) serves as a vital tool for achieving transparency within your software supply chain. By providing a detailed inventory of all components, including open-source software, an SBOM enables organizations to track and manage potential security vulnerabilities effectively. This transparency allows for timely updates and patches, reducing the risk of supply chain attacks. Implementing an SBOM is a best practice that enhances the security of your software applications, ensuring that your infrastructure remains safeguarded against emerging threats and that customer trust is maintained.
Application Security Testing Techniques
Application security testing techniques, such as static application security testing, are critical in identifying and addressing security vulnerabilities within your software applications. By employing both static and dynamic application security testing methods, organizations can thoroughly evaluate their software components for weaknesses. These testing techniques help detect potential security risks before they can be exploited, allowing for timely remediation. Ensuring that application security testing is an integral part of your software development process Implementing security checks is a best practice that fortifies your defenses, safeguarding your enterprise against supply chain attacks and ensuring the reliability of your software supply chain.
Strategies to Mitigate Supply Chain Attacks
Proactive Measures Against Supply Chain Attacks
In the ever-evolving landscape of software development, implementing proactive measures is crucial to securing your software supply chain against potential threats. Organizations must establish robust security controls that encompass every facet of the software development lifecycle to prevent supply chain attacks. This includes conducting regular security audits, enhancing visibility through a software bill of materials, and fostering a culture of security awareness among development teams. By actively identifying and addressing security vulnerabilities, businesses can fortify their defenses, ensuring the integrity of their software applications and safeguarding their infrastructure.
Incident Response Plans for Supply Chain Breaches
Having a well-defined incident response plan is essential for effectively managing supply chain attacks. Organizations must be prepared to react swiftly to security breaches to mitigate damage and protect sensitive data. This involves establishing a dedicated security team equipped with the necessary tools to identify and respond to threats promptly. Regular training and simulated attack scenarios can help ensure that response teams are ready to tackle real-world security challenges. A robust incident response plan not only minimizes the impact of a breach but also reinforces customer trust and confidence in your organization’s commitment to security.
Continuous Monitoring of Software Supply Chains
Continuous monitoring of software supply chains is a critical strategy for maintaining a secure software environment. By leveraging advanced security tools and dynamic application security testing techniques, organizations can detect anomalies and potential threats in real-time. This proactive approach allows security teams to anticipate and address security issues before they can be exploited. Continuous monitoring ensures that your software components remain compliant with security best practices, reducing the likelihood of supply chain attacks. The commitment to vigilance and constant improvement fortifies your enterprise against emerging threats and ensures the resilience of your software applications.
Conclusion
Summarizing Key Takeaways
In conclusion, implementing software composition analysis is essential for organizations to ensure robust security measures. securing the software supply chain is a multifaceted endeavor requiring a comprehensive approach. Key takeaways emphasize the importance of understanding software supply chains, the value of employing a software bill of materials, and the necessity of rigorous application security testing. Organizations must prioritize supply chain security best practices to mitigate potential security risks effectively. By adopting proactive measures, maintaining continuous monitoring, and ensuring a robust incident response plan, businesses can safeguard their infrastructure, ensuring the reliability and security of their software applications and, ultimately, their success.
Future Trends in Software Supply Chain Security
Looking ahead, the landscape of software supply chain security is poised for significant evolution. As organizations continue to recognize the importance of securing their entire software supply chain, the adoption of advanced technologies such as artificial intelligence and machine learning for threat detection will become increasingly prevalent. Furthermore, the integration of blockchain technology may offer enhanced transparency and traceability within software development processes. By staying abreast of these emerging trends and adapting to the evolving threat landscape, organizations can maintain a competitive edge and ensure the ongoing security of their software applications.
Final Recommendations for Secure Software
To secure your software supply chain, it is imperative to implement a holistic security strategy that encompasses all aspects of software development and distribution. This includes establishing stringent security controls, fostering a culture of security awareness, and leveraging advanced security tools to monitor and protect your software components. Organizations should remain vigilant and proactive in addressing security vulnerabilities, ensuring that their security posture is robust and resilient against potential threats. By prioritizing software supply chain security, businesses can protect their assets, maintain customer trust, and ensure the continued success and integrity of their software applications.
5 Surprising Facts About How to Build a Secure Software Supply Chain
- Many organizations underestimate the risk of third-party components, with studies showing that over 80% of software contains open-source libraries.
- Implementing automated security testing throughout the development lifecycle can reduce vulnerabilities by up to 50%.
- Supply chain attacks have increased by over 300% in the past year, highlighting the importance of securing every link in the chain.
- Over 60% of breaches occur due to misconfigured cloud settings, emphasizing the need for secure cloud practices in supply chain management.
- Training developers on secure coding practices can prevent up to 80% of security flaws in the software supply chain.
What are the best practices for securing the software supply chain?
To secure your software supply chain, it is essential to implement security best practices such as conducting regular security assessments, utilizing a software bill of materials (SBOM), and ensuring compliance with security frameworks. Additionally, organizations should adopt secure coding practices and maintain ongoing communication with software vendors to manage software dependencies effectively.
How can supply chain attacks compromise the security of software?
Supply chain attacks can compromise the security of software by exploiting vulnerabilities in third-party software or components within the software development lifecycle. Attackers may insert malicious code into compromised software, leading to security incidents that affect the integrity of software releases and increase the attack surface for potential security threats.
What is the role of a secure software development framework?
A secure software development framework provides guidelines and practices that help organizations build secure software products. This framework incorporates security practices throughout the software development lifecycle, ensuring that security and compliance are integral to the development process and that software supply chain security is maintained at all levels.
How do I improve software supply chain security?
To improve software supply chain security, organizations should perform risk assessments to identify supply chain vulnerabilities, implement security practices such as application security testing, and ensure that all software dependencies are regularly updated and monitored. Engaging in continuous improvement and training for development teams on security threats is also crucial.
What are the security vulnerabilities in the software supply chain?
Security vulnerabilities in the software supply chain can arise from a variety of sources, including outdated dependencies, insecure coding practices, and lack of visibility into third-party software components. These vulnerabilities can lead to supply chain risks that may expose organizations to attacks and security incidents if not properly managed.
How can organizations protect their software supply?
Organizations can protect their software supply by implementing a comprehensive approach to security that includes standardized security practices, regular security audits, and effective monitoring of supply chain activities. Establishing a secure software supply chain requires collaboration with software vendors to ensure that all components meet security and compliance standards.
What is the impact of software supply chain risk on development practices?
Software supply chain risk can significantly impact development practices by introducing potential security threats that require additional scrutiny and mitigation strategies. Development teams must adapt their practices to include security considerations, which may lead to changes in the software delivery process and increased focus on ensuring the integrity of software artifacts.
What measures can be taken to address supply chain security best practices?
To address supply chain security best practices, organizations should establish clear policies regarding the use of third-party software, maintain an updated inventory of software dependencies, and implement automated tools for monitoring and detecting vulnerabilities. Regular training sessions on secure coding and security awareness can also help reinforce the importance of supply chain security among development teams.